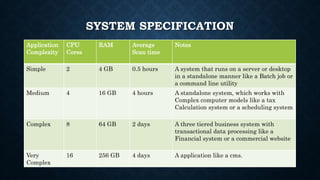
The document provides information on HP Fortify Source Code Analyzer (SCA). It can analyze source code for various languages like Java, .NET, PHP etc. to identify security vulnerabilities. The installation process involves extracting files and providing a license key. System requirements vary based on the size and complexity of the code being analyzed. Reports can be generated in different templates like OWASP Top 10. Filter sets help classify issues by priority. Commands are available to customize and optimize scans.









![FILTER SET
• Filter set is used to differentiate high , medium and low priority issues.
• By Default fortify enables two filters for viewing the issues 1)Quick View 2)Security
Audit View.
• Quick View -> 1.Hide Issue if impact is not in range [2.5,5.0]
2.Hide Issue if Likelihood is not in range [1,5]
• Security Audit View -> Show every issue based on category specified.
• We can add our customized filter set](https://image.slidesharecdn.com/hp-fortifysca-160921053251/85/Hp-fortify-source-code-analyzer-sca-11-320.jpg)
