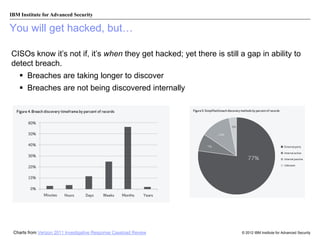
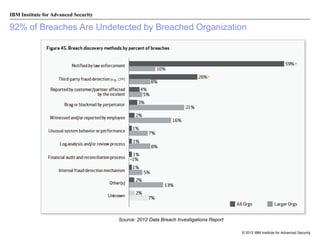
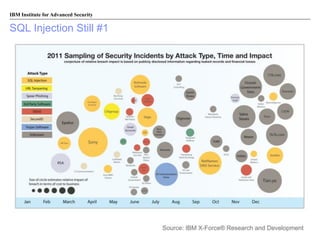
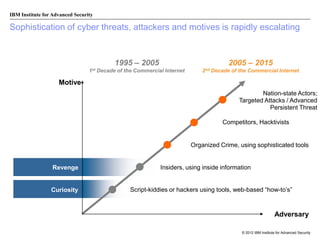
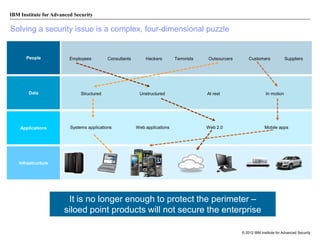
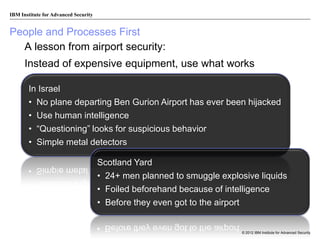
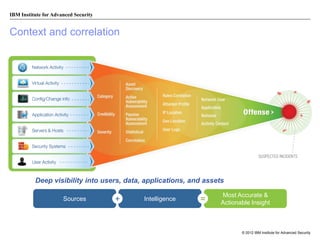
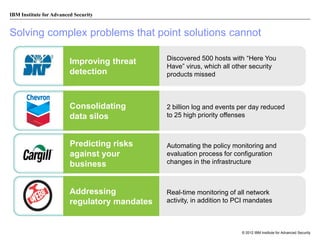
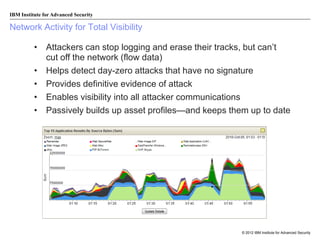
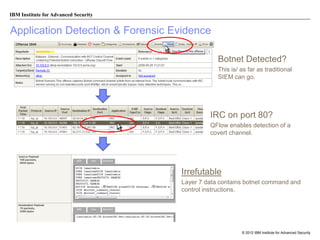
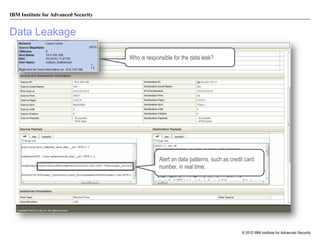
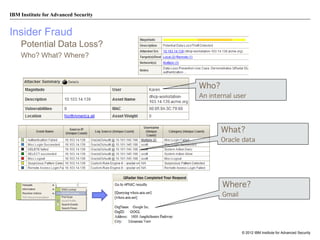
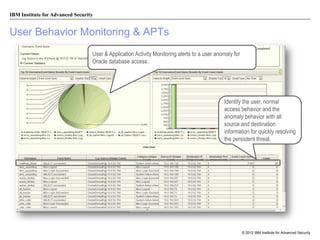
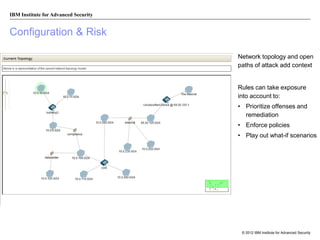
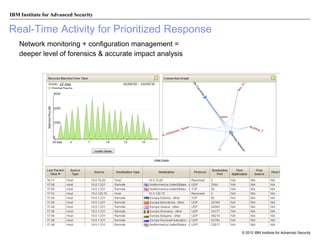
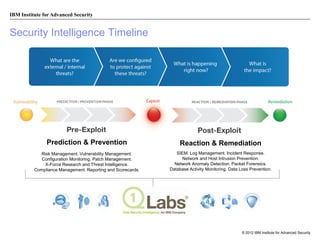
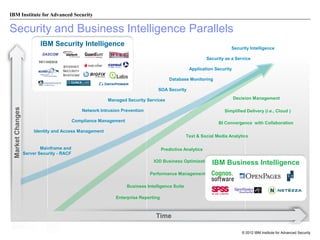
The document discusses the importance of security intelligence for enterprises, highlighting that breaches are often undetected and that organizations need better detection capabilities. It emphasizes that a comprehensive approach involving technology, processes, and human intelligence is essential for identifying and mitigating security threats. The need for real-time analytics and context in monitoring user and system behavior is also addressed to improve breach detection and response.