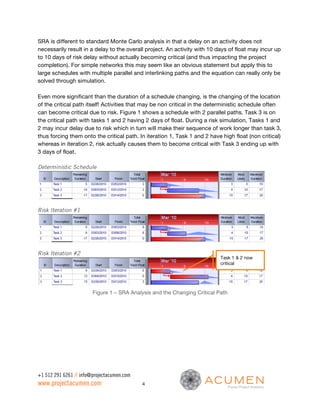
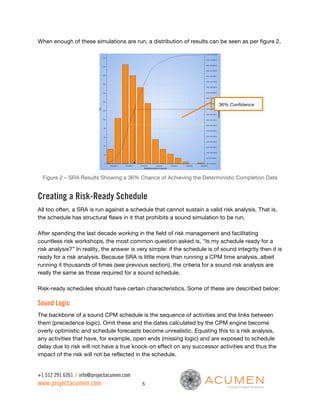
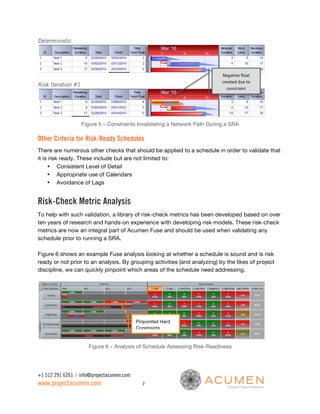
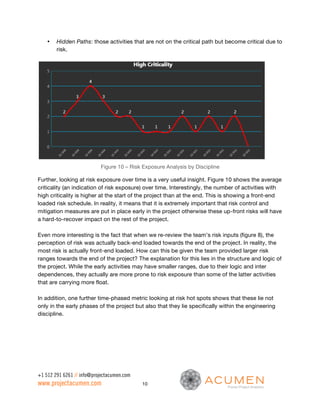
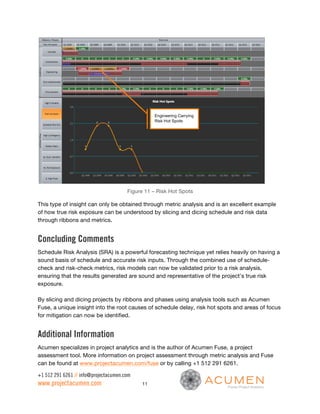
This document discusses the importance of sound schedule integrity and valid risk inputs for effective Schedule Risk Analysis (SRA), emphasizing the use of Monte Carlo simulations to assess project completion dates and associated risks. It outlines criteria for creating risk-ready schedules, highlights the impact of structural flaws, and details metrics for evaluating risk exposure and inputs. The analysis ensures accurate forecasting and identifies risk hot spots, allowing project teams to focus their mitigation efforts effectively.