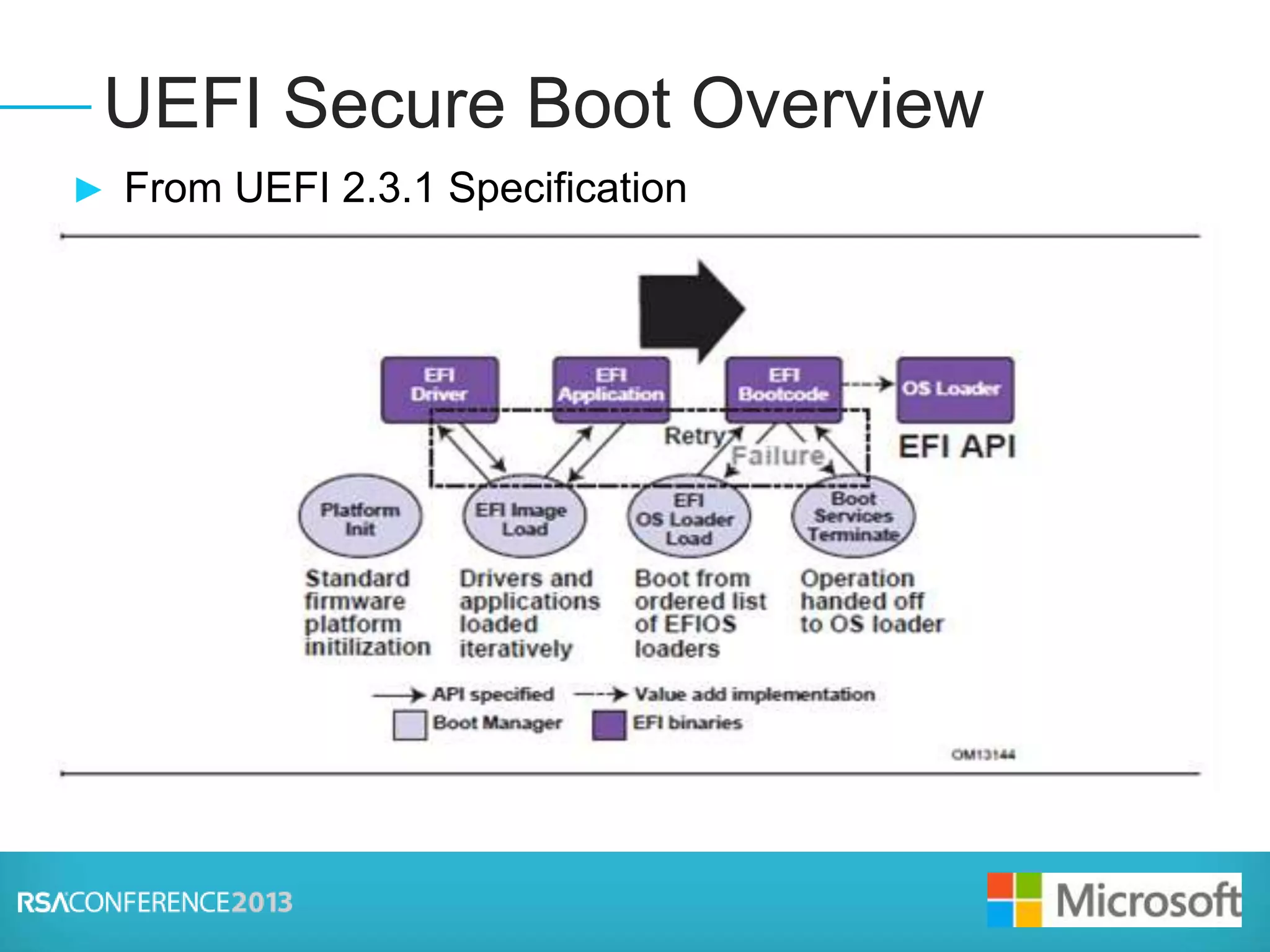
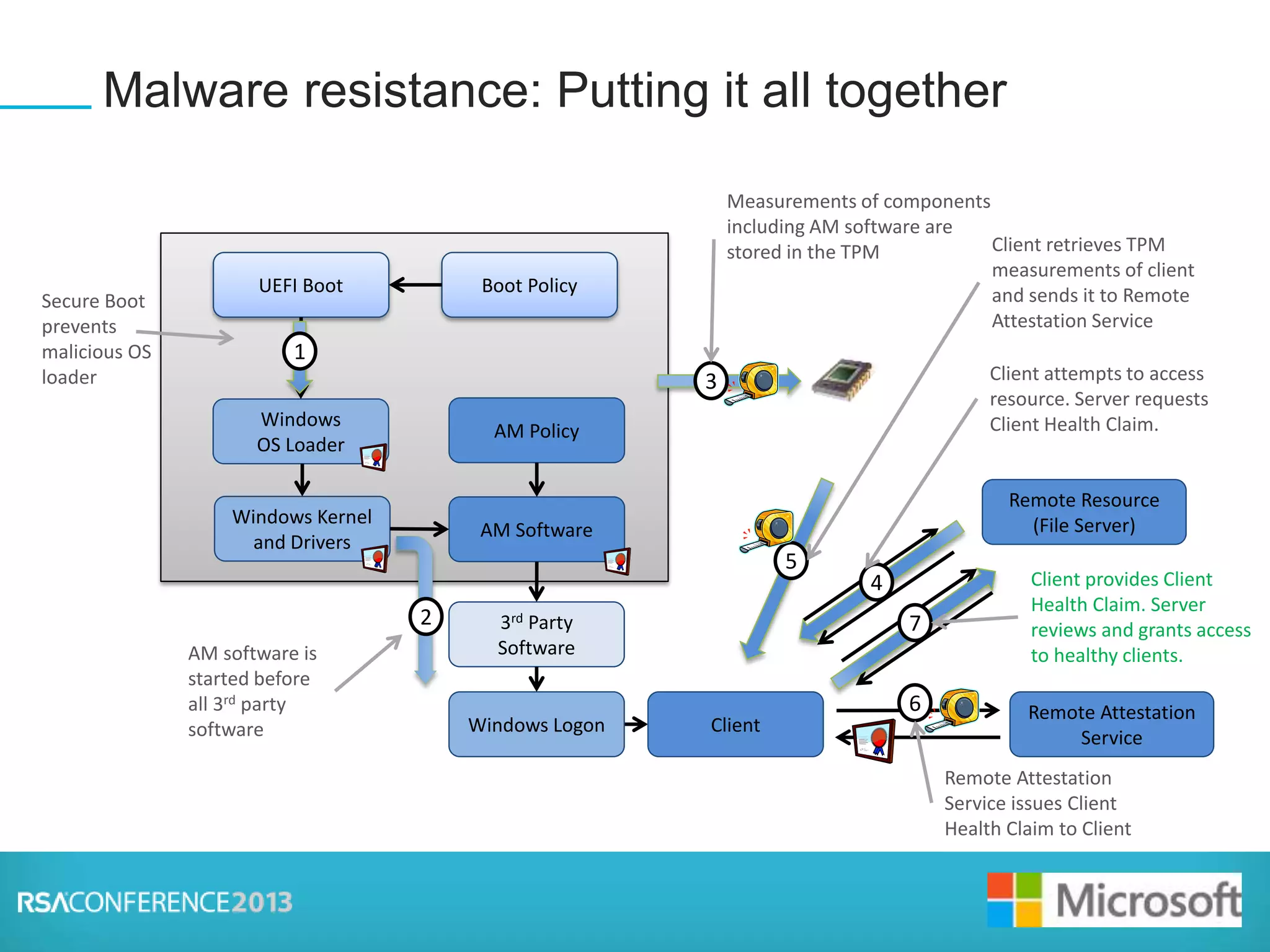
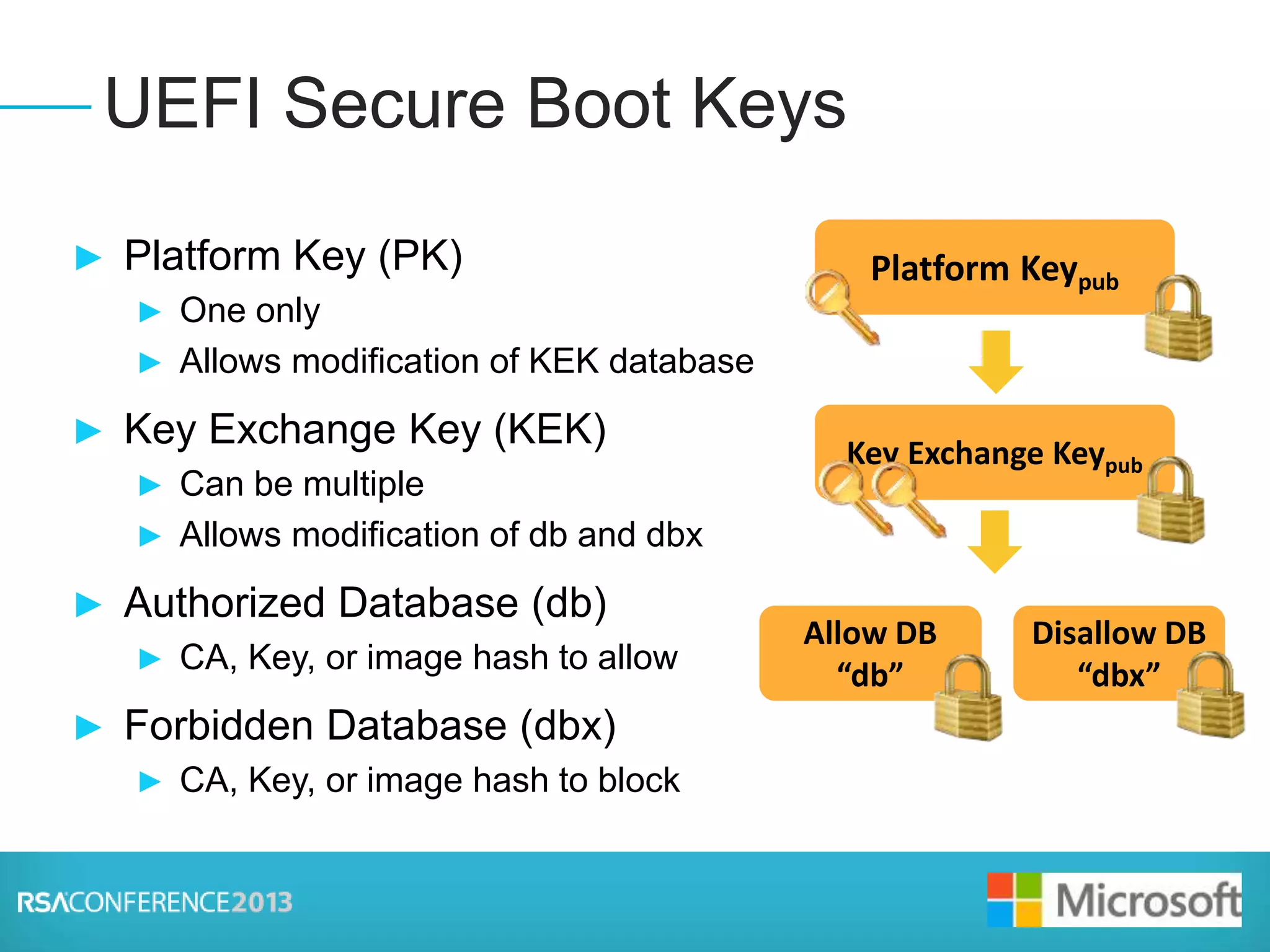
This document discusses firmware threats and solutions. It begins with a presentation on firmware threats, implications, and UEFI Secure Boot. It then discusses how UEFI Secure Boot and Windows 8 Trusted Boot work to secure the boot process. Finally, it covers secure firmware updates and concludes that securing firmware is foundational to system security.