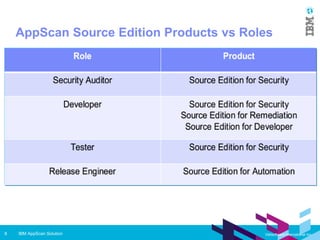
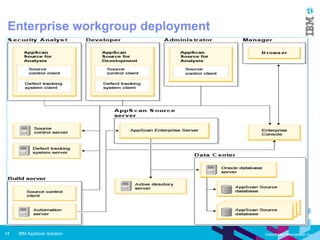
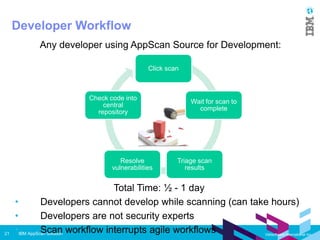
IBM AppScan Source is a static application security testing (SAST) tool that scans source code to identify vulnerabilities like SQL injection and cross-site scripting. It has components for analysis, development, remediation, and automation. It can be deployed as a standard desktop tool, in a small workgroup, or in an enterprise environment integrated with other tools. AppScan Source features include importing apps, configuring scans, viewing results, and generating reports. It aims to help security analysts, developers, and organizations identify and fix issues to prevent data breaches and other security problems.