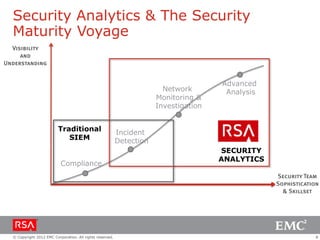
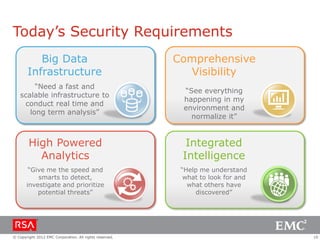
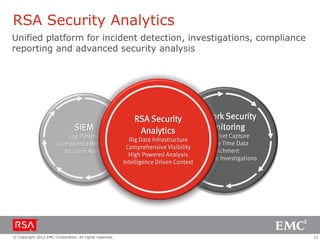
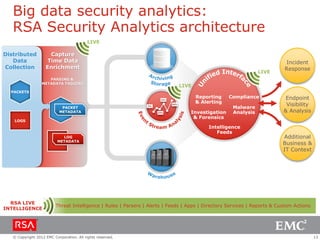
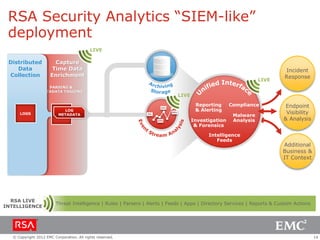
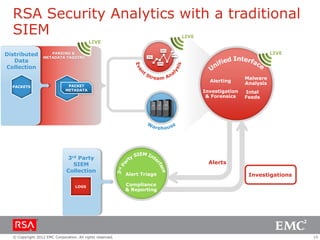
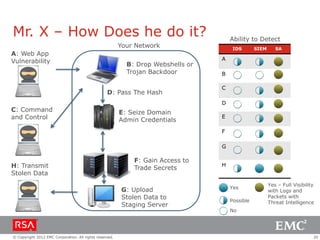
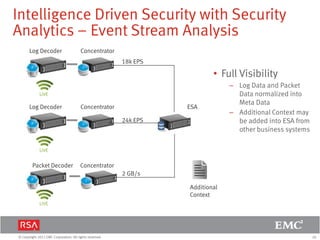
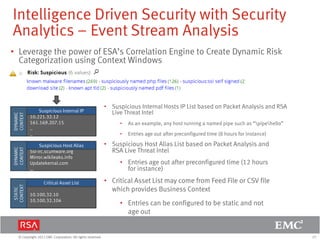
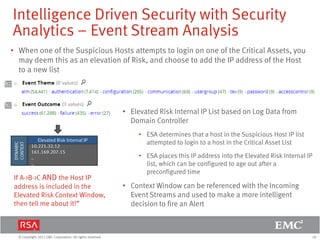
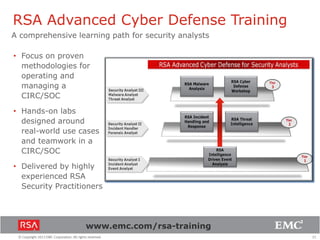
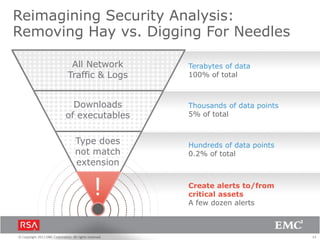
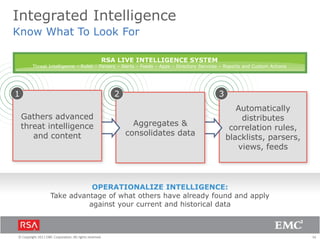
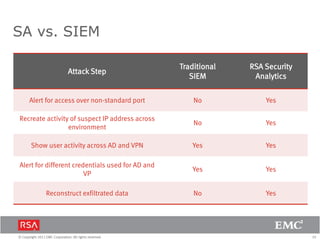
The document discusses the evolution of security information and event management (SIEM) systems towards intelligence-driven security analytics, highlighting the limitations of traditional SIEM in addressing complex threats. It introduces RSA Security Analytics as a unified platform that enhances incident detection and investigation capabilities, leveraging big data and real-time analysis to improve security measures. The shift from compliance-focused systems to proactive, intelligence-driven security is emphasized as essential for modern threat detection and response.