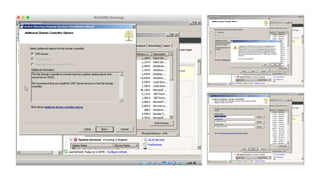
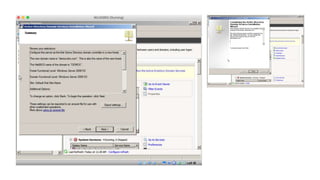
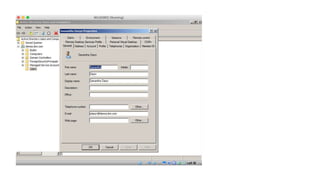
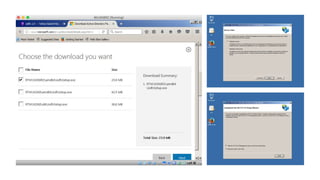
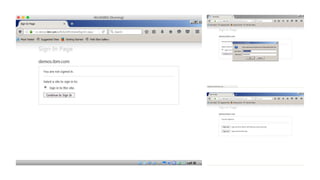
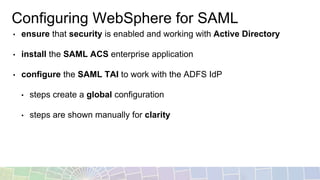
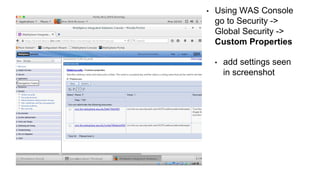
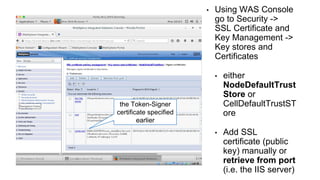
The document outlines the technical enablement process for configuring Active Directory and Active Directory Federation Services (ADFS) for Single Sign-On (SSO) using SAML. It details installation, configuration steps, and notable resources for WebSphere integration, emphasizing the ease of setup and the role of SSL certificates. Additional guides and resources for implementing SSO with various IBM products are also provided.