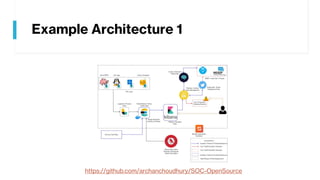
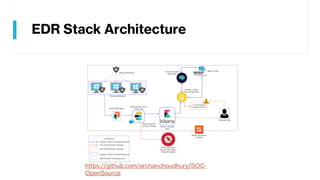
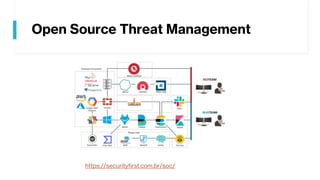
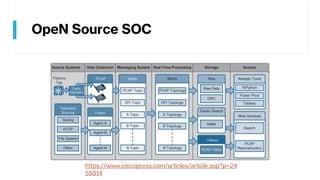
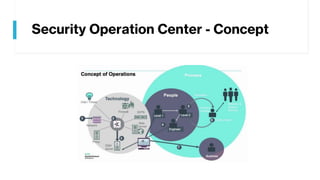
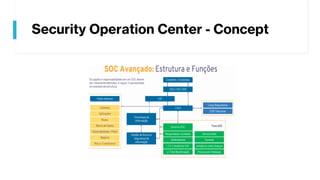
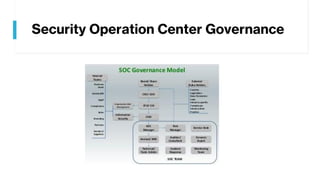
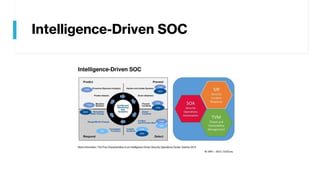
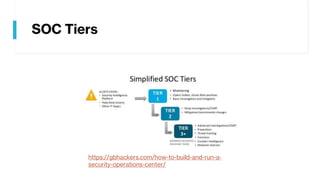
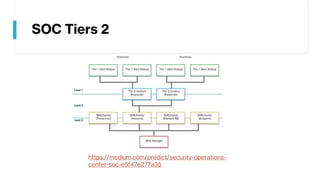
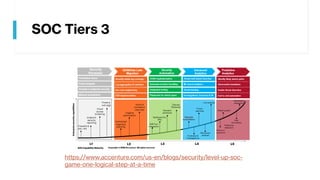
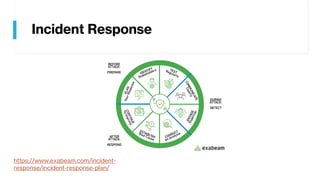
This document provides summaries of various security tools used in security operations centers. It describes the purpose and link for each tool, including Sooty for automating analyst workflows, Peepdf for analyzing PDF files, PyREBox for reverse engineering sandboxes, Fail2Ban for blocking brute force attacks, OSSEC for host-based intrusion detection, and Splunk for log management and analytics. Over 20 security tools in total are summarized.