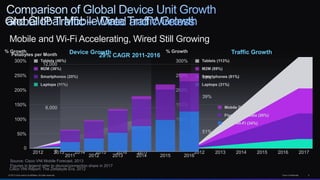
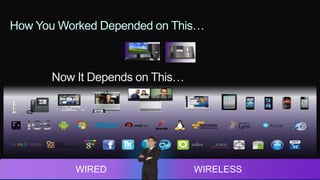
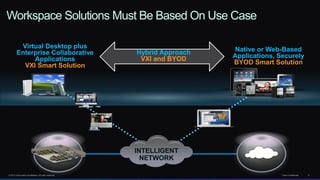
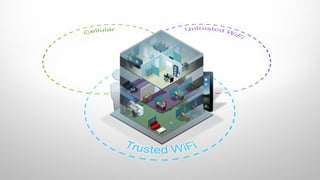
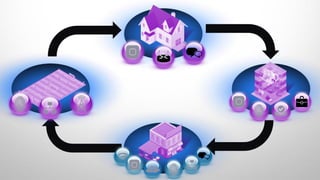
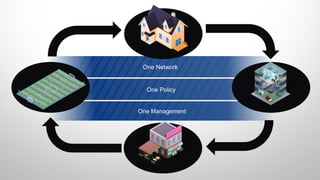
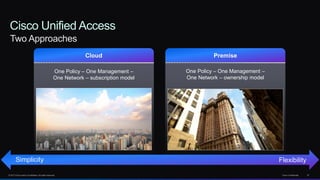
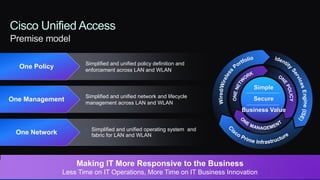
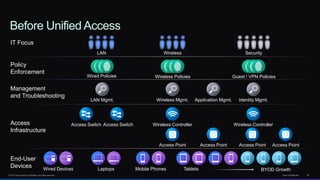
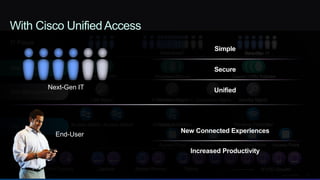
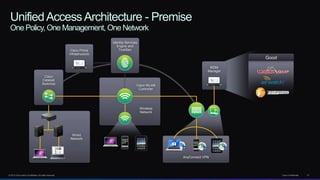
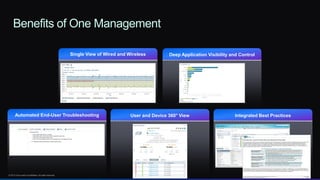
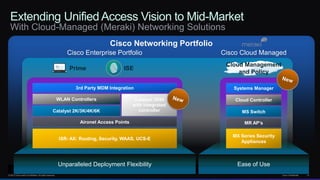
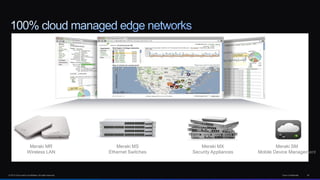
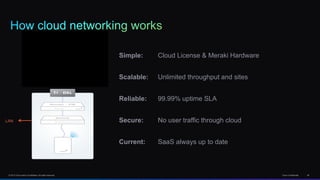
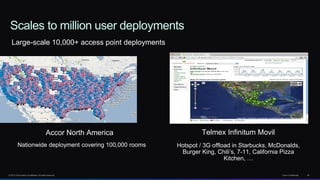
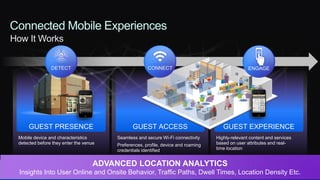
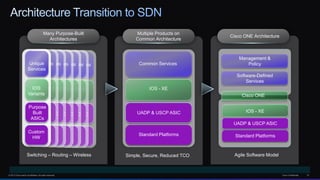
The document discusses Cisco's network vision and trends in enterprise mobility, emphasizing the growing adoption of BYOD (Bring Your Own Device) and cloud networking solutions. It highlights the transformation in workplace environments, driven by a proliferation of devices and the need for secure, seamless connections across various platforms. Cisco's Unified Access approach aims to simplify network management through a unified policy, management system, and infrastructure that caters to increasingly mobile workforces.