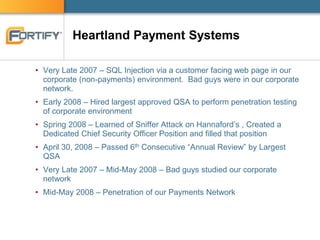
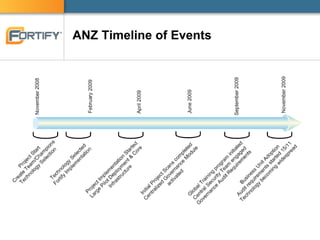
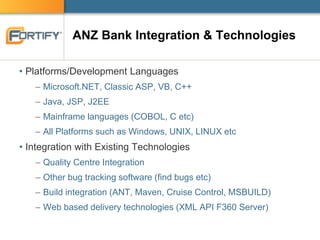
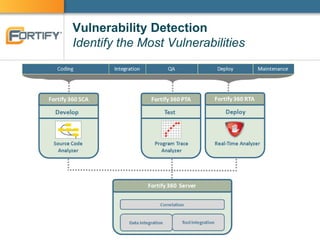
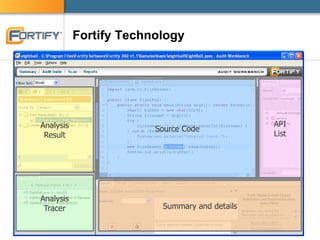
This document discusses enterprise software security and provides examples of how organizations like Accenture and ANZ Bank have implemented software security programs using Fortify's platform. It describes what organizations are protecting (e.g. personal information, financial data), the risks of data breaches, and case studies of past breaches at companies like Heartland Payment Systems. It then outlines how ANZ Bank established a "SAFE Program" using Fortify to integrate security practices into development and meet compliance obligations. The document promotes Fortify as a software security partner that can help achieve compliance, identify vulnerabilities, and effectively manage security programs.