This document provides an overview of routing protocols and network security concepts. It discusses distance vector protocols like RIP, path vector protocols like BGP, and link state protocols like OSPF. It covers routing attacks such as source routing, spoofing, and man-in-the-middle attacks. It also discusses secure routing requirements and authentication methods used in protocols.






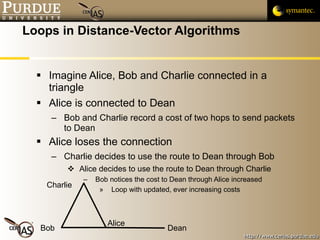


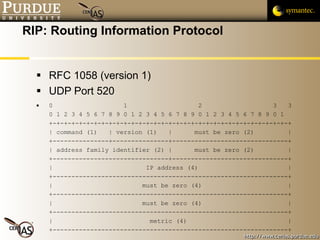


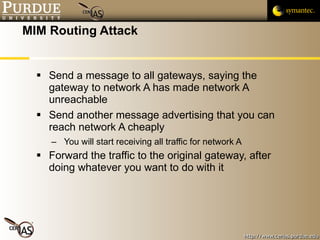

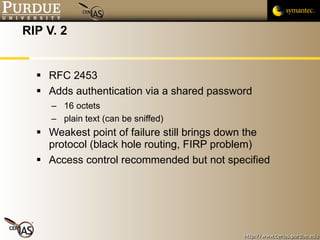














![Pascal Meunier [email_address] Contributors: Jared Robinson, Alan Krassowski, Craig Ozancin, Tim Brown, Wes Higaki, Melissa Dark, Chris Clifton, Gustavo Rodriguez-Rivera](https://image.slidesharecdn.com/6-routing-091013224335-phpapp01/85/6-Routing-48-320.jpg)