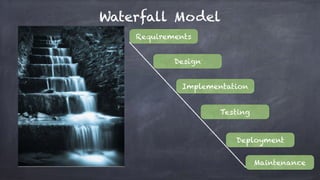
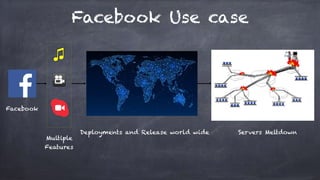
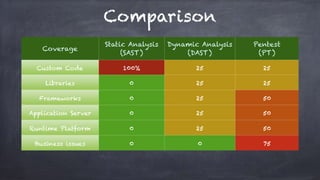
The document discusses the evolution and practices of DevSecOps, highlighting key methodologies like waterfall and agile, along with the integration of security tools such as SAST, DAST, and SIEM in the software development lifecycle. It outlines the benefits and drawbacks of various development methodologies and provides insights into real-world applications, including Facebook's 'dark launching' technique for feature deployment. Additionally, it details the importance of automating security assessments and vulnerability management in DevSecOps to enhance overall software security.