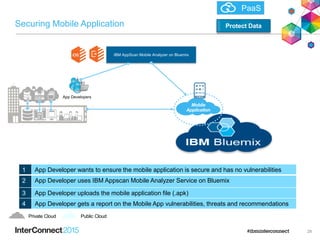
The document discusses IBM's cloud security solutions and their transformative impact on enterprise security practices. It outlines the security features of IBM's infrastructure and platform services, addressing key client imperatives such as threat detection, governance, and data protection. The content also highlights case studies, tools, and practices for managing access and vulnerabilities in cloud environments.