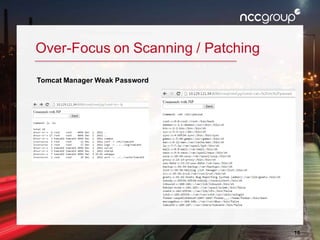
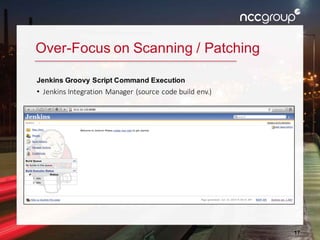
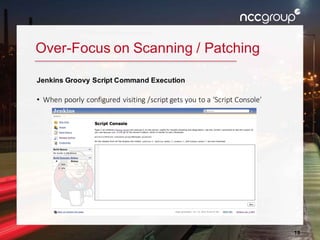
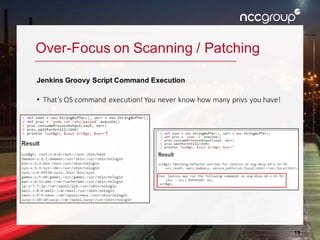
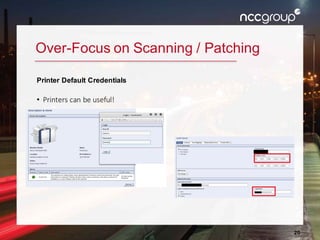
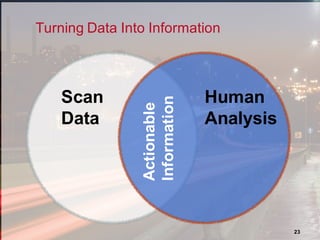
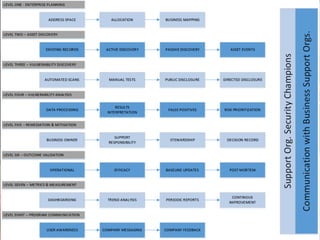
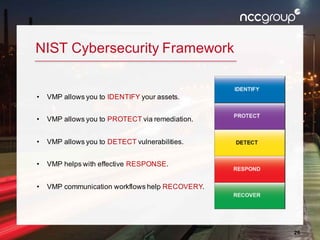
The document outlines a presentation on enterprise vulnerability management by NCC Group, highlighting the importance of effective vulnerability identification, classification, and remediation strategies. It discusses common pitfalls in vulnerability management processes, emphasizing the need for integrating workflows and effective asset management over merely increasing scan frequency. The speakers, Damon Small and Kevin Dunn, encourage organizations to focus on comprehensive vulnerability management design rather than solely on scanning efforts.