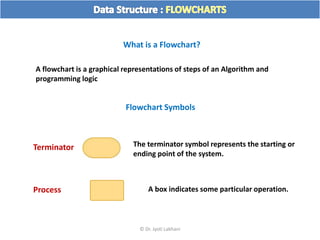
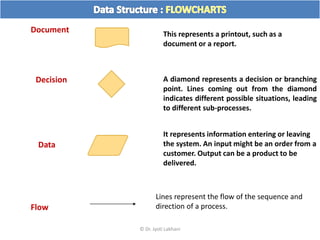
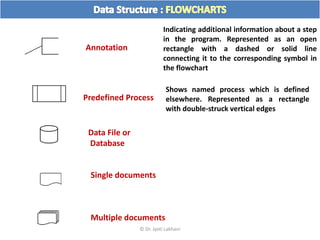
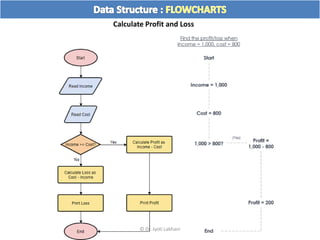
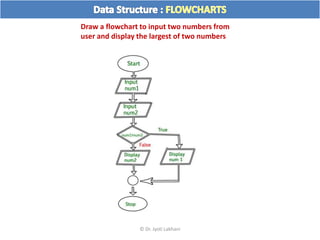
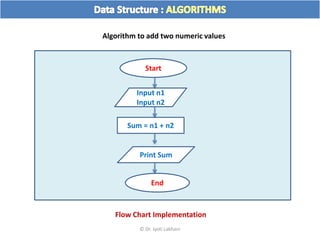
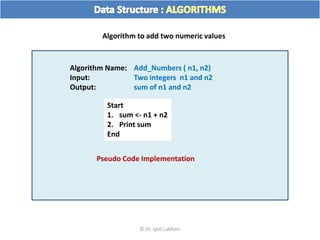
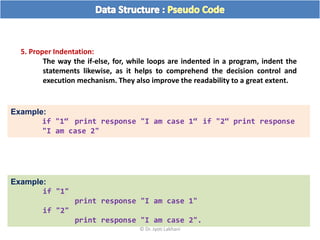
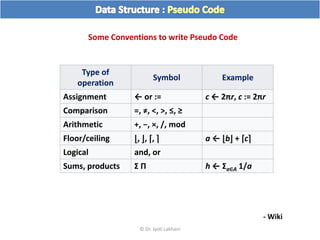
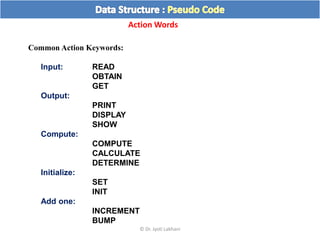
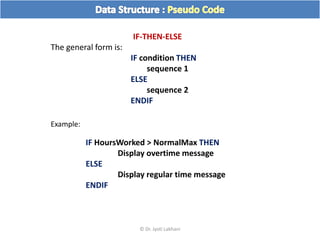
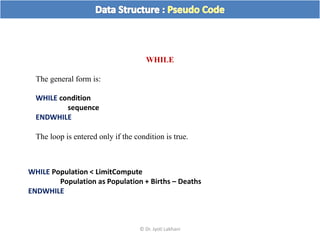
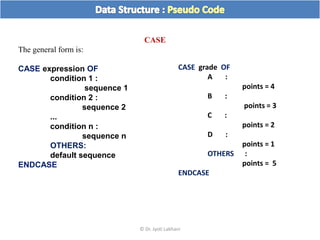
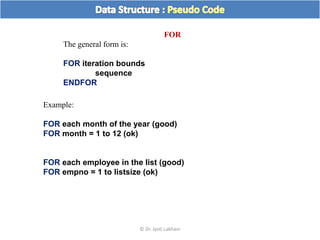
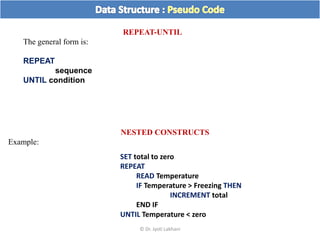
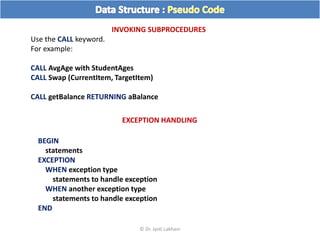
The document discusses flow charts and pseudo code. It provides an overview of flow chart symbols and conventions, examples of algorithms expressed as both a flow chart and pseudo code, guidelines for writing pseudo code, and conventions commonly used in pseudo code.