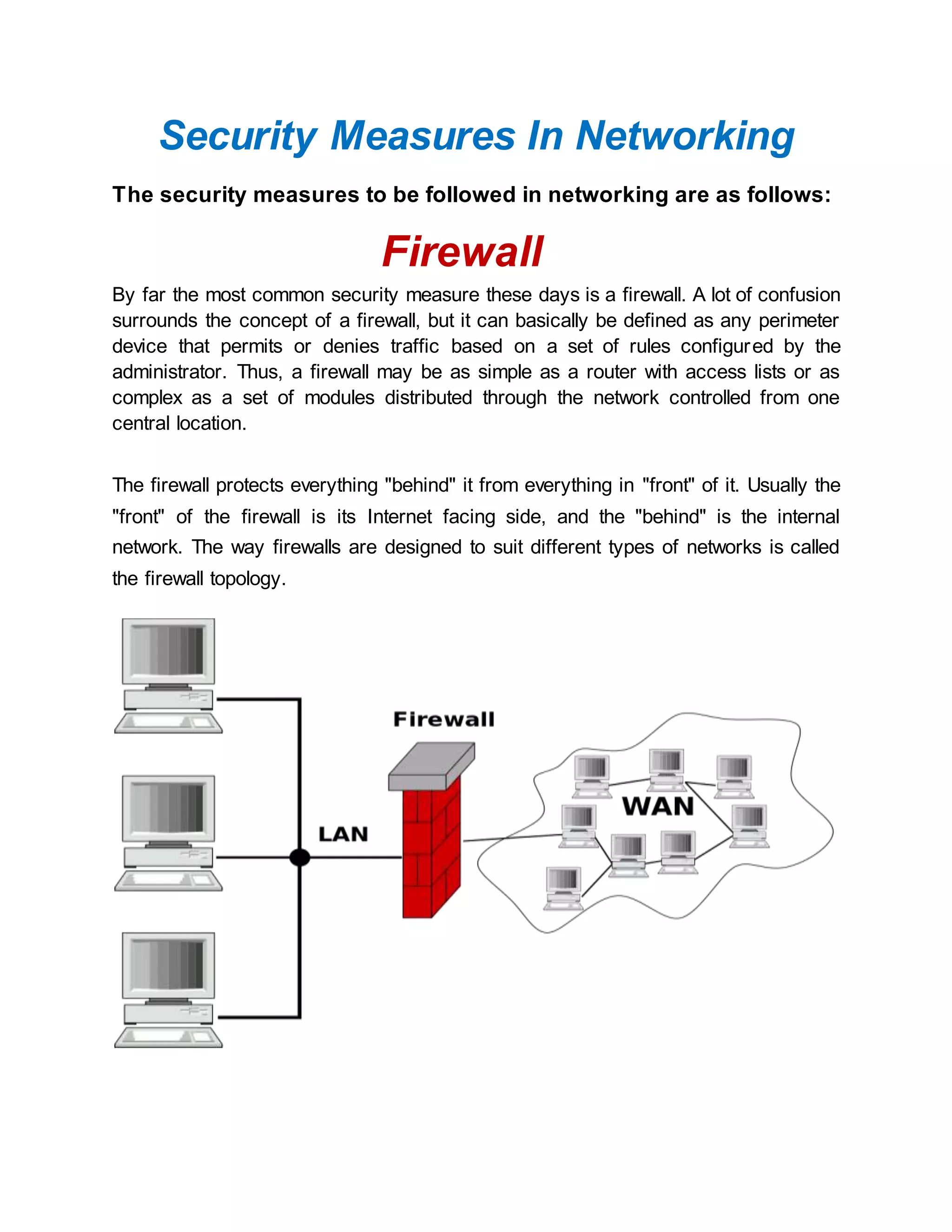
The document discusses various security measures for networking, including firewalls, antivirus systems, intrusion detection systems, and general network tools used by attackers. It describes how firewalls control inbound and outbound traffic based on configured rules. Antivirus systems use signature-based scanning to detect viruses. Intrusion detection systems can be host-based or network-based, and monitor for known attack patterns but can generate false alarms. The document also outlines common network tools used by attackers such as port scanners, network sniffers, and vulnerability scanners.