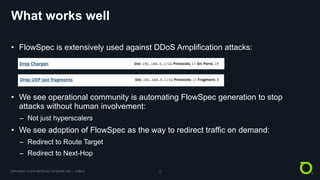
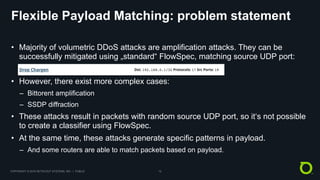
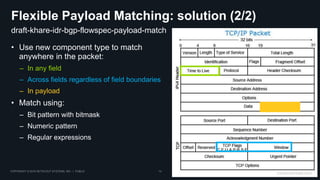
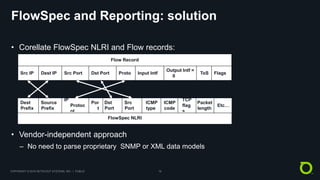
This document discusses BGP FlowSpec, which is a technique for mitigating DDoS attacks. It provides an overview of FlowSpec implementations by various vendors and open source tools. It also discusses operational experience with FlowSpec deployments. While FlowSpec works well against many amplification attacks, the document notes some limitations and areas for improvement. This includes improving router scale, adding flexibility to payload matching, and developing standards for traffic reporting across administrative domains. Overall, FlowSpec is presented as a mature mitigation technique, but one that requires continued development and vendor/operator collaboration to address evolving attacks.