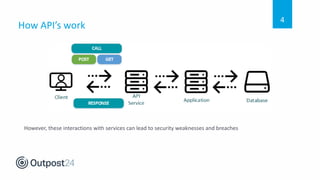
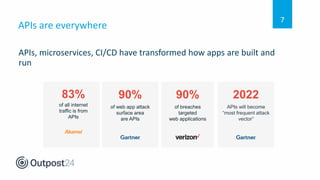
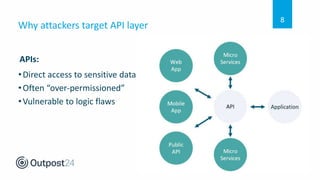
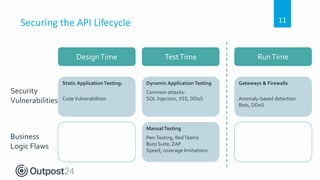
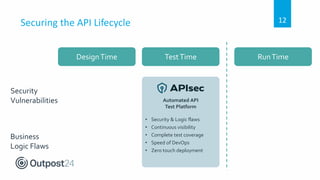
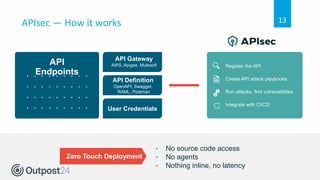
API 101 discusses how to secure web applications and APIs. APIs are used extensively in web and mobile applications to allow communication between services but this can introduce security weaknesses if not implemented properly. API attacks are a growing threat, with 90% of breaches targeting web applications and APIs projected to become the most common attack vector by 2022. The document outlines security best practices for securing APIs throughout the development lifecycle from design to testing to runtime, and how one company implemented API security testing to improve their compliance and privacy posture.