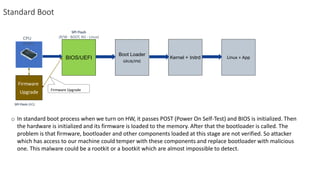
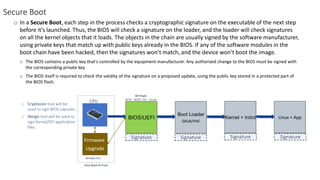
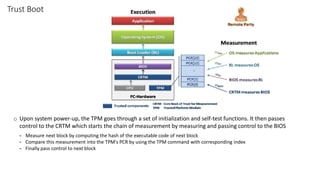
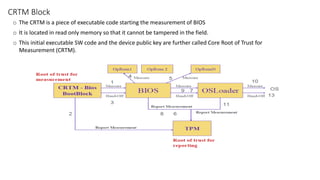
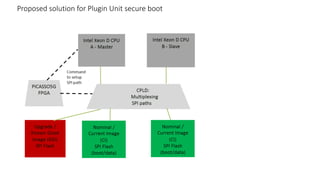
The document discusses secure boot, trusted boot, and their differences. It provides an overview of standard boot processes, secure boot processes where each step is cryptographically signed, and trusted boot which records measurements to the TPM for later verification. It also proposes a solution for secure boot in 5G plugin units using platform keys, key exchange keys, and allowed/forbidden signature databases.