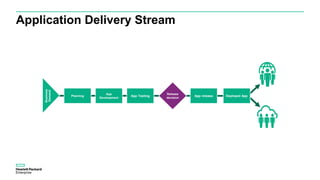
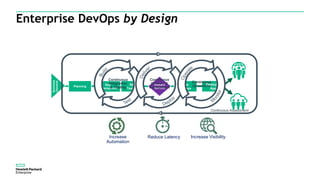
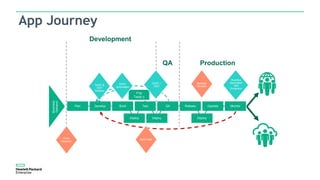
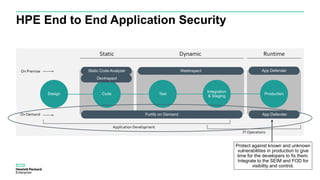
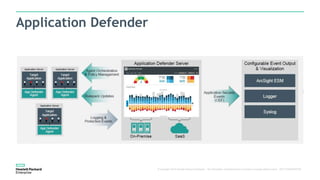
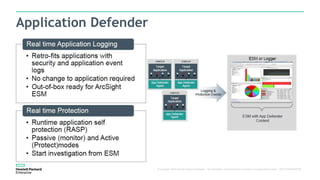
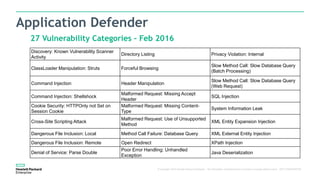
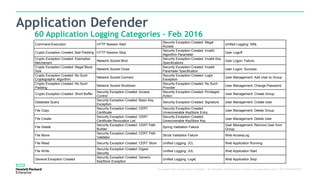
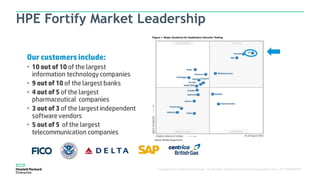
The document discusses Fortify and DevOps for MBFS. It provides an overview of the DevOps lifecycle including planning, development, testing, release decision making, and deploying applications. It then summarizes Hewlett Packard Enterprise's end-to-end application security solution using Fortify on Demand, App Defender, and other tools to integrate security across the development lifecycle and provide protection for applications in production. Charts show the top vulnerability categories and application logging categories detected by Application Defender in February 2016. The document concludes by thanking the readers and providing contact information for Mike Coleman and Thomas Ryan from HPE to answer any questions.