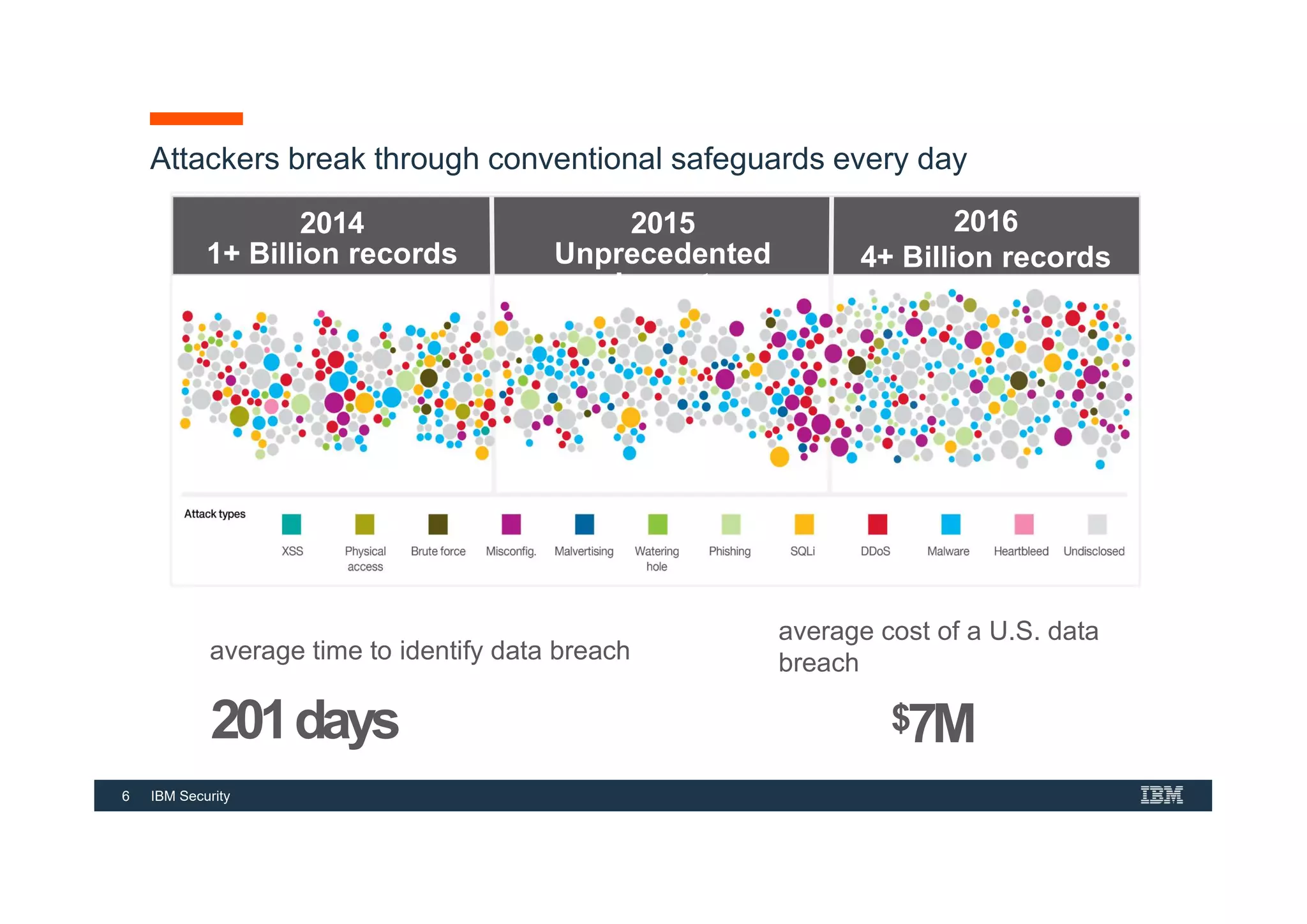
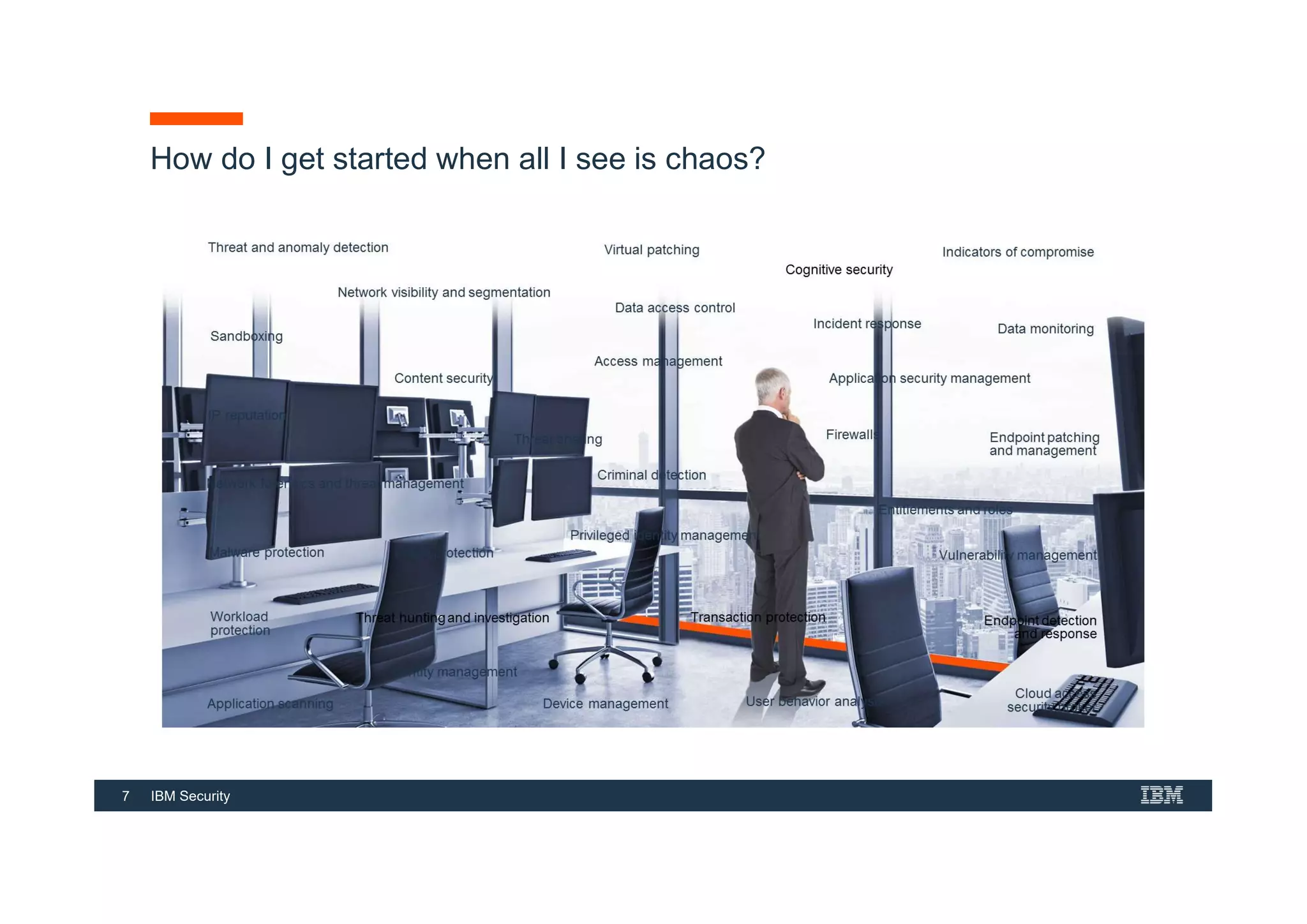
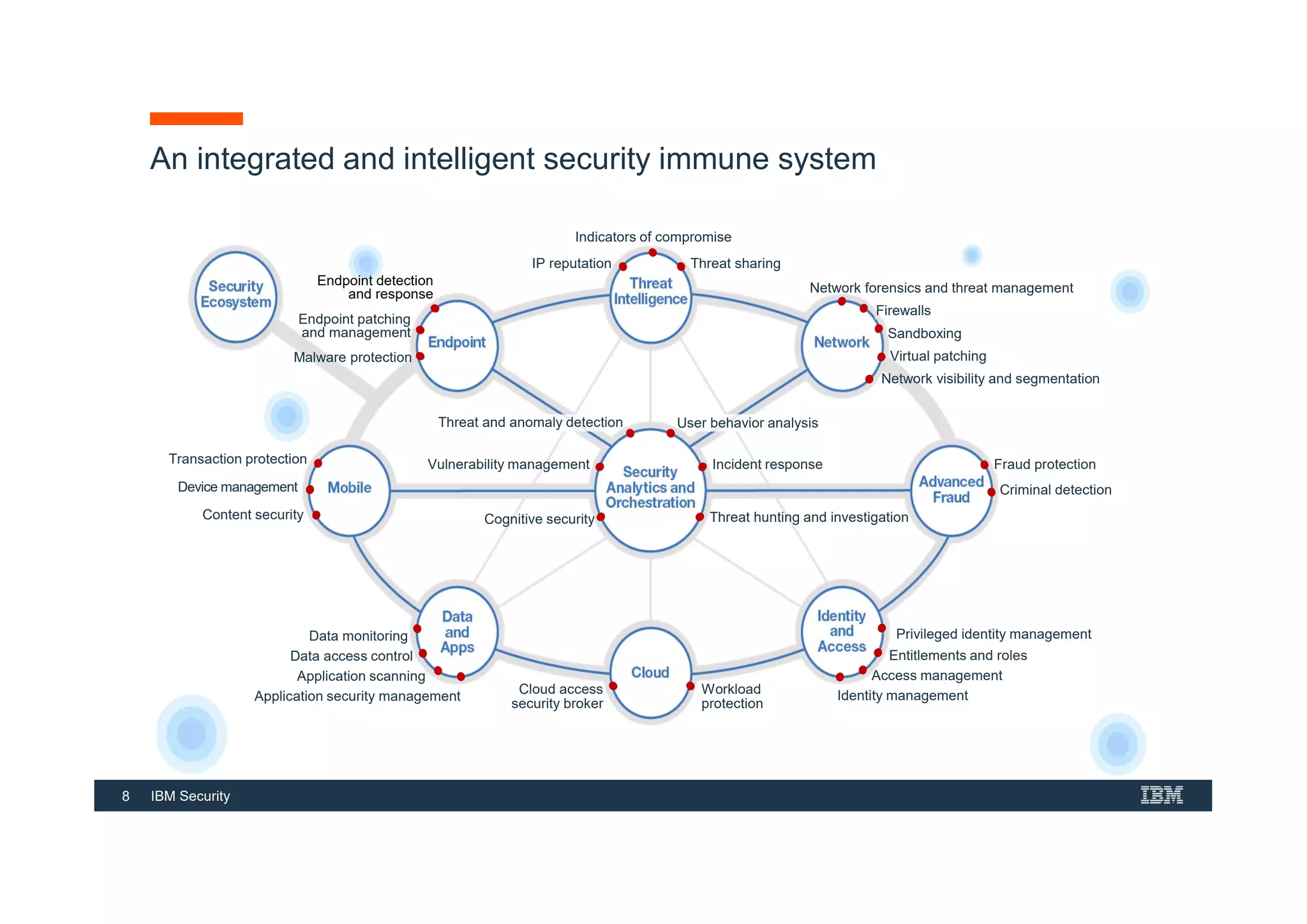
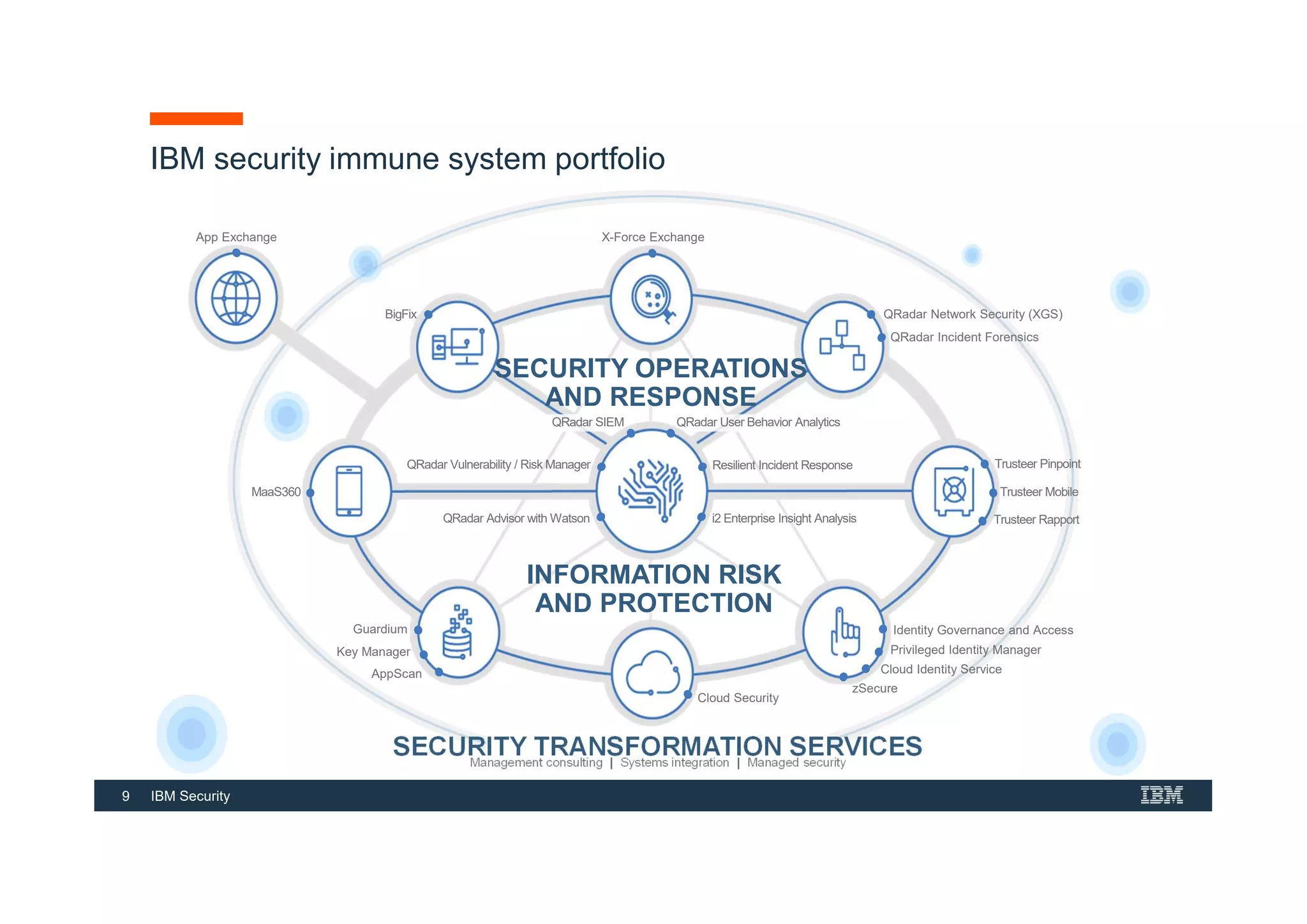
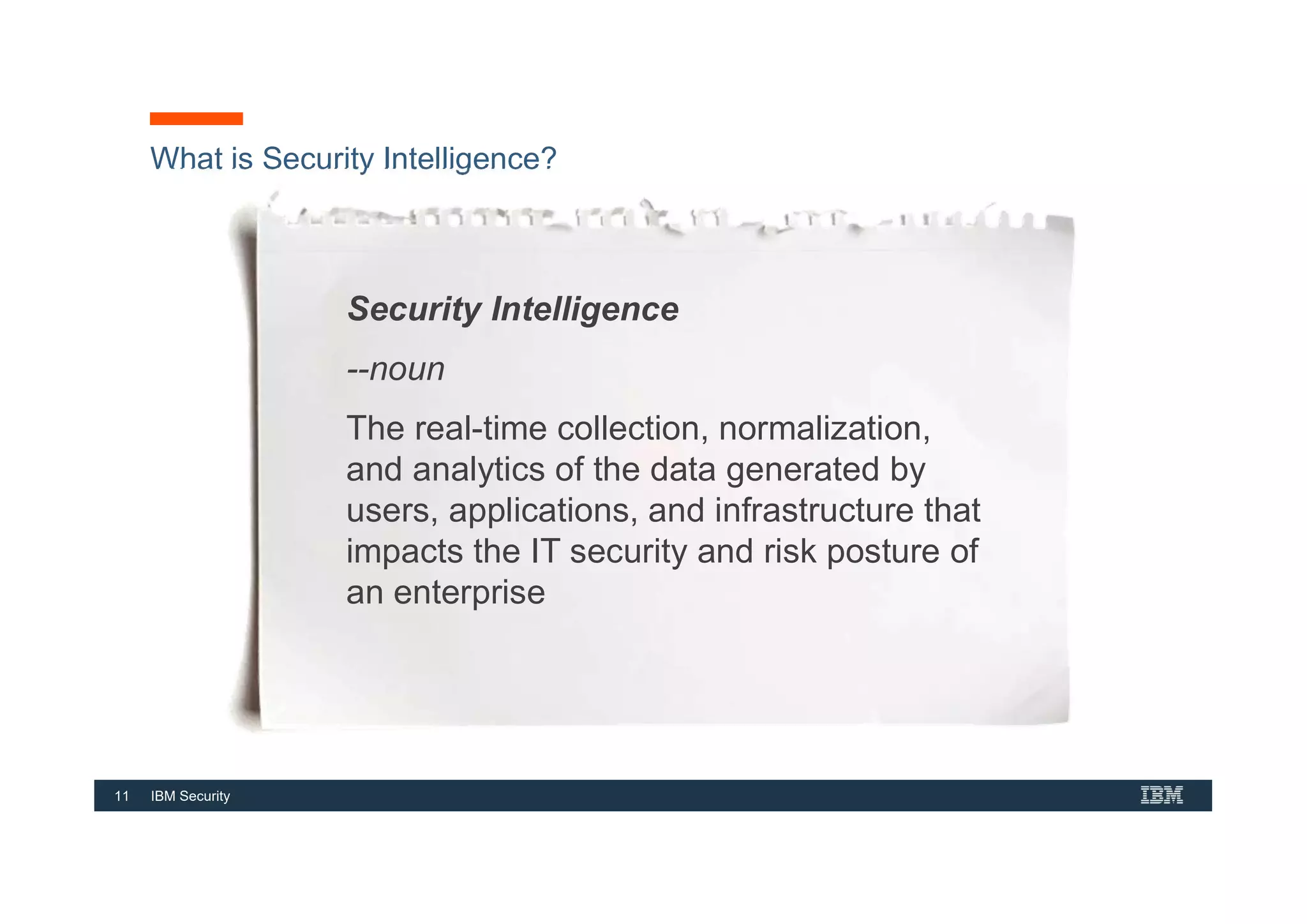
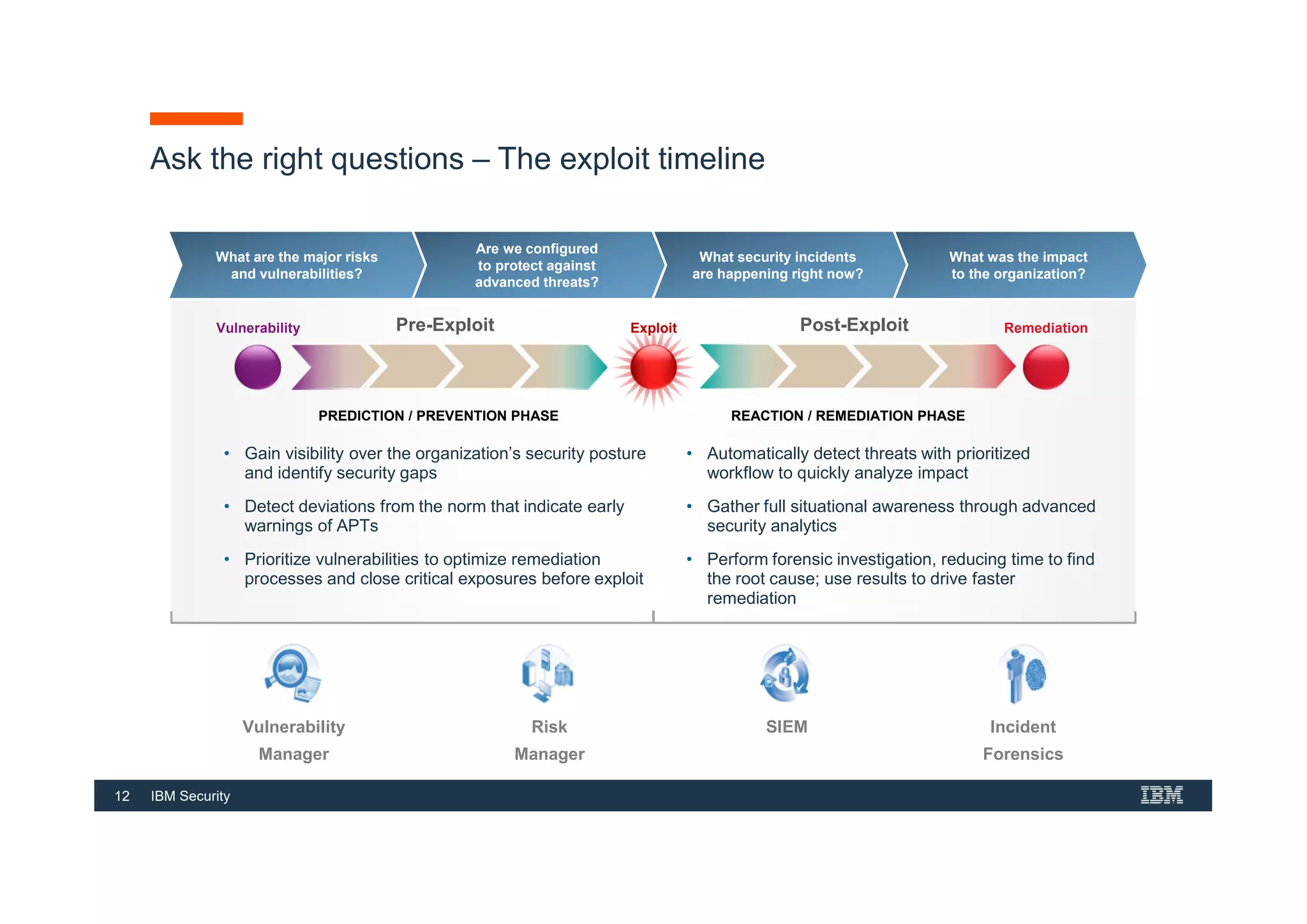
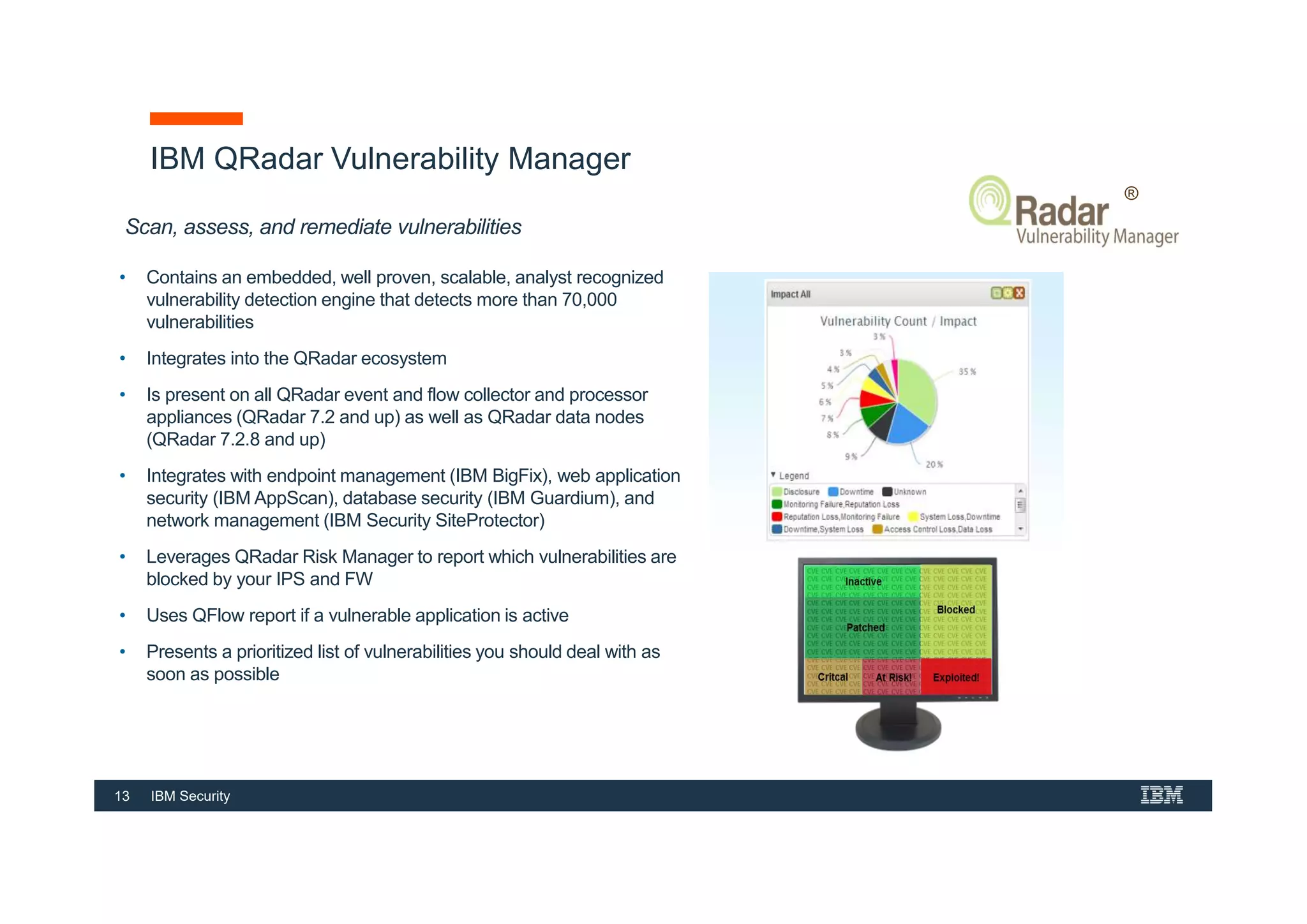
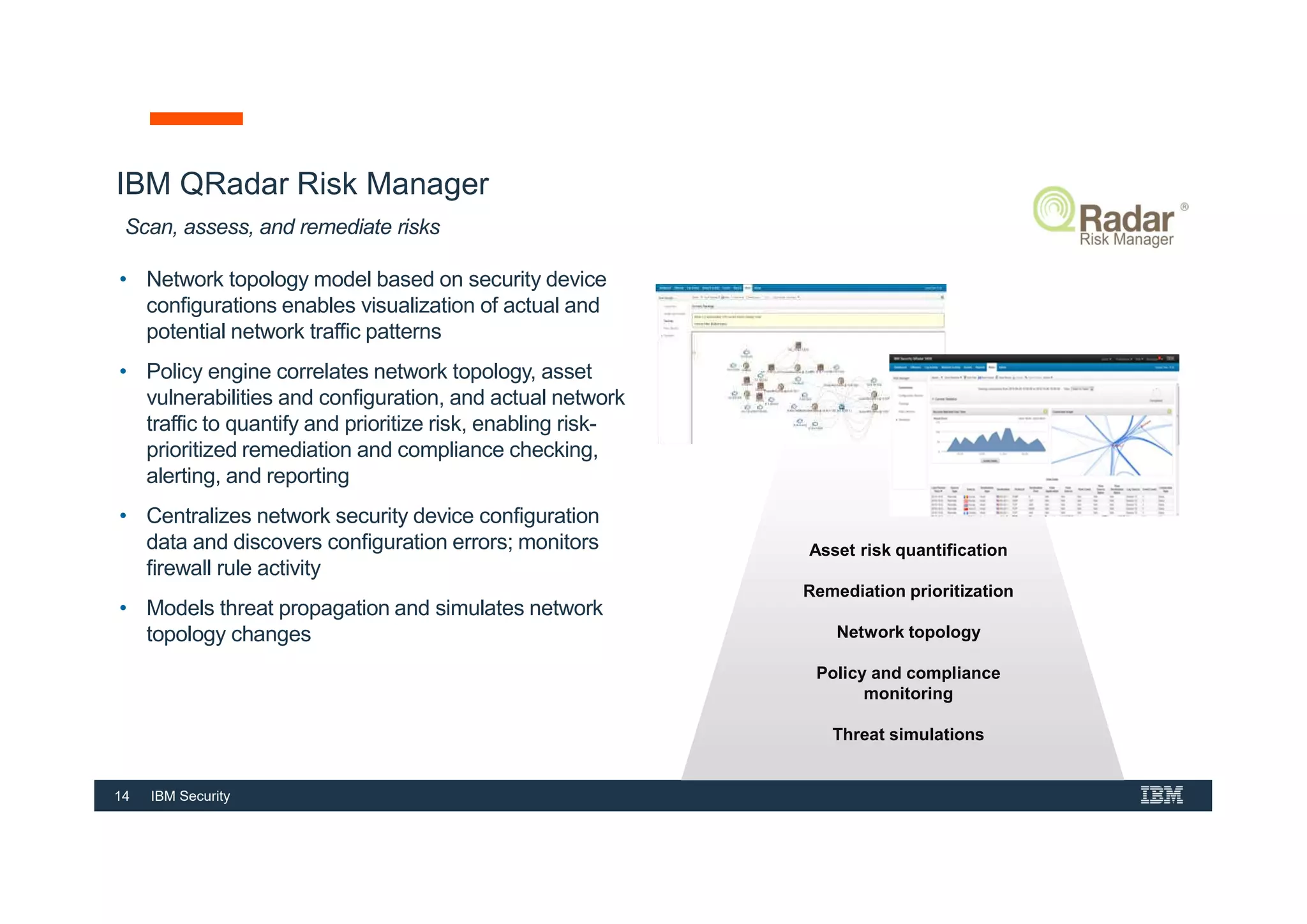
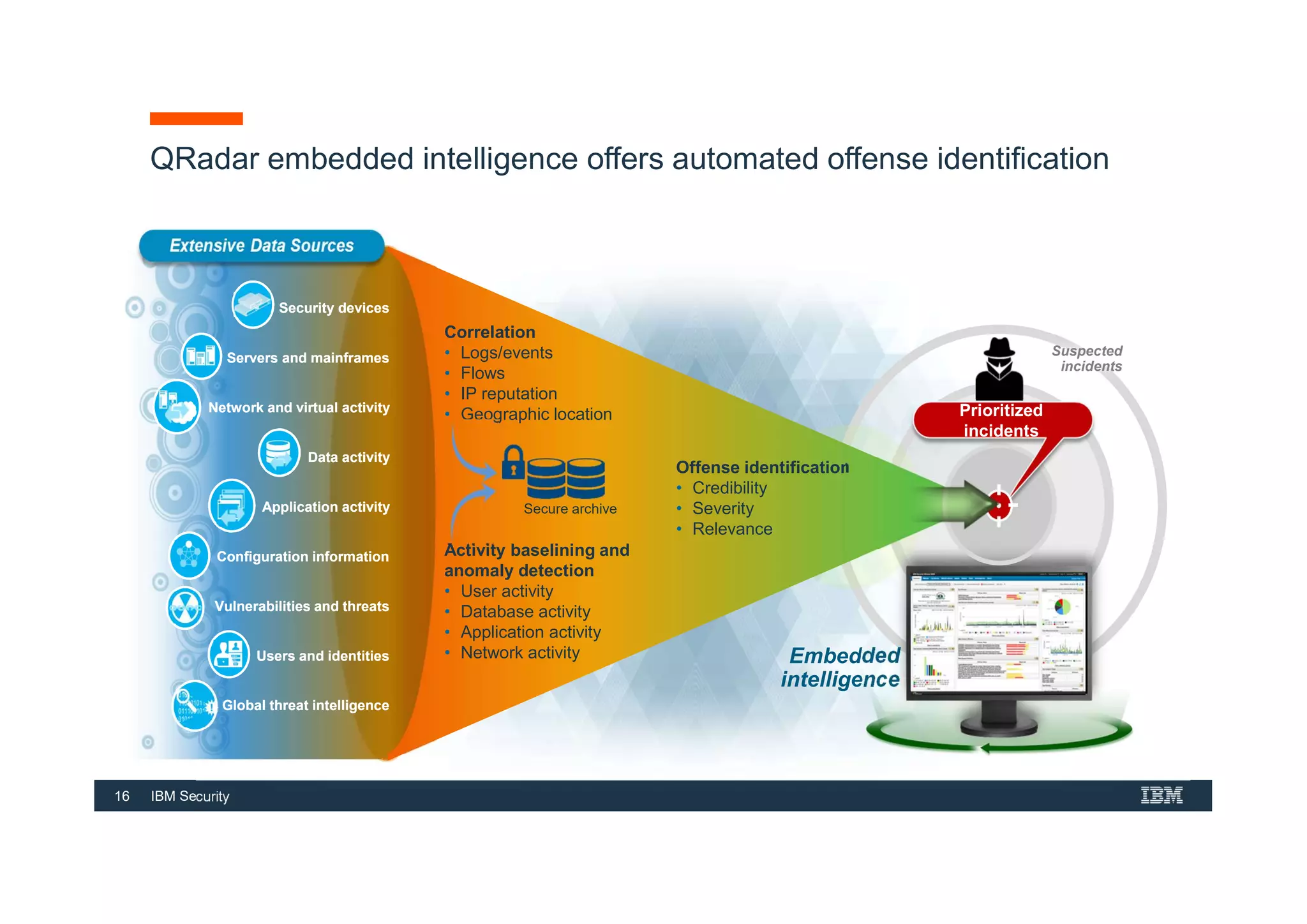
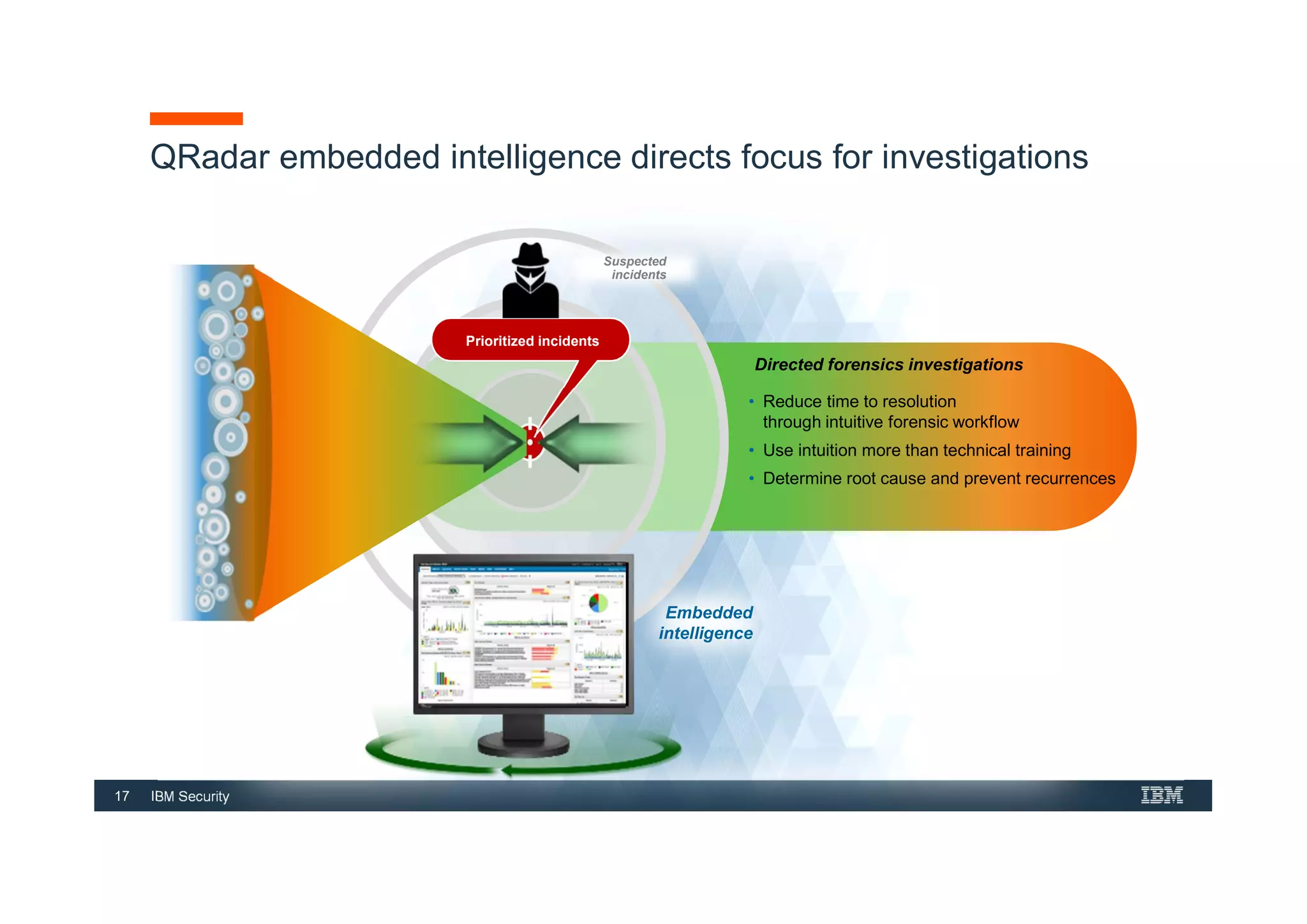
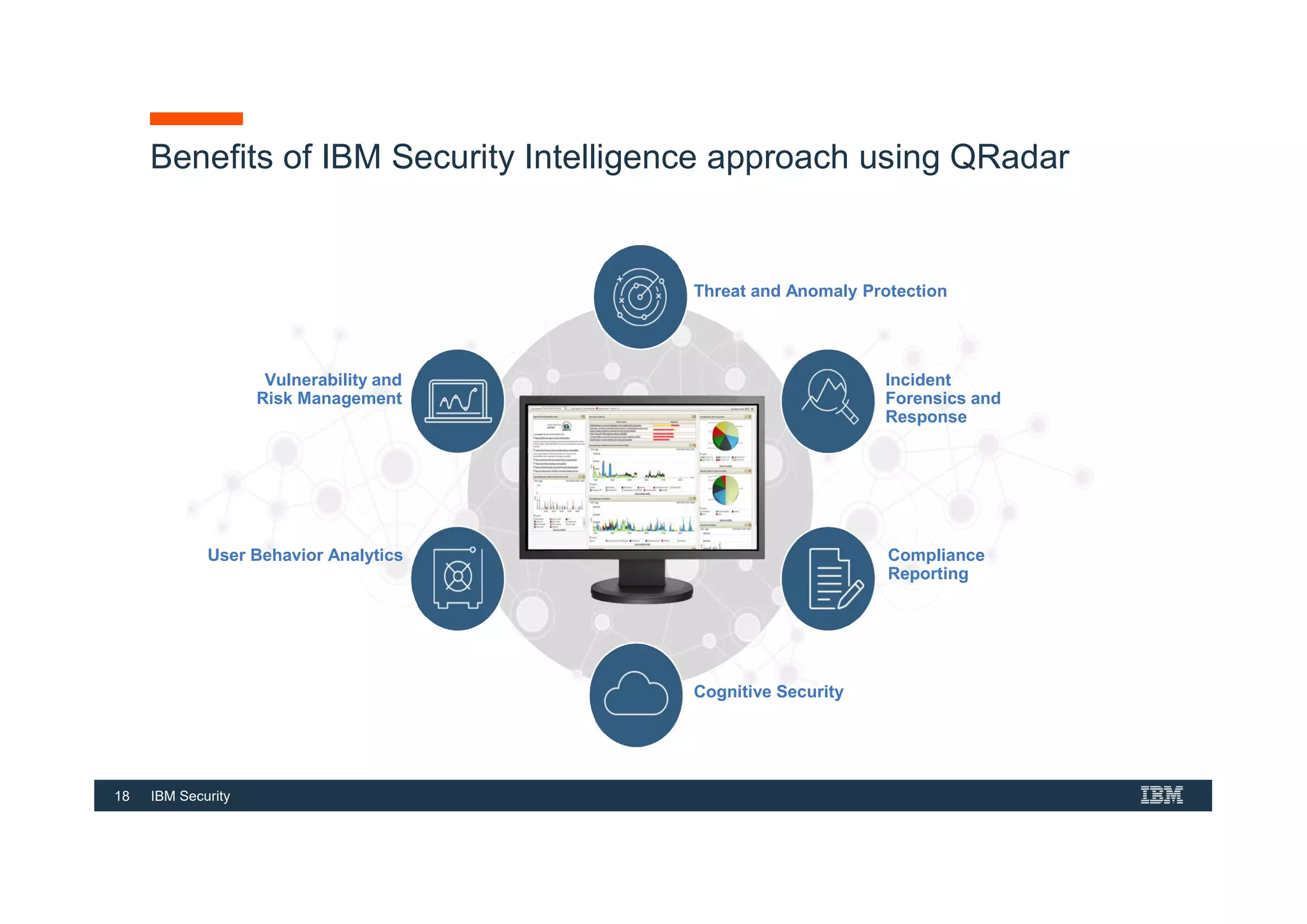
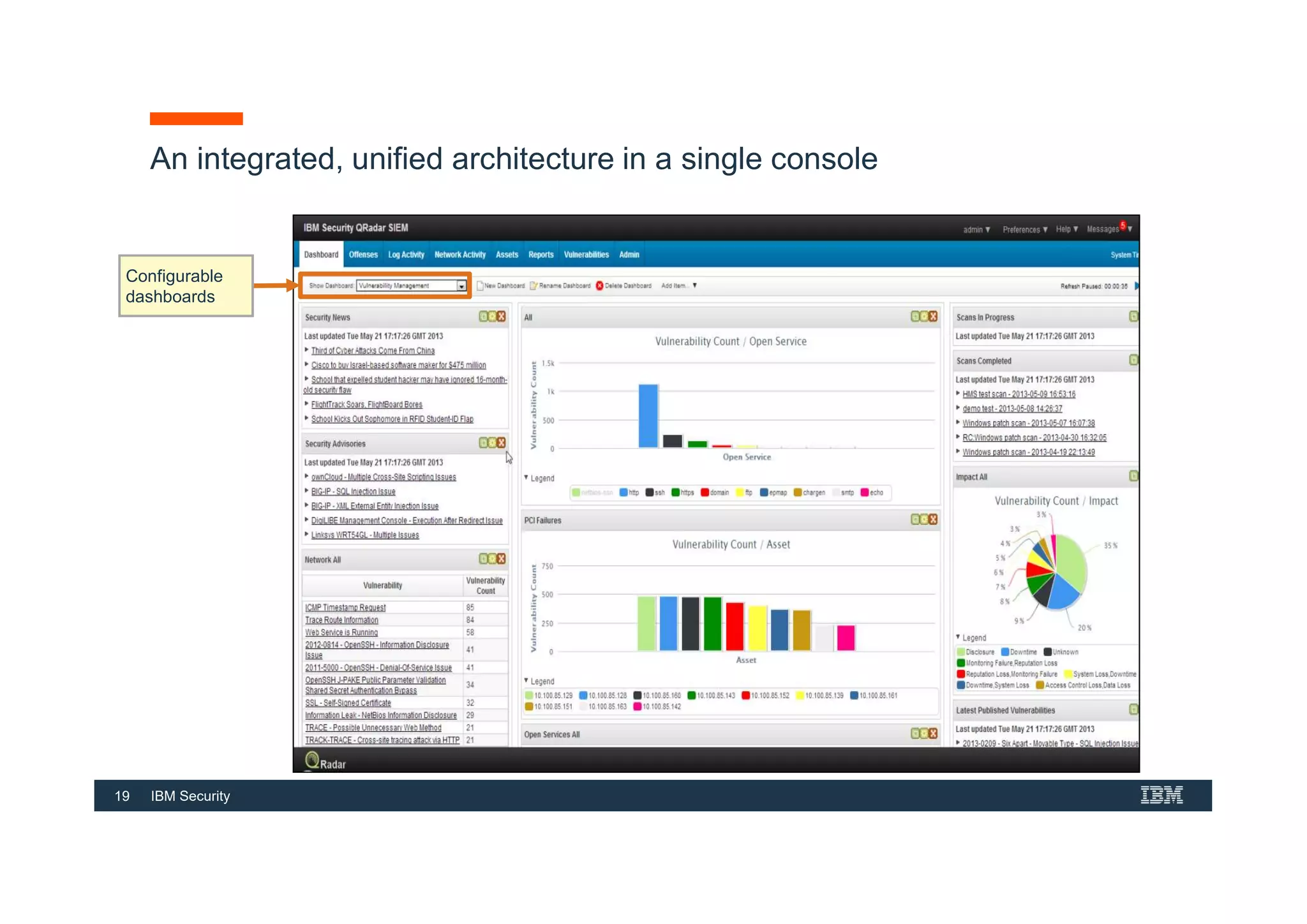
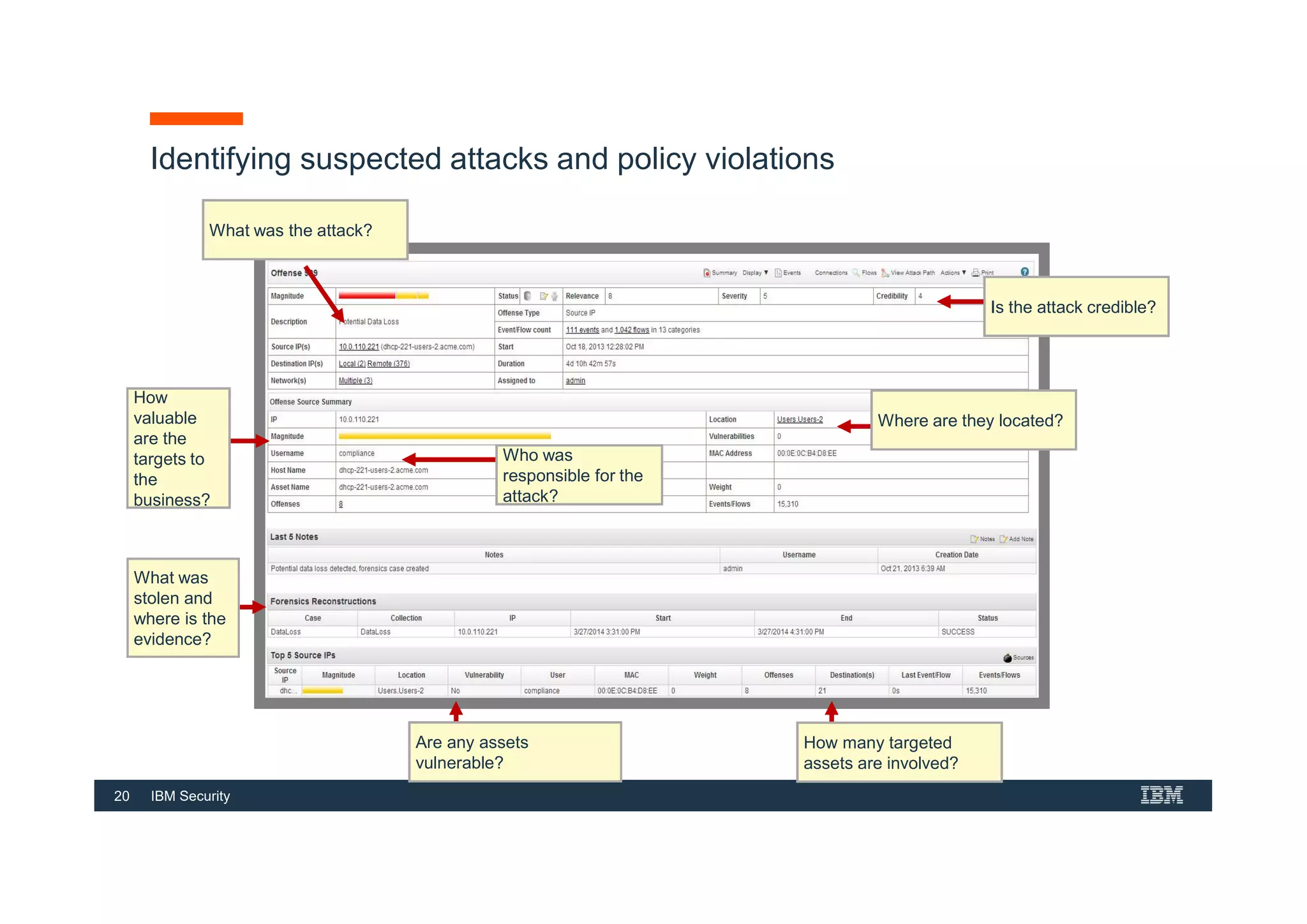
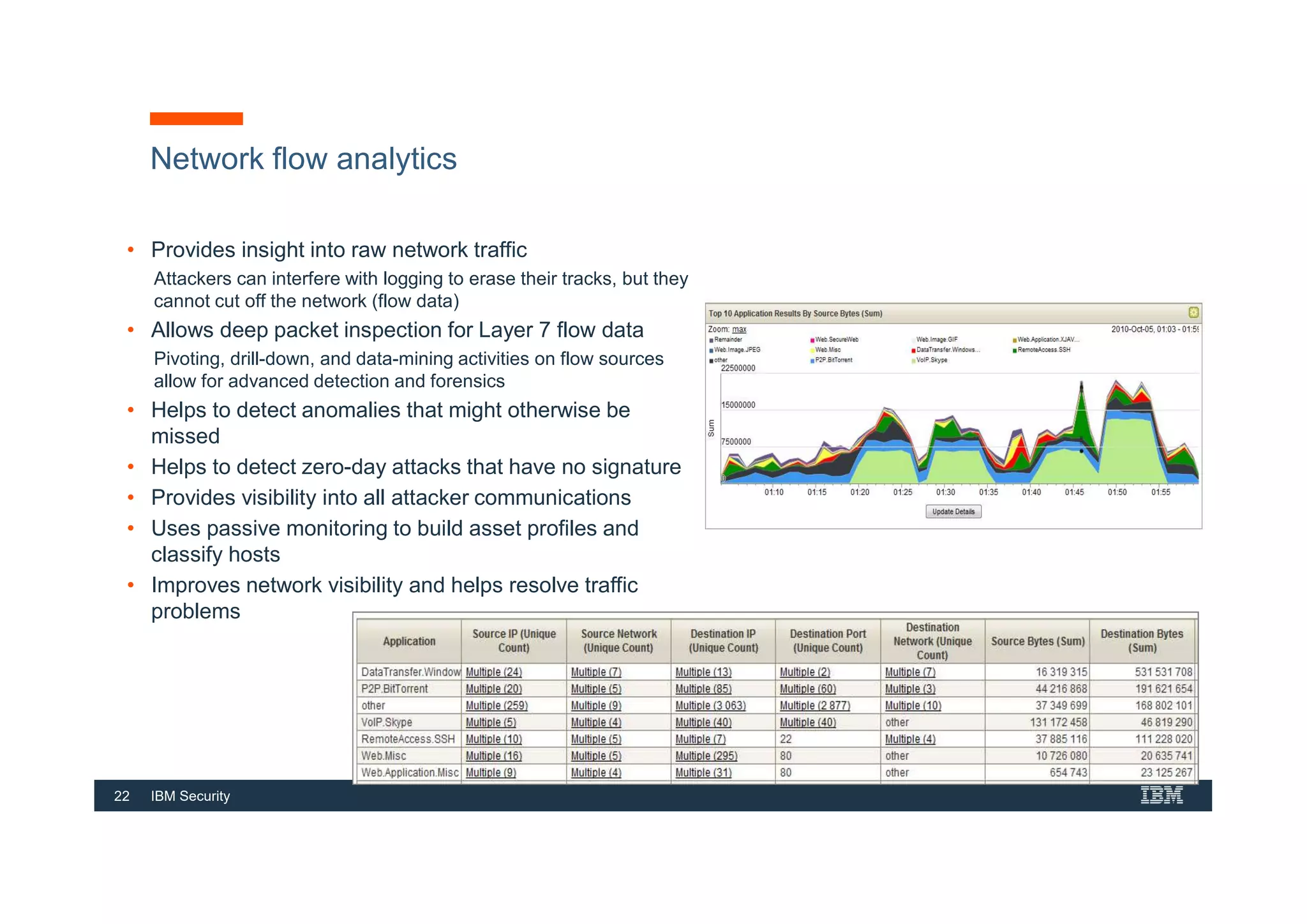
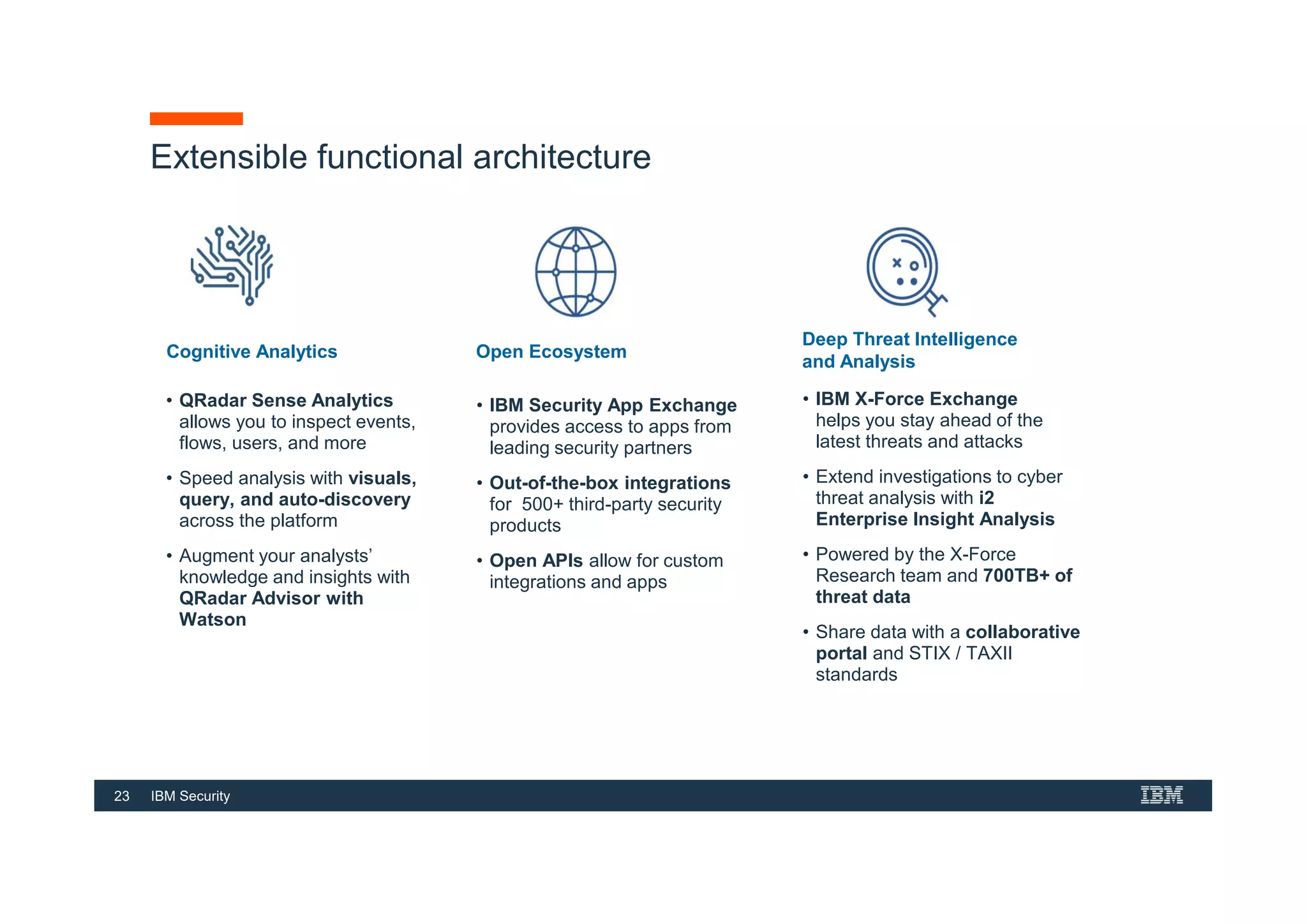
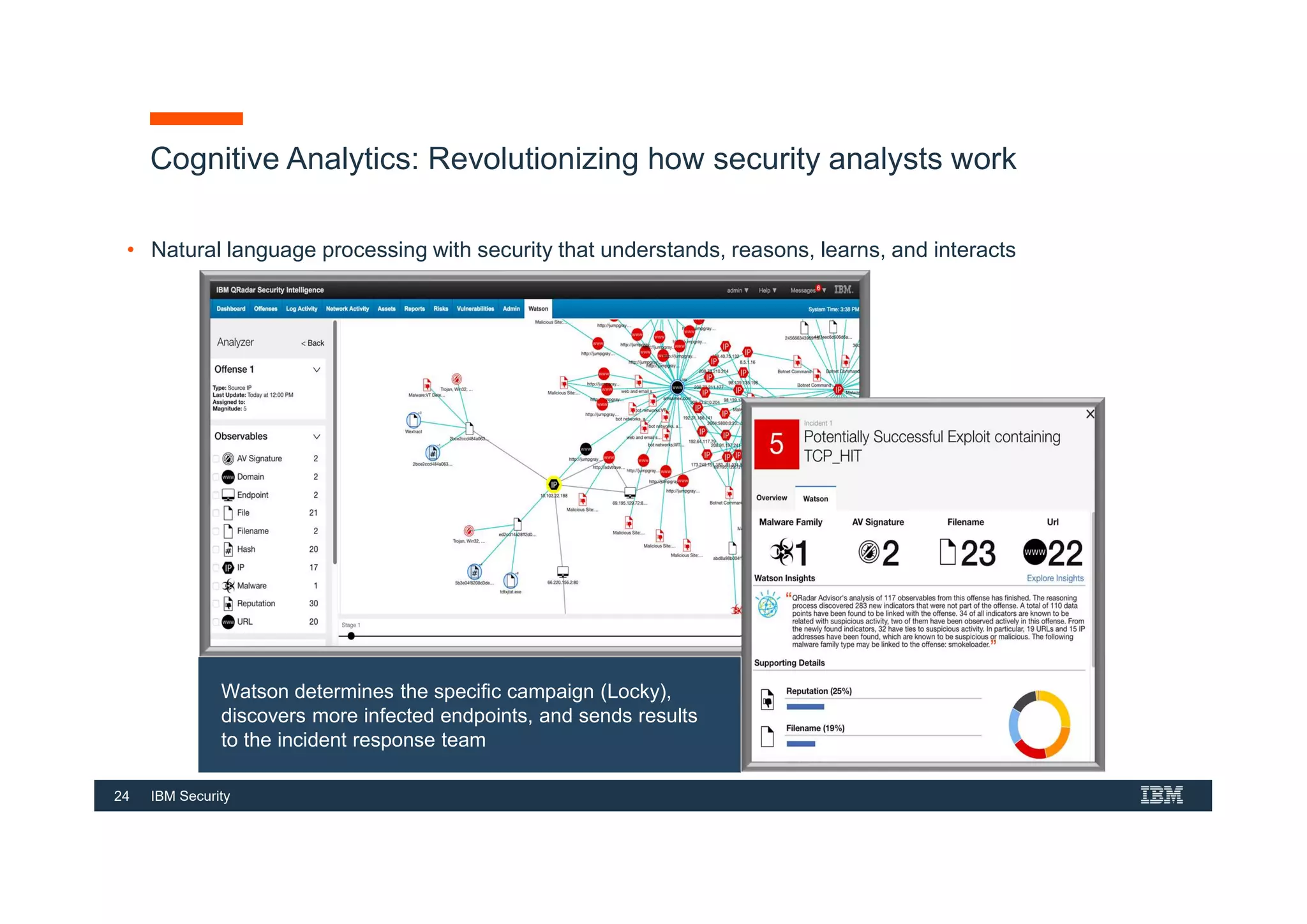
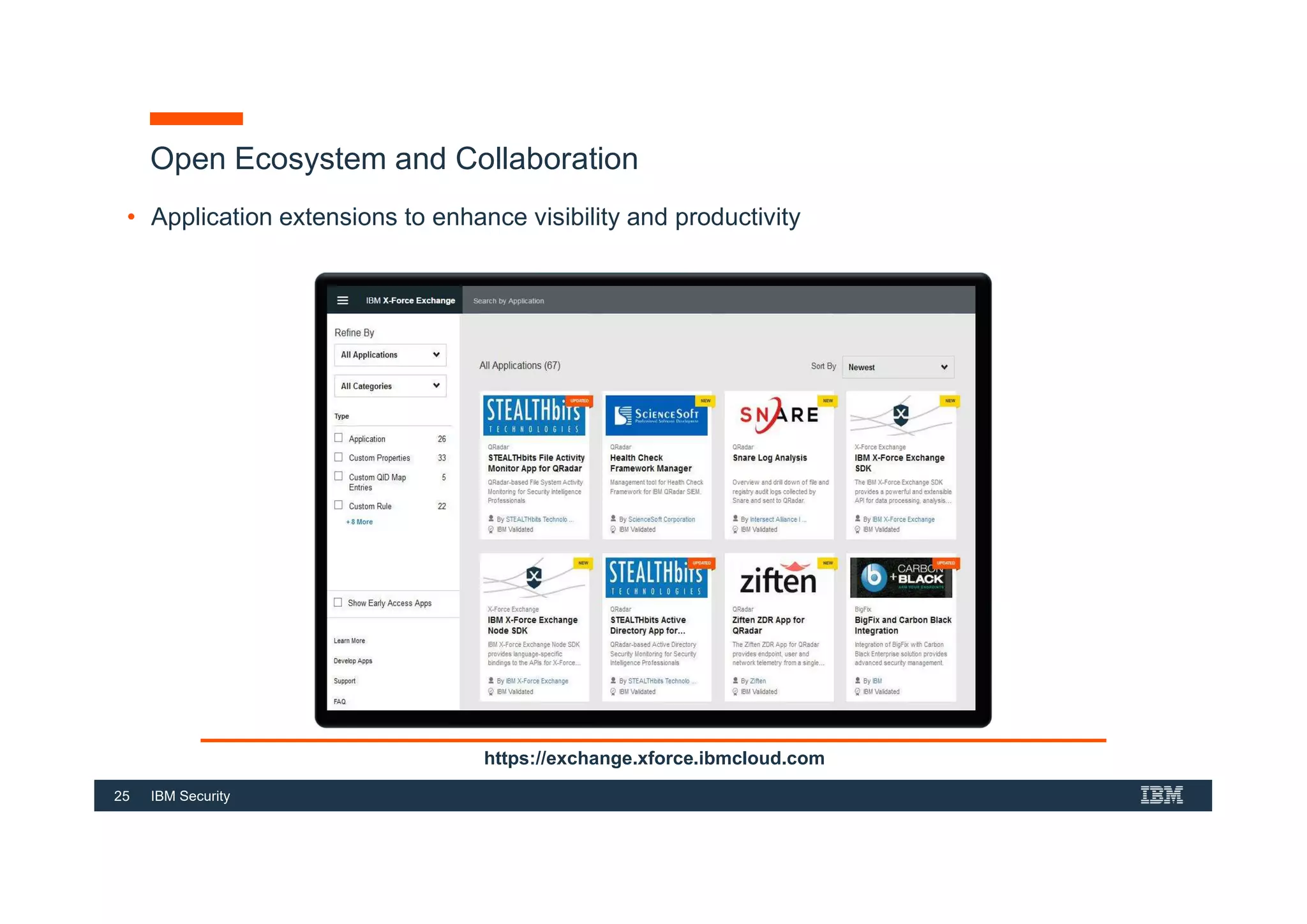
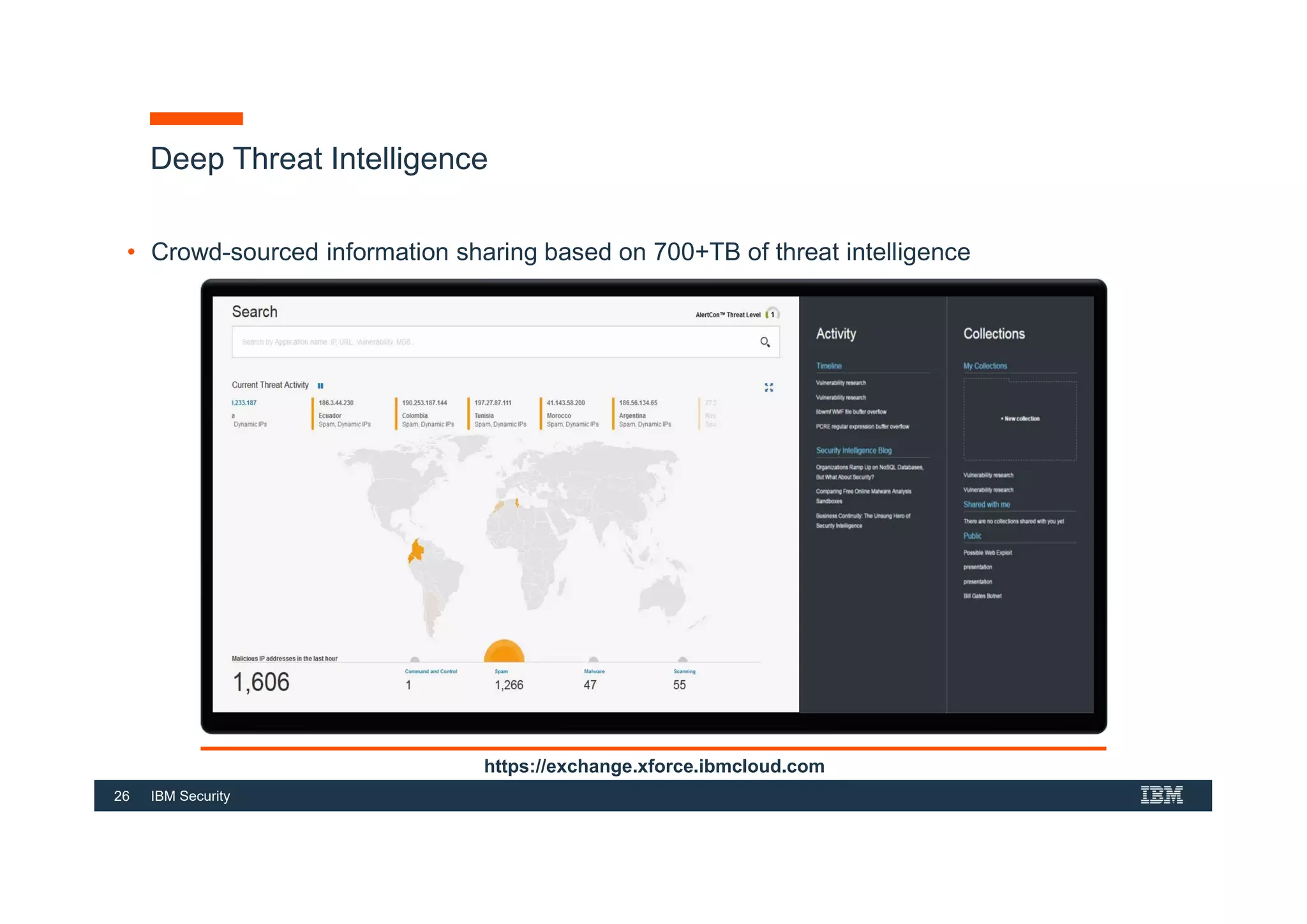
This document provides an overview of an IBM Security QRadar SIEM Foundations course. The course covers topics such as QRadar data flow architecture, deployment options, navigating the user interface, building searches and reports, managing assets and rules. It describes how QRadar integrates various security tools and uses correlation to detect threats. The document highlights how QRadar provides security intelligence through network flow analysis, cognitive analytics, and an open ecosystem.