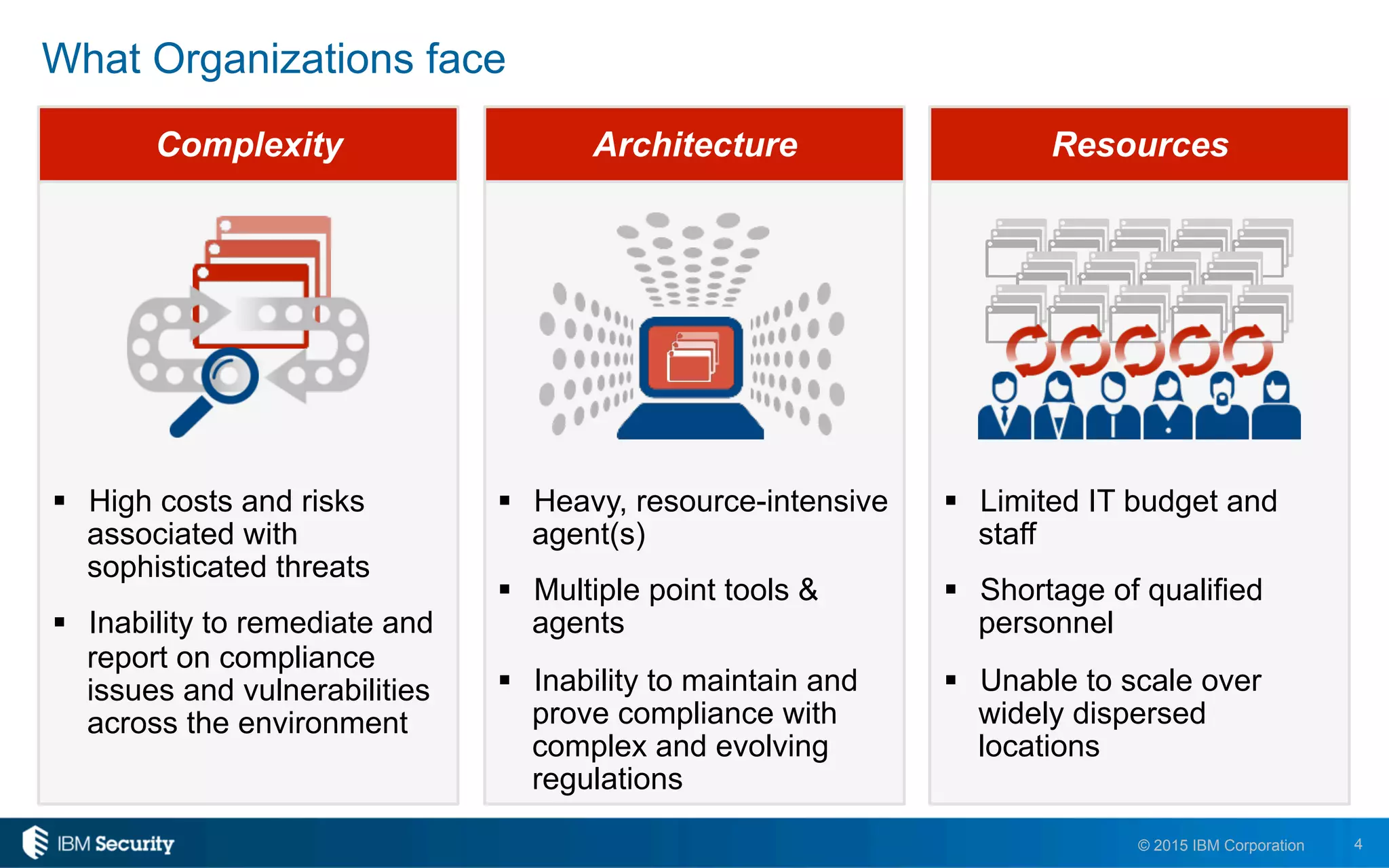
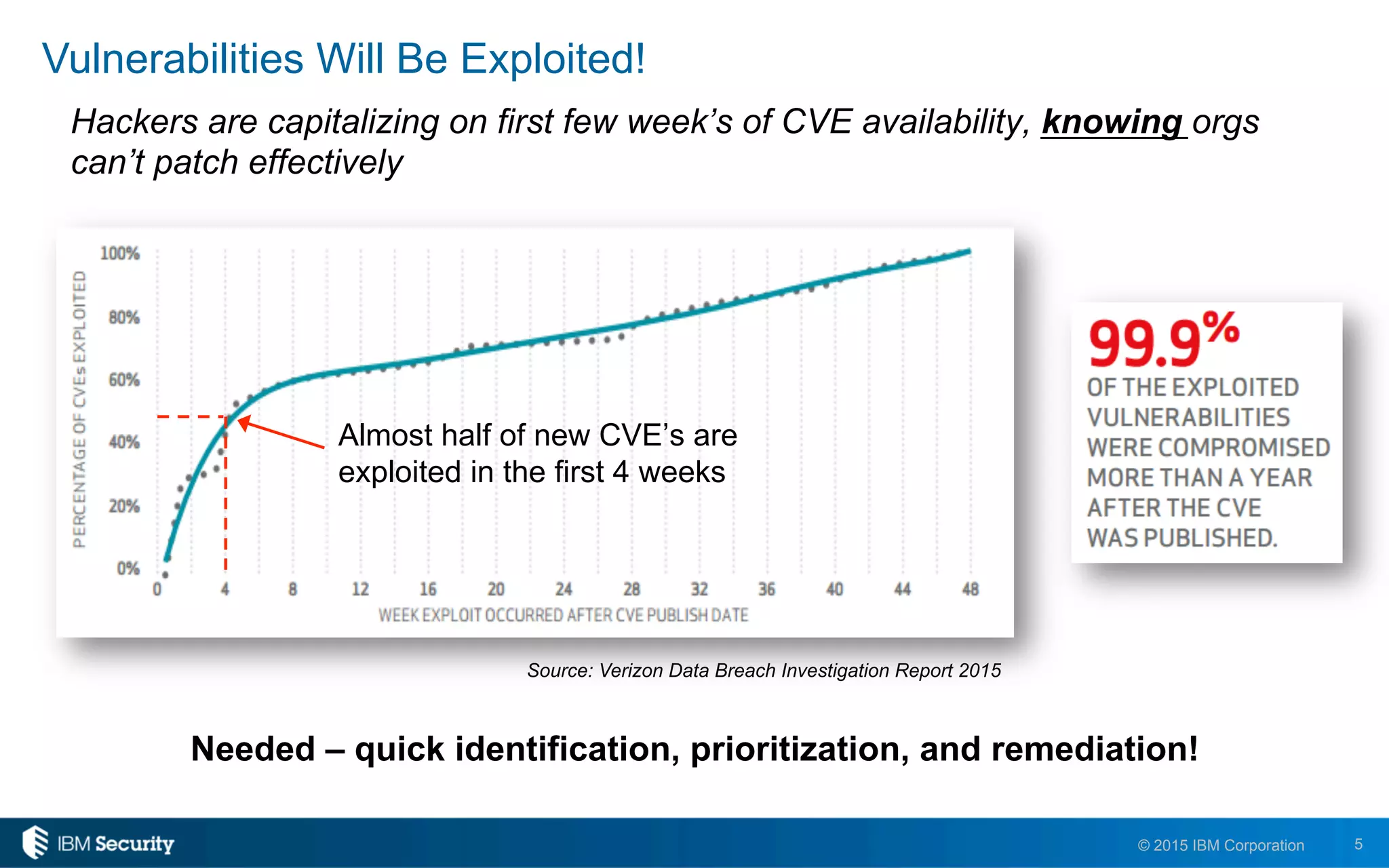
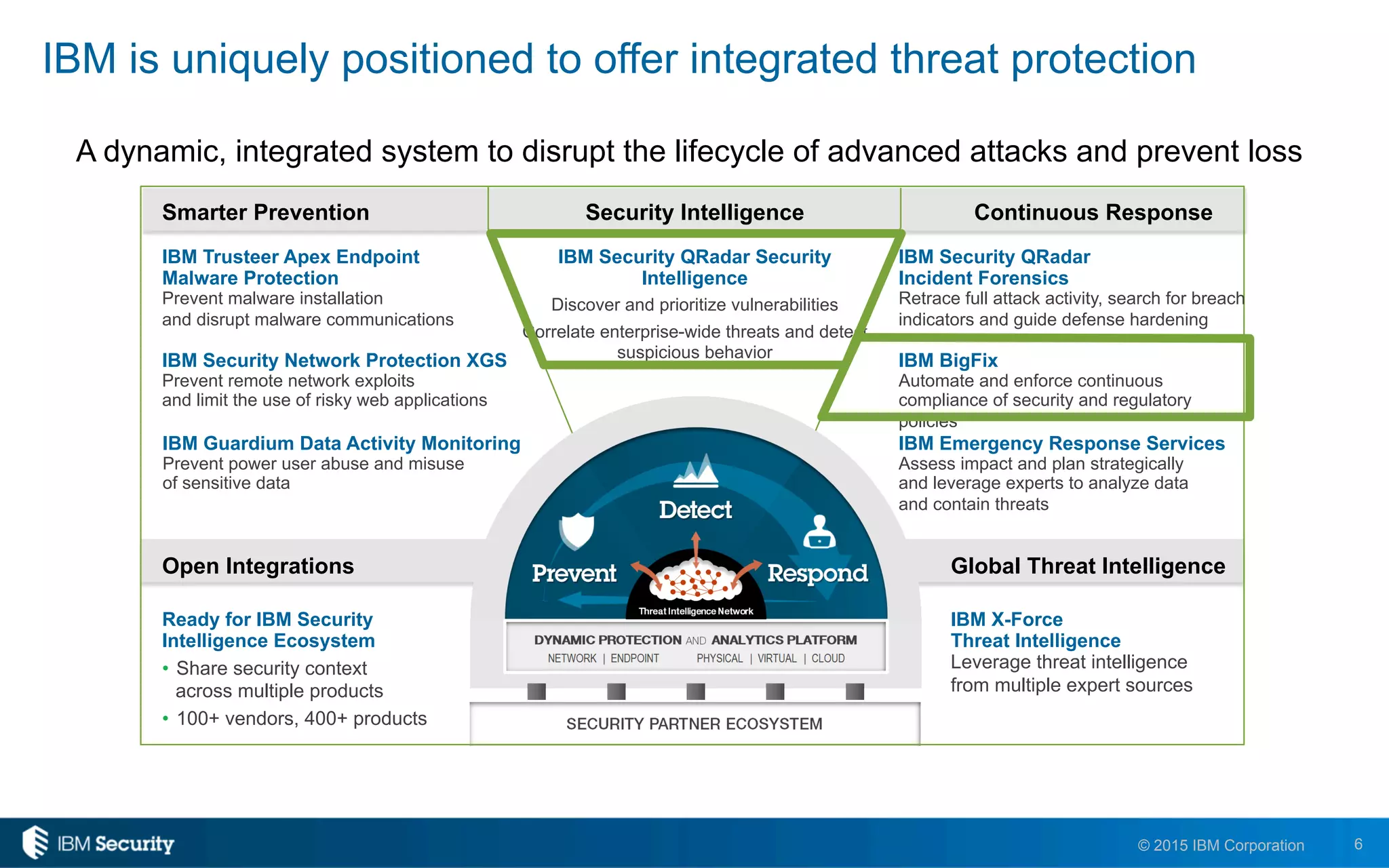
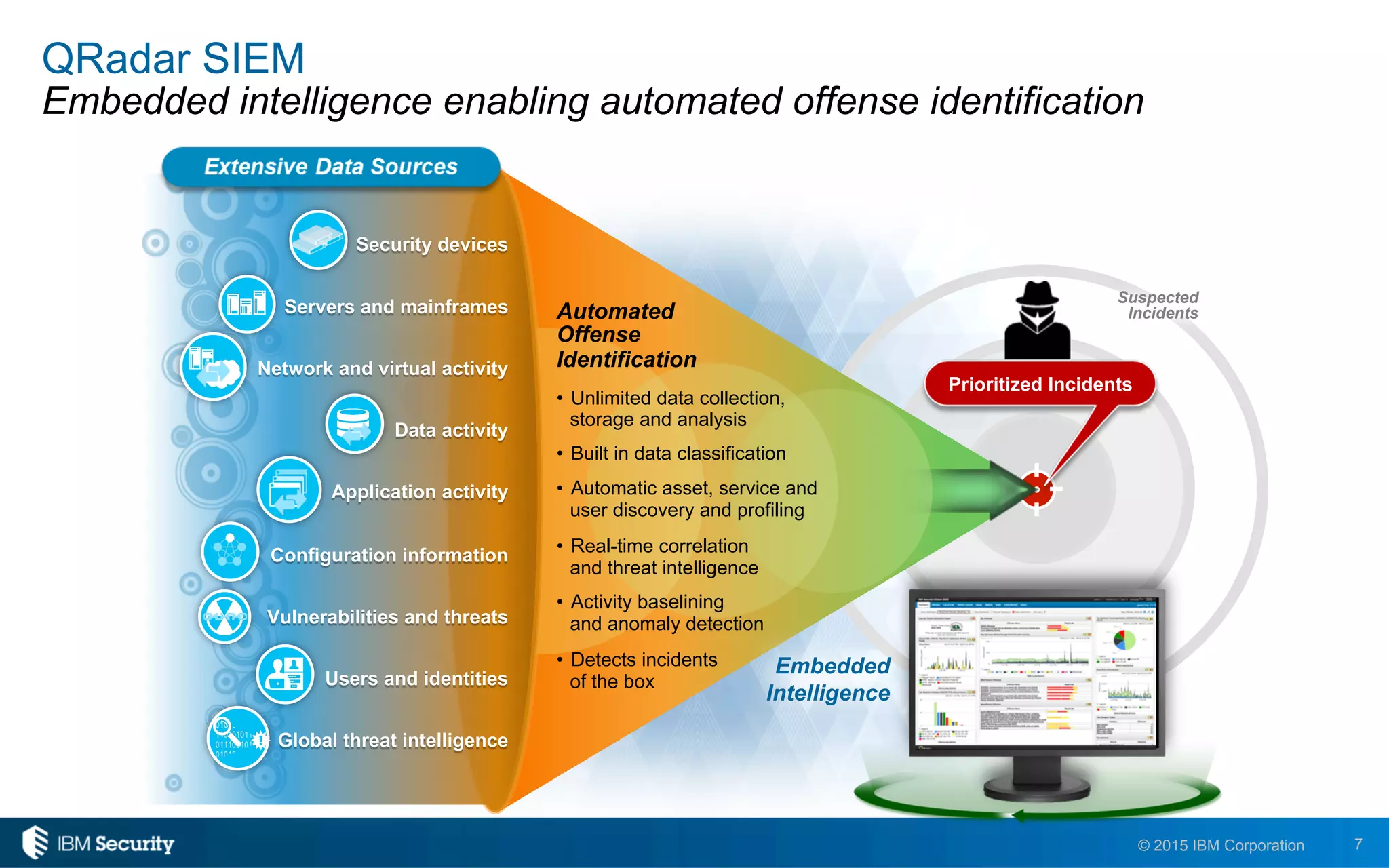
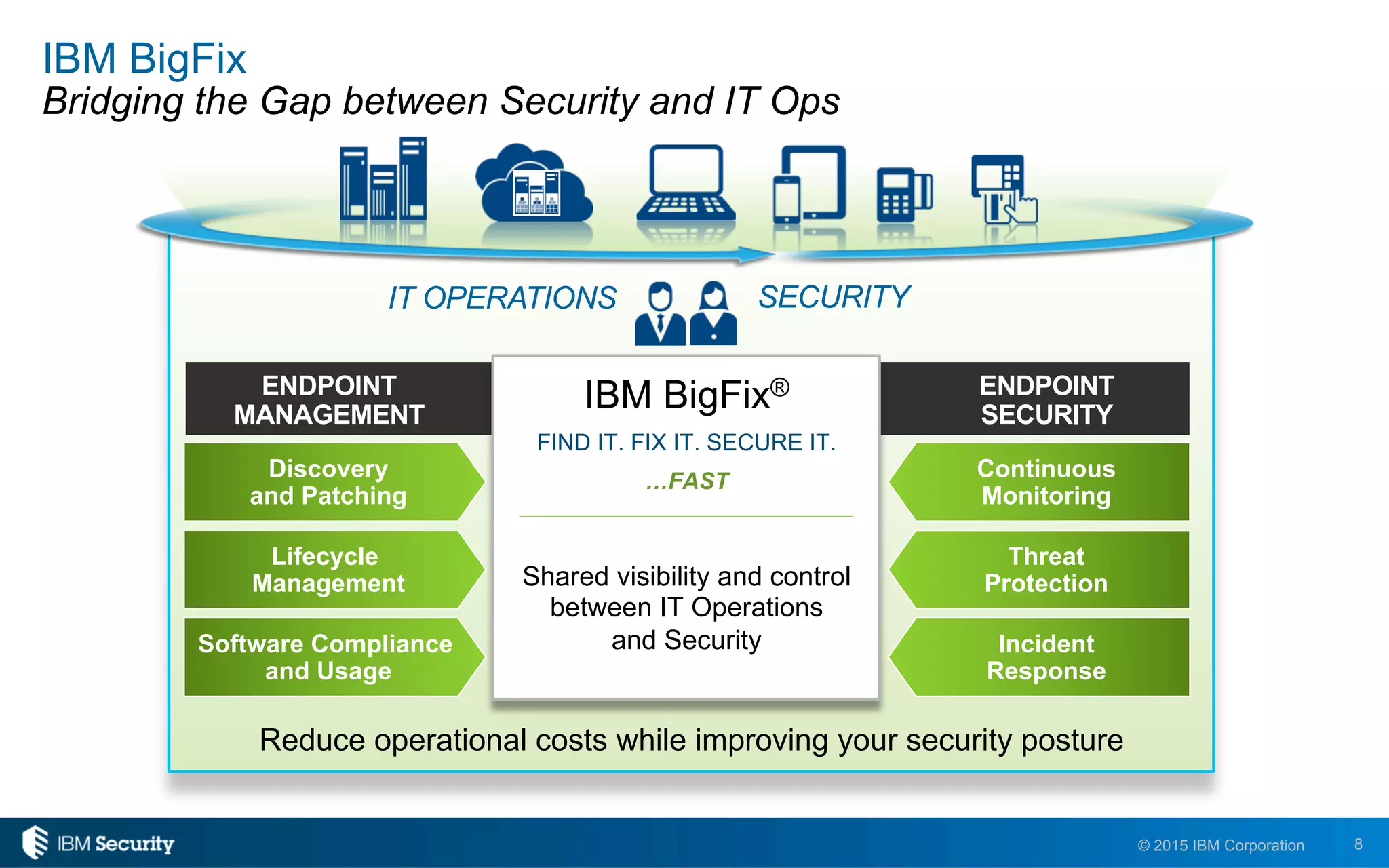
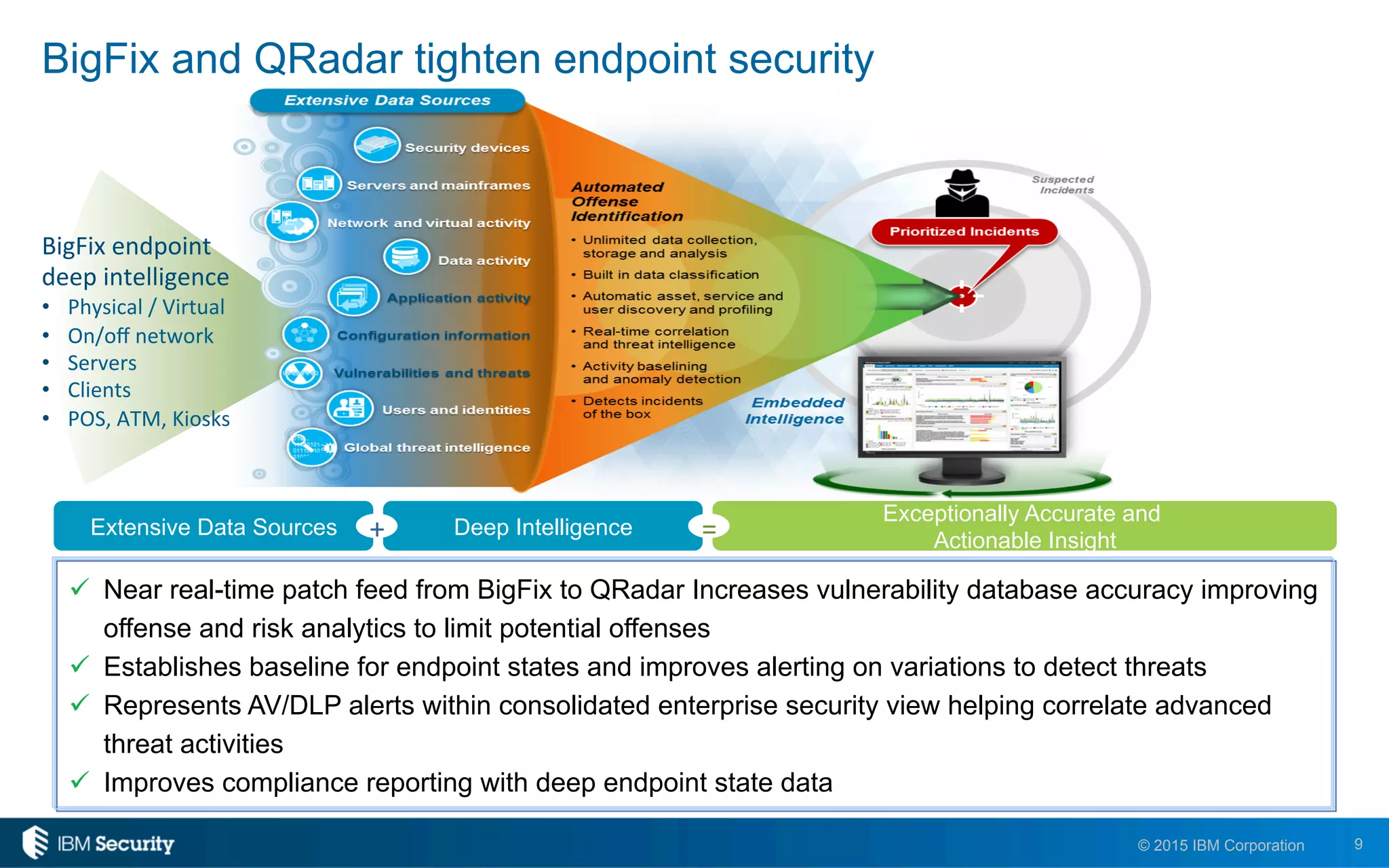
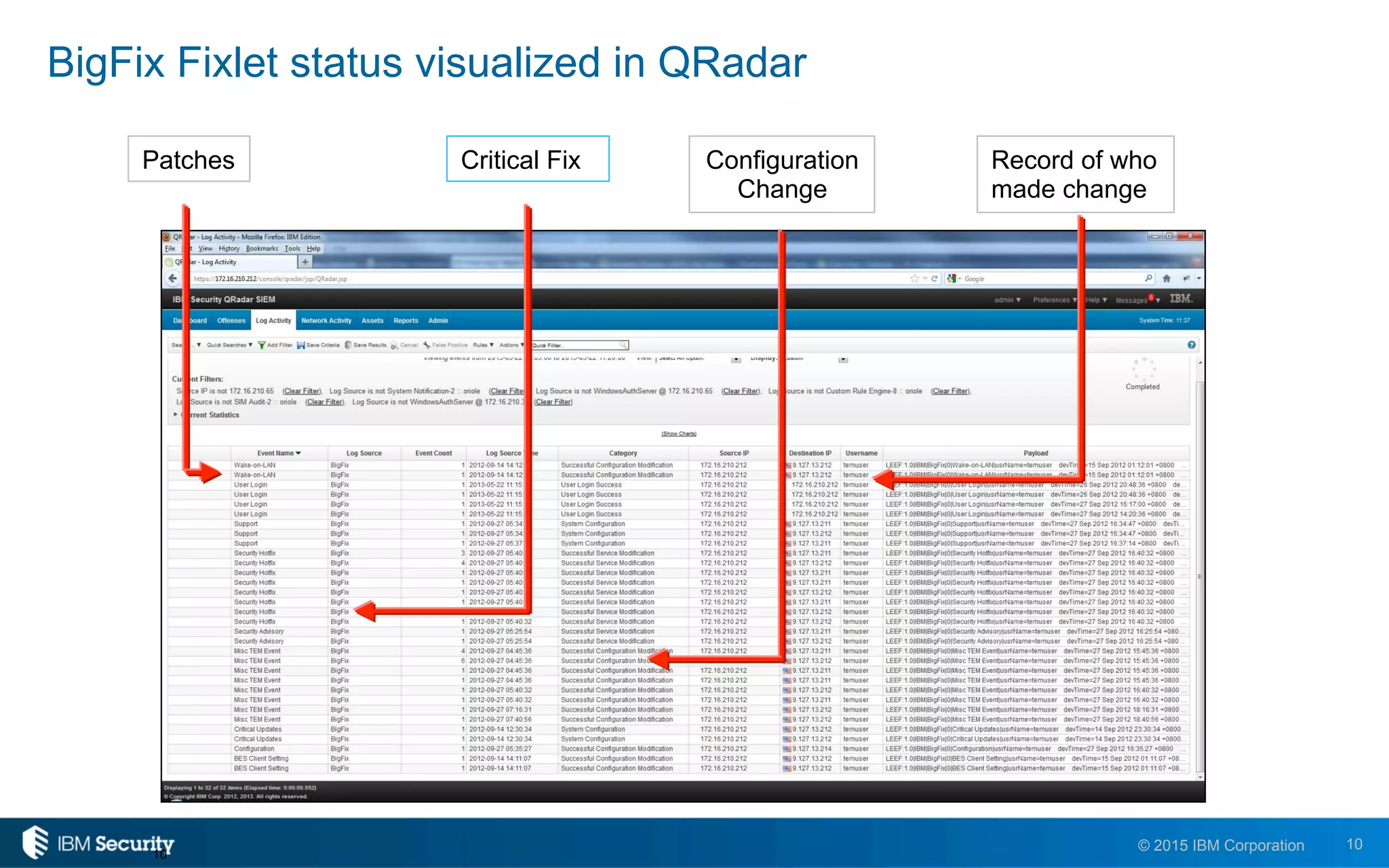
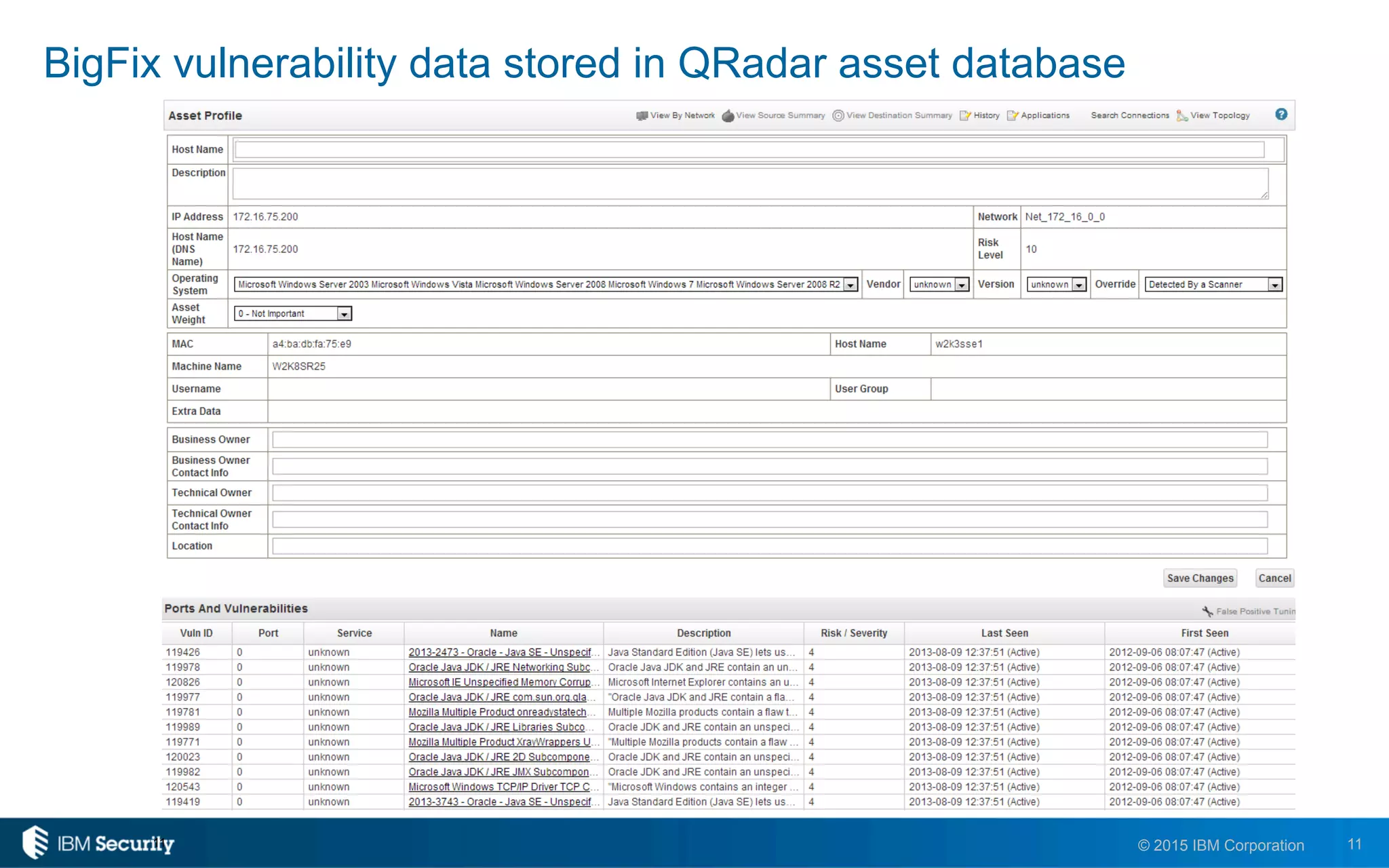
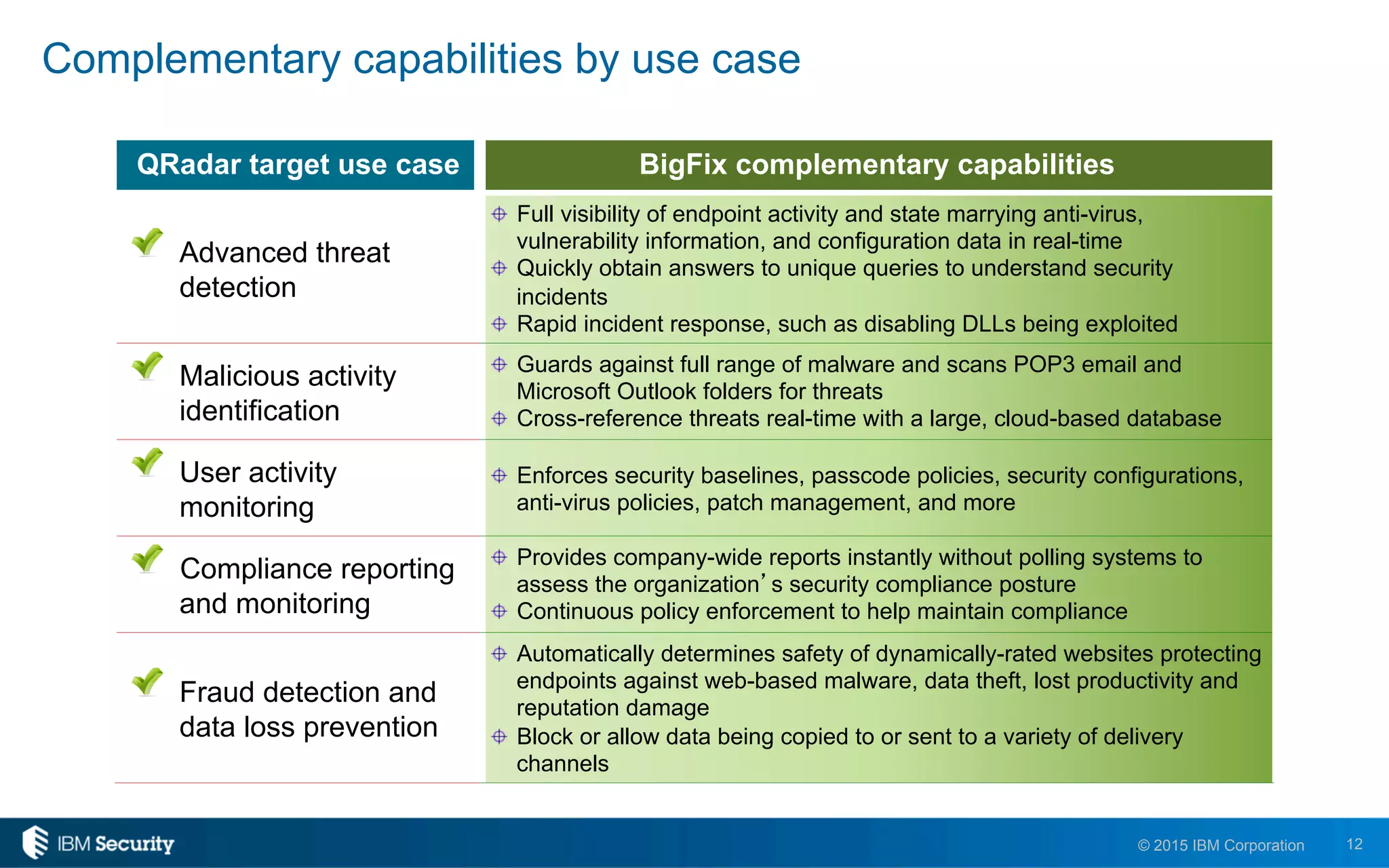
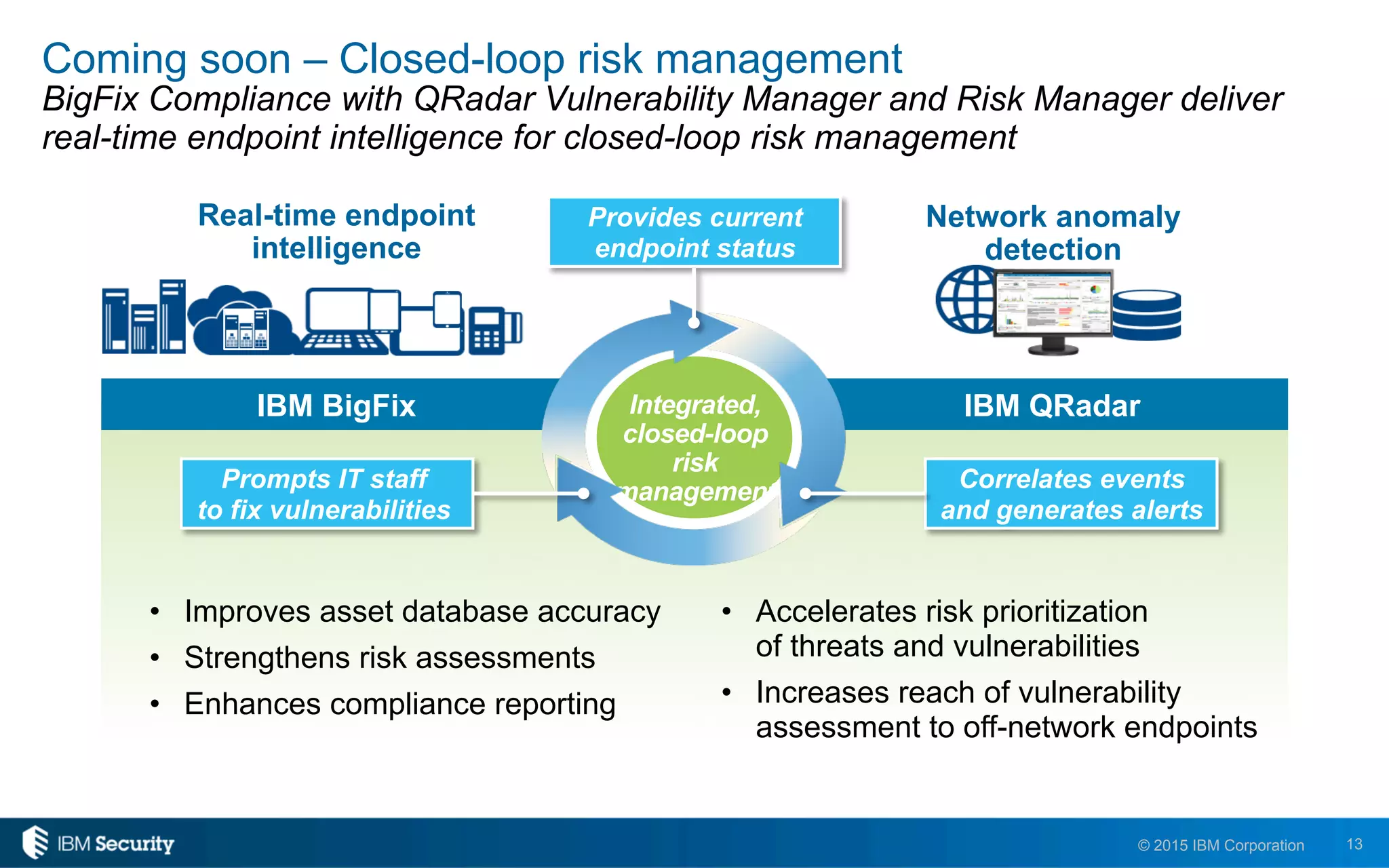
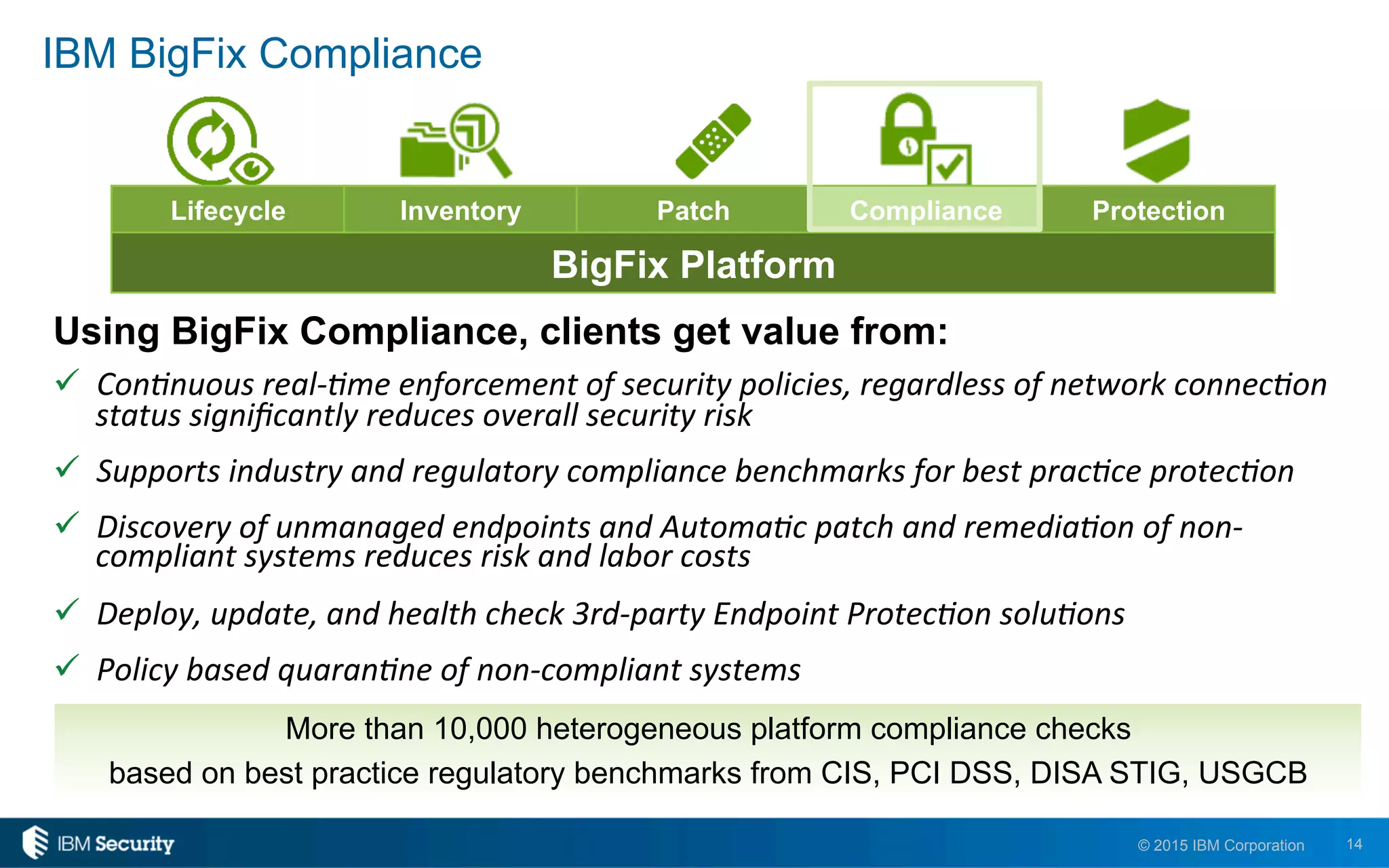
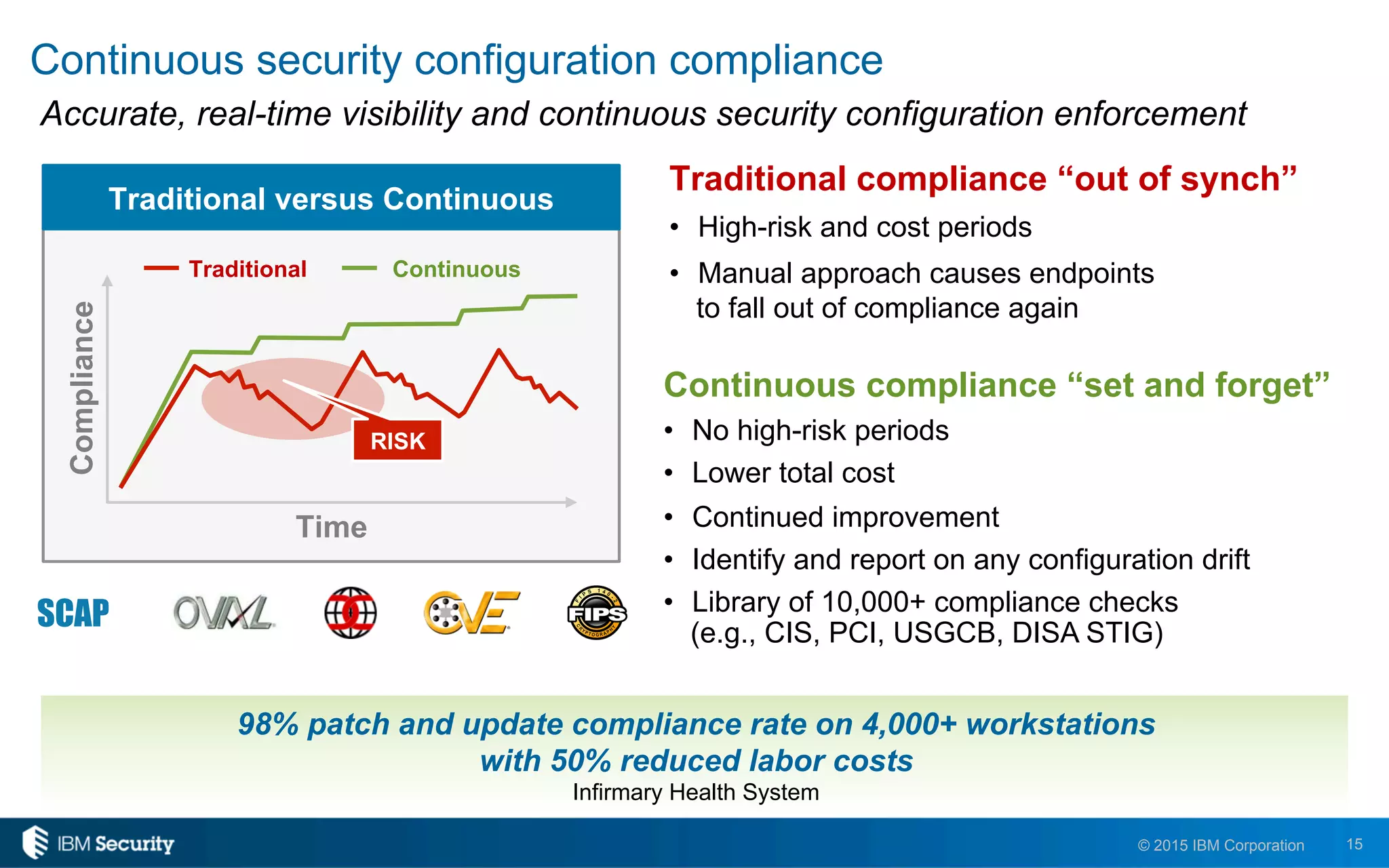
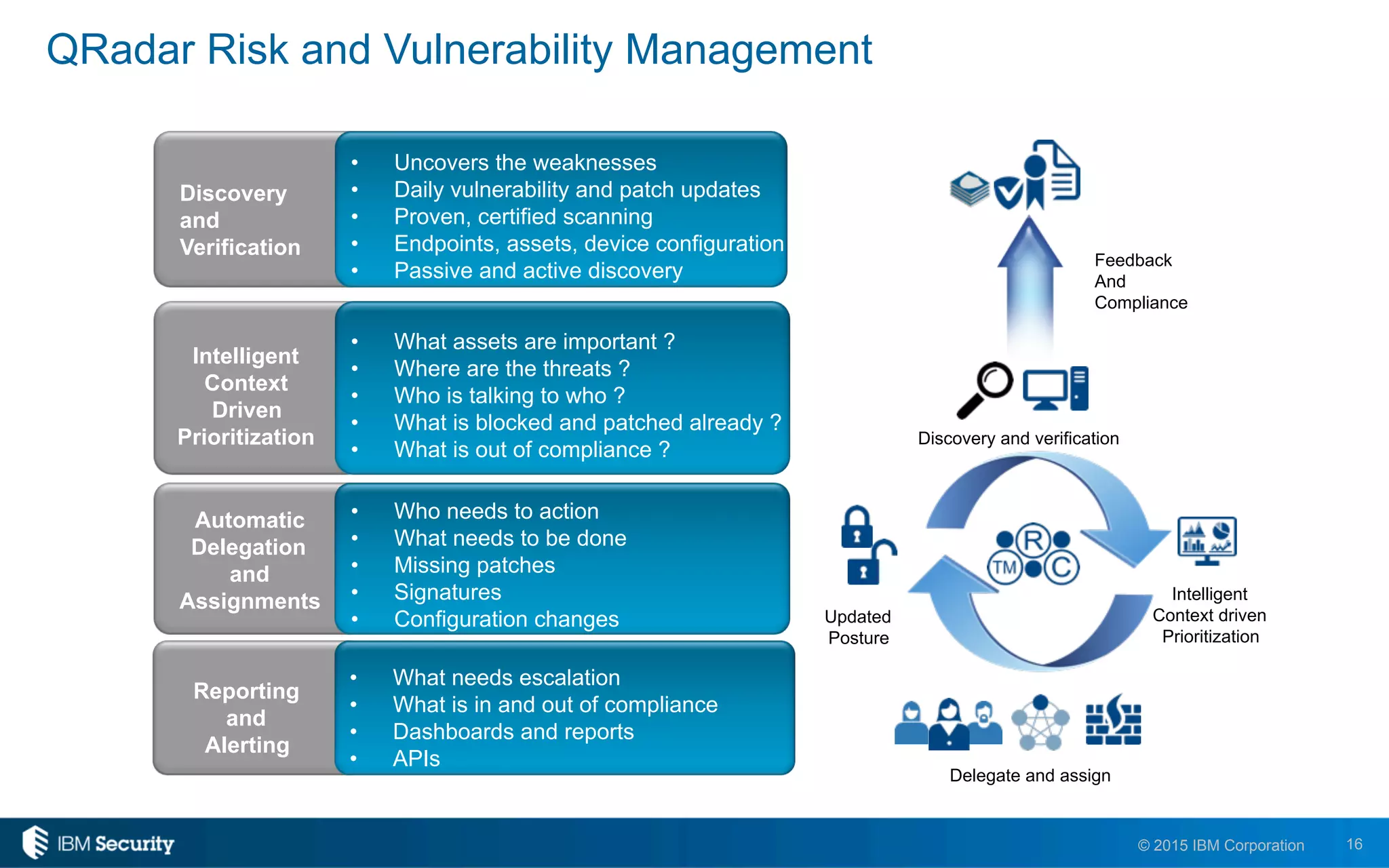
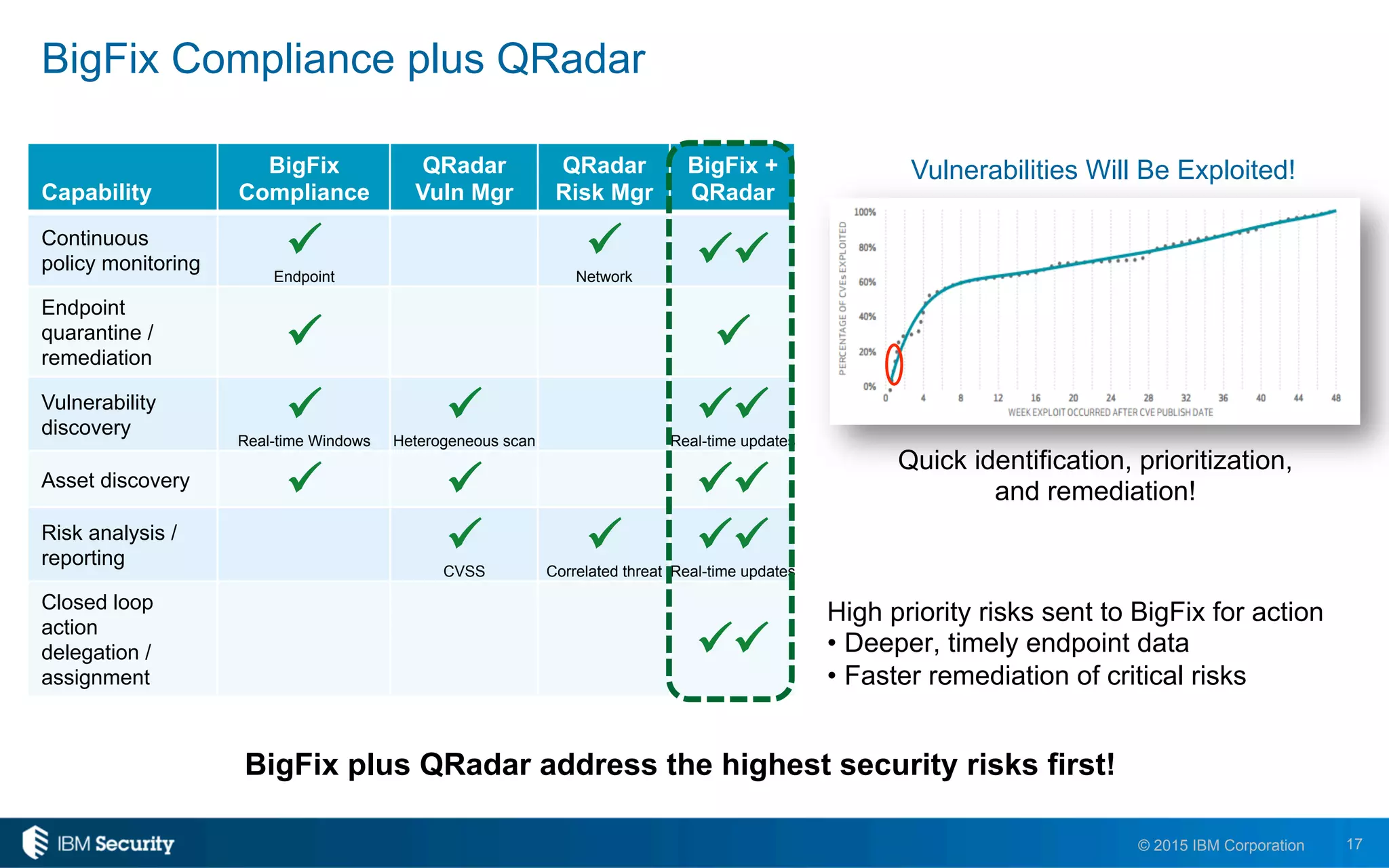
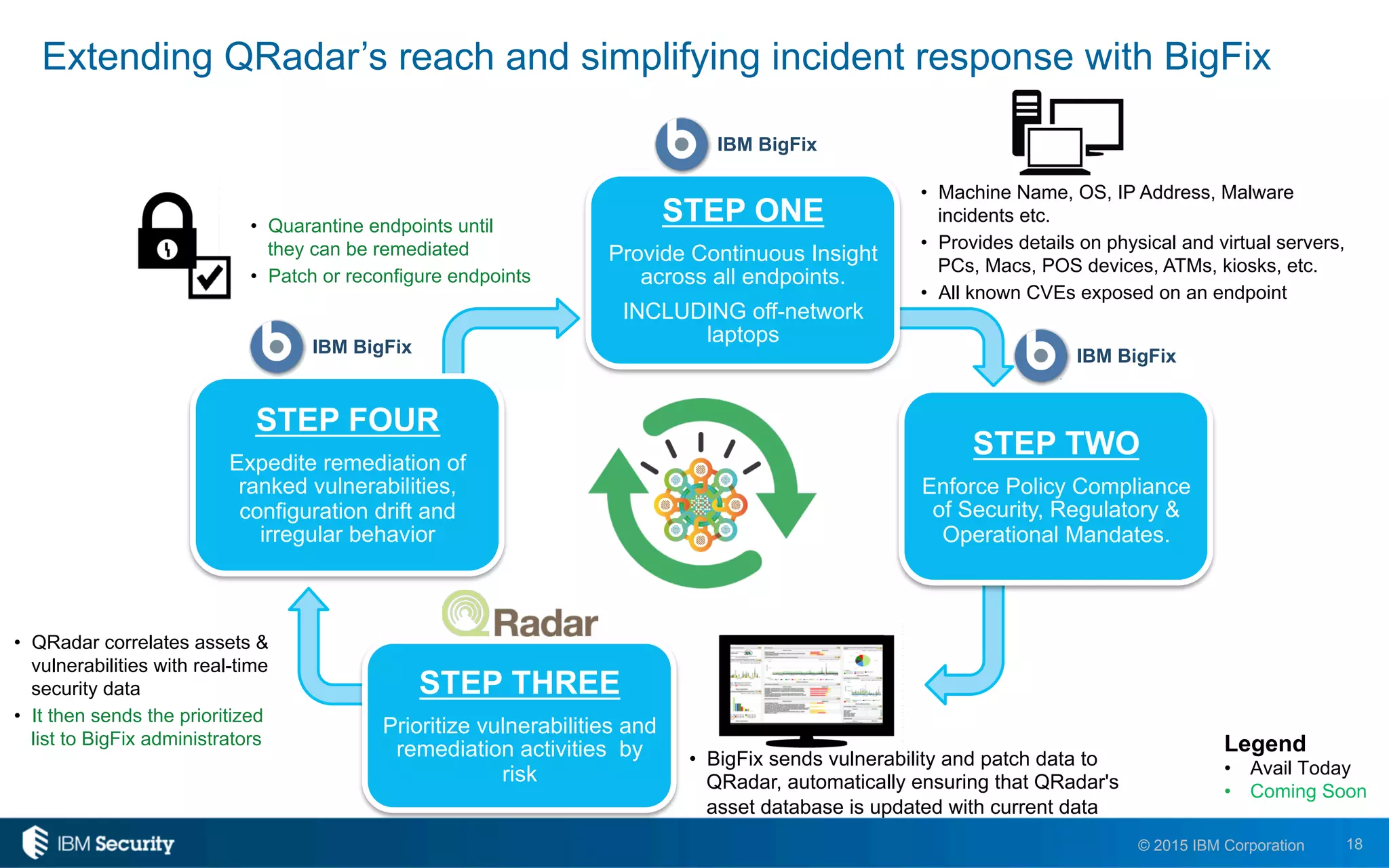
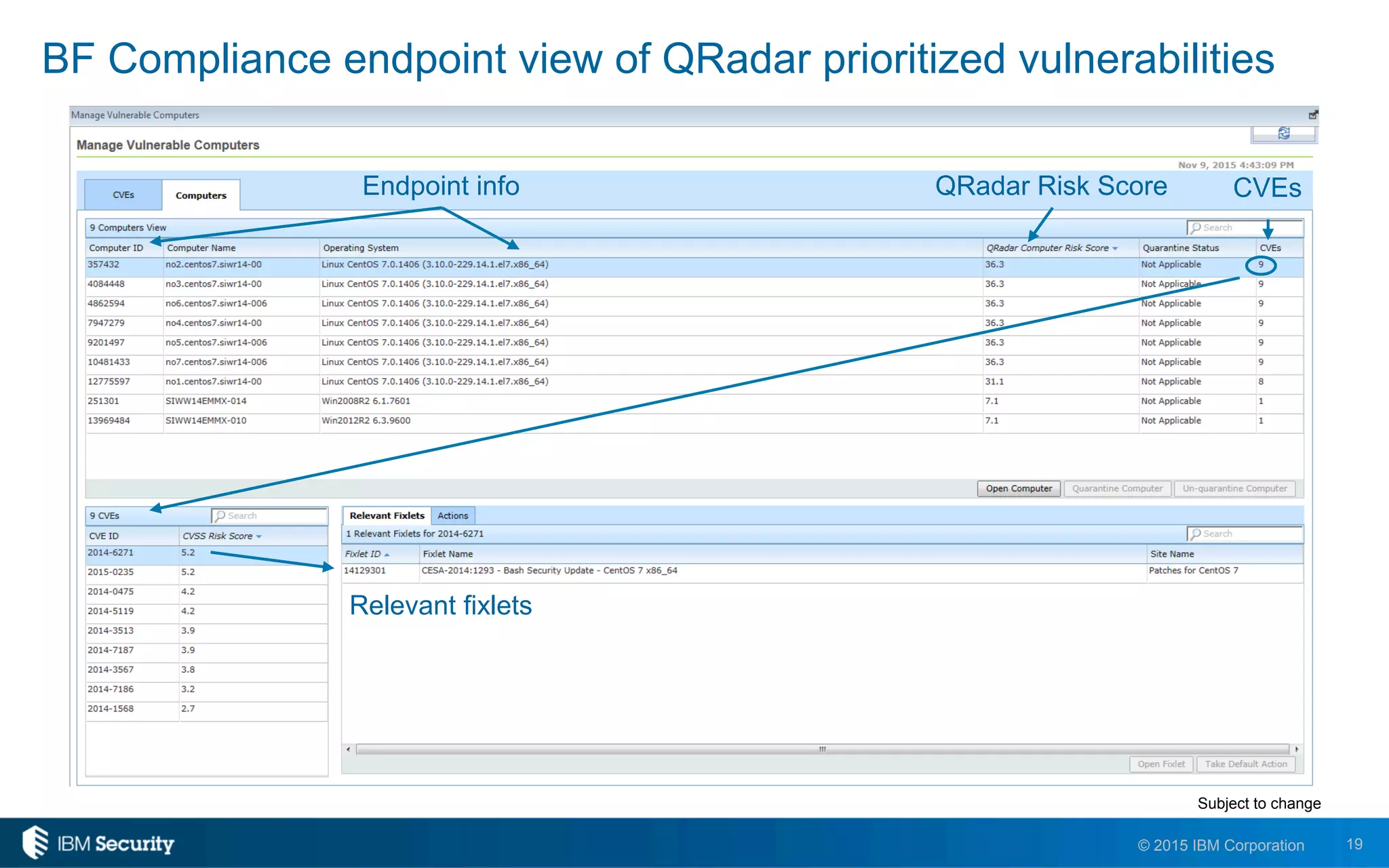
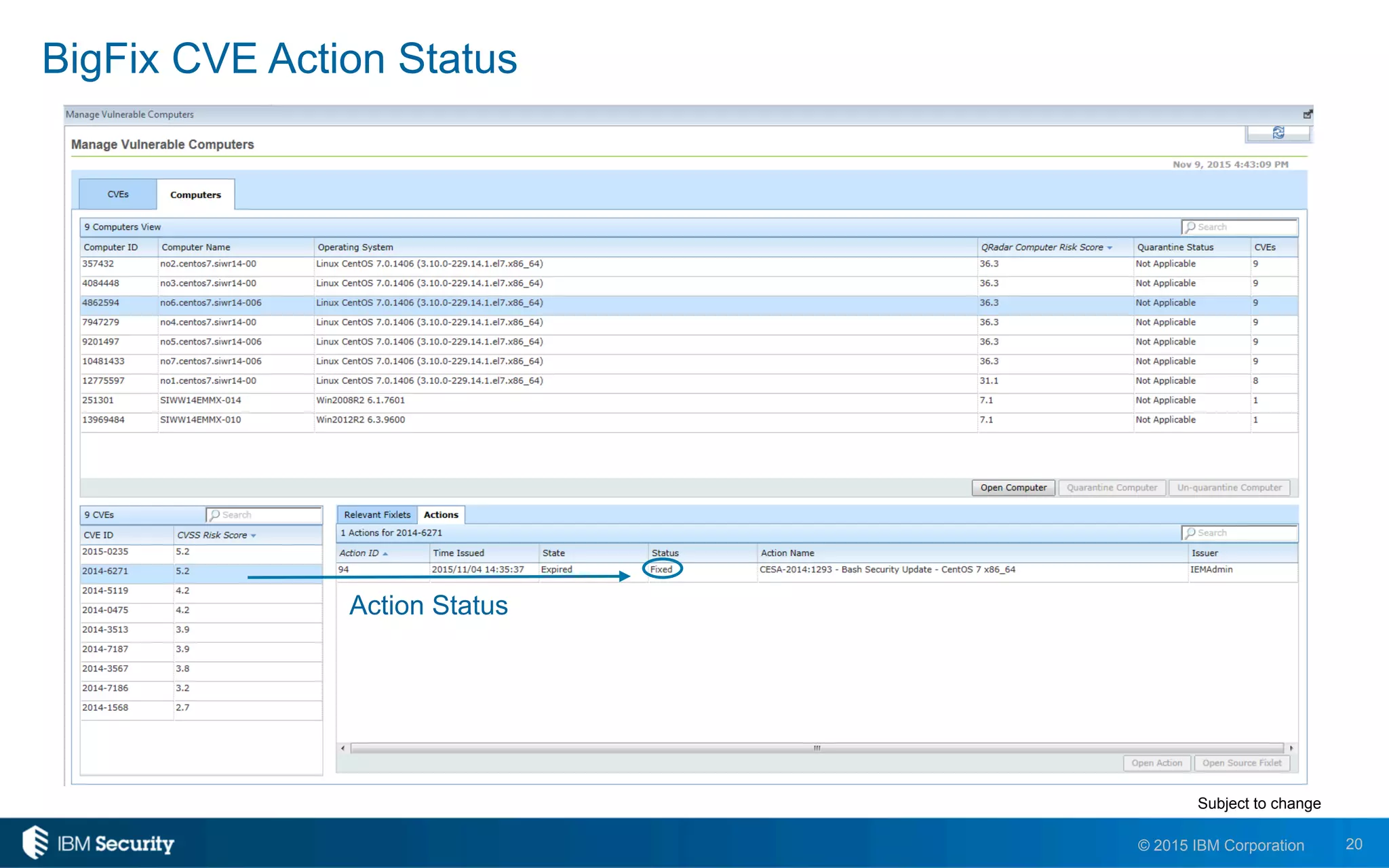
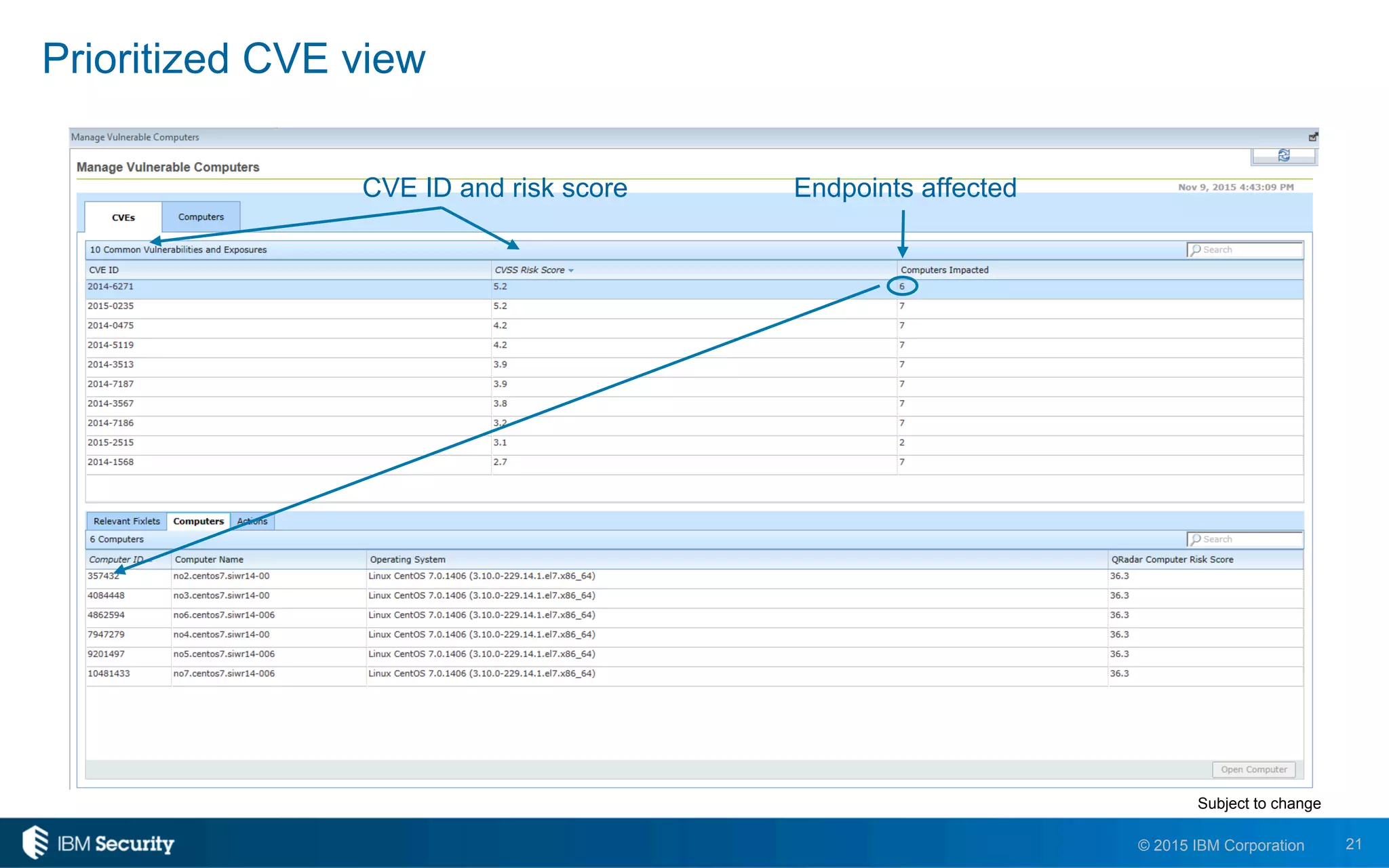
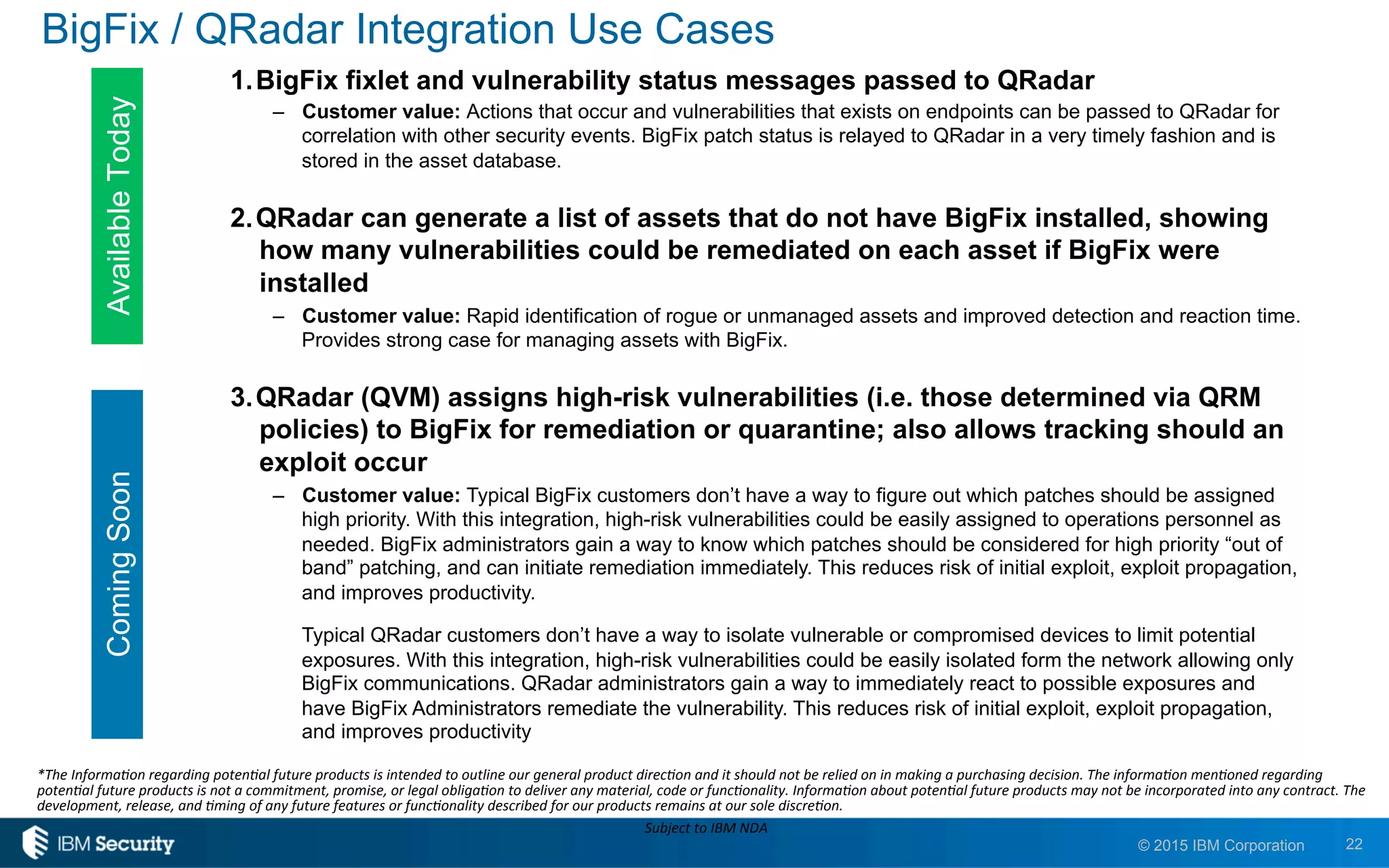
The document discusses IBM's BigFix and QRadar solutions for enhancing endpoint security and managing cyber threats effectively. It highlights the challenges organizations face in cybersecurity, such as compliance issues and limited resources, and presents an integrated approach to threat management through automation and real-time intelligence. The collaboration between BigFix and QRadar is positioned as a way to streamline vulnerability management and improve compliance reporting while reducing operational risks.