Sacon - IoT Forum Fresh Thinking (Arvind Tiwary + Bikash Barai)
•
1 like•2,534 views
The document discusses the formation of an IoT Security Task Force by the IoT Forum and CISO Platform to develop approaches for improving IoT security in India. It proposes a framework called SECURENET that uses principles of fresh thinking to better identify cyber attackers, authorize network access, monitor for anomalies, and allow reactive measures like quarantining threats. The framework also suggests a managed security provider model and exploring legal protocols to enable cross-border cooperation against cyber criminals, drawing from concepts in maritime law. Feedback is sought from stakeholders on the technical, legal and policy approaches proposed.
Report
Share
Report
Share
Download to read offline
Recommended
Moving Beyond Zero Trust

Jonathan Nguyen-Duy, VP, Global Field CISO Team, Fortinet
Security Transformation Summit 2019
SACON - Threat Hunting Workshop (Shomiron Das Gupta)

SACON - Threat Hunting Workshop (Shomiron Das Gupta)
How Zero Trust Makes the Mission Simple & Secure

Dug Song, VP & GM, Cisco & Co-Founder, Duo Security
Zero Trust Security Summit 2020
01.28.2020 International Spy Museum
Debunked: 5 Myths About Zero Trust Security

In 2018, Zero Trust Security gained popularity due to its simplicity and effectiveness. Yet despite a rise in awareness, many organizations still don’t know where to start or are slow to adopt a Zero Trust approach.
The result? Breaches affected as many as 66% of companies just last year. And as hackers become more sophisticated and resourceful, the number of breaches will continue to rise.
Unless organizations adopt Zero Trust Security. In 2019, take some time to assess your company’s risk factors and learn how to implement Zero Trust Security in your organization.
The Internet of Everything is Here

The idea of a more connected world is an exciting prospect. The proliferation of Internet-enabled cars, appliances, medical devices, thermostats, and so on has already changed the way we live and will only continue grow. Unfortunately, these devices are expanding an already large attack surface, and cybercriminals are eager to exploit them.
If we do not prepare for this influx of new, specialized devices on our networks, the Internet of Things (IoT) will leave gaping holes in our cybersecurity practices. But securing these many devices is a daunting task for even the bravest security professional.
Join Keith Wilson of Cisco Security for a webinar to discuss the security challenges related to IoT. Topics covered include:
-Why IoT devices can be difficult to secure
-Industries already affected by this trend such as health care, manufacturing, financial services and retail
-The various approaches to securing these devices
-How you can best keep IoT devices from becoming a security liability
Tenable Solutions for Enterprise Cloud Security

Prezentace z konference Virtualization Forum 2019
Praha, 3.10.2019
Sál B
Recommended
Moving Beyond Zero Trust

Jonathan Nguyen-Duy, VP, Global Field CISO Team, Fortinet
Security Transformation Summit 2019
SACON - Threat Hunting Workshop (Shomiron Das Gupta)

SACON - Threat Hunting Workshop (Shomiron Das Gupta)
How Zero Trust Makes the Mission Simple & Secure

Dug Song, VP & GM, Cisco & Co-Founder, Duo Security
Zero Trust Security Summit 2020
01.28.2020 International Spy Museum
Debunked: 5 Myths About Zero Trust Security

In 2018, Zero Trust Security gained popularity due to its simplicity and effectiveness. Yet despite a rise in awareness, many organizations still don’t know where to start or are slow to adopt a Zero Trust approach.
The result? Breaches affected as many as 66% of companies just last year. And as hackers become more sophisticated and resourceful, the number of breaches will continue to rise.
Unless organizations adopt Zero Trust Security. In 2019, take some time to assess your company’s risk factors and learn how to implement Zero Trust Security in your organization.
The Internet of Everything is Here

The idea of a more connected world is an exciting prospect. The proliferation of Internet-enabled cars, appliances, medical devices, thermostats, and so on has already changed the way we live and will only continue grow. Unfortunately, these devices are expanding an already large attack surface, and cybercriminals are eager to exploit them.
If we do not prepare for this influx of new, specialized devices on our networks, the Internet of Things (IoT) will leave gaping holes in our cybersecurity practices. But securing these many devices is a daunting task for even the bravest security professional.
Join Keith Wilson of Cisco Security for a webinar to discuss the security challenges related to IoT. Topics covered include:
-Why IoT devices can be difficult to secure
-Industries already affected by this trend such as health care, manufacturing, financial services and retail
-The various approaches to securing these devices
-How you can best keep IoT devices from becoming a security liability
Tenable Solutions for Enterprise Cloud Security

Prezentace z konference Virtualization Forum 2019
Praha, 3.10.2019
Sál B
Cisco Security Presentation

As the industry’s first Secure Internet Gateway in the cloud, Cisco Umbrella provides the first line of defense against threats on the internet, protecting all your users within minutes.
Cisco Advanced Malware Protection offers global threat intelligence, advanced sandboxing and real-time malware blocking to prevent breaches while it continuously analyzes file activity across your network, so that you can quickly detect, contain and remove advanced malware.
Presentation of Cisco Security Architecture and Solutions such as Cisco Advanced Malware Protection (AMP) and Cisco Umbrella during Simplex-Cisco Technology Session that took place at the Londa Hotel in Limassol on 14 March 2018.
[Round table] zeroing in on zero trust architecture![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Idea of Zero Trust
Frameworks e.g. NIST framework
Building a Zero Trust Architecture
Building Tech stack for transition to Zero Trust Architecture
Building Tech stack for directly implementing Zero Trust Architecture
Tomorrow Starts Here - Security Everywhere 

Mandar Rege, Security Principal, Cisco Security Solutions presents the evolution of security at Cisco Connect Toronto 2015.
Kaspersky Lab’s Webinar ‘Emerging Threats in the APT World: Predictions for 2...

For several years now, Kaspersky Lab’s Global Research and Analysis Team (GReAT) has been monitoring more than 60 threat actors responsible for cyber-attacks worldwide. By closely observing these organizations, which appear to be fluent in many languages, including Russian, Chinese, German, Spanish, Arabic and Persian, we have put together a list of what seem to be the emerging threats in the APT world. We think these will play an important role in 2015 and deserve special attention. As a participant of the webinar, you will be the first to hear our detailed analysis of the trends.
The webinar was hosted by Costin Raiu, Director of GReAT at Kaspersky Lab, on December 11.
“If we can call 2014‘sophisticated’, then the word for 2015 will be ‘elusive’. We believe that APT groups will evolve to become stealthier and sneakier, in order to better avoid exposure. This year we’ve already discovered APT players using several zero-days, and we’ve observed new persistence and stealth techniques. We have used this to develop and deploy several new defense mechanisms for our users,” comments Costin Raiu.
Listen to the presentation https://kas.pr/aptwebinar
Read the full report https://kas.pr/ksb
Inteligentní ochrana osobních údajů v procesu digitální transformace

Prezentace z konference Virtualization Forum 2019
Praha, 3.10.2019
Sál B
Zero Trust Network Access 

The above PPT explains the working of the ZTNA model for Network Security,
An in depth understanding in the application of the zero-trust security model...

The Goal for this presentation is to define the concepts behind “Zero-Trust” models; demonstrate how the theory has developed and changed over time; present how the Zero-Trust theory is used; provide lessons learned from the challenges and problems implementing “Zero-Trust” concepts; share some use cases demonstrating the success and failures applying the Zero-Trust theory.
Business Continuity and app Security 

Mediante el uso del marco de perímetro digital seguro, implementando un modelo “defense-in depth” se logrará la continuidad de las operaciones para evitar que los ataques maliciosos afecten las mismas y proporcionar resiliencia de acceso seguro y de red durante interrupciones, desastres naturales y calamidades. Esto permite a la fuerza de trabajo reanudar rápidamente industrias de actividades críticas y esenciales.
Web Application Security

Prezentace z konference Virtualization Forum 2019
Praha, 3.10.2019
Sál F5 Networks
Zero trust in a hybrid architecture

Why is there zero trust in a hybrid architecture you may ask? Akamai Technologies' Patrick Sullivan discusses just that and more in his presentation.
What is Zero Trust

Zero Trust: the idea that all access to corporate resources should be restricted until the user has proven their identity and access permissions, and the device has passed a security profile check. A core concept for Okta.
Proteja sus datos en cualquier servicio Cloud y Web de forma unificada

Hoy en día, una media de más de 1000 aplicaciones Cloud se está utilizando en cada empresa, de las cuales, el 98% se categoriza como «Shadow IT», lo cual significa que la dirección IT no las controla.
Además, 80% de la información que sale afuera de las empresas se comparte utilizando aplicaciones Cloud. Y más de 50% del acceso y uso de las aplicaciones Cloud se realiza desde fuera de las redes corporativas.
Zero Trust Framework for Network Security

Forrester Privacy & Security 2018
September 25-26 2018, Washington DC
Zero Trust Cybersecurity for Microsoft Azure Cloud 

Block Armour offers a holistic Zero Trust cybersecurity solution for Microsoft Azure based hybrid IT environments
Kent King - PKI: Do You Know Your Exposure?

Since the introduction of public key cryptography by Diffie and Hellman in 1976, uses and infrastructure have grown in unimaginable ways. The security that has been afforded through Public Key Infrastructure (PKI) is now an integral and essential part of the internet. The proliferation of digital certificates, certificate authorities and PKI implementations creates a large and enticing attack surface. Most businesses rely heavily on PKI for their data security, yet few organizations could tell you how many certificates they have deployed, where they are and their current status. This presentation will discuss a few of the most critical PKI implementations and threats they face today. The talk will conclude with mitigation recommendations and practical ways you can improve the PKI in your organization.
Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)

La seguridad cibernética es claramente un tema de creciente importancia en estos días. La presentación invitará a reflexionar sobre la semántica de las palabras que usamos al hablar sobre seguridad cibernética, y lo guiará a través del mapa de perspectivas y metodologías hacia su propio camino para estar seguros y protegidos en el entorno digital. La charla se ajusta tanto para los líderes empresariales como técnicos.
More Related Content
What's hot
Cisco Security Presentation

As the industry’s first Secure Internet Gateway in the cloud, Cisco Umbrella provides the first line of defense against threats on the internet, protecting all your users within minutes.
Cisco Advanced Malware Protection offers global threat intelligence, advanced sandboxing and real-time malware blocking to prevent breaches while it continuously analyzes file activity across your network, so that you can quickly detect, contain and remove advanced malware.
Presentation of Cisco Security Architecture and Solutions such as Cisco Advanced Malware Protection (AMP) and Cisco Umbrella during Simplex-Cisco Technology Session that took place at the Londa Hotel in Limassol on 14 March 2018.
[Round table] zeroing in on zero trust architecture![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Idea of Zero Trust
Frameworks e.g. NIST framework
Building a Zero Trust Architecture
Building Tech stack for transition to Zero Trust Architecture
Building Tech stack for directly implementing Zero Trust Architecture
Tomorrow Starts Here - Security Everywhere 

Mandar Rege, Security Principal, Cisco Security Solutions presents the evolution of security at Cisco Connect Toronto 2015.
Kaspersky Lab’s Webinar ‘Emerging Threats in the APT World: Predictions for 2...

For several years now, Kaspersky Lab’s Global Research and Analysis Team (GReAT) has been monitoring more than 60 threat actors responsible for cyber-attacks worldwide. By closely observing these organizations, which appear to be fluent in many languages, including Russian, Chinese, German, Spanish, Arabic and Persian, we have put together a list of what seem to be the emerging threats in the APT world. We think these will play an important role in 2015 and deserve special attention. As a participant of the webinar, you will be the first to hear our detailed analysis of the trends.
The webinar was hosted by Costin Raiu, Director of GReAT at Kaspersky Lab, on December 11.
“If we can call 2014‘sophisticated’, then the word for 2015 will be ‘elusive’. We believe that APT groups will evolve to become stealthier and sneakier, in order to better avoid exposure. This year we’ve already discovered APT players using several zero-days, and we’ve observed new persistence and stealth techniques. We have used this to develop and deploy several new defense mechanisms for our users,” comments Costin Raiu.
Listen to the presentation https://kas.pr/aptwebinar
Read the full report https://kas.pr/ksb
Inteligentní ochrana osobních údajů v procesu digitální transformace

Prezentace z konference Virtualization Forum 2019
Praha, 3.10.2019
Sál B
Zero Trust Network Access 

The above PPT explains the working of the ZTNA model for Network Security,
An in depth understanding in the application of the zero-trust security model...

The Goal for this presentation is to define the concepts behind “Zero-Trust” models; demonstrate how the theory has developed and changed over time; present how the Zero-Trust theory is used; provide lessons learned from the challenges and problems implementing “Zero-Trust” concepts; share some use cases demonstrating the success and failures applying the Zero-Trust theory.
Business Continuity and app Security 

Mediante el uso del marco de perímetro digital seguro, implementando un modelo “defense-in depth” se logrará la continuidad de las operaciones para evitar que los ataques maliciosos afecten las mismas y proporcionar resiliencia de acceso seguro y de red durante interrupciones, desastres naturales y calamidades. Esto permite a la fuerza de trabajo reanudar rápidamente industrias de actividades críticas y esenciales.
Web Application Security

Prezentace z konference Virtualization Forum 2019
Praha, 3.10.2019
Sál F5 Networks
Zero trust in a hybrid architecture

Why is there zero trust in a hybrid architecture you may ask? Akamai Technologies' Patrick Sullivan discusses just that and more in his presentation.
What is Zero Trust

Zero Trust: the idea that all access to corporate resources should be restricted until the user has proven their identity and access permissions, and the device has passed a security profile check. A core concept for Okta.
Proteja sus datos en cualquier servicio Cloud y Web de forma unificada

Hoy en día, una media de más de 1000 aplicaciones Cloud se está utilizando en cada empresa, de las cuales, el 98% se categoriza como «Shadow IT», lo cual significa que la dirección IT no las controla.
Además, 80% de la información que sale afuera de las empresas se comparte utilizando aplicaciones Cloud. Y más de 50% del acceso y uso de las aplicaciones Cloud se realiza desde fuera de las redes corporativas.
Zero Trust Framework for Network Security

Forrester Privacy & Security 2018
September 25-26 2018, Washington DC
Zero Trust Cybersecurity for Microsoft Azure Cloud 

Block Armour offers a holistic Zero Trust cybersecurity solution for Microsoft Azure based hybrid IT environments
Kent King - PKI: Do You Know Your Exposure?

Since the introduction of public key cryptography by Diffie and Hellman in 1976, uses and infrastructure have grown in unimaginable ways. The security that has been afforded through Public Key Infrastructure (PKI) is now an integral and essential part of the internet. The proliferation of digital certificates, certificate authorities and PKI implementations creates a large and enticing attack surface. Most businesses rely heavily on PKI for their data security, yet few organizations could tell you how many certificates they have deployed, where they are and their current status. This presentation will discuss a few of the most critical PKI implementations and threats they face today. The talk will conclude with mitigation recommendations and practical ways you can improve the PKI in your organization.
Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)

La seguridad cibernética es claramente un tema de creciente importancia en estos días. La presentación invitará a reflexionar sobre la semántica de las palabras que usamos al hablar sobre seguridad cibernética, y lo guiará a través del mapa de perspectivas y metodologías hacia su propio camino para estar seguros y protegidos en el entorno digital. La charla se ajusta tanto para los líderes empresariales como técnicos.
What's hot (20)
[Round table] zeroing in on zero trust architecture![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Round table] zeroing in on zero trust architecture](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Round table] zeroing in on zero trust architecture
[Cisco Connect 2018 - Vietnam] Brian cotaz cyber security strategy ![[Cisco Connect 2018 - Vietnam] Brian cotaz cyber security strategy](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Cisco Connect 2018 - Vietnam] Brian cotaz cyber security strategy](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Cisco Connect 2018 - Vietnam] Brian cotaz cyber security strategy
Kaspersky Lab’s Webinar ‘Emerging Threats in the APT World: Predictions for 2...

Kaspersky Lab’s Webinar ‘Emerging Threats in the APT World: Predictions for 2...
Inteligentní ochrana osobních údajů v procesu digitální transformace

Inteligentní ochrana osobních údajů v procesu digitální transformace
An in depth understanding in the application of the zero-trust security model...

An in depth understanding in the application of the zero-trust security model...
Proteja sus datos en cualquier servicio Cloud y Web de forma unificada

Proteja sus datos en cualquier servicio Cloud y Web de forma unificada
Zero Trust Cybersecurity for Microsoft Azure Cloud 

Zero Trust Cybersecurity for Microsoft Azure Cloud
Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)

Ciberseguridad: Enemigos o defraudadores (MAGISTRAL)
Viewers also liked
SACON - Mobile App Security (Srinath Venkataramani)

SACON - Mobile App Security (Srinath Venkataramani)
SACON - Incident Response Automation & Orchestration (Amit Modi)

SACON - Incident Response Automation & Orchestration (Amit Modi)
SACON - Security Architecture (Arnab Chattopadhayay)

SACON - Security Architecture (Arnab Chattopadhayay)
SACON - Cyber Risk Assessment Using Bayesian Network (R Venkat)

SACON - Cyber Risk Assessment Using Bayesian Network (R Venkat)
SACON - Cloud Security Architecture (Moshe Ferber)

SACON - Cloud Security Architecture (Moshe Ferber)
SACON - Enterprise Security Architecture (Bikash Barai)

SACON - Enterprise Security Architecture (Bikash Barai)
Viewers also liked (17)
SACON - Mobile App Security (Srinath Venkataramani)

SACON - Mobile App Security (Srinath Venkataramani)
SACON - Incident Response Automation & Orchestration (Amit Modi)

SACON - Incident Response Automation & Orchestration (Amit Modi)
SACON - Security Architecture (Arnab Chattopadhayay)

SACON - Security Architecture (Arnab Chattopadhayay)
SACON - Cyber Risk Assessment Using Bayesian Network (R Venkat)

SACON - Cyber Risk Assessment Using Bayesian Network (R Venkat)
SACON - Cloud Security Architecture (Moshe Ferber)

SACON - Cloud Security Architecture (Moshe Ferber)
SACON - Enterprise Security Architecture (Bikash Barai)

SACON - Enterprise Security Architecture (Bikash Barai)
Similar to Sacon - IoT Forum Fresh Thinking (Arvind Tiwary + Bikash Barai)
IoT security fresh thinking 2017 sep 9

A fresh new way to secure IoTnetworks. Current approaches and NIST Standards may not be sufficient
Achieving Caribbean Cybersecuirty

A look at why Caribbean cyber security is important, Caribbean experiences achieving cyber security, why an effective strategy is critical and the importance of an effective Information Governance strategy.
Internet of Things - Privacy and Security issues

Yesterday Pierluigi Paganini, CISO Bit4Id and founder Security Affairs, presented at the ISACA Roma & OWASP Italy conference the state of the art for the Internet of Things paradigm. The presentation highlights the security and privacy issues for the Internet of Things, a technology that is changing user’s perception of the technology.
All you need to know about SSI for Corporates and IoT – Heather Vescent

https://ssimeetup.org/gaps-corporate-iot-identity-heather-vescent-webinar-35/
Heather Vescent, the owner of The Purple Tornado a foresight and strategic intelligence consultancy, explains how Digital identity gaps in Corporate and IoT Identity can be solved from an NPE (non-person entity) point of view. The webinar will answer: What is an NPE? How is an NPE both different and similar to human identity? What is the relationship humans have with NPEs? How is NPE identity more complex than the identity we know today? What considerations do we need to make when developing identity solutions for the future?
The webinar defines a taxonomy for Non-Person Entities (NPEs), defines the relationships NPEs have with humans and each other, and identifies 11 market gaps in today’s technology solutions, that have the potential to be solved using decentralized identity technology. Industry-wide solutions must be forged collaboratively in order to address a broad set of digital identity and data privacy problems.
This webinar shares research funded by the Department of Homeland Security Science & Technology, Cybersecurity directorate by The Purple Tornado, with Heather Vescent as the Principal Investigator. Vescent has delivered research insights to governments and corporations in digital identity, military learning, payments, transactions, and new economic models. She is the writer/producer of 14 documentaries and short films about future technology. Her clients include US & UK governments, SWIFT, CitiVentures, Disney, IEEE, mid-size companies and start-ups. Her research has been covered in the New York Times, CNN, American Banker, CNBC, Fox, and the Atlantic. She is an author of the Cyber Attack Survival Manual, published by Weldon-Owen. Her work has won multiple awards from the Association of Professional Futurists.
Fintech & blockchain technology 06.12.2021

Self study into cryptocurrency, blockchain technology and Finicial technology.
The Realm Of Digital Forensics

26th March 2009, The Realm of Digital Forensics, Educational Seminar, ISACA Malta
BitGo Presents Multi-Sig Bitcoin Security at Inside Bitcoins NYC

How to Stop Bitcoin Theft:
Multi-Sig Wallets Make Bitcoin Secure and Useful for New Industries
Internet of things, New Challenges in Cyber Crime

Dr. Murray presented current issues with IoT technologies at the Information Systems Security Association (ISSA). The ISSA Colorado Springs Chapter - Cyber Focus Day on Wednesday, March 25, 2015 at the University of Colorado Colorado Springs (UCCS). The theme for CFD 2015 was “Cybercrime”.
Cyber Security College Workshop

Cyber Security is: “Protection of information systems against unauthorized access to or modification of information, whether in storage, processing or transit, and against the denial of service to authorized users, including those measures necessary to detect, document, and counter such threats.”
Axxera End Point Security Protection

The Best Online Security Service for
CIM – Central Management
Log Monitoring
Intrusion Detection Systems
Firewall Monitoring System
Host based IDSs
Vulnerability Scanning
Evidence Retention
CIM Intelligence
A must to see for all,......!!!
Brian Isle: The Internet of Things: Manufacturing Panacea - or - Hacker's Dream?

The Internet of Things (IoT) has the potential to drive new innovation in products, services, and improve "how things are done" in manufacturing. However IoT also brings-to-light safety and security issues when purpose-built computing and network devices are exposed to the internet. This session will review case studies of IoT enabled exploits, explore some of the underlying cause of the vulnerabilities, and briefly review of steps vendors and end-users are taking to mitigate the risk.
From the 2014 Taking Shape Summit: The Internet of Things & the Future of Manufacturing.
AUTM_WRM_Blockchain FINAL.pptx

How not to get blocked out from blockchain?
Over the last decade there has been enormous pressure on tech transfer offices (TTOs) to perform in the traditional metrics such as licenses and revenues generated without much increase in the budget. Blockchain as a tool is slowly being adopted by mainstream businesses but universities have not yet joined that bandwagon. Blockchain in IP transactions are probably the next generation technology wave which will likely take over the world of IP. With the recent announcement of IBM to play a major role in tracking patents with NFTs, the major players are looking at adopting new ways for transacting IP. Should TTOs adopt blockchain for managing licensing and compliance of patents or know-how? Will this be the new way of licensing and monetization? Will your next licensee pay with bitcoins? All of these questions will be addressed by experts in the field of transactions, IP markets, compliance and licensing.
The Legal Case for Cybersecurity - SecureWorld Denver 2017 (Lunch Keynote)

Cybersecurity & Data Privacy Attorney Shawn Tuma presents the lunch keynote on the Legal Case for Cybersecurity at SecureWorld-Denver in 2017.
Similar to Sacon - IoT Forum Fresh Thinking (Arvind Tiwary + Bikash Barai) (20)
All you need to know about SSI for Corporates and IoT – Heather Vescent

All you need to know about SSI for Corporates and IoT – Heather Vescent
BitGo Presents Multi-Sig Bitcoin Security at Inside Bitcoins NYC

BitGo Presents Multi-Sig Bitcoin Security at Inside Bitcoins NYC
Noah Maina: Computer Emergency Response Team (CERT)

Noah Maina: Computer Emergency Response Team (CERT)
Brian Isle: The Internet of Things: Manufacturing Panacea - or - Hacker's Dream?

Brian Isle: The Internet of Things: Manufacturing Panacea - or - Hacker's Dream?
The Legal Case for Cybersecurity - SecureWorld Denver 2017 (Lunch Keynote)

The Legal Case for Cybersecurity - SecureWorld Denver 2017 (Lunch Keynote)
More from Priyanka Aash
Digital Personal Data Protection (DPDP) Practical Approach For CISOs

Key Discussion Pointers:
1. Introduction to Data Privacy
- What is data privacy
- Privacy laws around the globe
- DPDPA Journey
2. Understanding the New Indian DPDPA 2023
- Objectives
- Principles of DPDPA
- Applicability
- Rights & Duties of Individuals
- Principals
- Legal implications/penalties
3. A practical approach to DPDPA compliance
- Personal data Inventory
- DPIA
- Risk treatment
Verizon Breach Investigation Report (VBIR).pdf

Annual report by Verizon, analyzing cybersecurity incidents
Cloud attack vectors_Moshe.pdf

It covers popular IaaS/PaaS attack vectors, list them, and map to other relevant projects such as STRIDE & MITRE. Security professionals can better understand what are the common attack vectors that are utilized in attacks, examples for previous events, and where they should focus their controls and security efforts.
Stories From The Web 3 Battlefield

Discuss Security Incidents & Business Use Case, Understanding Web 3 Pros
and Web 3 Cons. Prevention mechanism and how to make sure that it doesn’t happen to you?
Lessons Learned From Ransomware Attacks

Importance of learning from the experience and continually improving security measures to stay ahead of evolving threats
Part of chennai chapter
Emerging New Threats And Top CISO Priorities In 2022 (Chennai)

Round Table Discussion On "Emerging New Threats And Top CISO Priorities In 2022"_ Chennai
Date - 6 September, 2022
Emerging New Threats And Top CISO Priorities In 2022 (Mumbai)

Round Table Discussion On "Emerging New Threats And Top CISO Priorities In 2022"_ Mumbai
Date - 14 September, 2022
Emerging New Threats And Top CISO Priorities in 2022 (Bangalore)

Round Table Discussion On "Emerging New Threats And Top CISO Priorities In 2022"_ Bangalore
Date - 28 September, 2022. Decision Makers of different organizations joined this discussion and spoke on New Threats & Top CISO Priorities
Cloud Security: Limitations of Cloud Security Groups and Flow Logs

Cloud Security Groups are the firewalls of the cloud. They are built-in and provide basic access control functionality as part of the shared responsibility model. However, Cloud Security Groups do not provide the same protection or functionality that enterprises have come to expect with on-premises deployments. In this talk we will discuss the top cloud risks in 2020, why perimeters are a concept of the past and how in the world of no perimitiers do Cloud Security groups, the "Cloud FIrewalls", fit it. We will practically explore Cloud Security Group limitations across different cloud setups from a single vNet to multi-cloud
Cyber Security Governance

Most organizations have good enterprise-level security policies that define their approach to maintaining, improving, and securing their information and information systems. However, once the policies are signed by senior leadership and distributed throughout the organization, significant cybersecurity governance challenges remain. In this workshop I will explain the transforming organizational security to strengthen defenses and integrate cybersecurity with the overall approach toward security governance, risk management and compliance.
Ethical Hacking

The Internet is home to seemingly infinite amounts of confidential and personal information. As a result of this mass storage of information, the system needs to be constantly updated and enforced to prevent hackers from retrieving such valuable and sensitive data. This increasing number of cyber-attacks has led to an increasing importance of Ethical Hacking. So Ethical hackers' job is to scan vulnerabilities and to find potential threats on a computer or networks. An ethical hacker finds the weakness or loopholes in a computer, web applications or network and reports them to the organization. It requires a thorough knowledge of Networks, web servers, computer viruses, SQL (Structured Query Language), cryptography, penetration testing, Attacks etc. In this session, you will learn all about ethical hacking. You will understand the what ethical hacking, Cyber- attacks, Tools and some hands-on demos. This session will also guide you with the various ethical hacking certifications available today.
More from Priyanka Aash (20)
Digital Personal Data Protection (DPDP) Practical Approach For CISOs

Digital Personal Data Protection (DPDP) Practical Approach For CISOs
EVERY ATTACK INVOLVES EXPLOITATION OF A WEAKNESS.pdf

EVERY ATTACK INVOLVES EXPLOITATION OF A WEAKNESS.pdf
Cyber Truths_Are you Prepared version 1.1.pptx.pdf

Cyber Truths_Are you Prepared version 1.1.pptx.pdf
Emerging New Threats And Top CISO Priorities In 2022 (Chennai)

Emerging New Threats And Top CISO Priorities In 2022 (Chennai)
Emerging New Threats And Top CISO Priorities In 2022 (Mumbai)

Emerging New Threats And Top CISO Priorities In 2022 (Mumbai)
Emerging New Threats And Top CISO Priorities in 2022 (Bangalore)

Emerging New Threats And Top CISO Priorities in 2022 (Bangalore)
Cloud Security: Limitations of Cloud Security Groups and Flow Logs

Cloud Security: Limitations of Cloud Security Groups and Flow Logs
Recently uploaded
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

In today's fast-changing business world, Companies that adapt and embrace new ideas often need help to keep up with the competition. However, fostering a culture of innovation takes much work. It takes vision, leadership and willingness to take risks in the right proportion. Sachin Dev Duggal, co-founder of Builder.ai, has perfected the art of this balance, creating a company culture where creativity and growth are nurtured at each stage.
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
Connector Corner: Automate dynamic content and events by pushing a button

Here is something new! In our next Connector Corner webinar, we will demonstrate how you can use a single workflow to:
Create a campaign using Mailchimp with merge tags/fields
Send an interactive Slack channel message (using buttons)
Have the message received by managers and peers along with a test email for review
But there’s more:
In a second workflow supporting the same use case, you’ll see:
Your campaign sent to target colleagues for approval
If the “Approve” button is clicked, a Jira/Zendesk ticket is created for the marketing design team
But—if the “Reject” button is pushed, colleagues will be alerted via Slack message
Join us to learn more about this new, human-in-the-loop capability, brought to you by Integration Service connectors.
And...
Speakers:
Akshay Agnihotri, Product Manager
Charlie Greenberg, Host
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

As AI technology is pushing into IT I was wondering myself, as an “infrastructure container kubernetes guy”, how get this fancy AI technology get managed from an infrastructure operational view? Is it possible to apply our lovely cloud native principals as well? What benefit’s both technologies could bring to each other?
Let me take this questions and provide you a short journey through existing deployment models and use cases for AI software. On practical examples, we discuss what cloud/on-premise strategy we may need for applying it to our own infrastructure to get it to work from an enterprise perspective. I want to give an overview about infrastructure requirements and technologies, what could be beneficial or limiting your AI use cases in an enterprise environment. An interactive Demo will give you some insides, what approaches I got already working for real.
When stars align: studies in data quality, knowledge graphs, and machine lear...

Keynote at DQMLKG workshop at the 21st European Semantic Web Conference 2024
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Have you ever wanted a Ruby client API to communicate with your web service? Smithy is a protocol-agnostic language for defining services and SDKs. Smithy Ruby is an implementation of Smithy that generates a Ruby SDK using a Smithy model. In this talk, we will explore Smithy and Smithy Ruby to learn how to generate custom feature-rich SDKs that can communicate with any web service, such as a Rails JSON API.
Key Trends Shaping the Future of Infrastructure.pdf

Keynote at DIGIT West Expo, Glasgow on 29 May 2024.
Cheryl Hung, ochery.com
Sr Director, Infrastructure Ecosystem, Arm.
The key trends across hardware, cloud and open-source; exploring how these areas are likely to mature and develop over the short and long-term, and then considering how organisations can position themselves to adapt and thrive.
Accelerate your Kubernetes clusters with Varnish Caching

A presentation about the usage and availability of Varnish on Kubernetes. This talk explores the capabilities of Varnish caching and shows how to use the Varnish Helm chart to deploy it to Kubernetes.
This presentation was delivered at K8SUG Singapore. See https://feryn.eu/presentations/accelerate-your-kubernetes-clusters-with-varnish-caching-k8sug-singapore-28-2024 for more details.
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scalable Platform by VP of Product, The New York Times
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designer, Beats by Dr Dre
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
Elevating Tactical DDD Patterns Through Object Calisthenics

After immersing yourself in the blue book and its red counterpart, attending DDD-focused conferences, and applying tactical patterns, you're left with a crucial question: How do I ensure my design is effective? Tactical patterns within Domain-Driven Design (DDD) serve as guiding principles for creating clear and manageable domain models. However, achieving success with these patterns requires additional guidance. Interestingly, we've observed that a set of constraints initially designed for training purposes remarkably aligns with effective pattern implementation, offering a more ‘mechanical’ approach. Let's explore together how Object Calisthenics can elevate the design of your tactical DDD patterns, offering concrete help for those venturing into DDD for the first time!
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

“AGI should be open source and in the public domain at the service of humanity and the planet.”
AI for Every Business: Unlocking Your Product's Universal Potential by VP of ...

AI for Every Business: Unlocking Your Product's Universal Potential by VP of Product, Slack
Recently uploaded (20)
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
Connector Corner: Automate dynamic content and events by pushing a button

Connector Corner: Automate dynamic content and events by pushing a button
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024
When stars align: studies in data quality, knowledge graphs, and machine lear...

When stars align: studies in data quality, knowledge graphs, and machine lear...
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Generating a custom Ruby SDK for your web service or Rails API using Smithy
Key Trends Shaping the Future of Infrastructure.pdf

Key Trends Shaping the Future of Infrastructure.pdf
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
Accelerate your Kubernetes clusters with Varnish Caching

Accelerate your Kubernetes clusters with Varnish Caching
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designe...
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
Elevating Tactical DDD Patterns Through Object Calisthenics

Elevating Tactical DDD Patterns Through Object Calisthenics
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...
AI for Every Business: Unlocking Your Product's Universal Potential by VP of ...

AI for Every Business: Unlocking Your Product's Universal Potential by VP of ...
Sacon - IoT Forum Fresh Thinking (Arvind Tiwary + Bikash Barai)
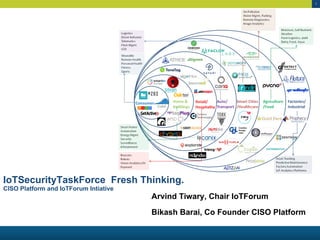
- 1. 1 IoTSecurityTaskForce Fresh Thinking. CISO Platform and IoTForum Intiative Arvind Tiwary, Chair IoTForum Bikash Barai, Co Founder CISO Platform
- 2. 2 IoTForum: Raising the IoT Quotient of India www.iotforindia.org
- 3. 3 Task Force on IoT Security IoT Forum & CISO platform join hands to create IoT Security Task force Readying up the Nation for #IoTSecurity The task force is chartered to develop threat models, controls and assist players in new techno-legal- commercial arrangements to improve IoT Security Fresh thinking around Security for IOThttp://wiki.iotforindia.org/FreshThinking
- 4. 4 IOT Security § Over 13 Standards bodies have a advisory § http://www.cisoplatform.com/profiles/blogs/survey-of-iot-security- standards § FTC, NIST § IoT Security Foundation, Broadband Internet Technical Advisory Group (BITAG) § OWASP § IETF § DICE MUD, OtrF, ACE § IIC Industrial Internet Consortium, Cybersecurity = risk is Money and reputation IoT = risk is accident and human lives
- 5. 5 Fresh Thinking: Is the Emperor Naked? You don’t change all the locks of each house in a city merrily because criminals can break 7 lever locks in less time
- 6. 6 IOT Security § Program COMPLEXITY= Algorithm + Data Structure § CyberSecurity Difficulty= Legal + Technical § Internet was designed to withstand disruptive nuclear attack § IP and MAC spoofing make it fundamentally unsecure § Legal Basis § Product Quality and Liability regime – USA § DDOS by House Owners is like Rioters are House owner responsibility? § Petty Wannacry type ransom ware is like carjacking in Joburg § Armoured car ? § Criminal Law § Territorial § Individual, layers of Government § Precinct, City, State, Nation § Right of Self defence We need attribution which can hold in a court of law and can be easily and routinely derived. not require weeks of research?
- 7. 7 Principles of FreshThinking: Blaming the Victim is so old fashioned § Reduce effort and skill required to secure § Increase probability of detection § Decrees success rewards § Impose costs on criminals. Pirates must be tamed § Law is Territorial. Cyberspace criminals must be caught and booked under laws of piracy and high seas § Special High frequency crime mitigation procedures § Instrument and infect hackers to provide evidence § Protocol between ISP of participating nations § Reduce burden and standard of care for network operators to act § Throttle and block suspicious activity For IoT Network 5 year Sandbox
- 8. 8 CyberLaw for the Cyber City § Recognize pervasive criminal activity § SPAM, Carjacking § Allow right to self defence § Can instrument, infect and hack-back to identify and prove attacker § The individual house owner is the victim and he should be able to count on neighbours, community and police and not be blamed or denied rights to chase and catch criminals No amount of passive defence can stop pervasive criminal succeeding once in a while Broken Glass syndrome : Catch petty criminals deters big crime also
- 9. 9 Managed SECURENET § A new business opportunity § Skills and effort required are increasing day by day § Pool and outsource § Hierarchy of Safety providers § Office security, Facility Security, Township , § Police, CISF, BSF, Army
- 10. 10 Legal Requirements § Fool Proof Identification of actor § Not spoofable MAC and probabilistic pattern based § Establish Mens Rea (Intent) § Deception based defence. Not accidental entrance § Cyber CCTV § Anton Pillar order capability § Civil search and seizure § Execute a Letter of marque § Piracy on high seas
- 11. 11 Before SECURENET A Few Security Trends …
- 12. 12 Security, Impossibility & Halting Problem
- 13. 13 Isolation, Walled Gardens … Zero Trust Model, Beyond Corp ..
- 14. 14 4 Pillars of SECURENET (1) Identify (Authenticate) (2) Onboard (Authorize) (3) Monitor (4) Off-Board (React)
- 15. 15 (1) Authenticate & (2) Authorize.. Identity/Authenticati on : Device, People, network Identity.. TPM, HW root of trust Social/Behavior, Biometrics, Multi Factor etc Authorization: Degrees of trust & scenario analysis, provision tiered authority
- 16. 16
- 17. 17 (3) Monitor •Centralized/Network Access Proxy: •At main entry point to subnet •Township entry/ Network Access Proxy •Decentralized: •Local Anomaly detection for neighbourhood •OSINT, SIEM, SA, NTA/NBA, CASB, UBA, UEBA •External & Hyper Local Threat Intelligence: •Central Intelligence to Neighbourhood watch
- 18. 18 (4) React/Offboard •Offboard •Reduce Access/Quarantine: •Deception/Offensive Countermeasures/Active Defense
- 19. 19 Delegated Police Authority § Semi Private and Semi Public Spaces § Cyber City and Cyber Neighbourhood not Cyber Jungle § Right of Self Defence § Chase a thief into other property § Enter a house from where enemy fire is coming § Stop a speeding truck trying to ram thru a entry gate inspection § Place a marker to trace stolen goods § High Seas and Space Piracy laws § Right for catching a cyberspace criminal § Letters of Marquee to bring criminals to justice
- 20. 20 CROSS BORDER § PROTOCOL for Countries allowed to connect on SECURENET § FAST , MINIMUM ACTION on suspect SITES automatically § MARTIME LAW is basis In the days of fighting sail, a letter of marque and reprisal was a government license authorizing a person (known as a privateer) to attack and capture enemy vessels and bring them before admiralty courts for condemnation and sale. A "letter of marque and reprisal" would include permission to cross an international border to effect a reprisal (take some action against an attack or injury) authorized by an issuing jurisdiction to conduct reprisal operations outside its borders. Wikipedia The United States Constitution grants to the Congress the power, among others, to issue “Letters of Marque and Reprisal.
- 21. 21 FreshThinking : Don’t blame victim but hurt criminals § SECURENET for IoT to test out new Techno Legal approach § Technical ability to identify source and produce actionable forensic evidence § Legal approach allowing cyber defence and chasing cyber pirates and hurting them and their assets § Broken Glass principle Security and safety is a stance. An Active defence posture will cut down lots of wannabe hackers. New types of instrumentation and network wide correlation will increase skills and costs of attackers
- 22. 22 Plan ü Initial discussions IoTNext 2016 (4Q 2016) ü Public Airing 9 Sep 2017 ü CISO Platform 14 Sep ü IoTNext Nov 9 ü SACON Nov 11 § December / January § TSDSI, DOT,TRAI,CDAC, § BSNL. Airtel, Jio, Vodafone, Ericson, Telco Stack § SoC, Chip mfgs § Lawyers, Free Internet § IEEE (Roof) § March 2018 Revisions based on feedback
- 23. 23 Critique, Alternative, Improvements § Volunteer Please…HARD PROBLEM § Technical Tools and approaches § Enterprise security at scale § Phishing and Super user hijack in IoT § Trigger words for Alexa, Google Home, Siri § MUD, DICE etc § Legal Tools and Approaches § Semi private and Semi Public in Cyberspace § Right to self defence § Delegated policing powers Join IoTSecurity Group www.iotforindia/beta
