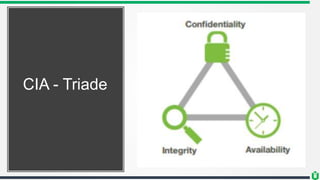
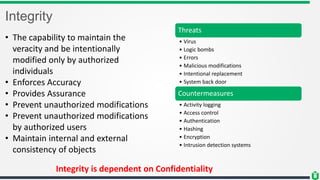
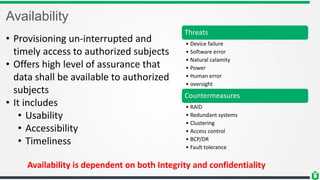
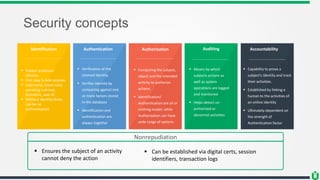
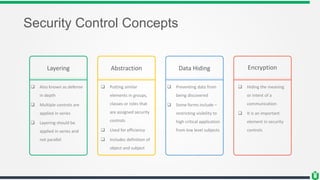
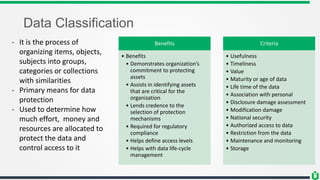
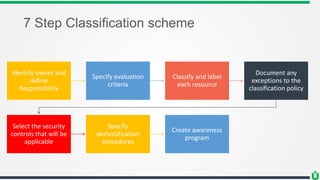
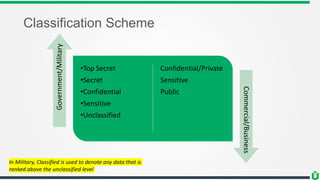
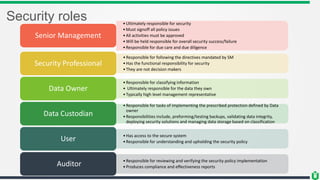
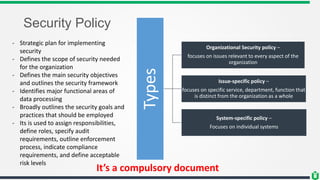
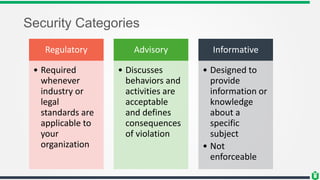
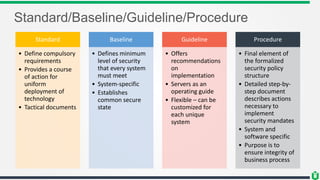
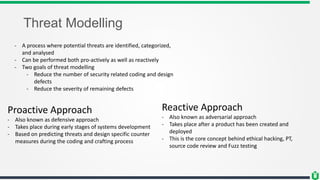
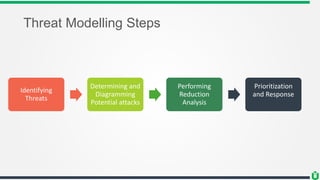
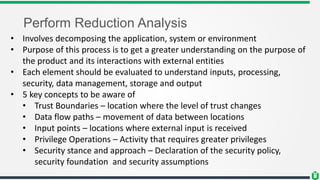
This document provides an overview of security fundamentals including the CIA triad of confidentiality, integrity and availability. It discusses common security threats and countermeasures for each component. Additional concepts covered include identification, authentication, authorization, auditing, accountability, non-repudiation, data classification, roles in security management, due care/diligence, security policies, standards/guidelines, threat modeling and prioritization. The document is intended as a high-level introduction to fundamental security concepts.