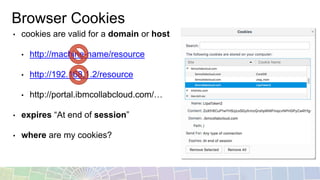
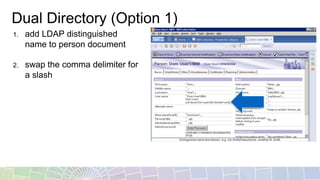
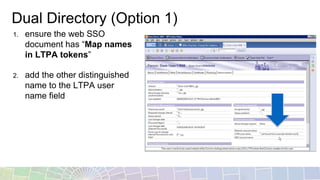
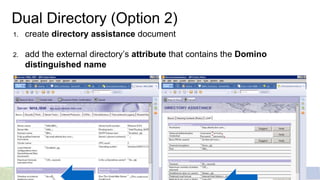
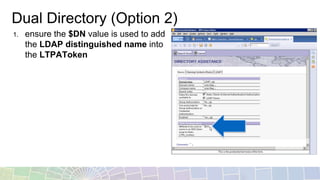
This document provides an overview of different techniques for implementing single sign-on (SSO):
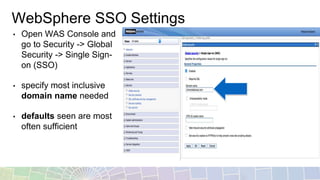
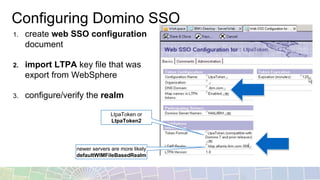
- LTPA is IBM's default SSO mechanism, using a Base64 encoded token containing user identity and expiration time.
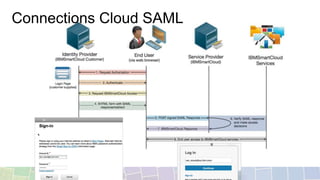
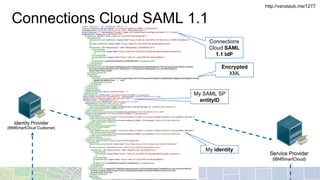
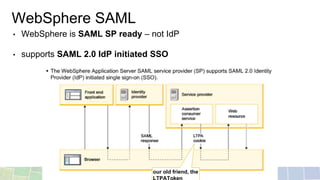
- SAML resolves domain boundaries using cookies and requires additional software, using XML assertion tokens between an identity provider and service provider.
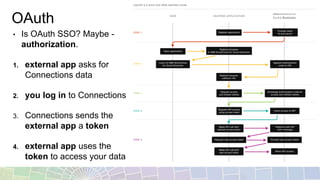
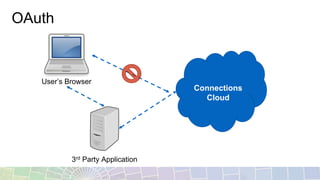
- OAuth allows external apps to access user data in Connections by obtaining a token after the user logs into Connections.
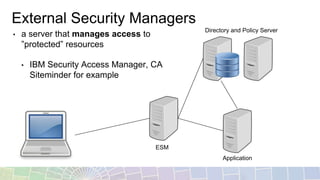
- SPNEGO provides SSO by logging into Windows and accessing IBM software without additional logins. External security managers can also manage access to protected resources across applications.