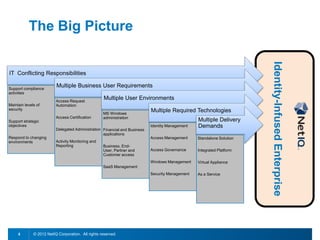
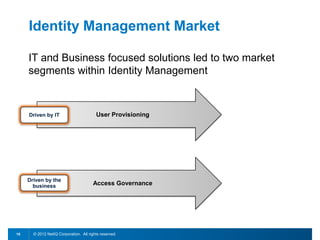
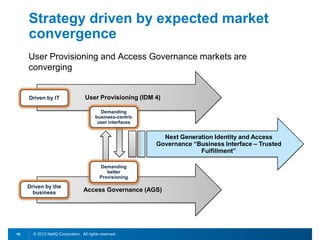
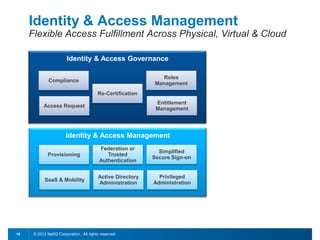
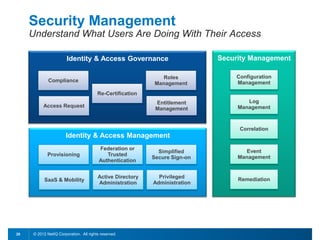
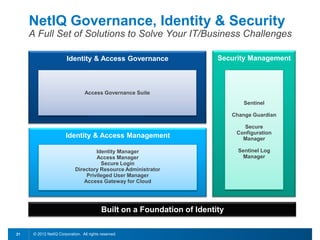
This document discusses leveraging identity to manage change and complexity in computing environments. It notes that computing goals in the 21st century include controlling risks across multiple environments, giving users appropriate access to needed services, and ensuring security, compliance and portability. The document states that change and complexity place pressure on identity and access management (IAM). It outlines an identity-infused enterprise approach and argues that next-generation IAM solutions should provide an integrated platform for identity, access governance, management and security.