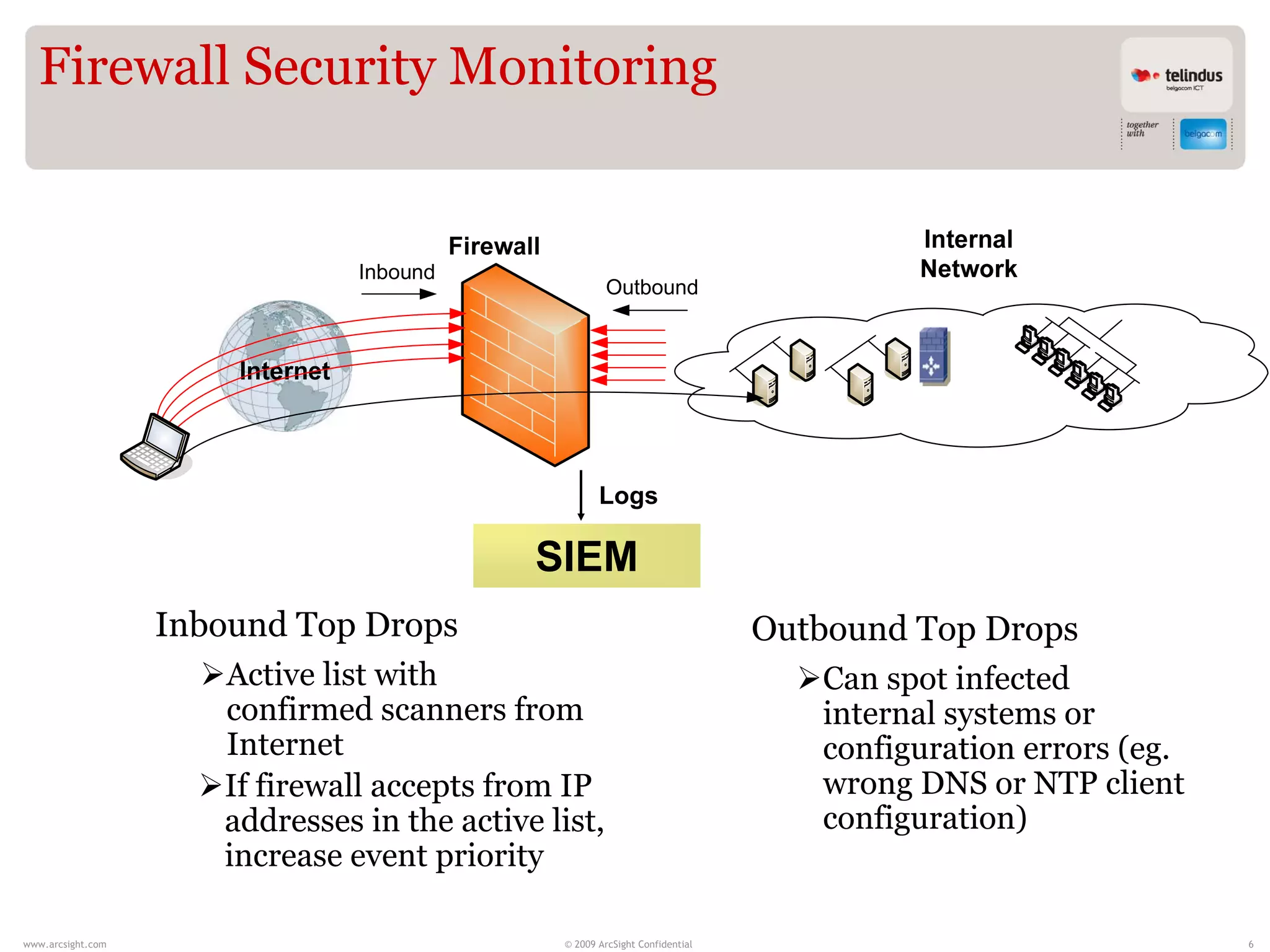
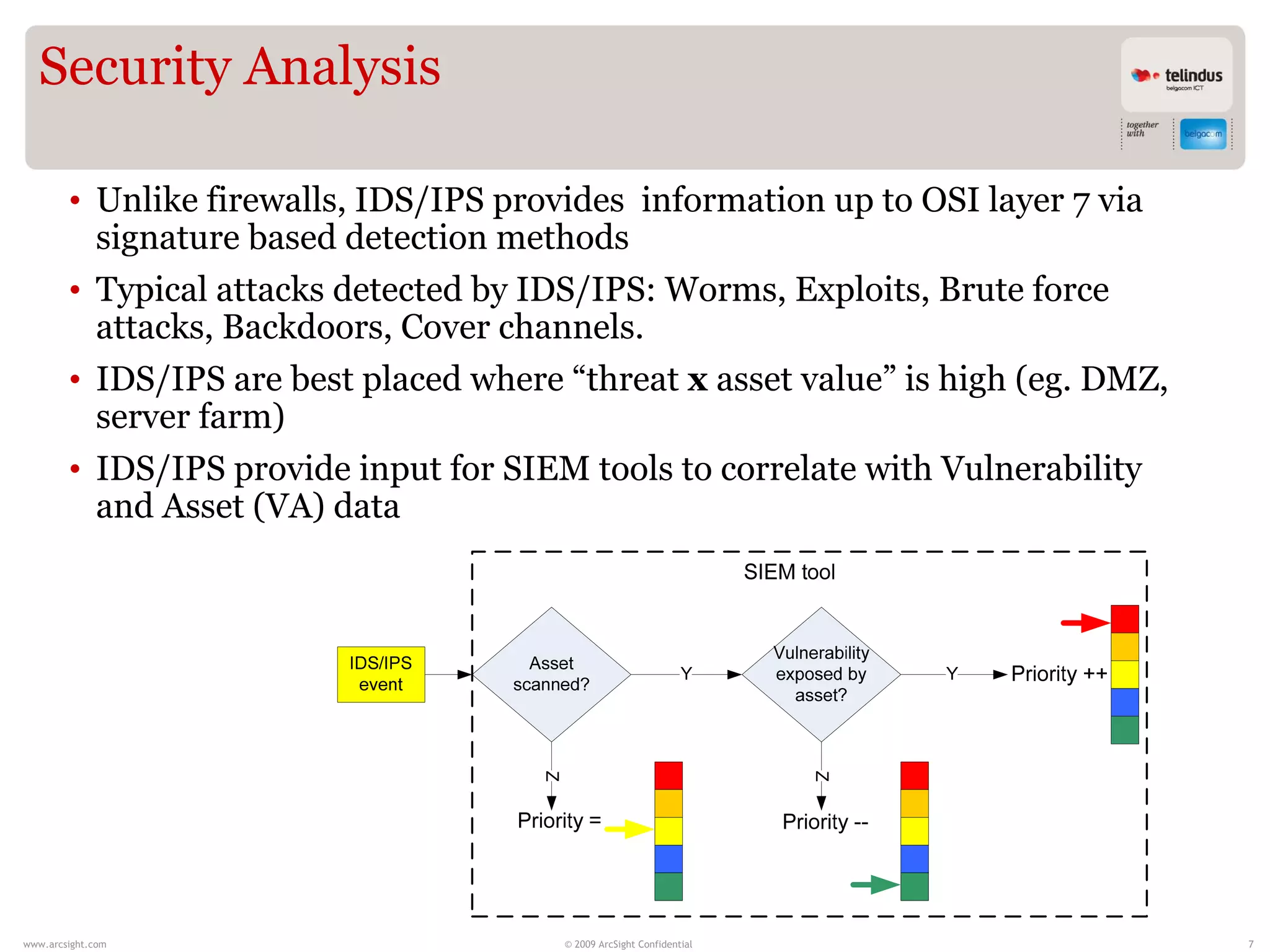
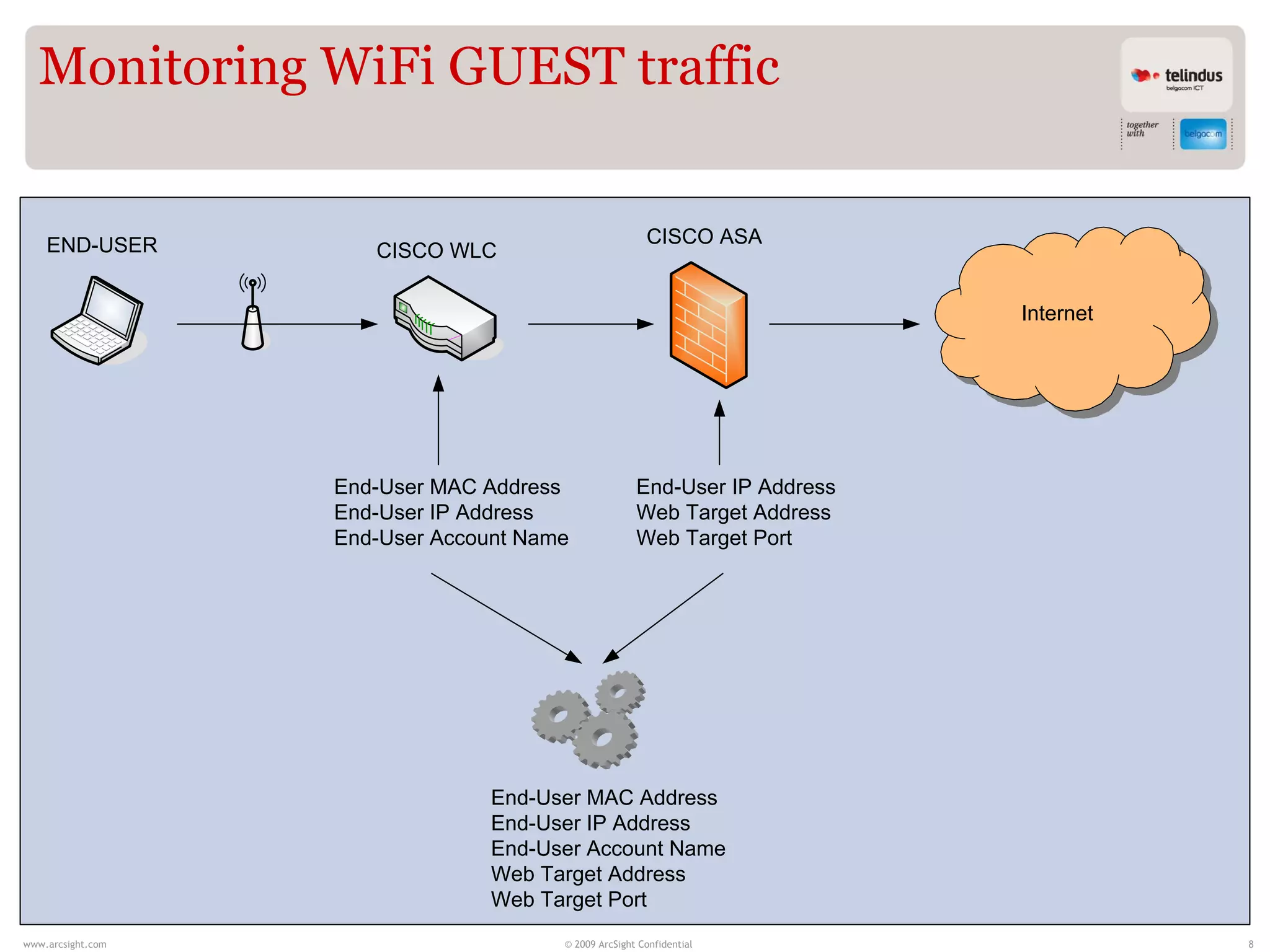
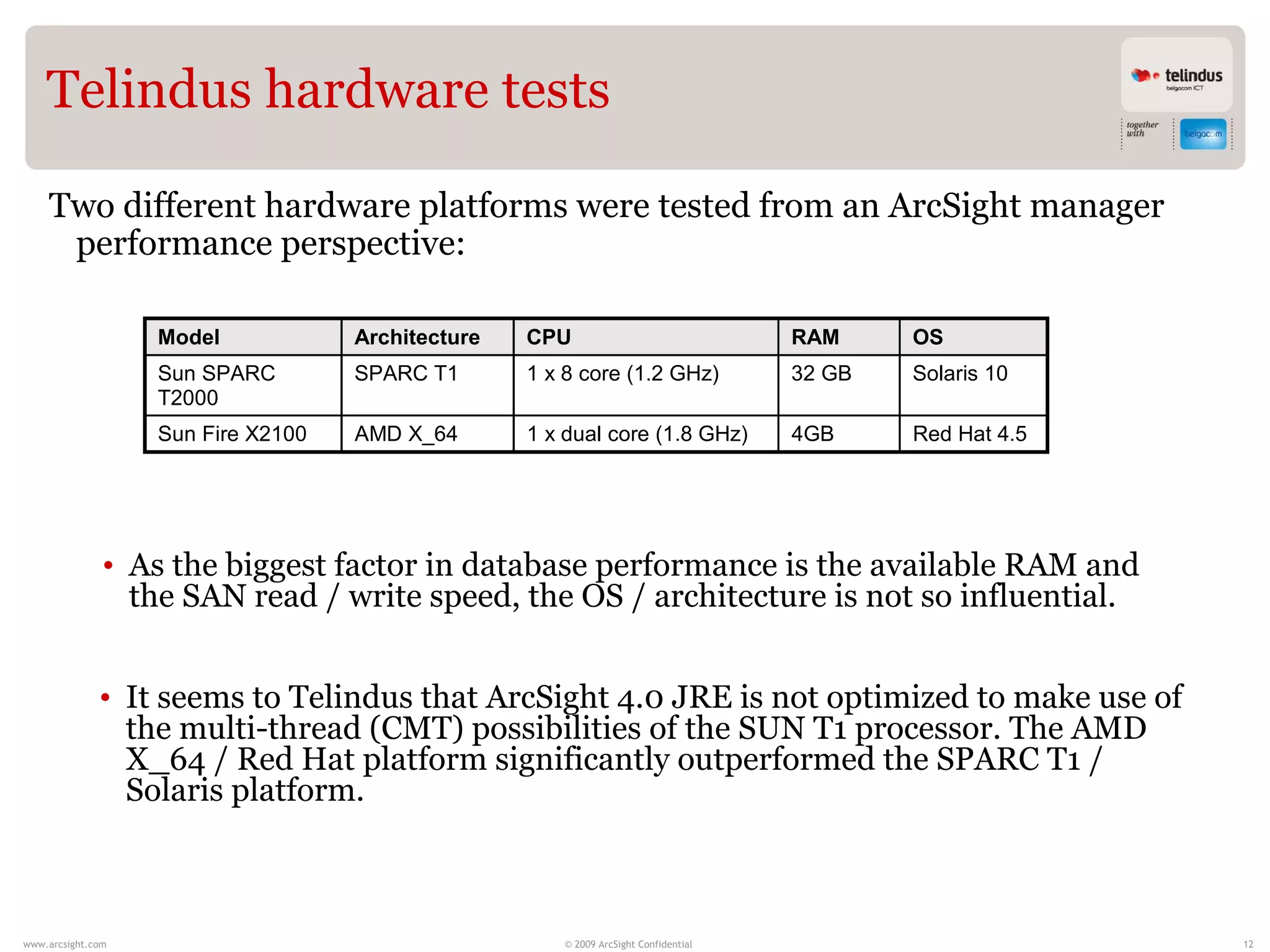
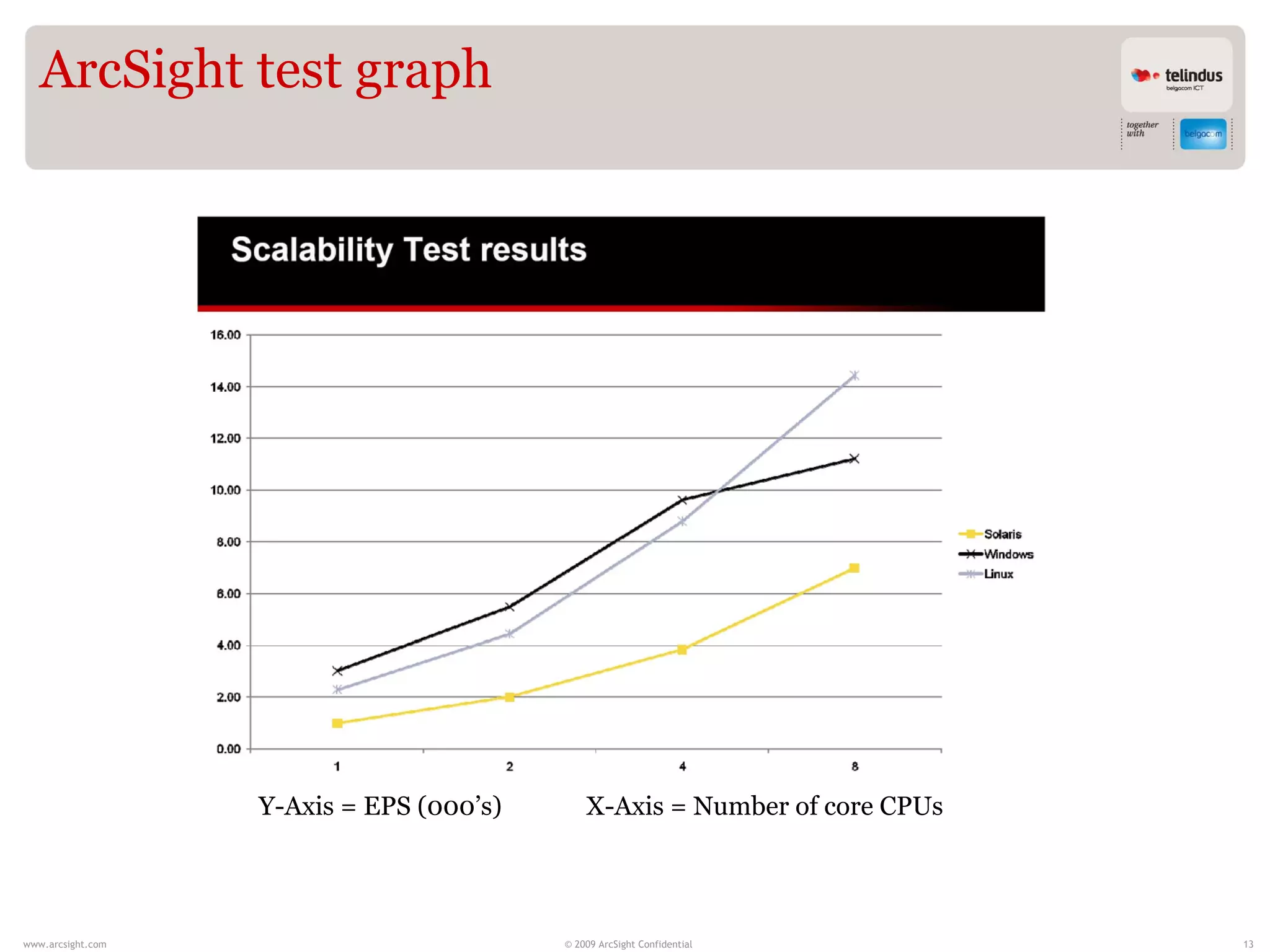
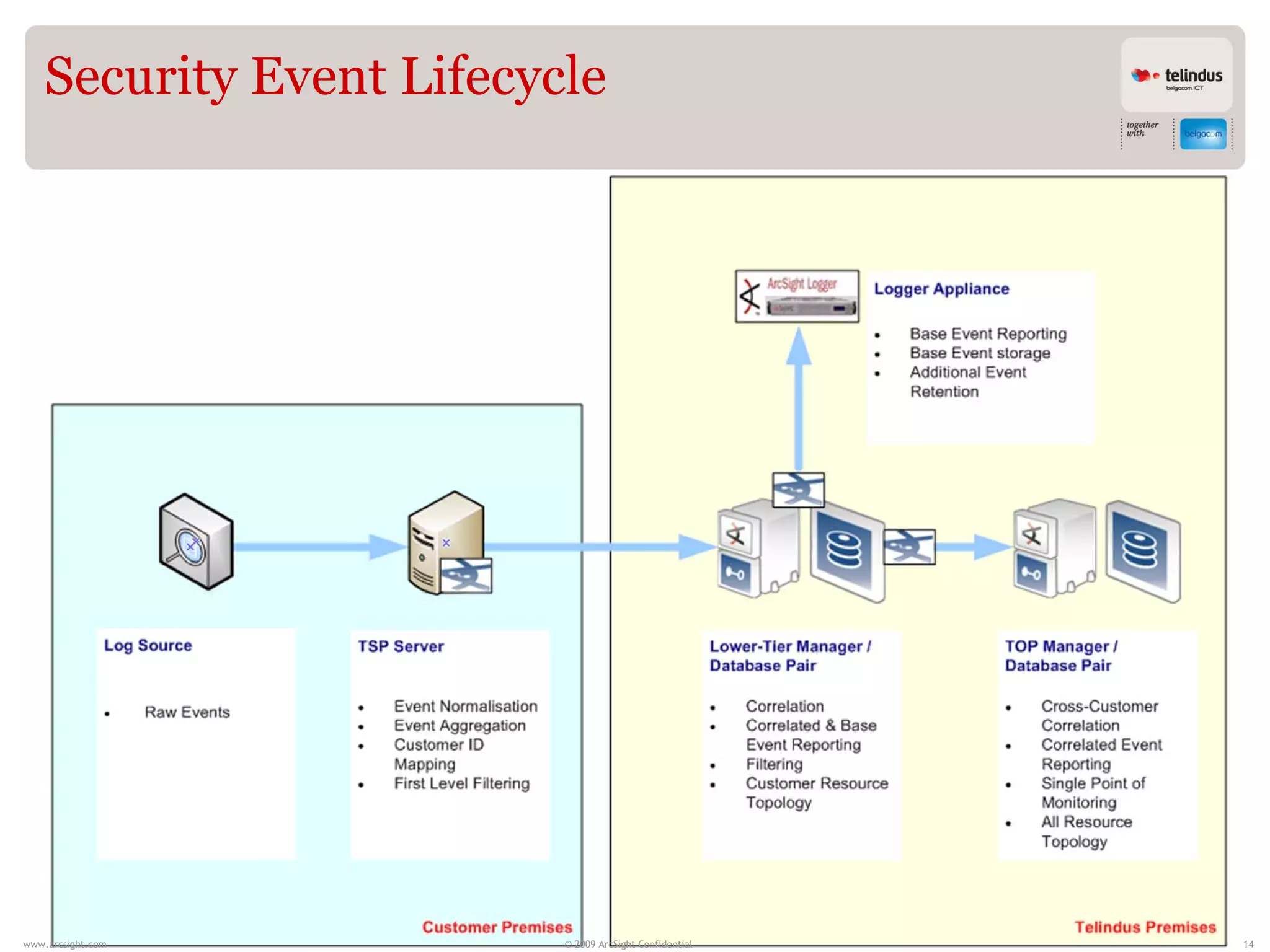
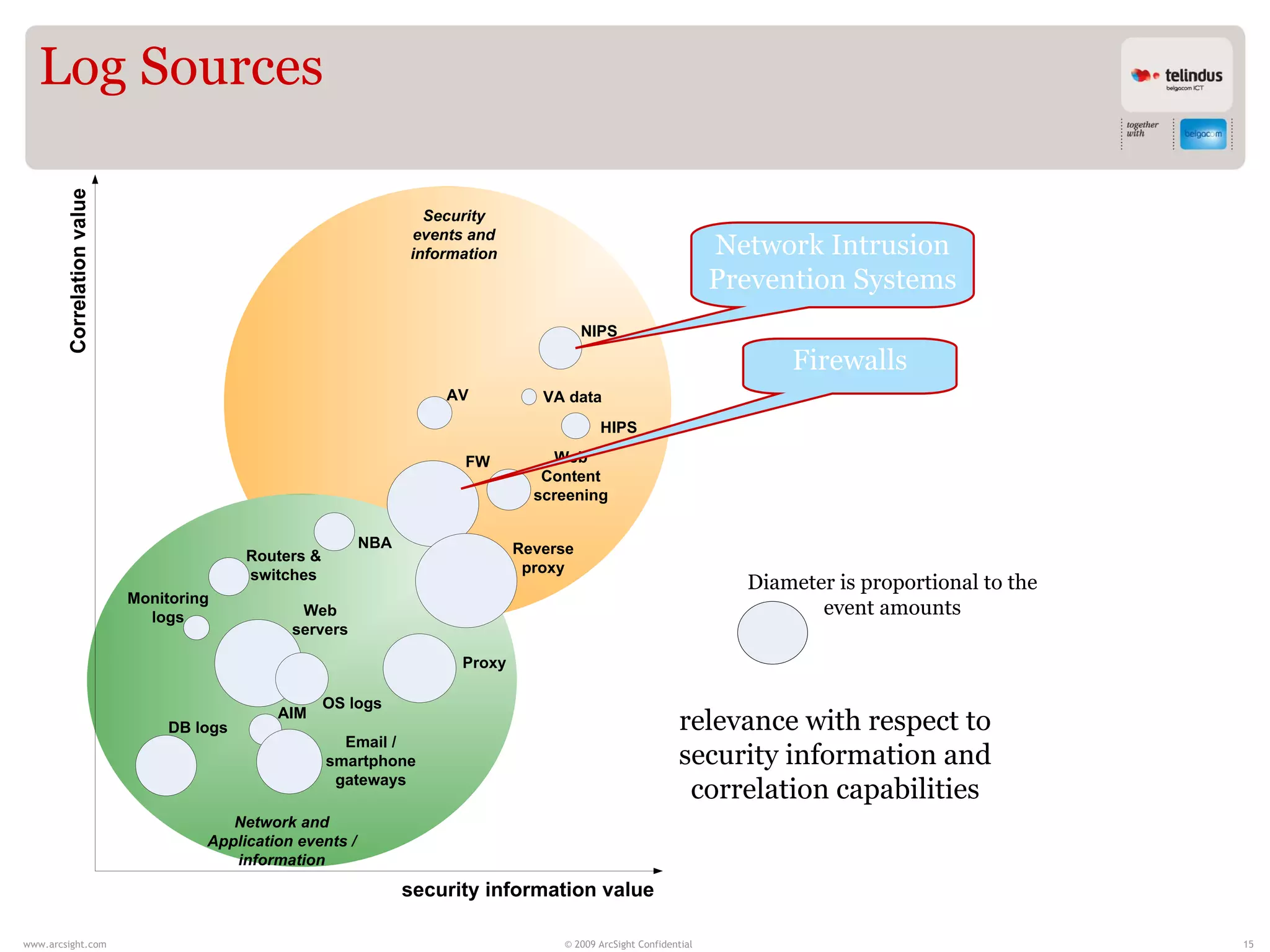
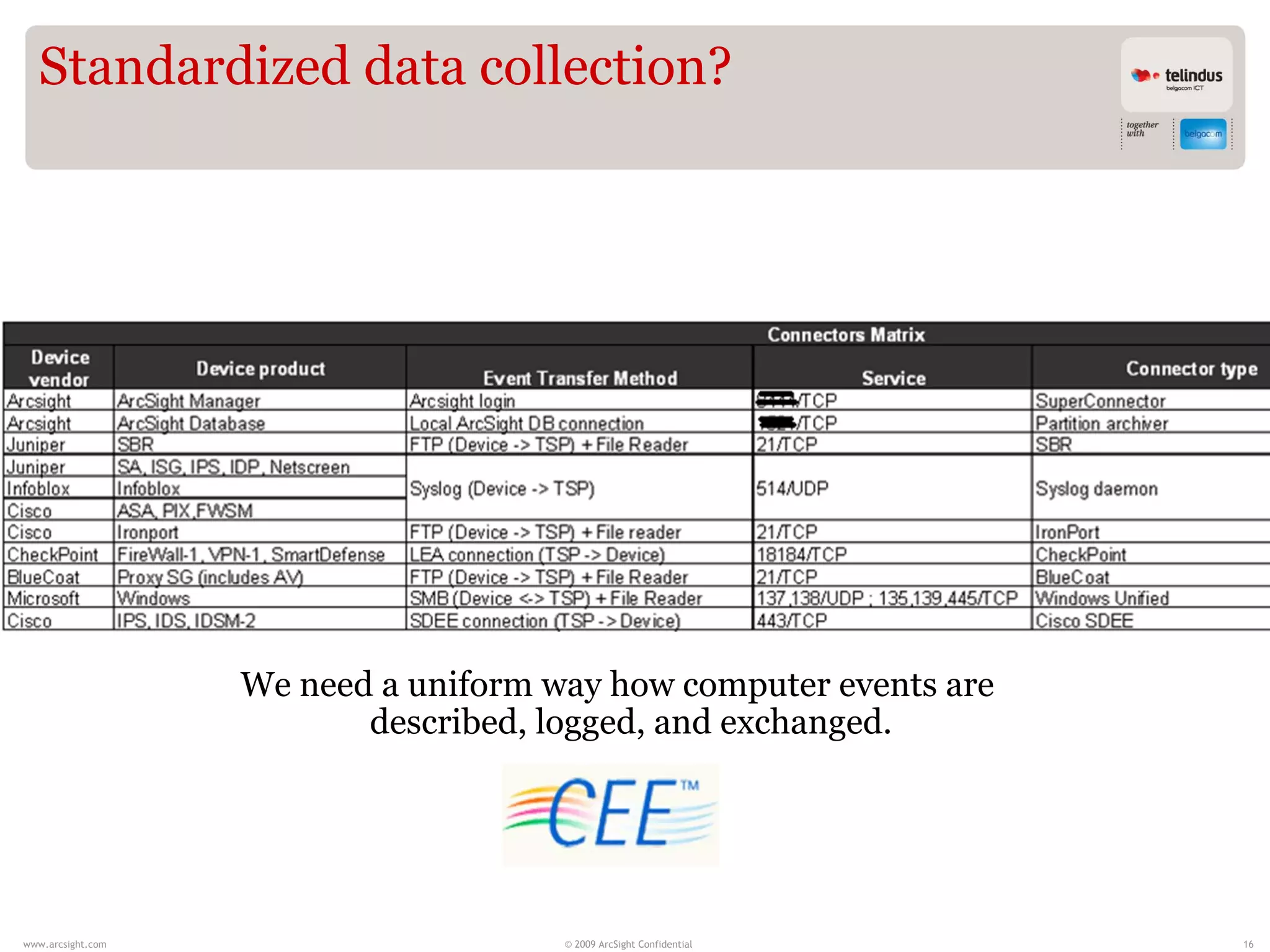
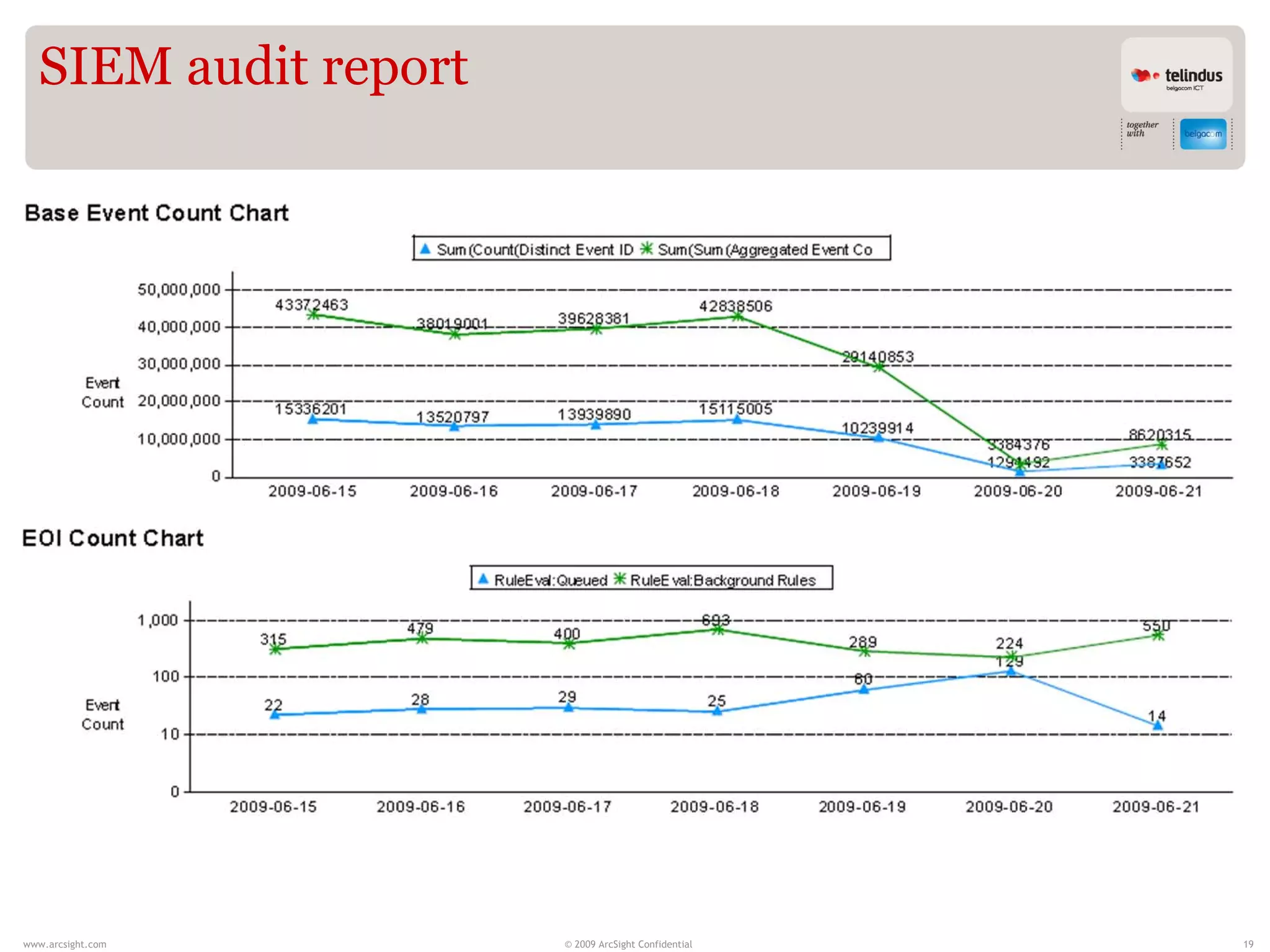
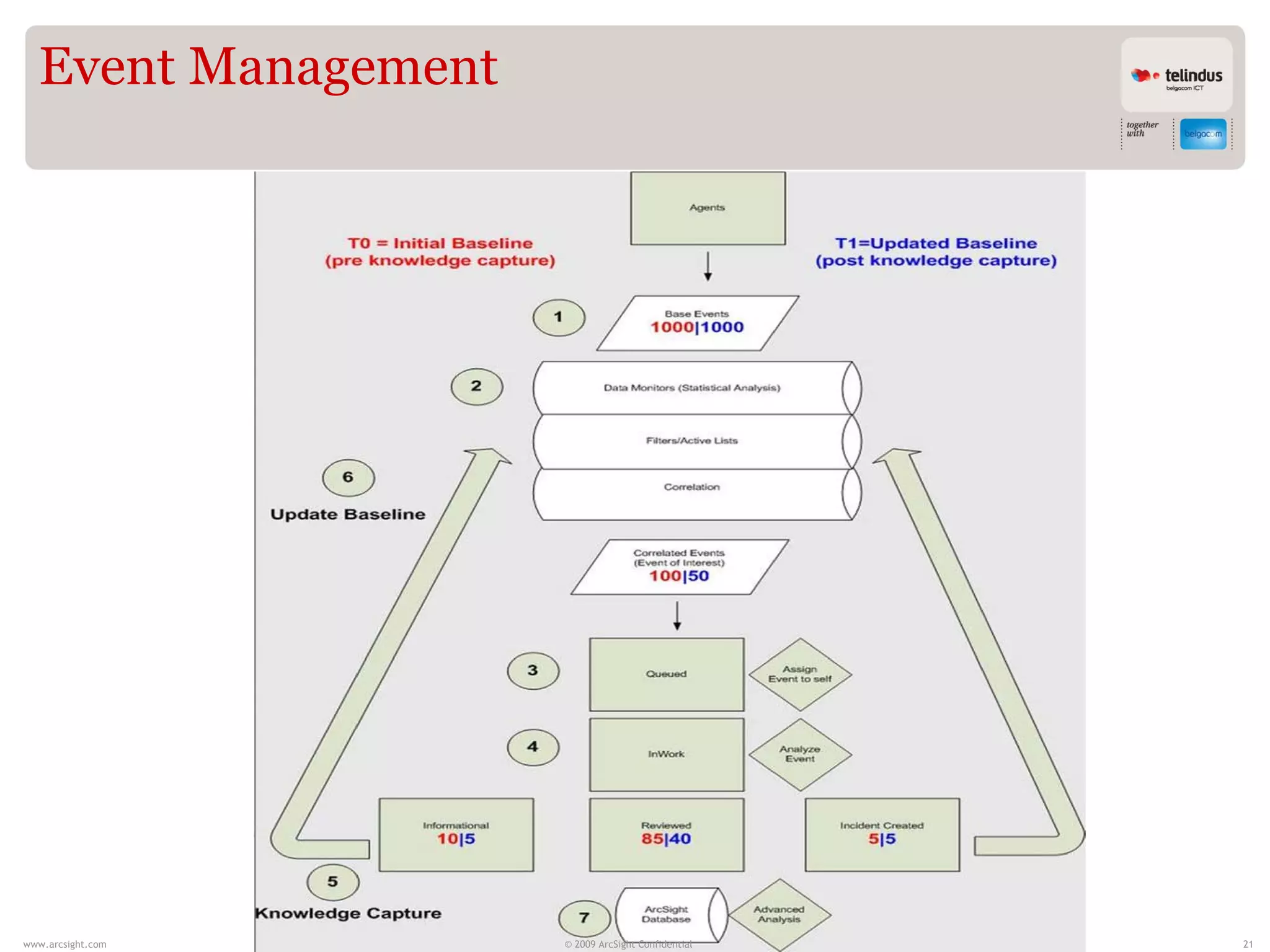
Stijn Vande Casteele is a security architect who provides solutions to underpin SIEM services. His responsibilities include engineering infrastructure to deliver security monitoring services to customers, integrating new technologies, and advising on pre-sales and security questions. He aims to create a center of excellence for SIEM within his company. The presentation discusses the evolution of SIEM, different SIEM architectures, use cases, and concludes with recommendations around carefully planning SIEM migrations and centralizing security monitoring efforts.