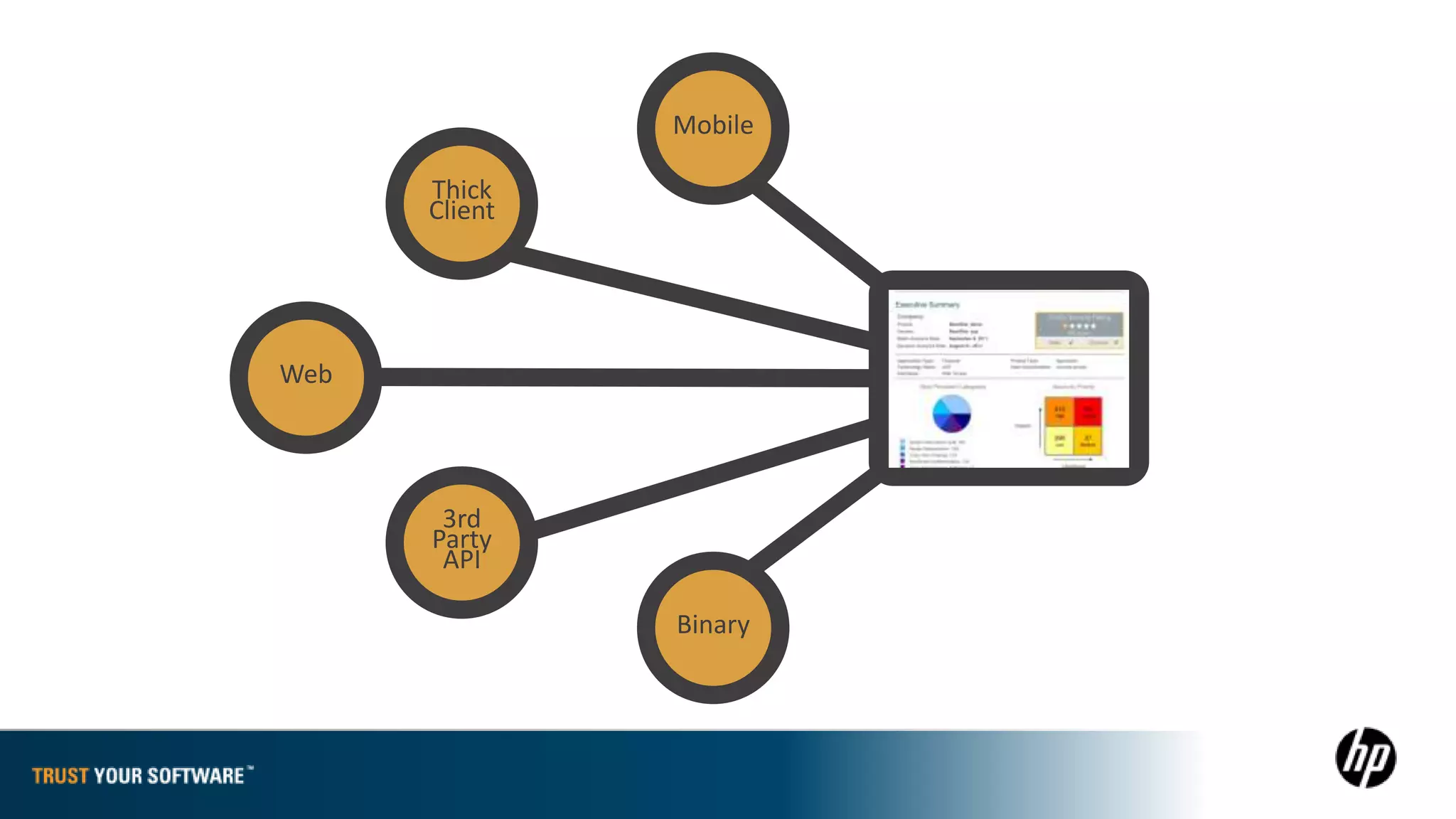
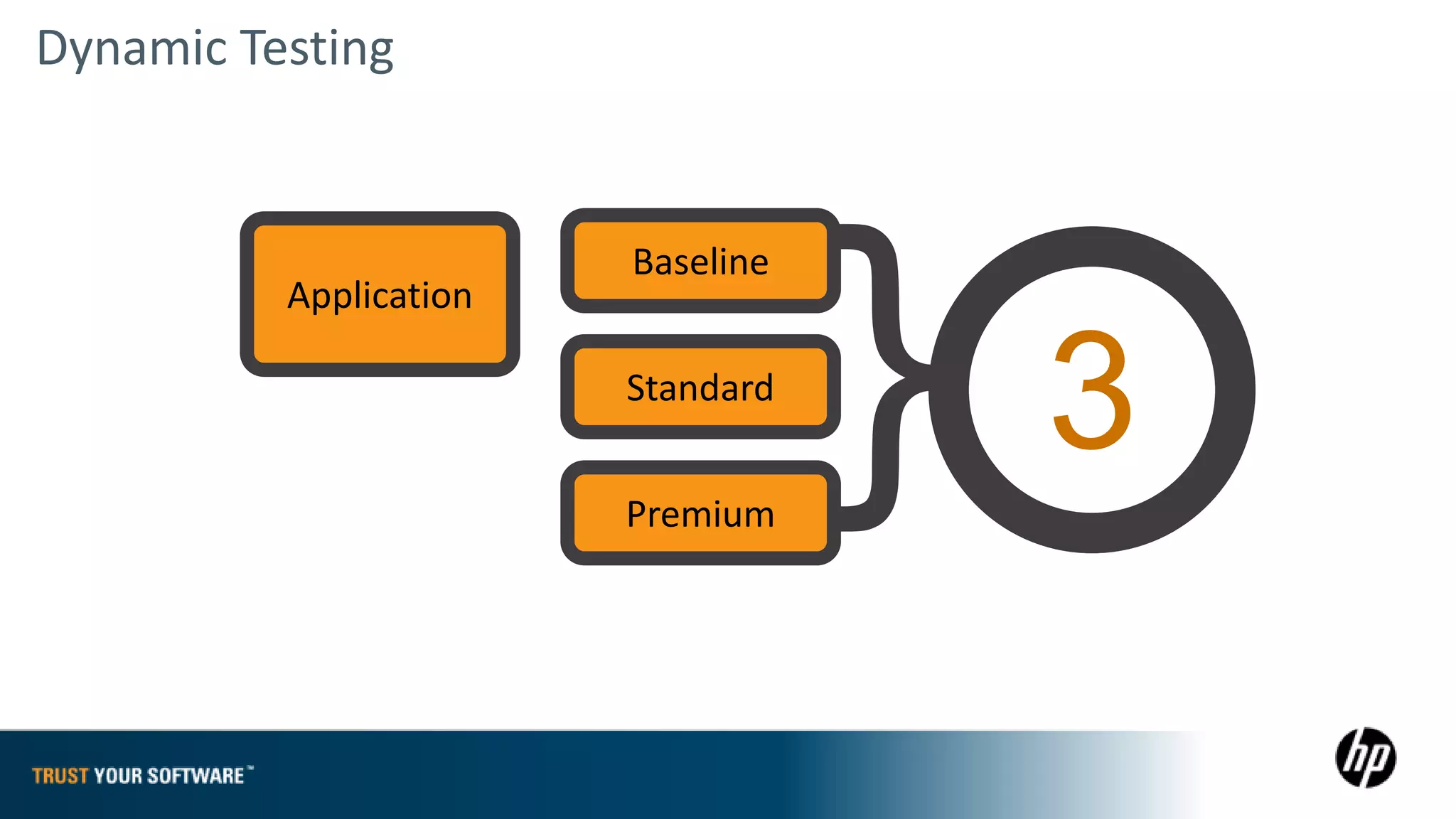
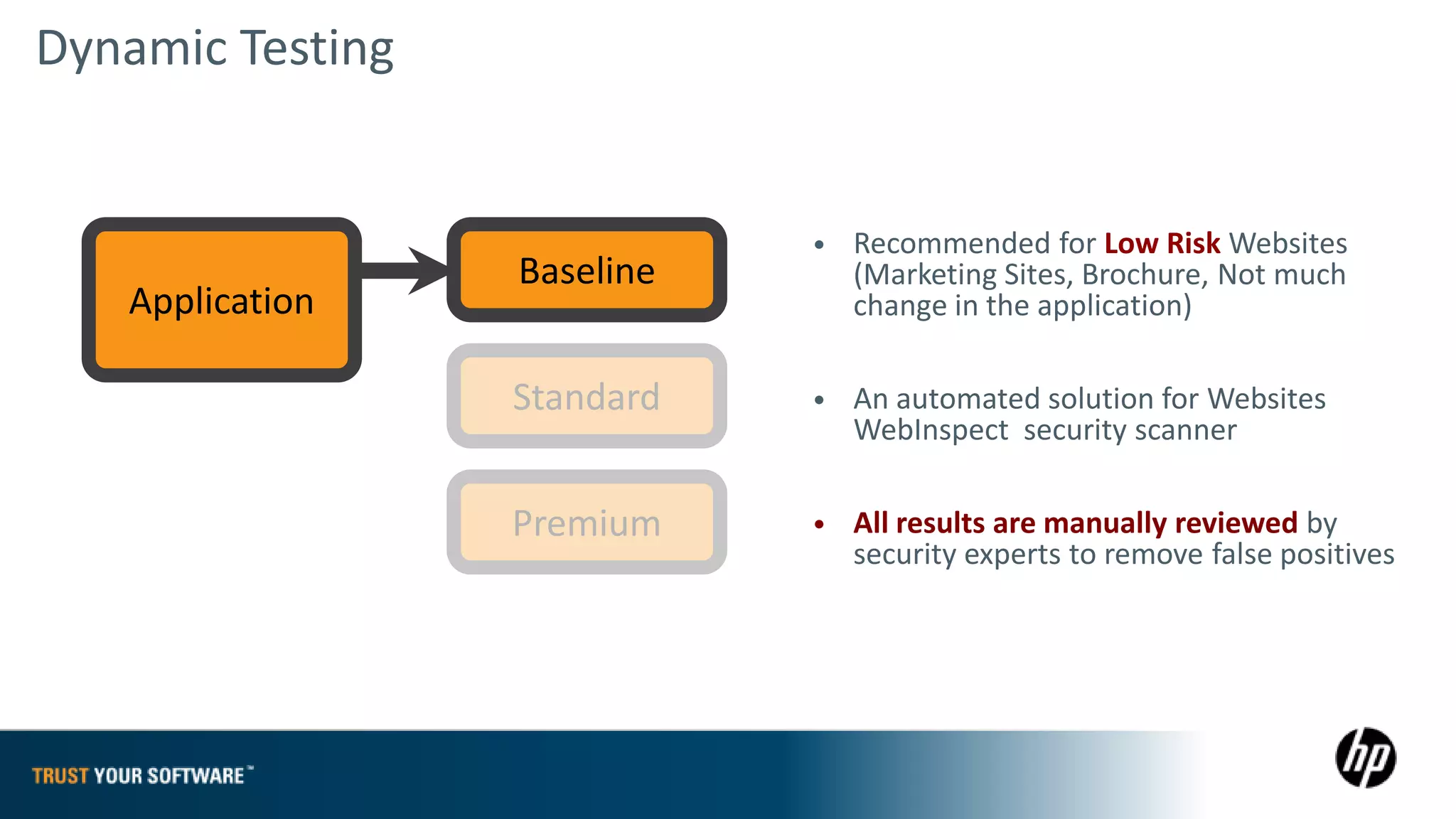
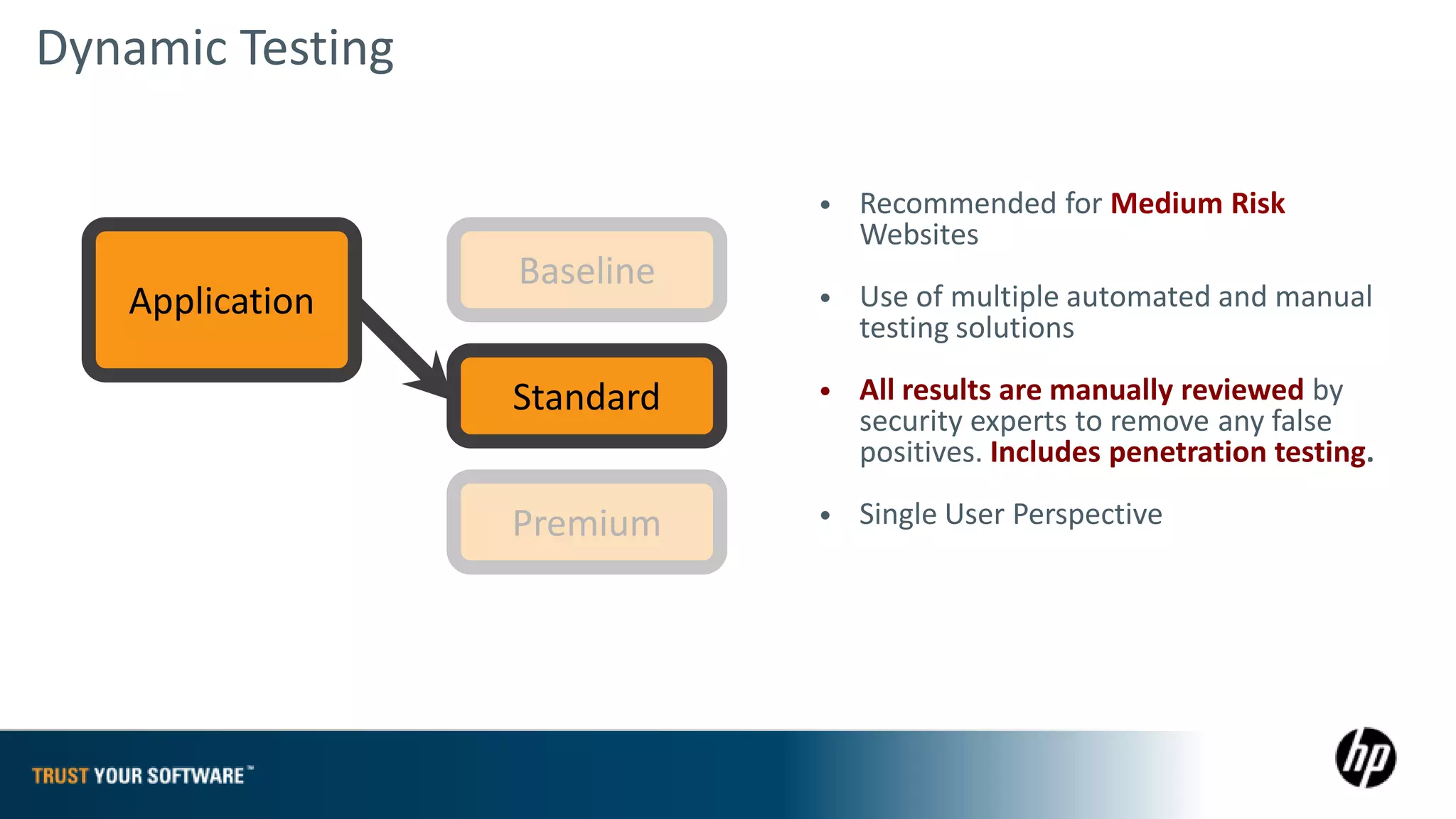
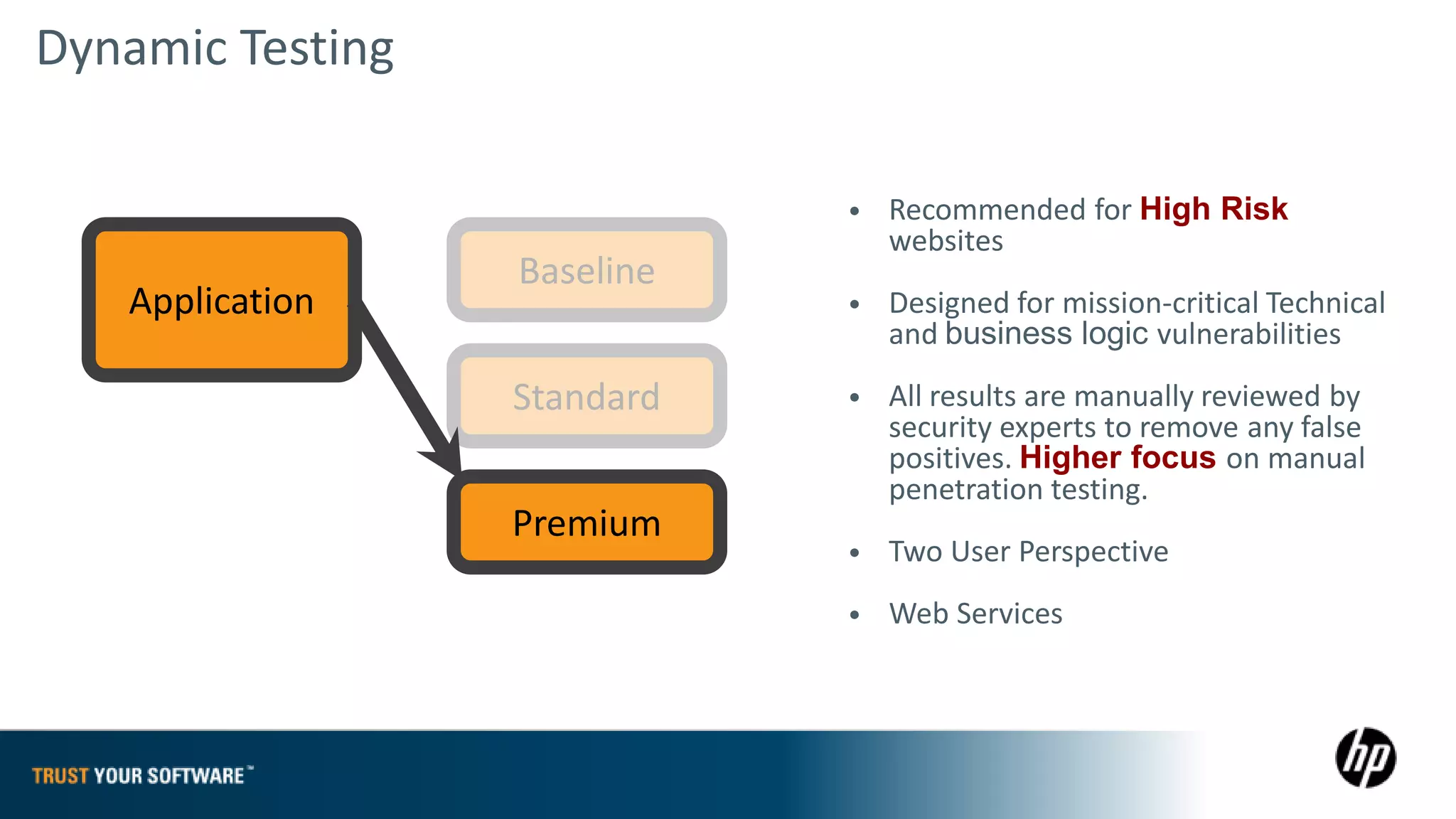
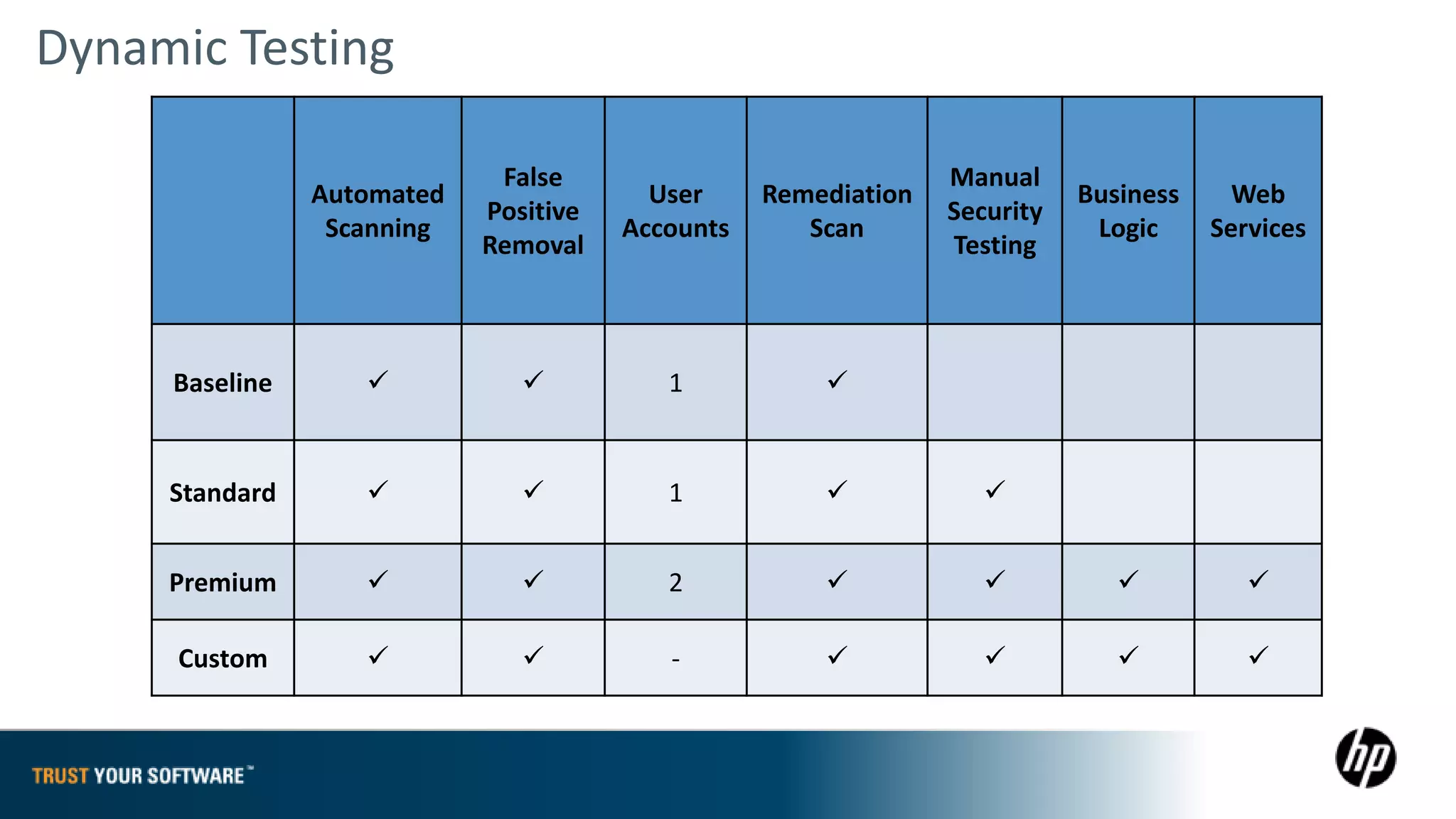
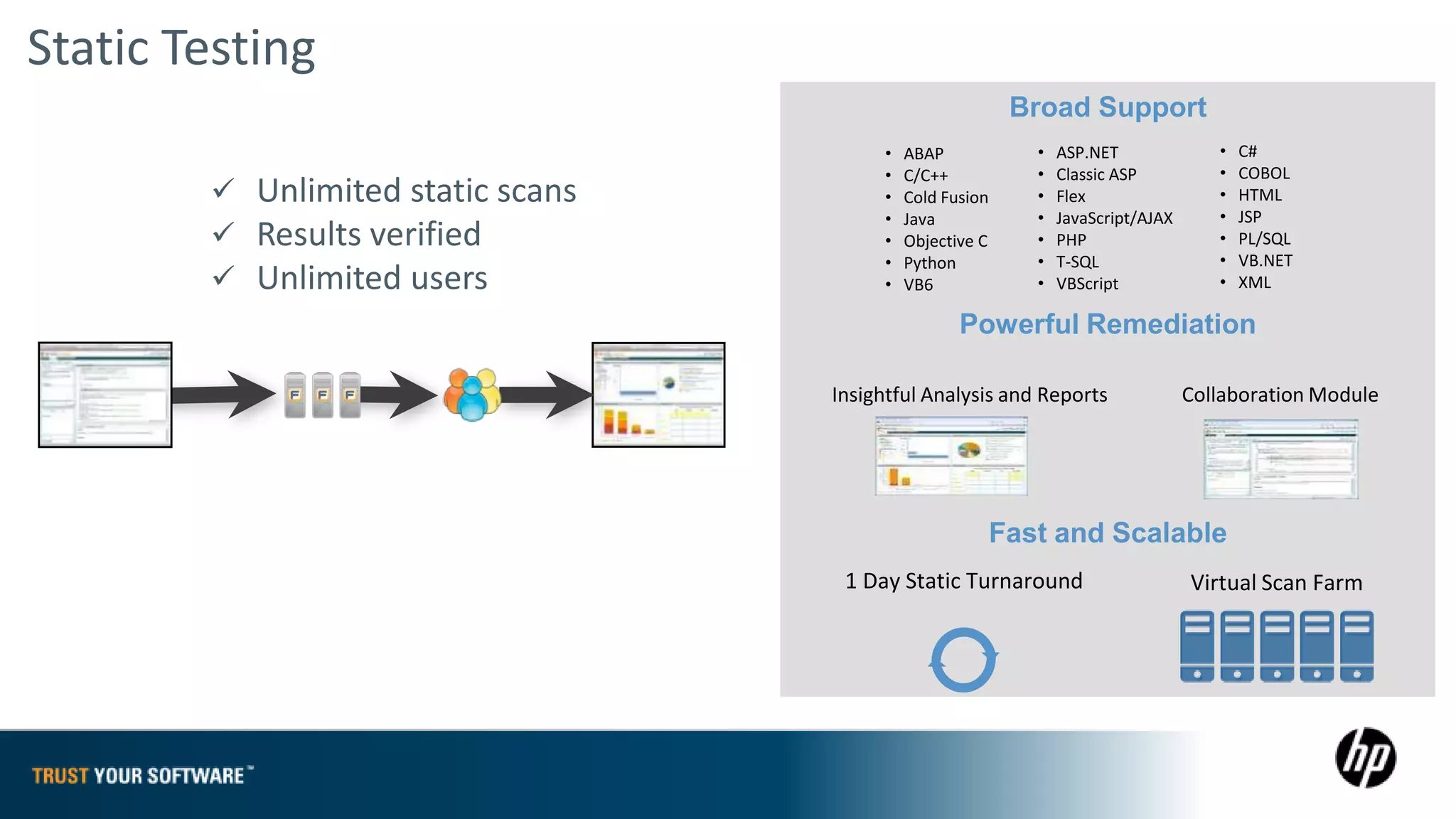
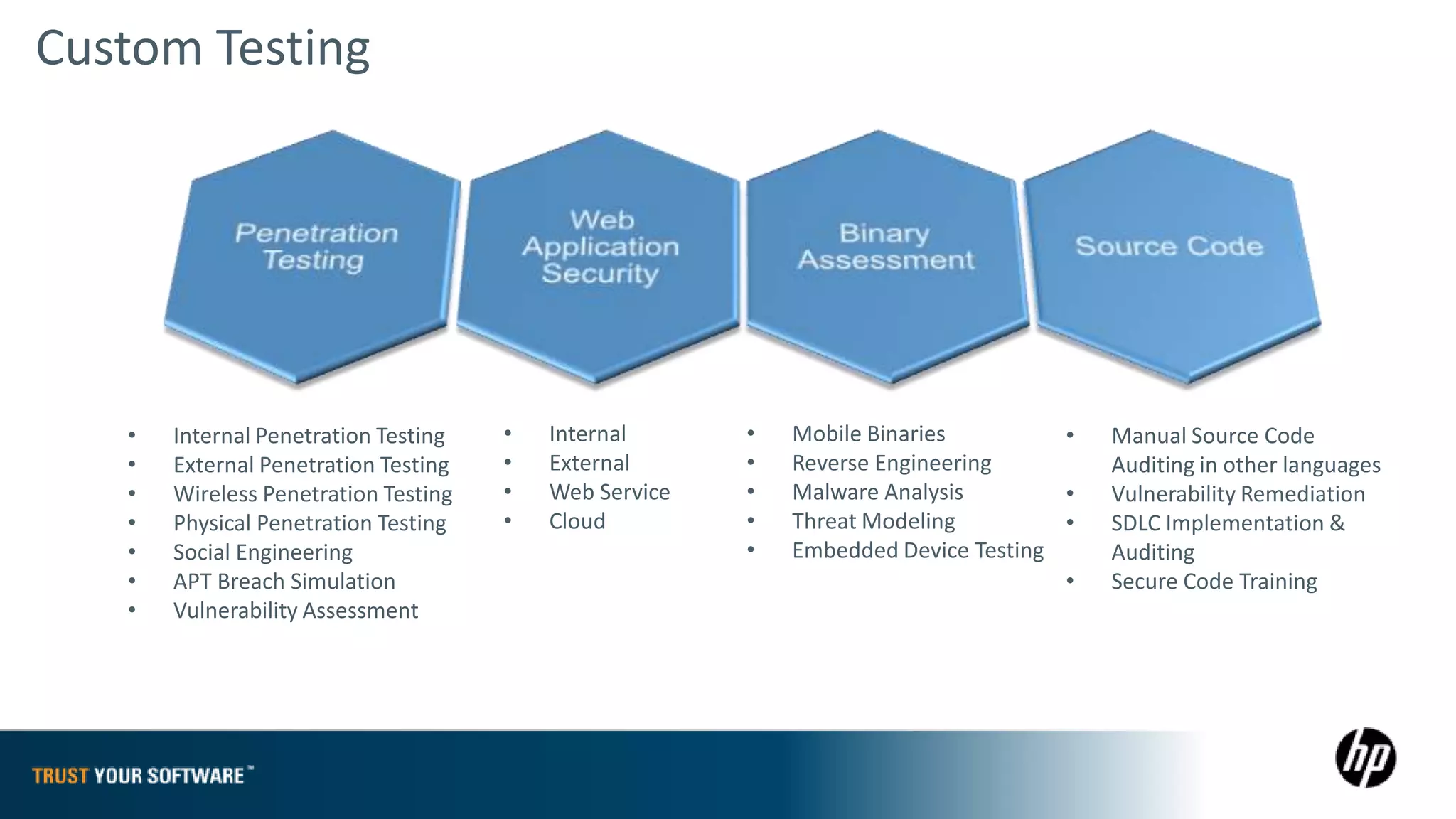
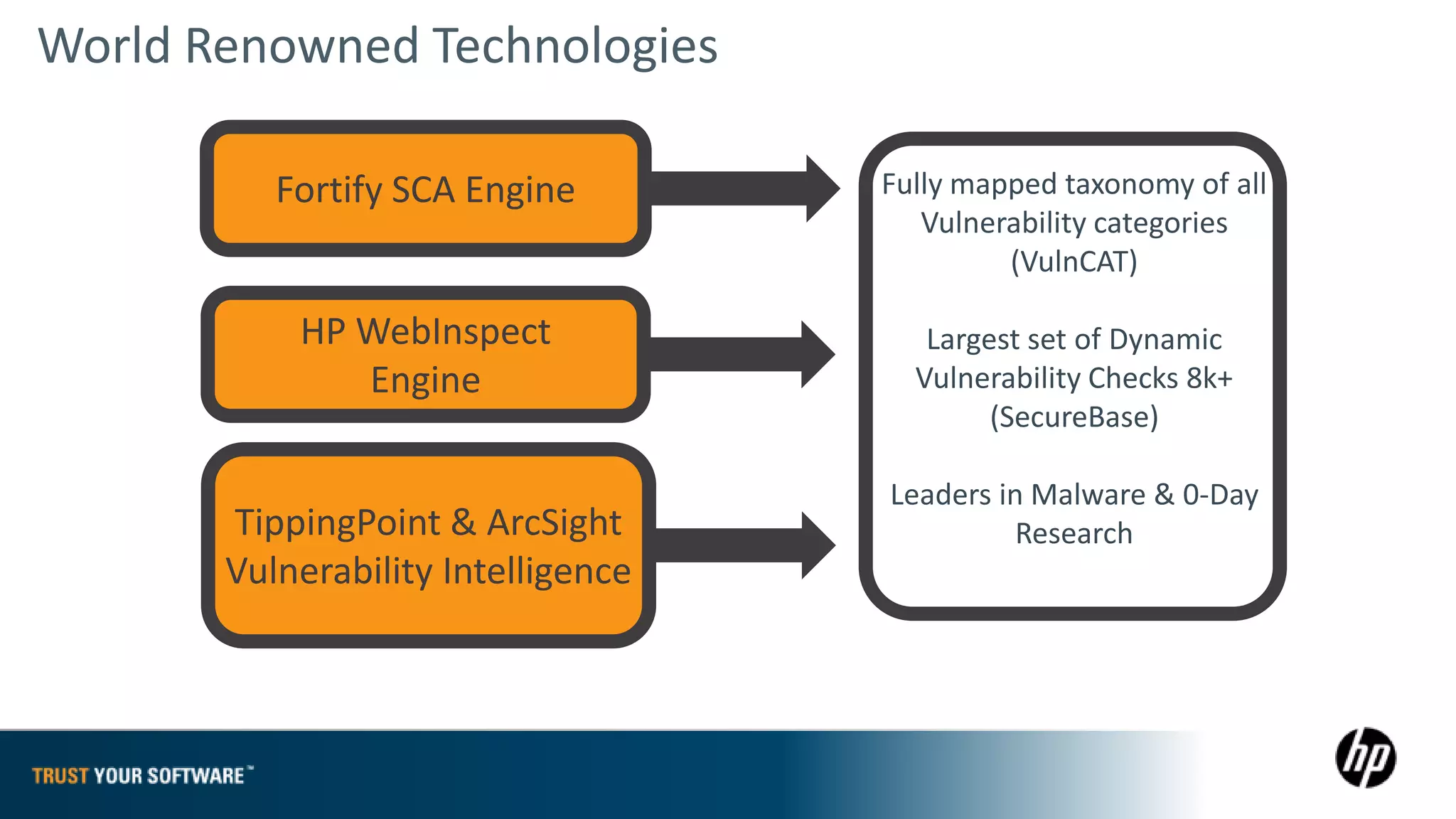
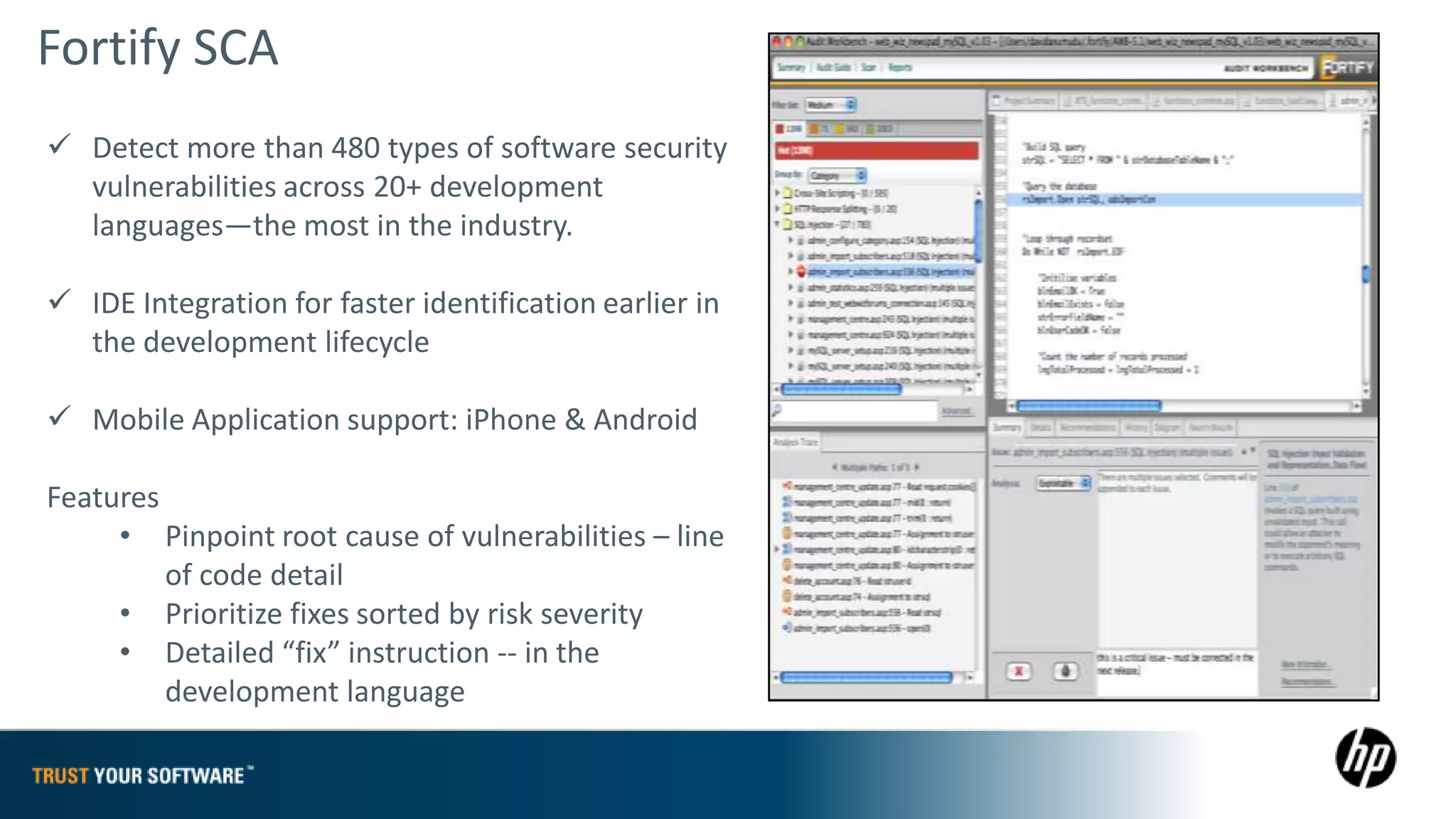
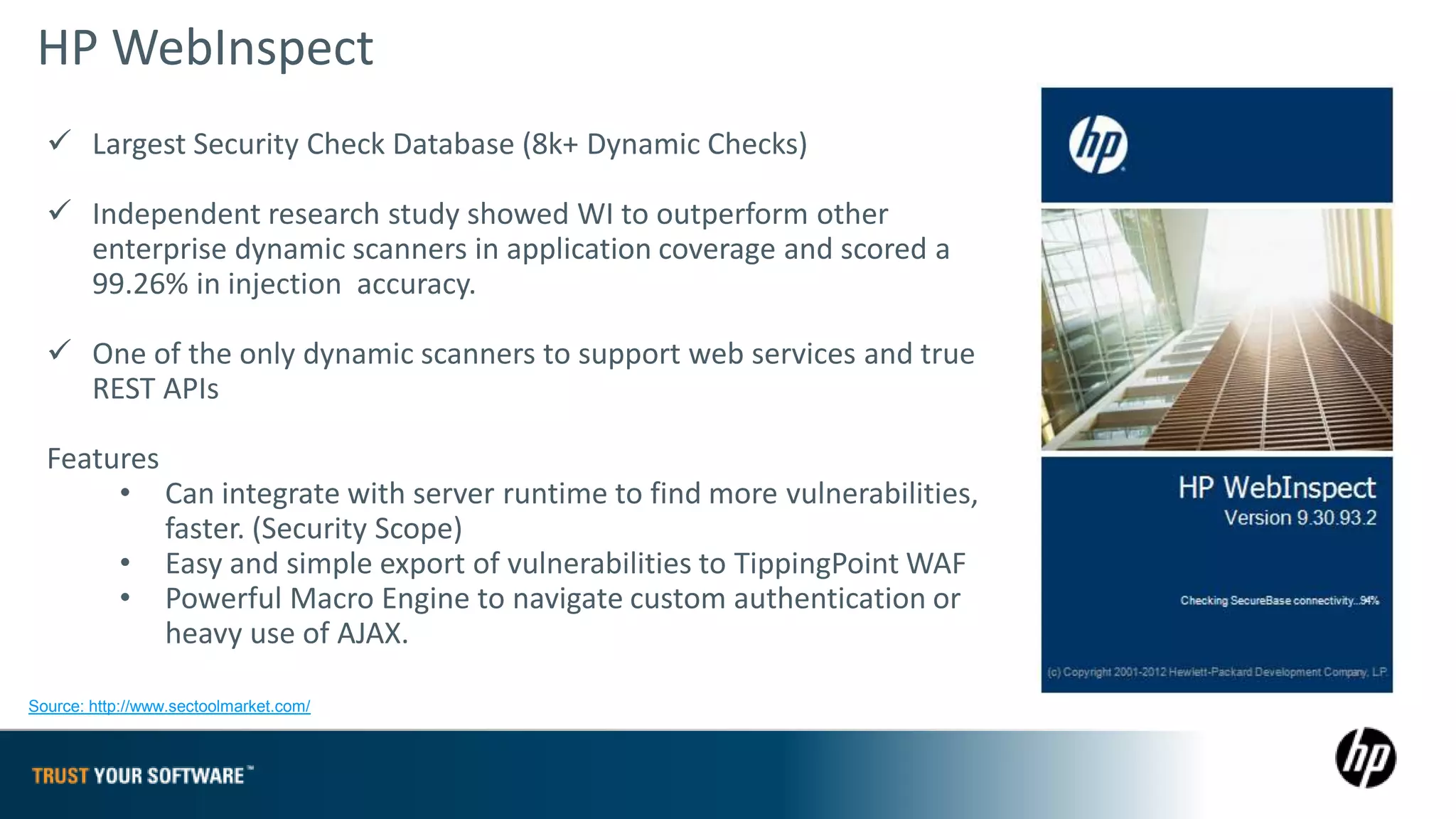
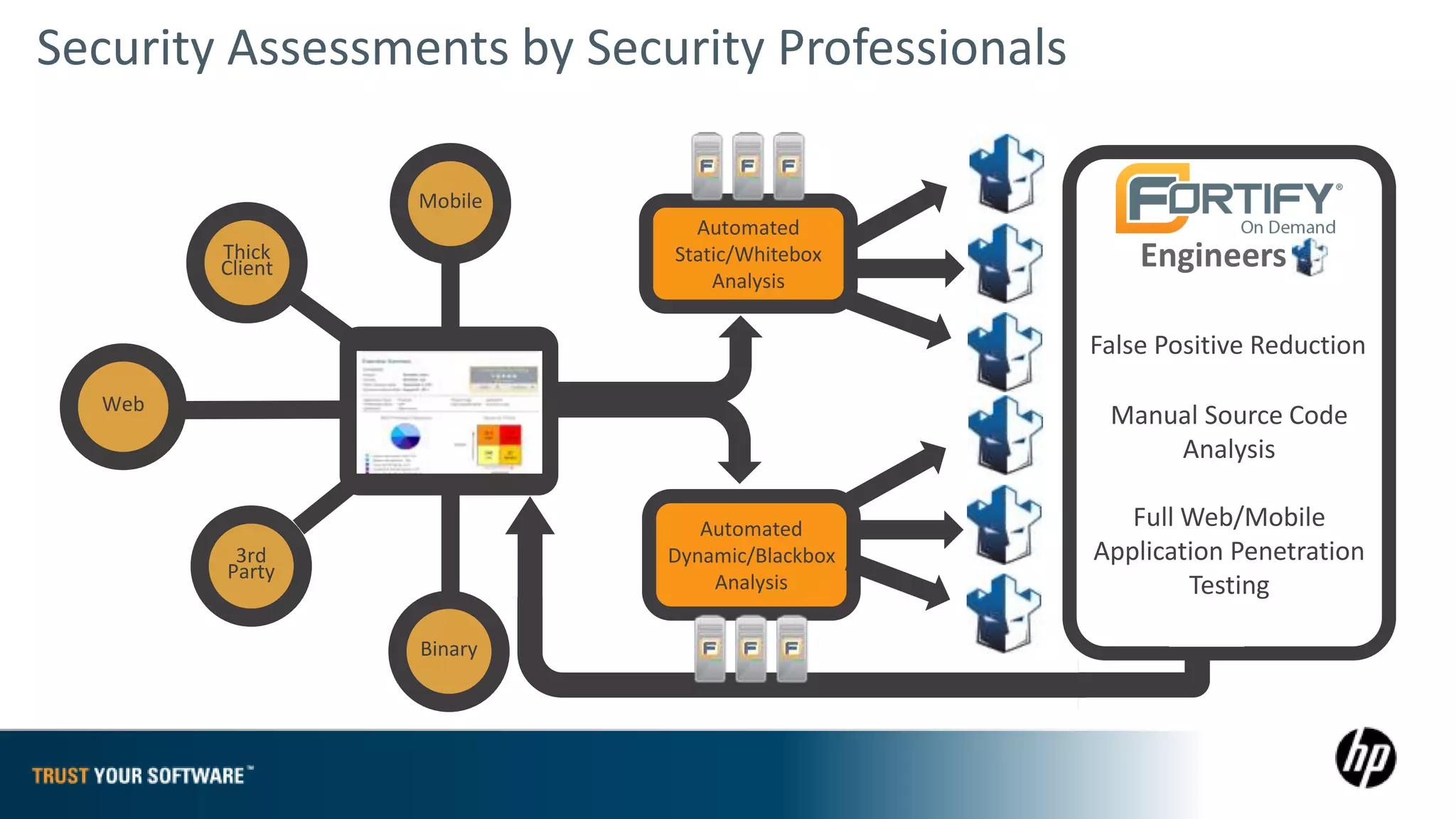
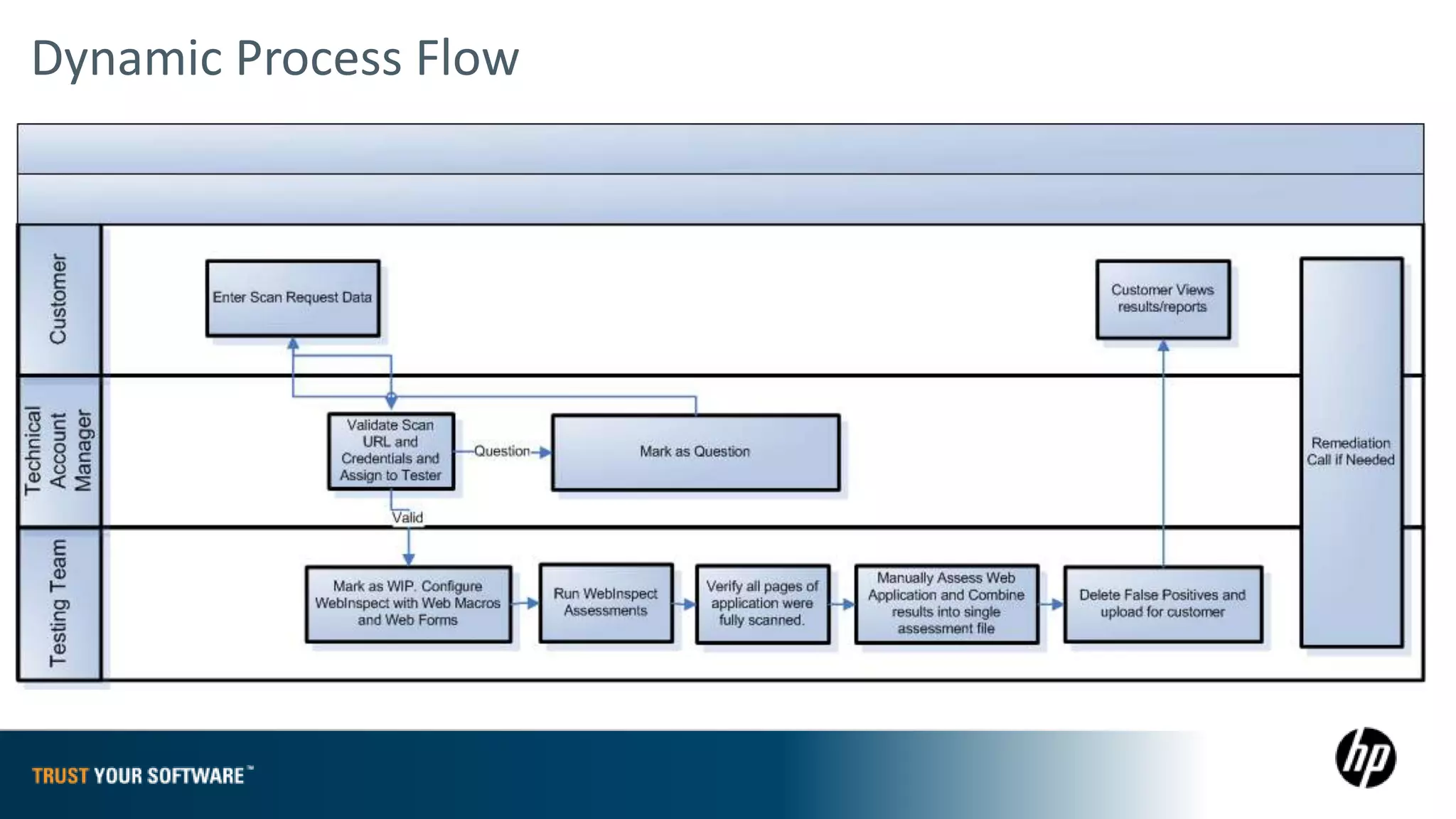
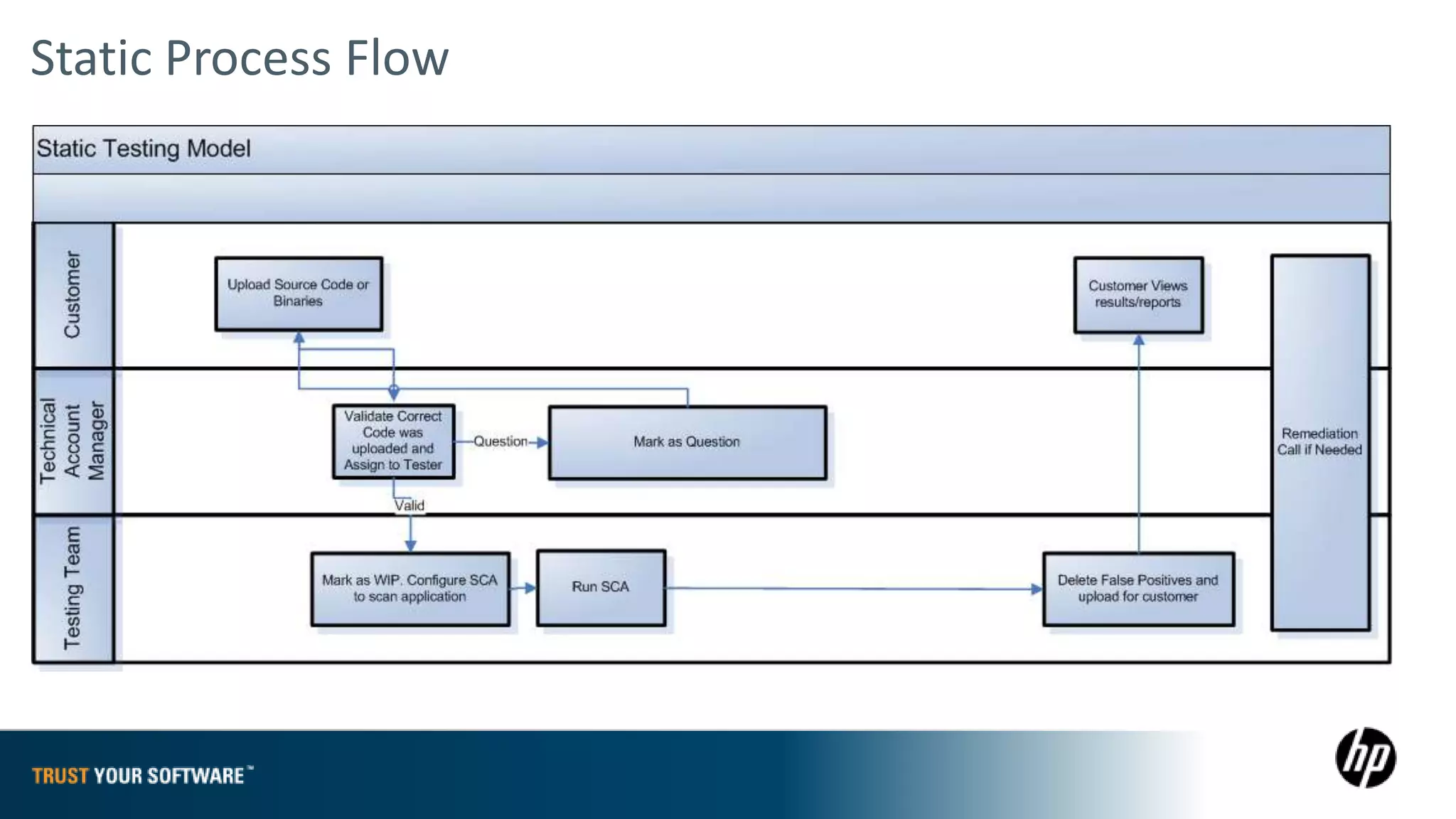
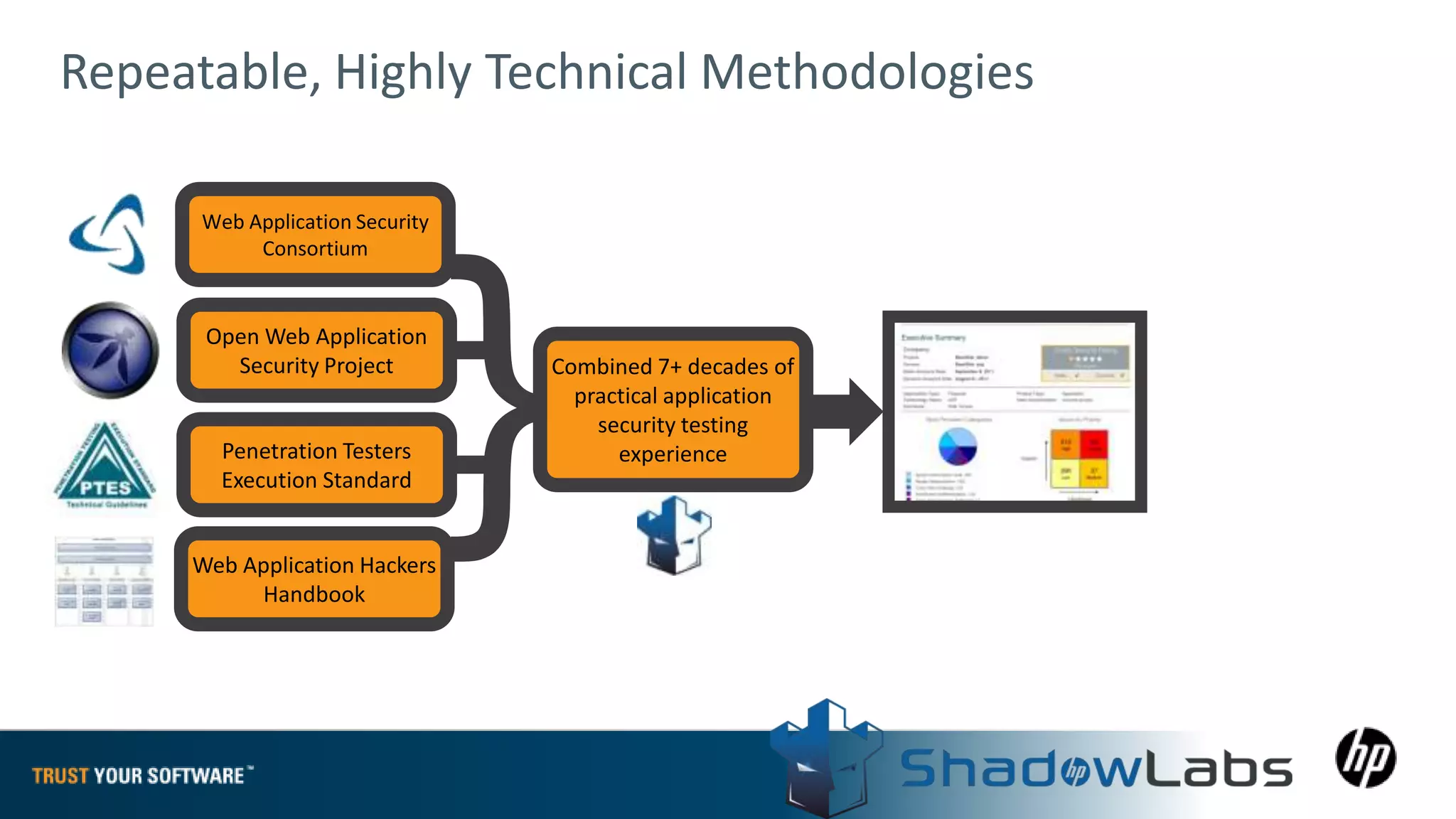
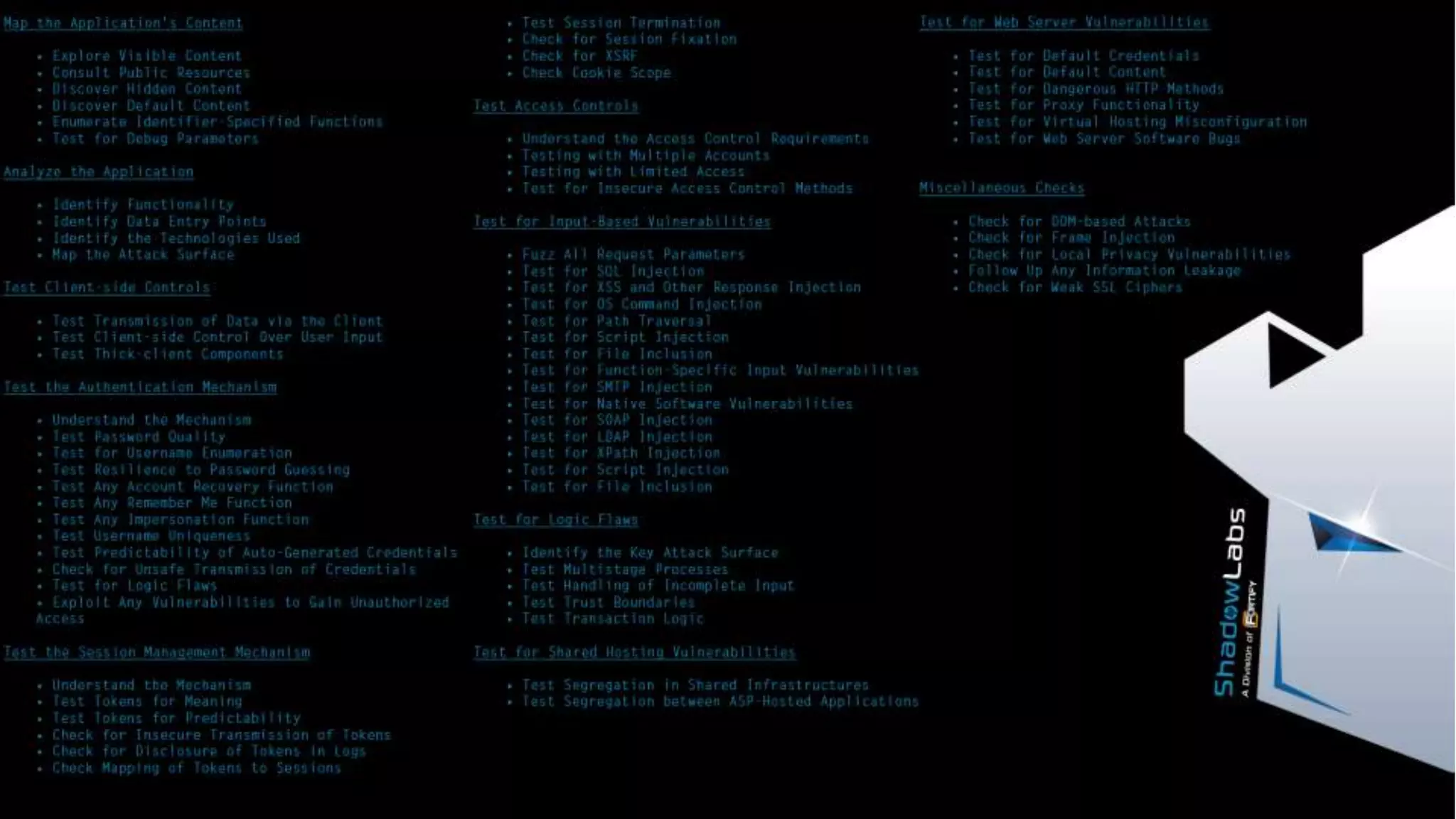
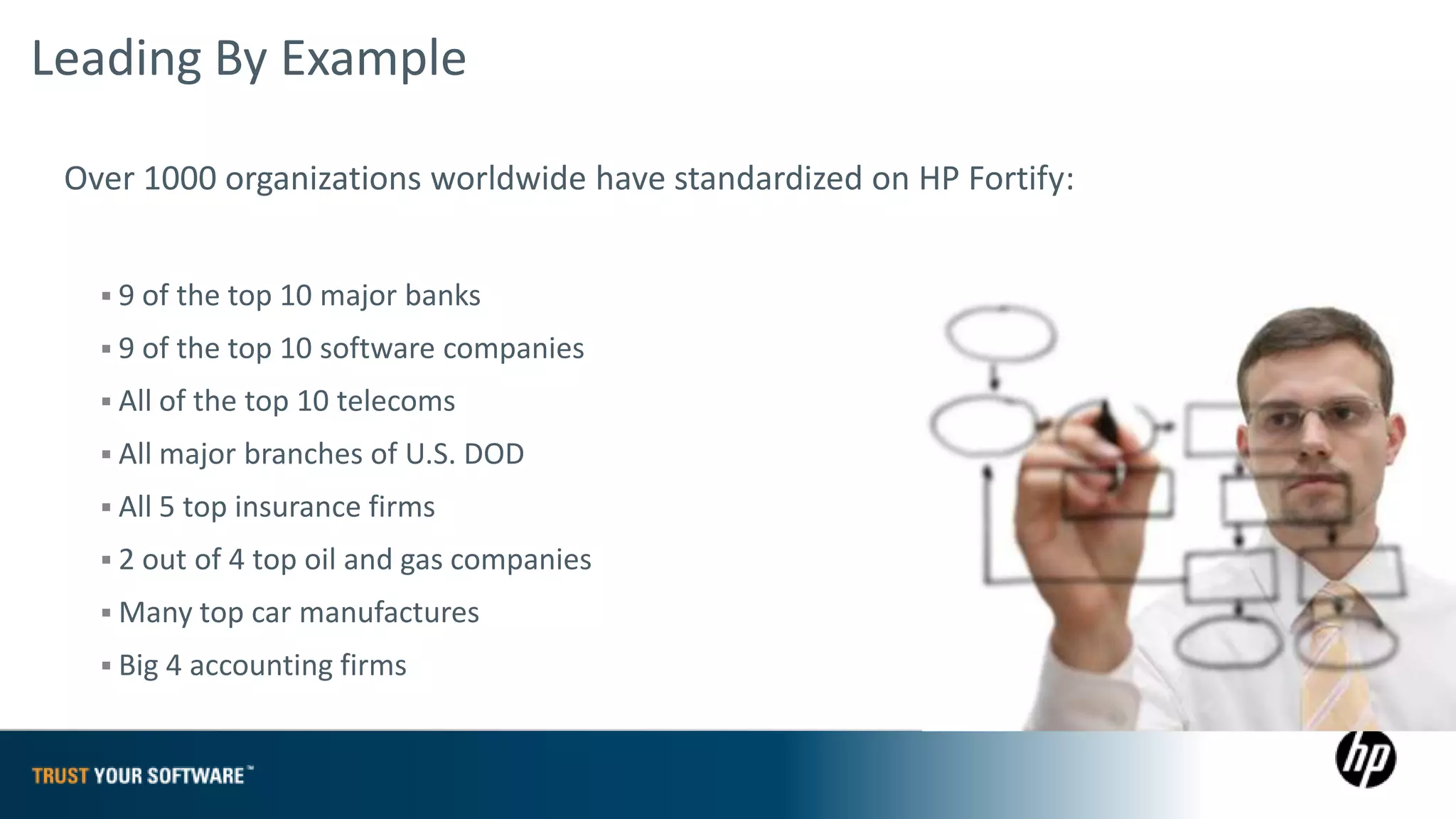
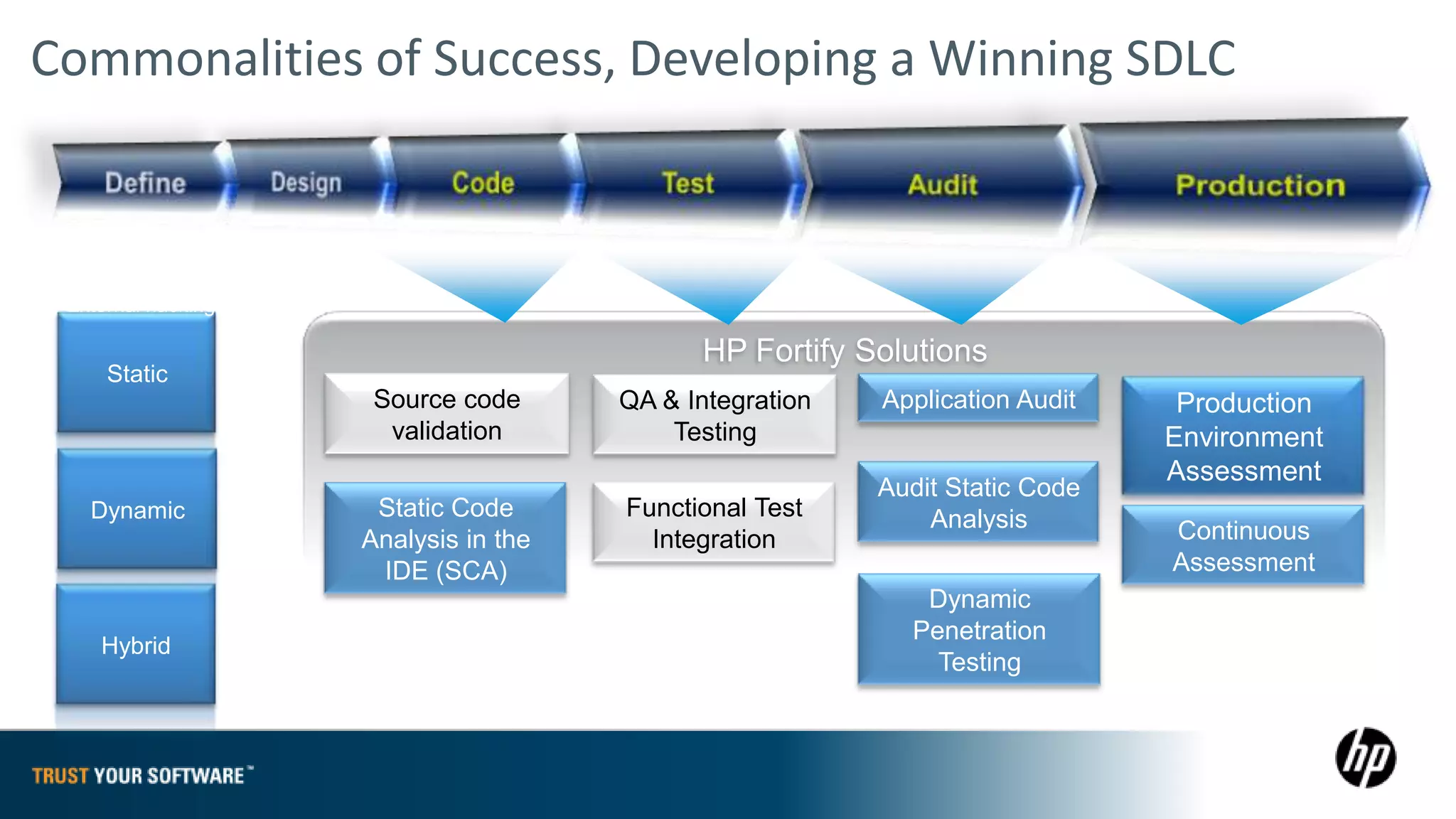
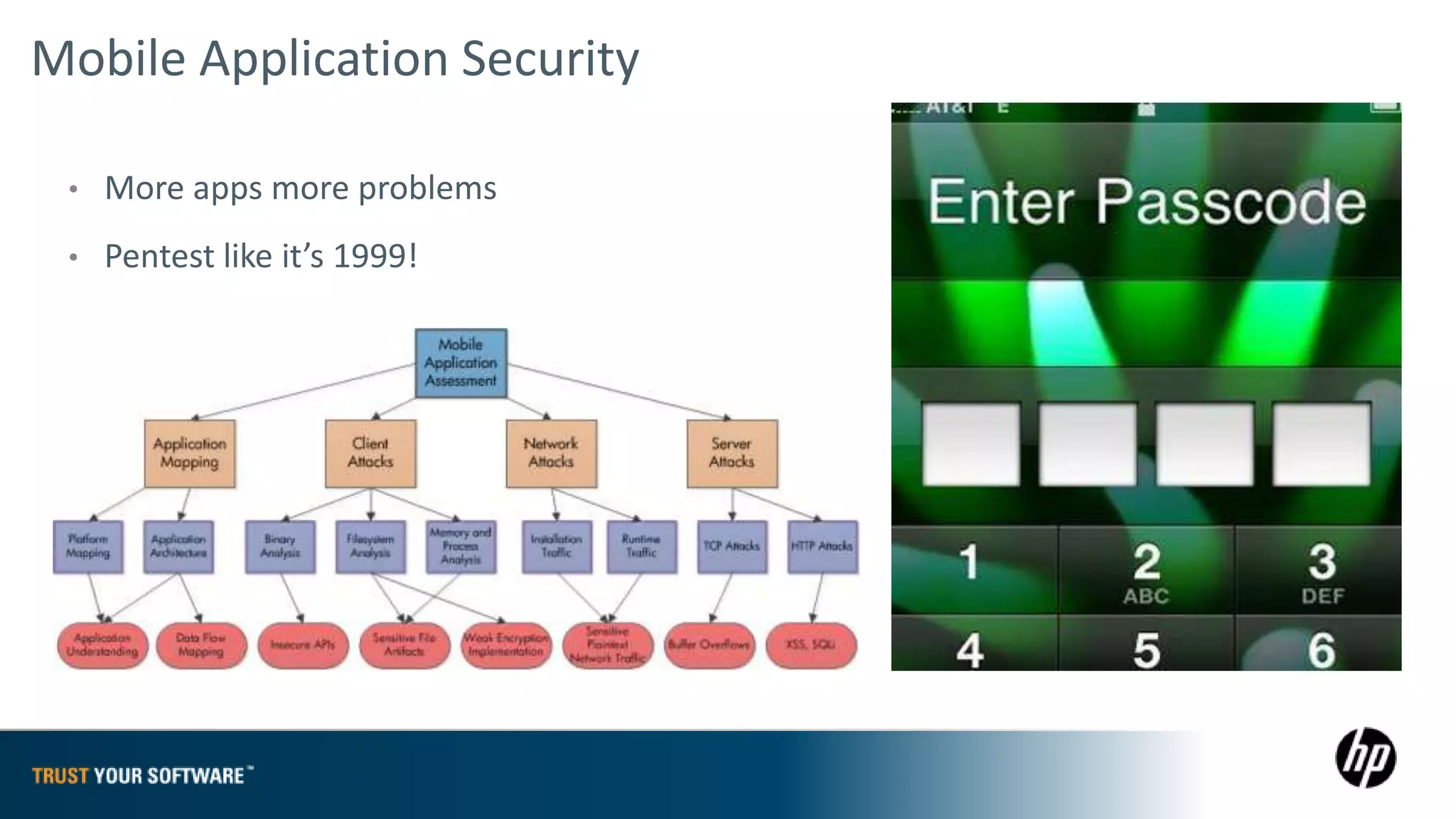
The document provides an overview of Fortify on Demand (FoD) security assessments. It summarizes that FoD offers automated static and dynamic application security testing through their analysis tools and security experts. It provides concise summaries of their baseline, standard, and premium assessment levels that vary in coverage, user accounts tested, and inclusion of manual security testing. The document highlights some customer success stories and commonalities that organizations achieving success have in developing a secure software development lifecycle.