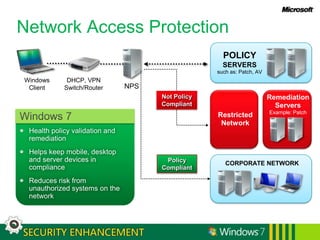
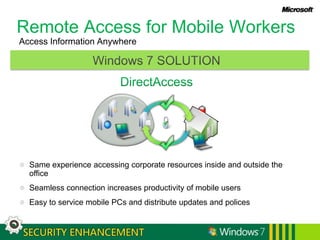
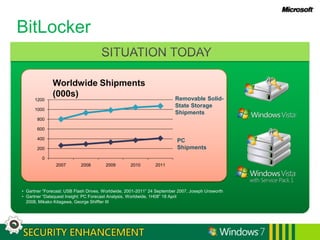
Windows 7 provides enhanced security features for IT professionals to securely manage access and protect data and infrastructure. It includes a fundamentally secure platform with strengthened access controls and auditing. Windows 7 also enables securing access from any location through improved network security, protection of mobile devices, and direct secure access. Additional features protect users and infrastructure through application control and data recovery tools, as well as protecting data from unauthorized viewing using encryption and information rights management.