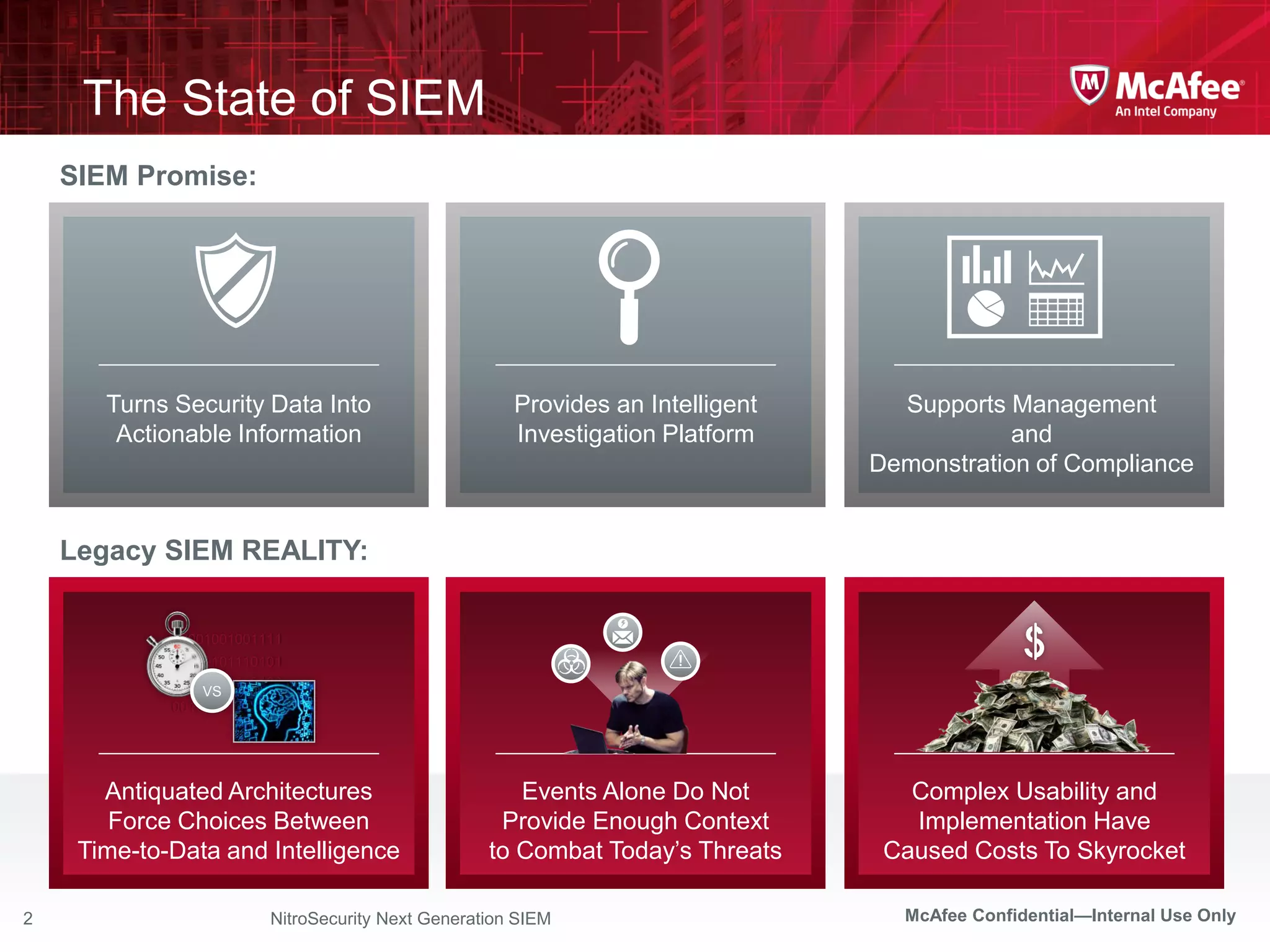
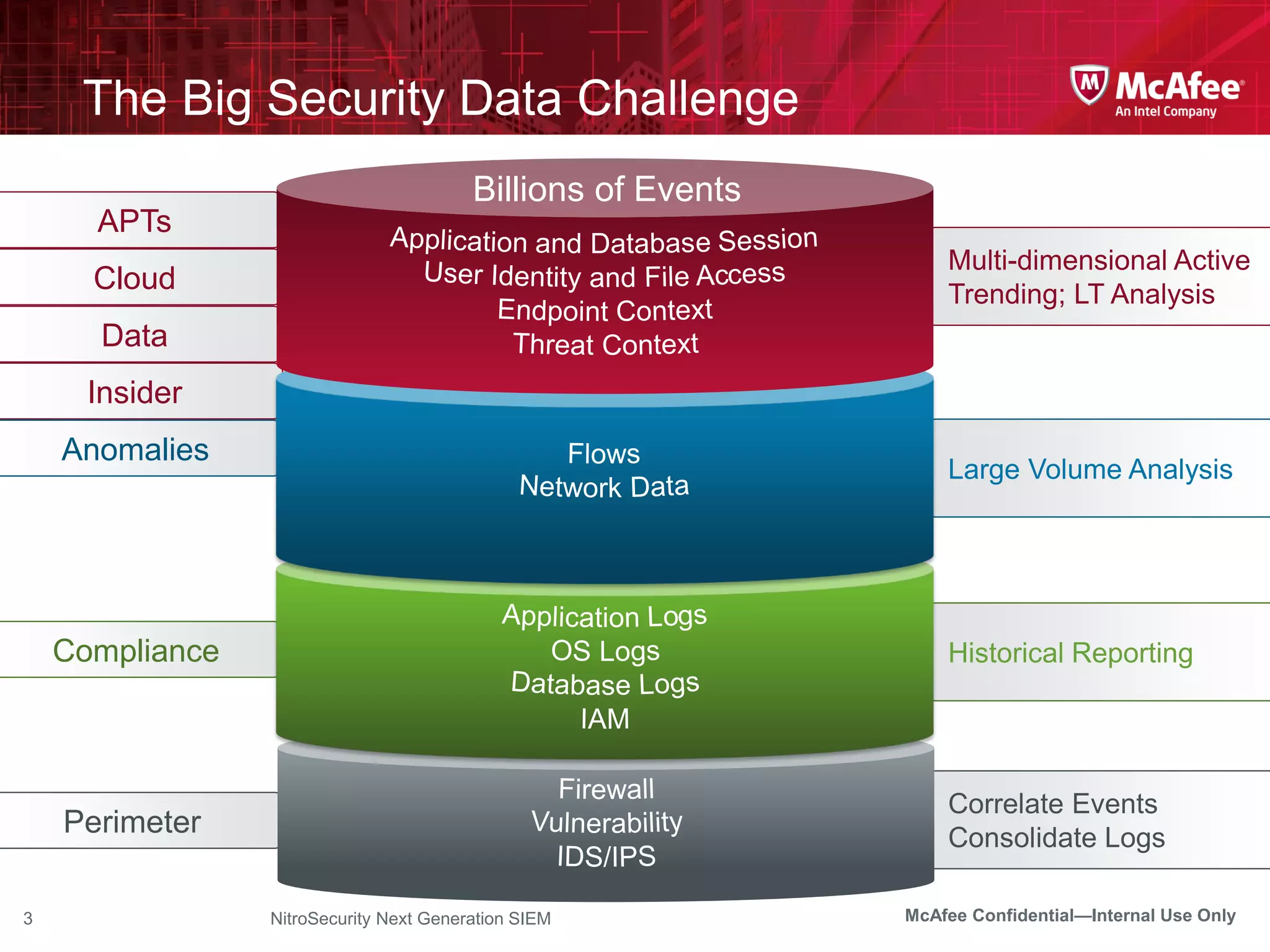
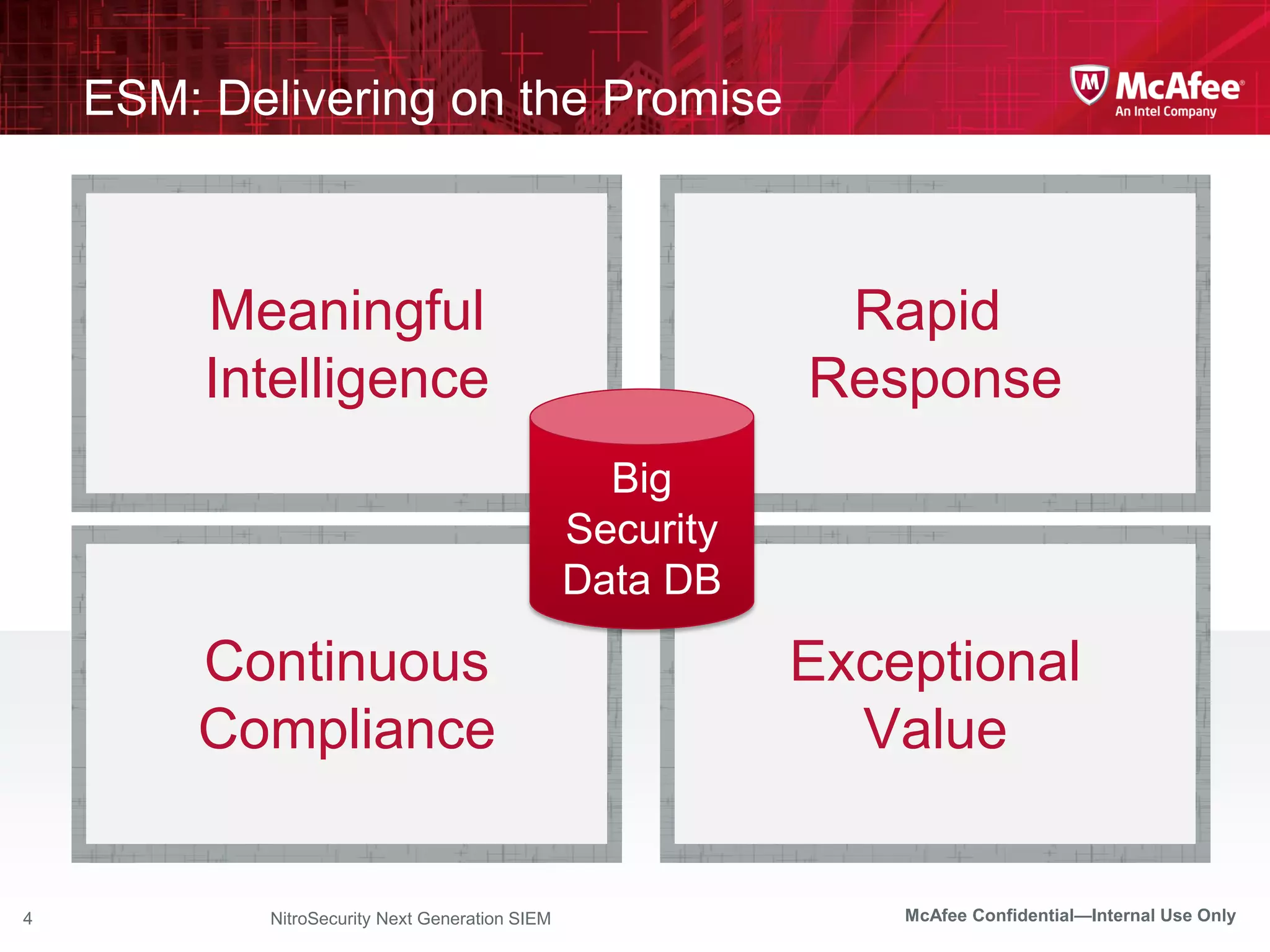
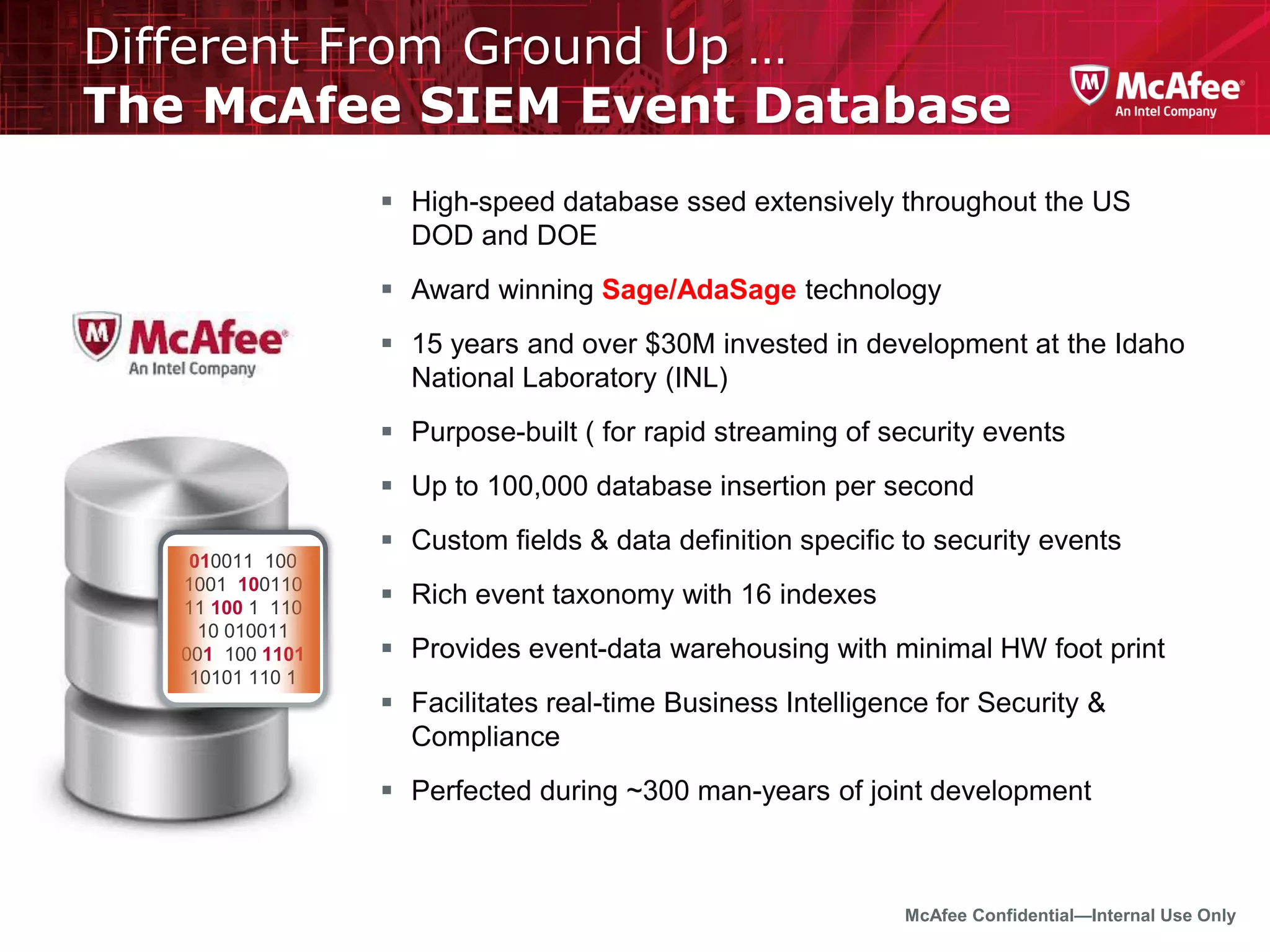
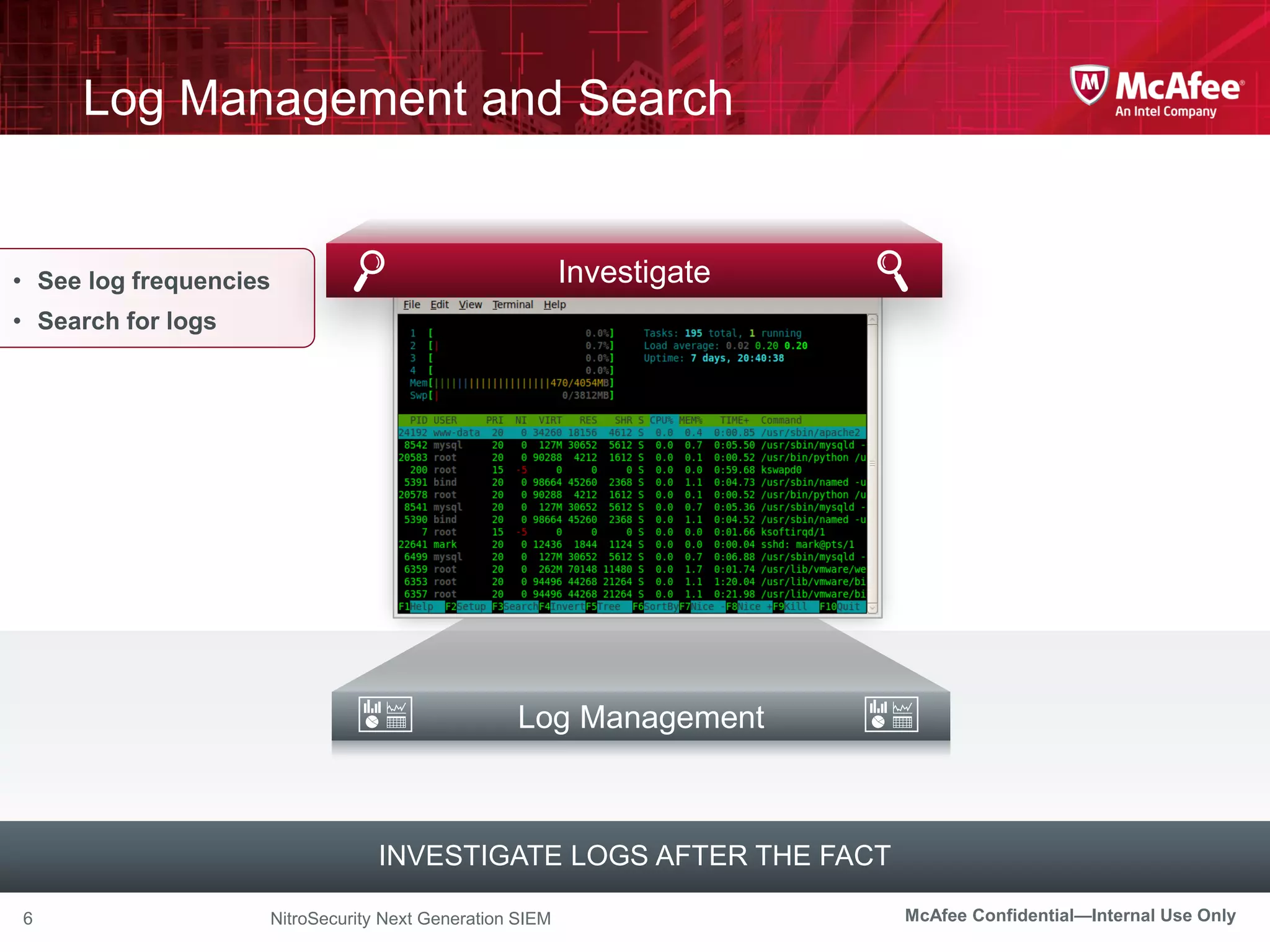
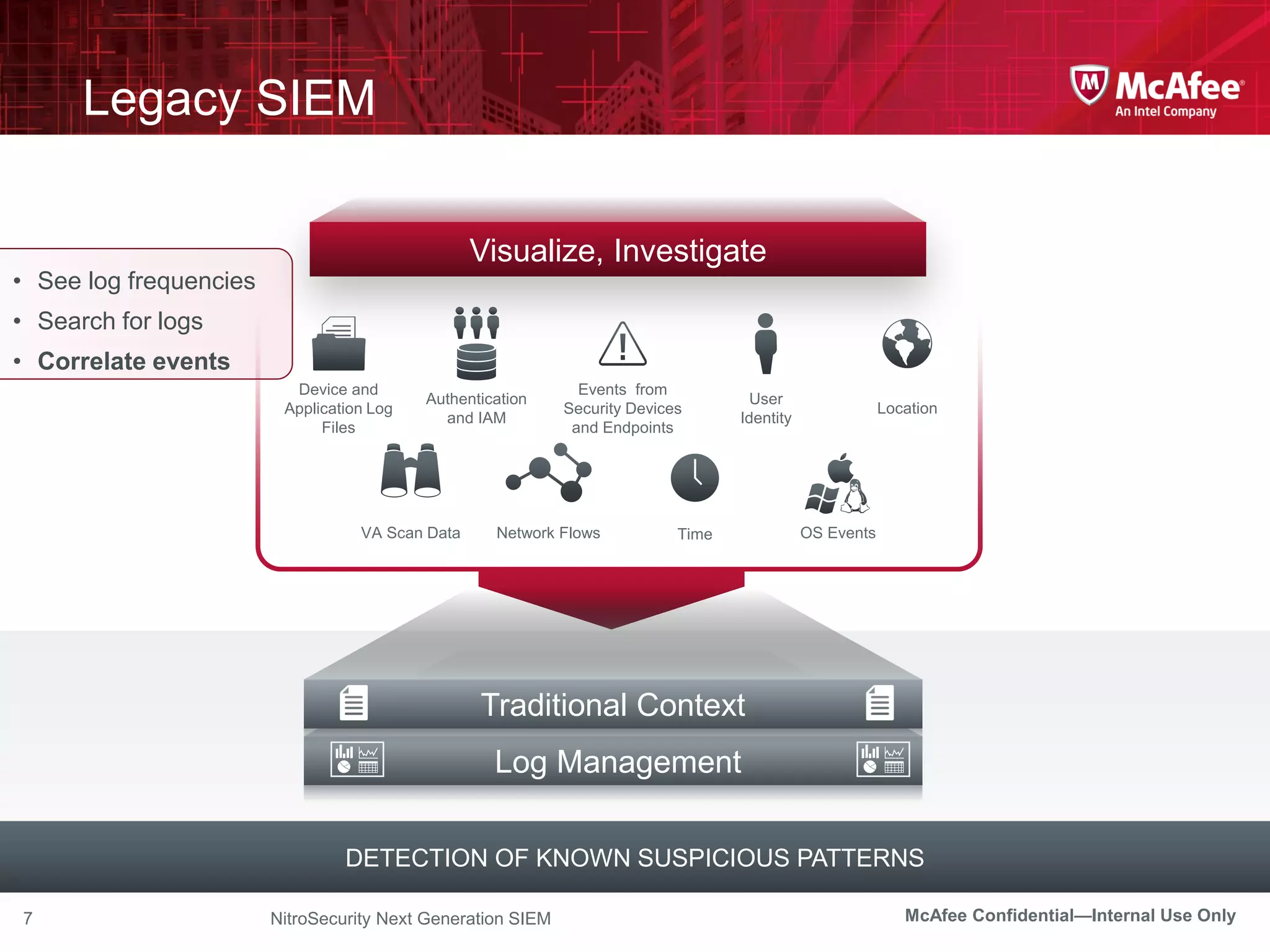
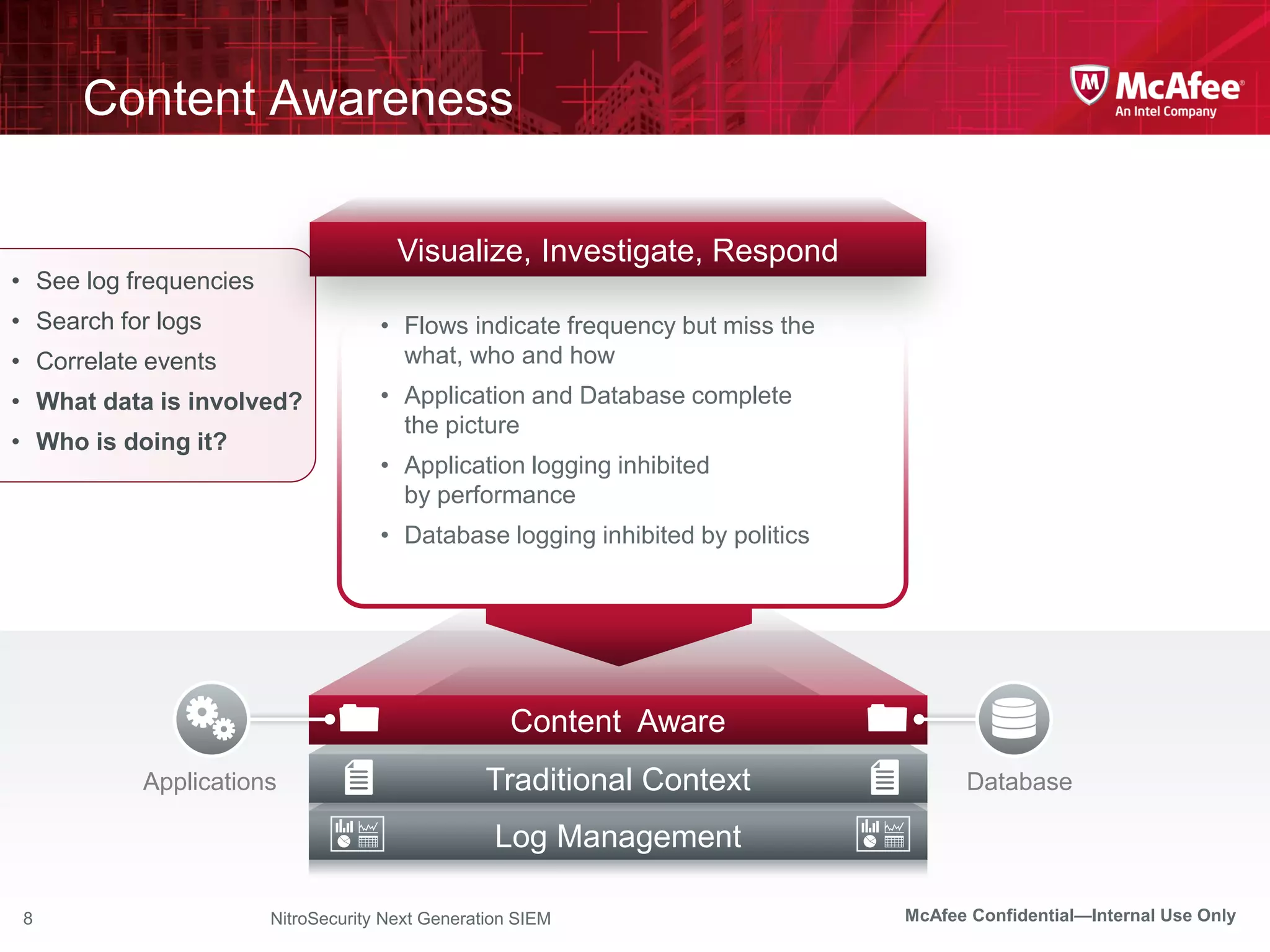
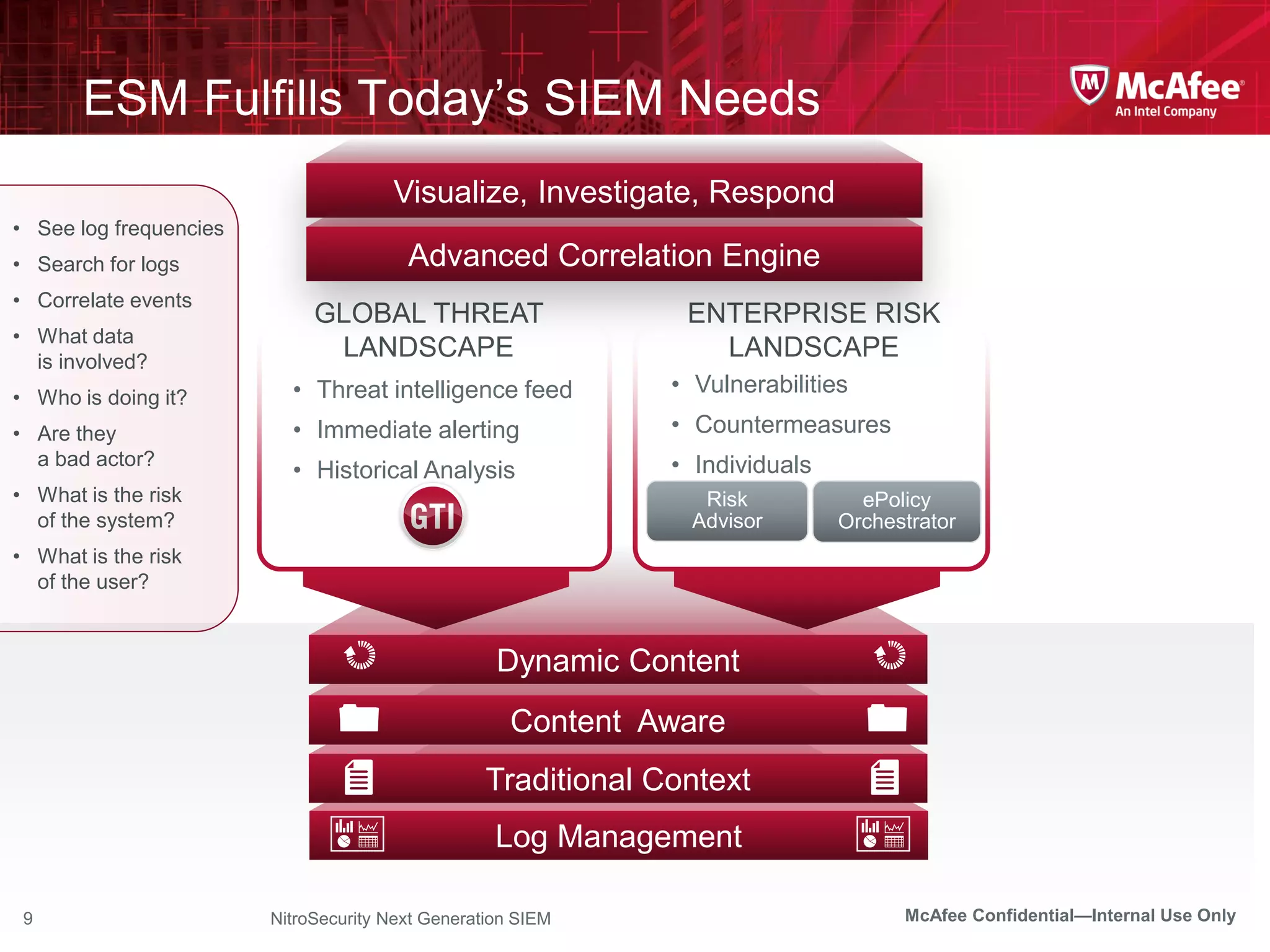
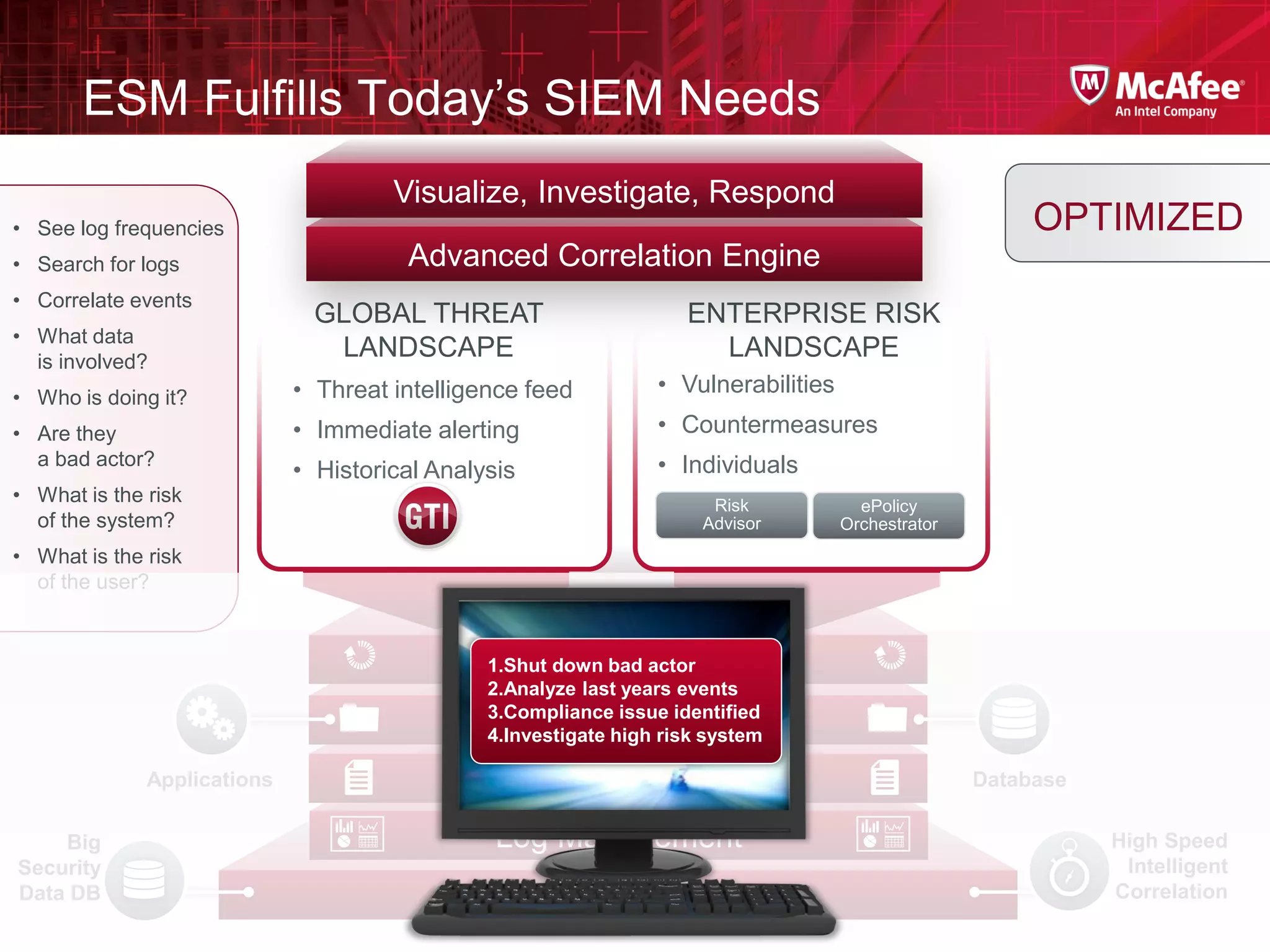
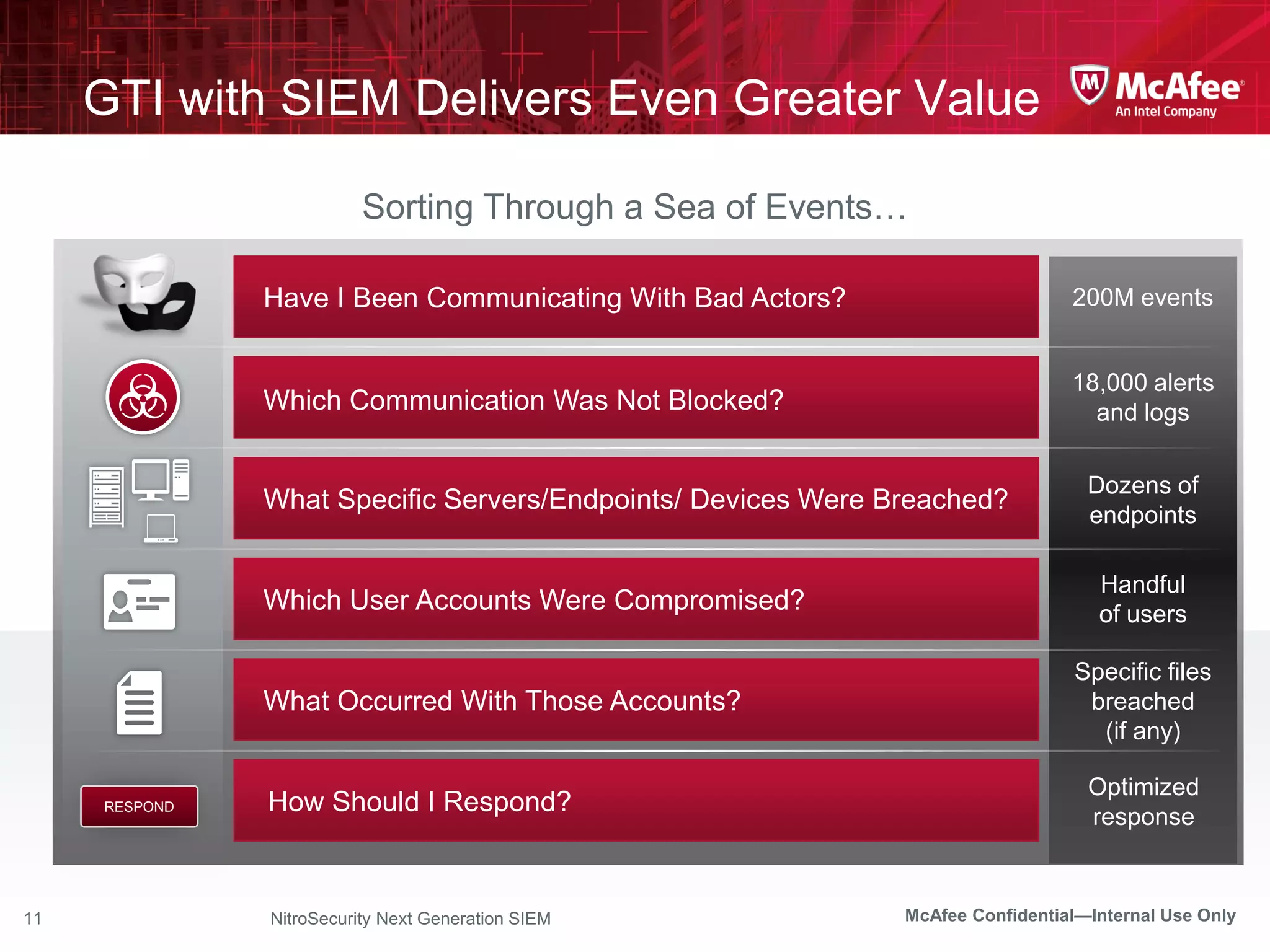
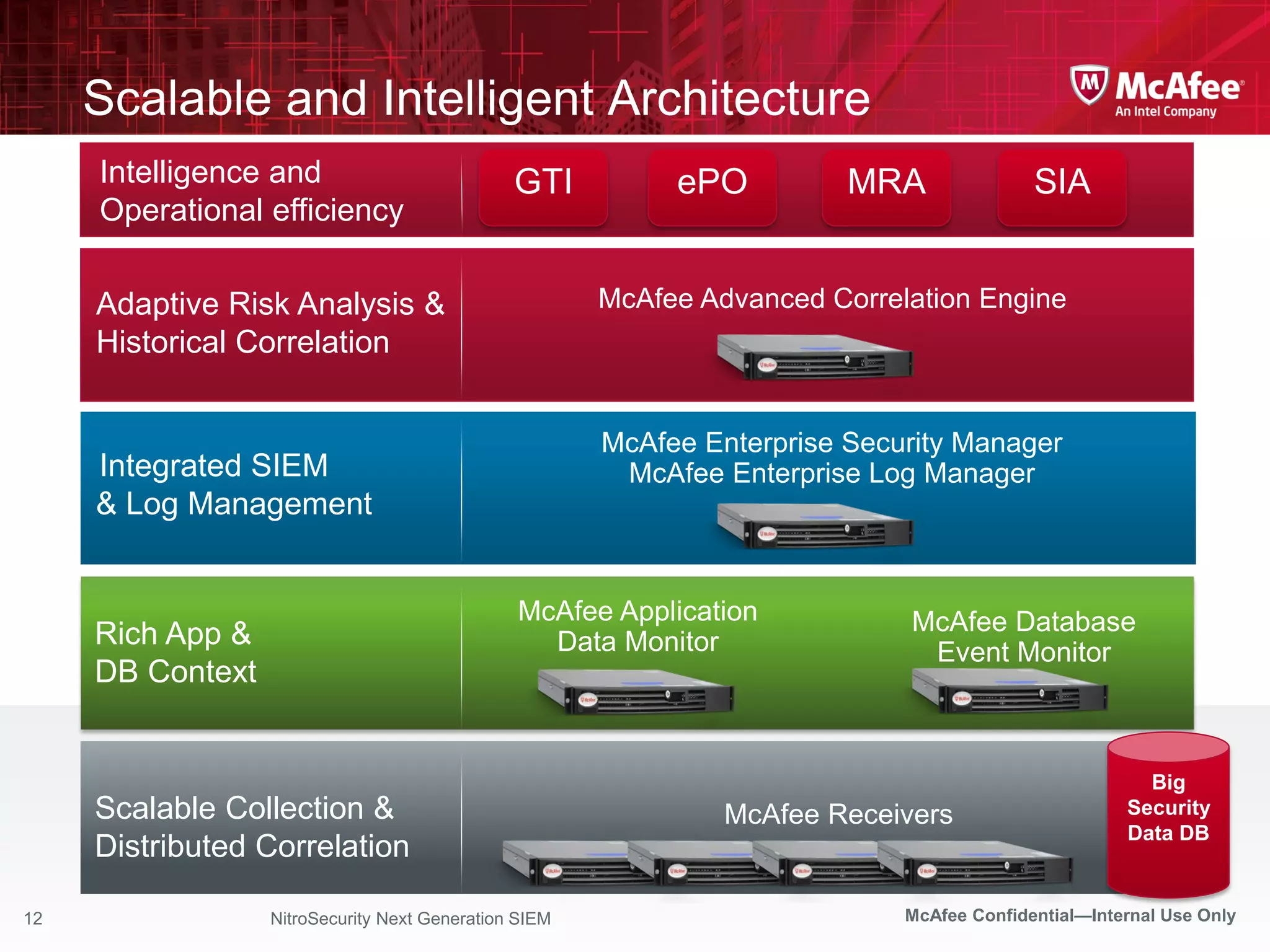
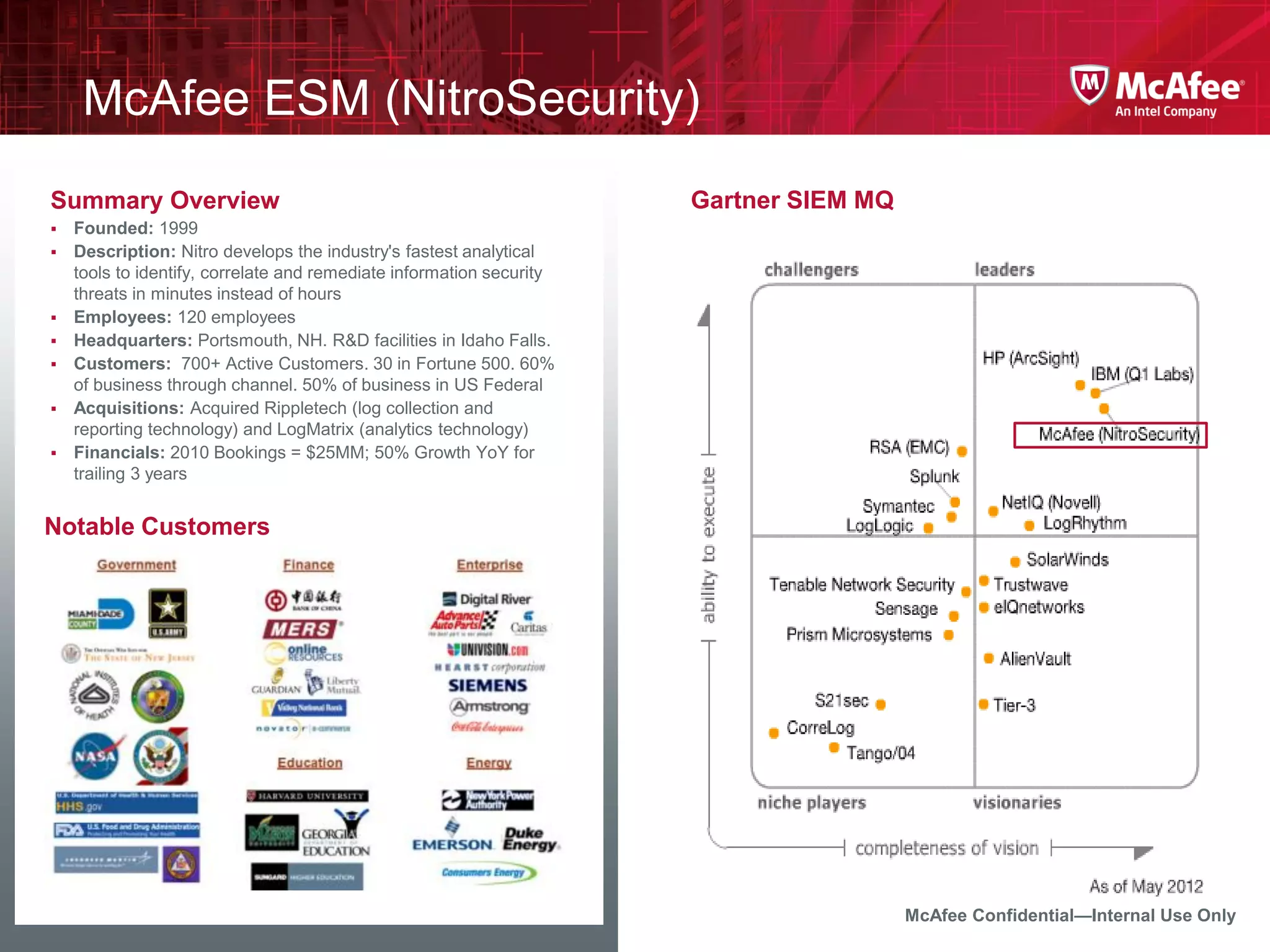
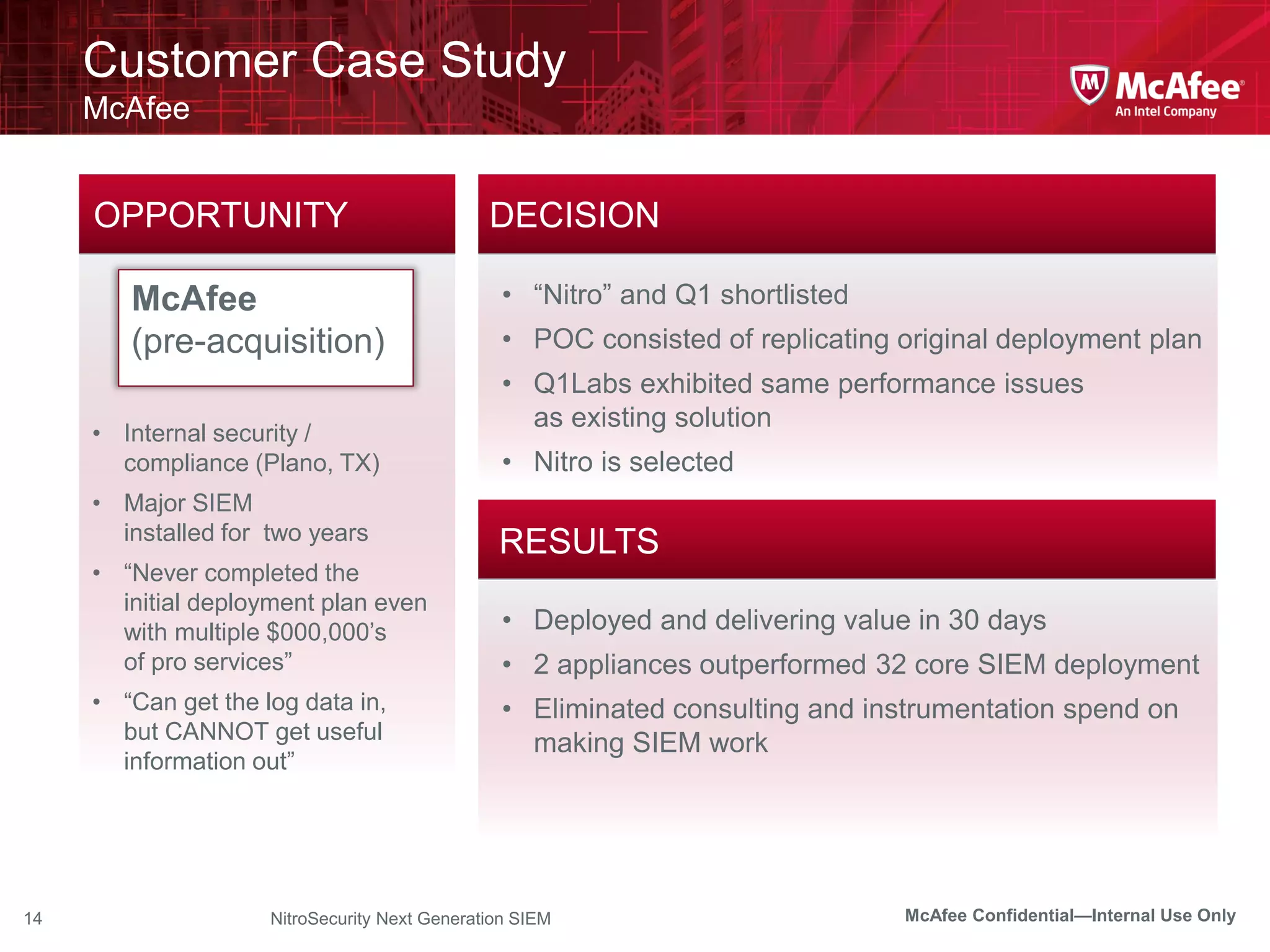
The document discusses McAfee's Enterprise Security Manager (ESM) as a next-generation Security Information and Event Management (SIEM) solution, focusing on transforming vast amounts of security data into actionable intelligence. It highlights the limitations of legacy SIEM systems and showcases ESM's rapid response capabilities, compliance monitoring, and advanced correlation engine features. The summary includes an overview of McAfee's market position, technological innovations, and customer success stories, emphasizing its effectiveness in detecting and remediating security threats efficiently.