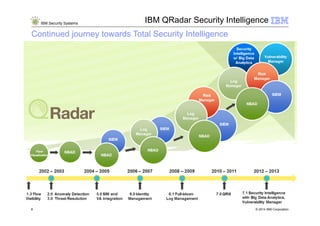
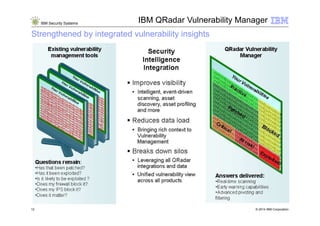
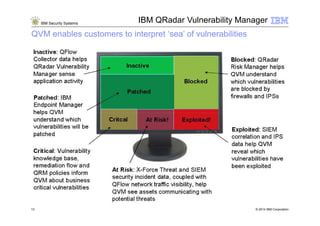
1) Security intelligence refers to the collection, normalization, and analysis of data from users, applications, and infrastructure across an enterprise to gain comprehensive insight into security risks and threats.
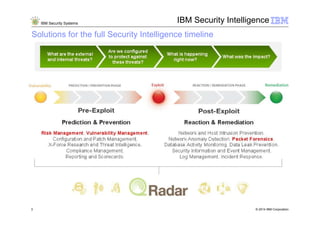
2) IBM Security Intelligence solutions provide security capabilities across the full timeline from protection to detection to remediation.
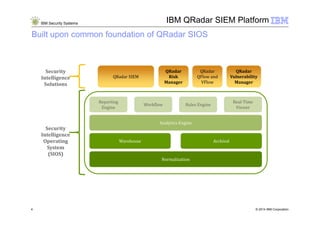
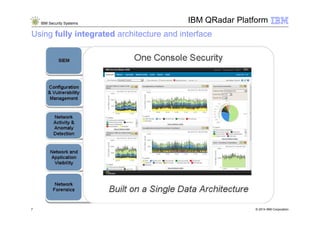
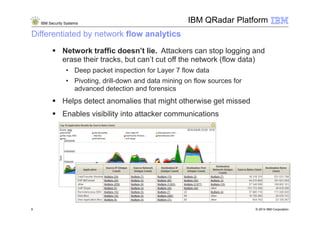
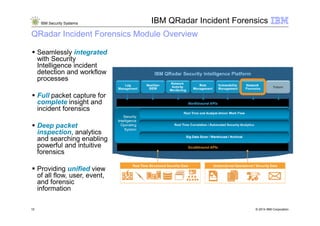
3) The IBM QRadar security intelligence platform collects both structured and unstructured data from multiple sources and performs automated analytics to identify and prioritize security and operational incidents.