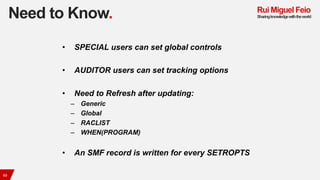
The document provides a comprehensive overview of the Resource Access Control Facility (RACF), an IBM security management product, detailing its functionalities like user identification, access control, and resource protection on mainframe systems. It explains how RACF uses profiles to manage user access to critical resources, categorizing resources into user profiles, group profiles, and dataset profiles, alongside their associated access levels. The document also covers RACF group management and commands for user and group administration, emphasizing the importance of defining access to maintain security protocol.