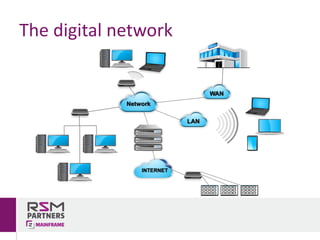
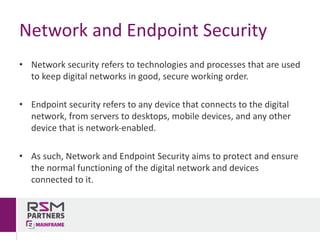
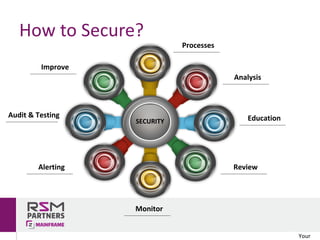
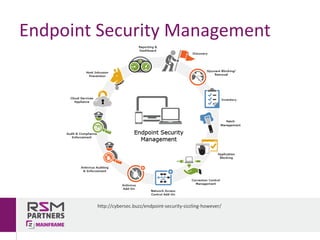
The document discusses network and endpoint security, outlining its importance in protecting digital networks and devices from cyber threats. Key topics include the impact and costs of security breaches, real-world examples of inadequate security measures, and best practices for securing systems. The author, Rui Miguel Feio, emphasizes the need for continuous evaluation, education, and updates to security measures in an increasingly digital world.