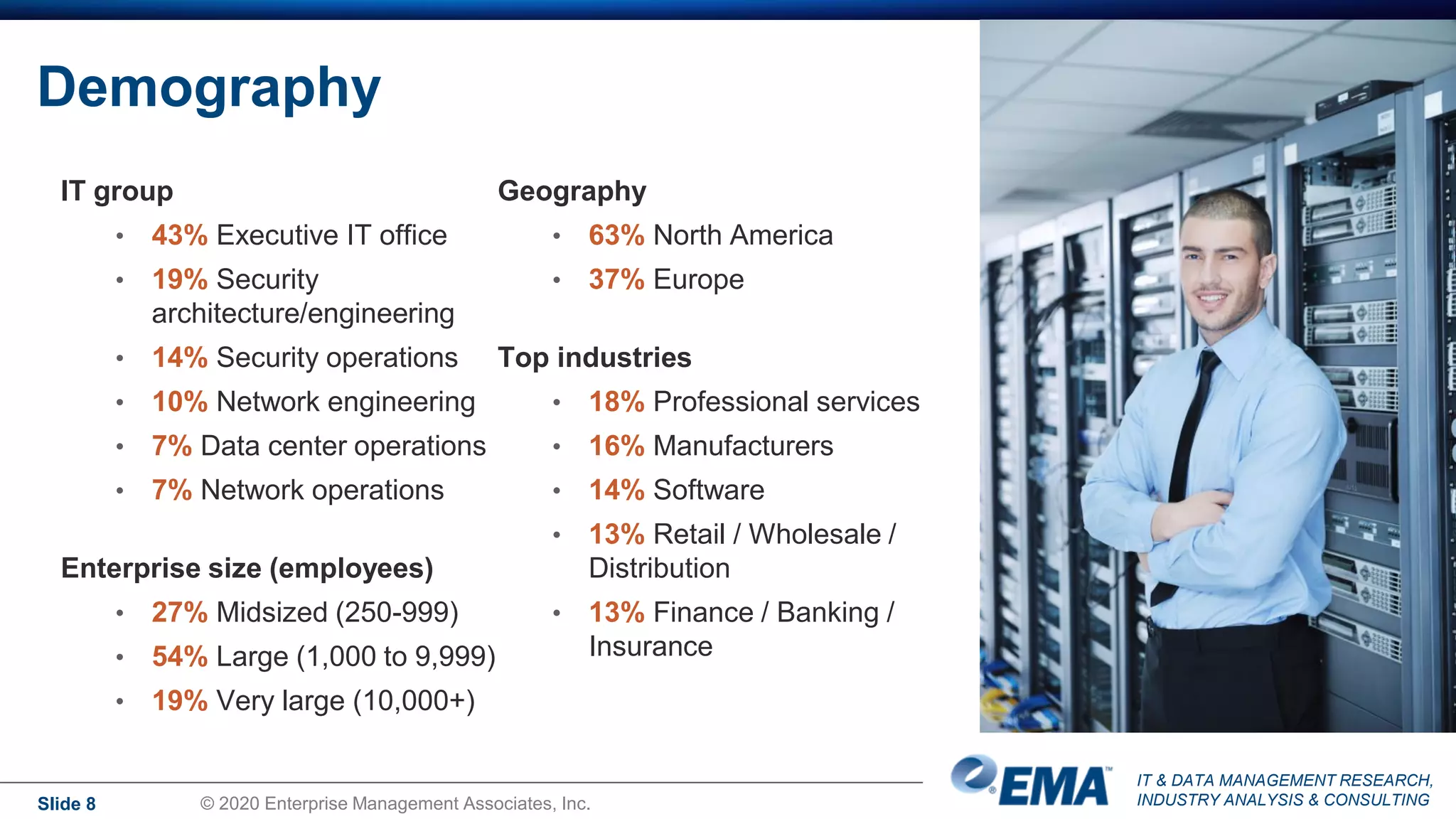
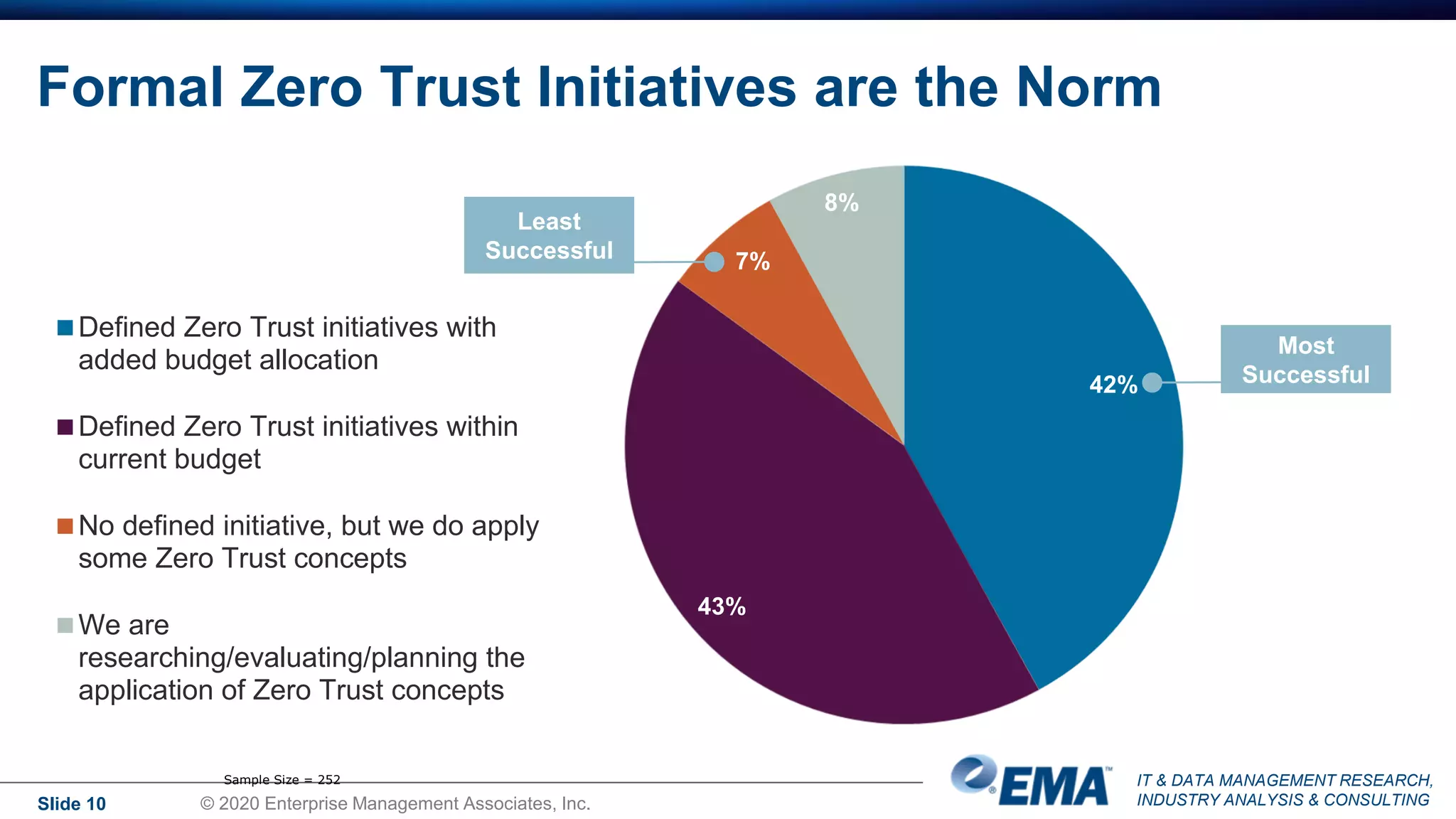
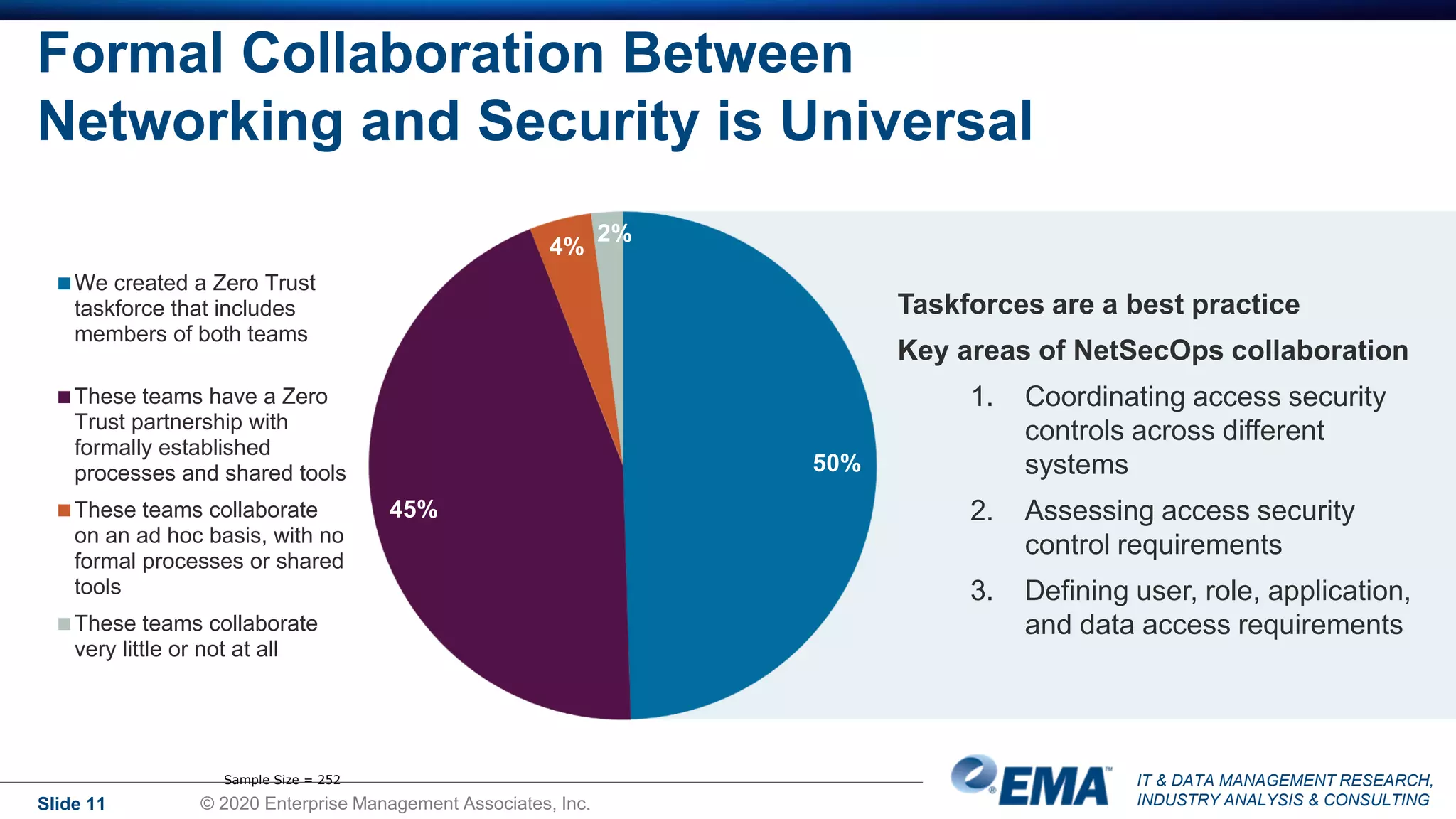
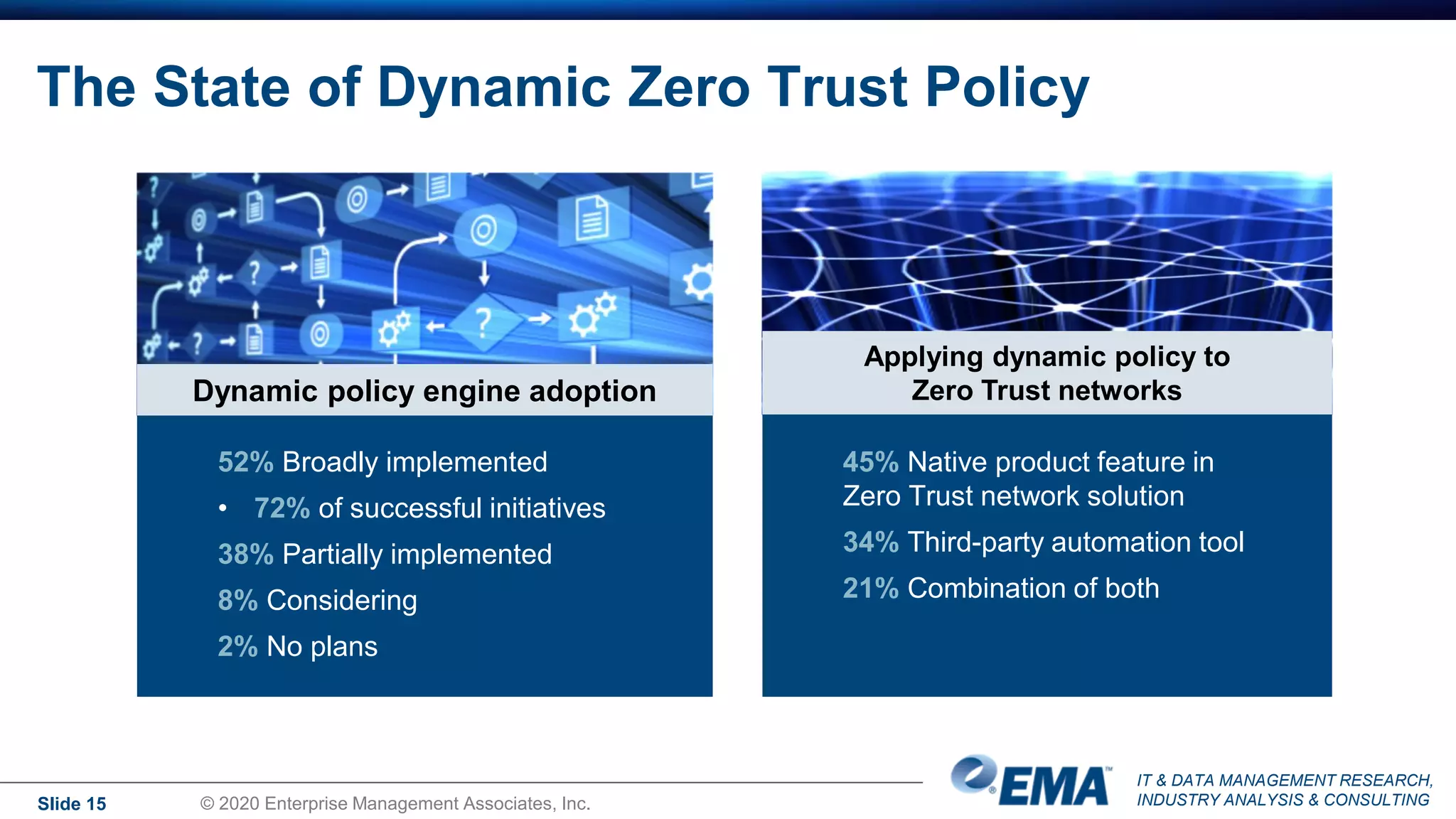
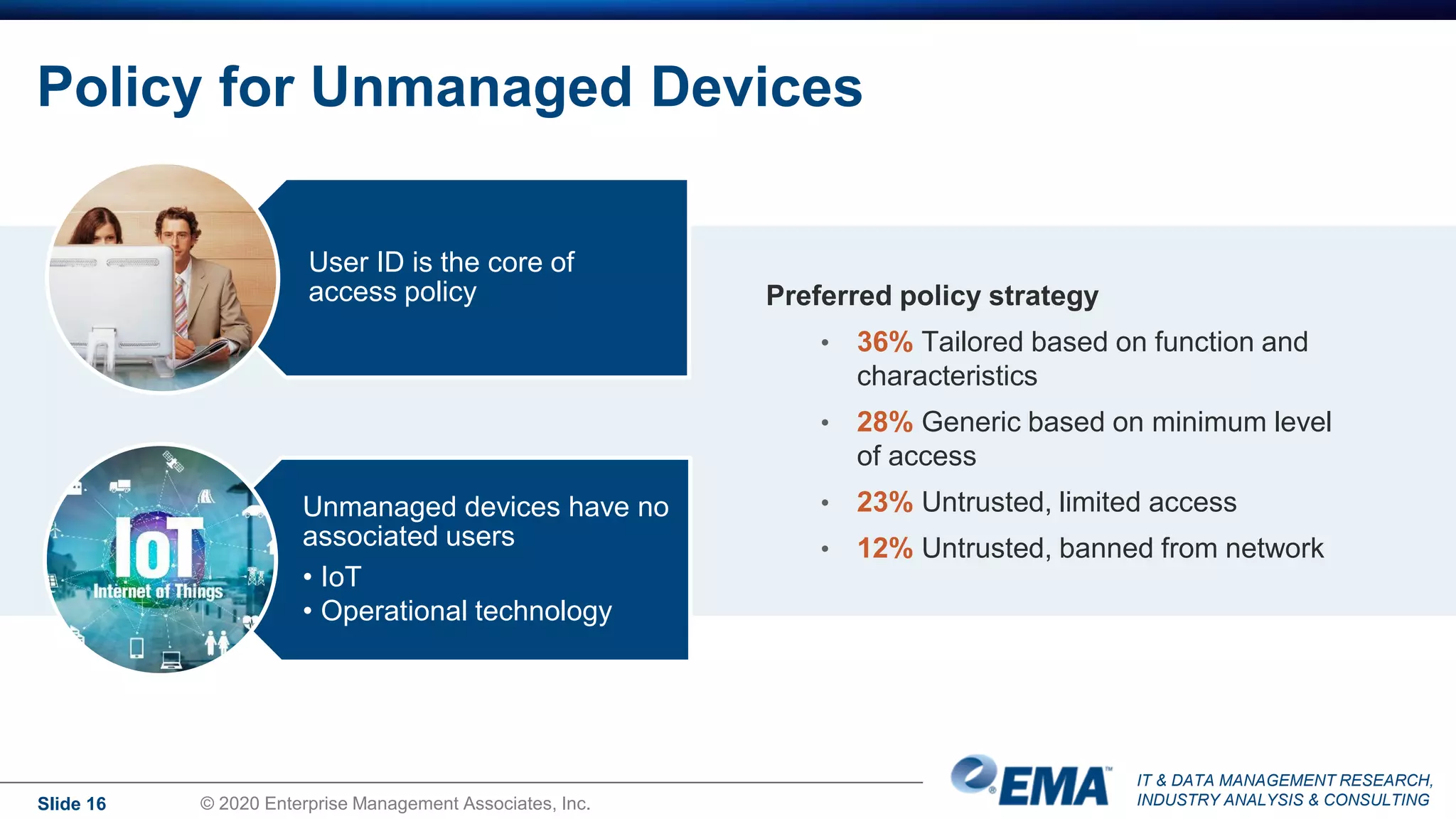
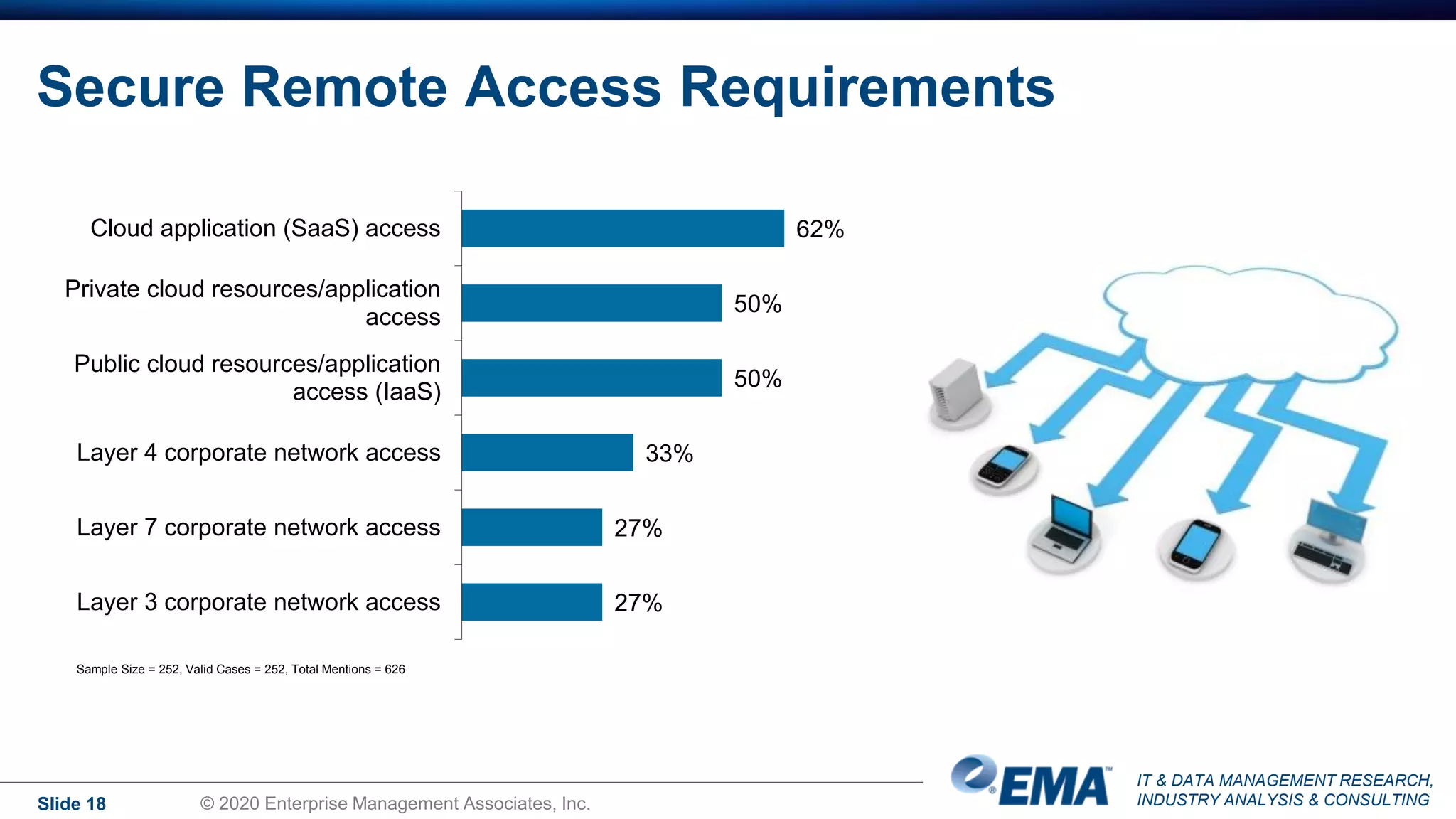
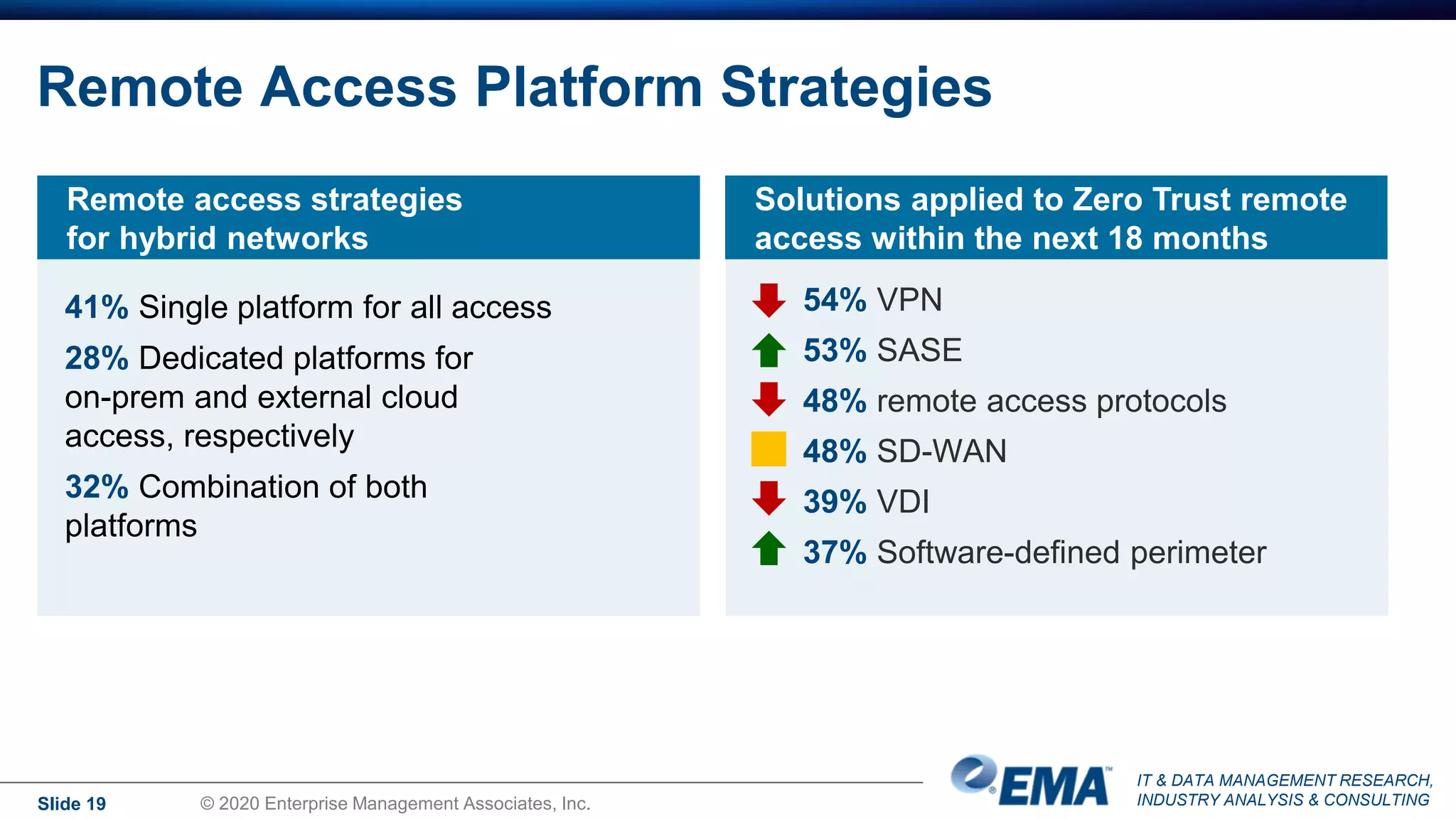
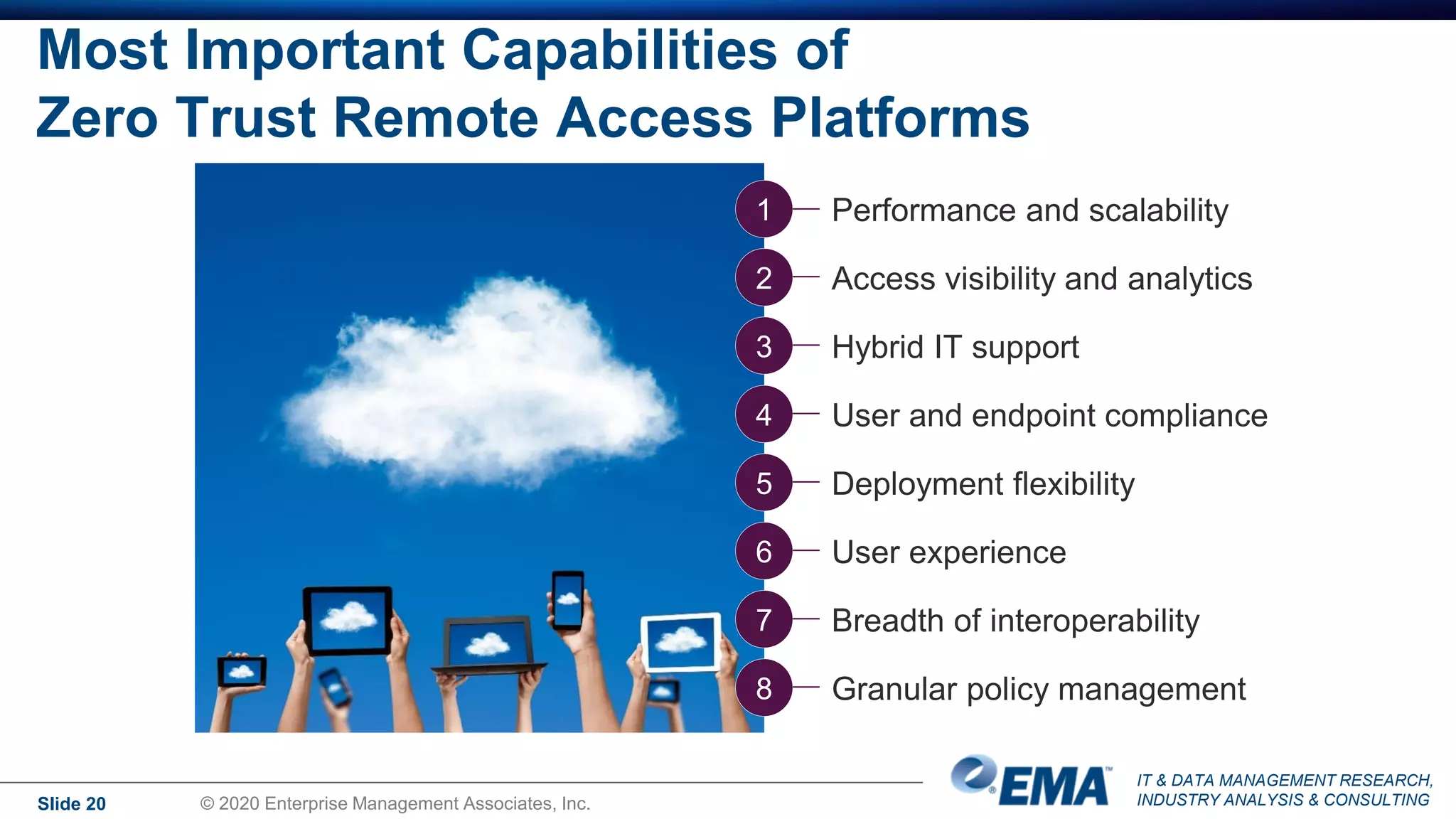
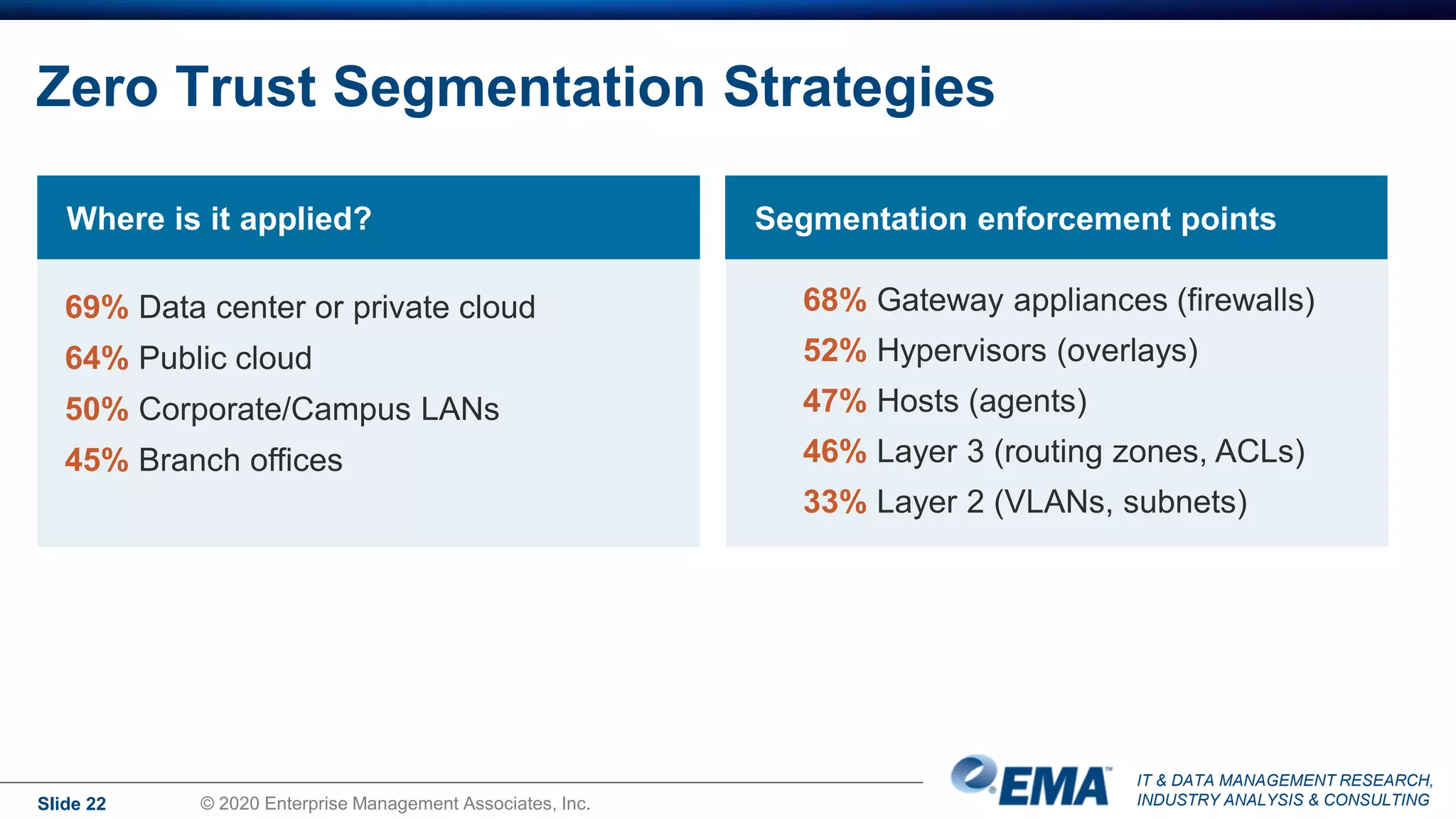
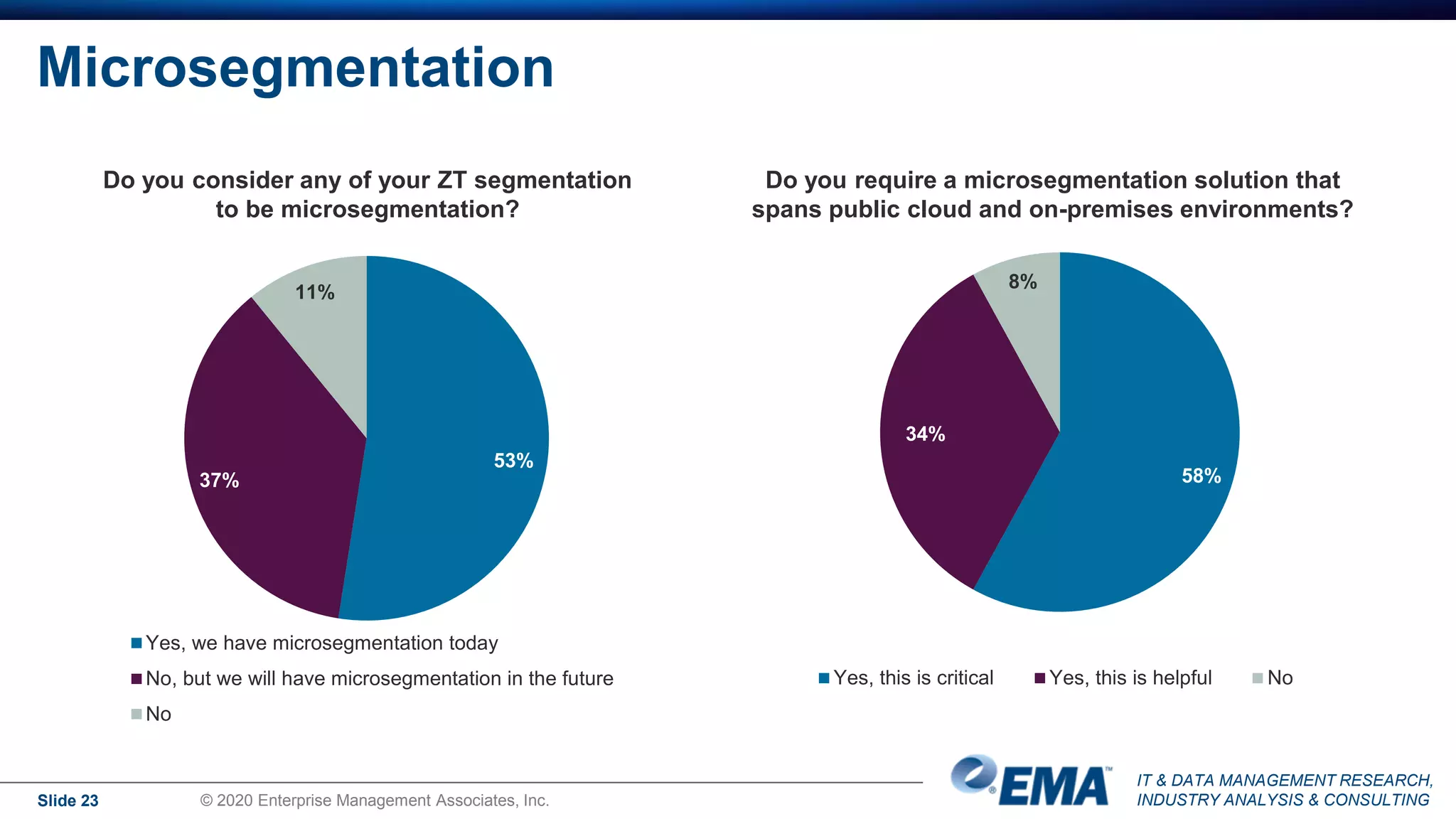
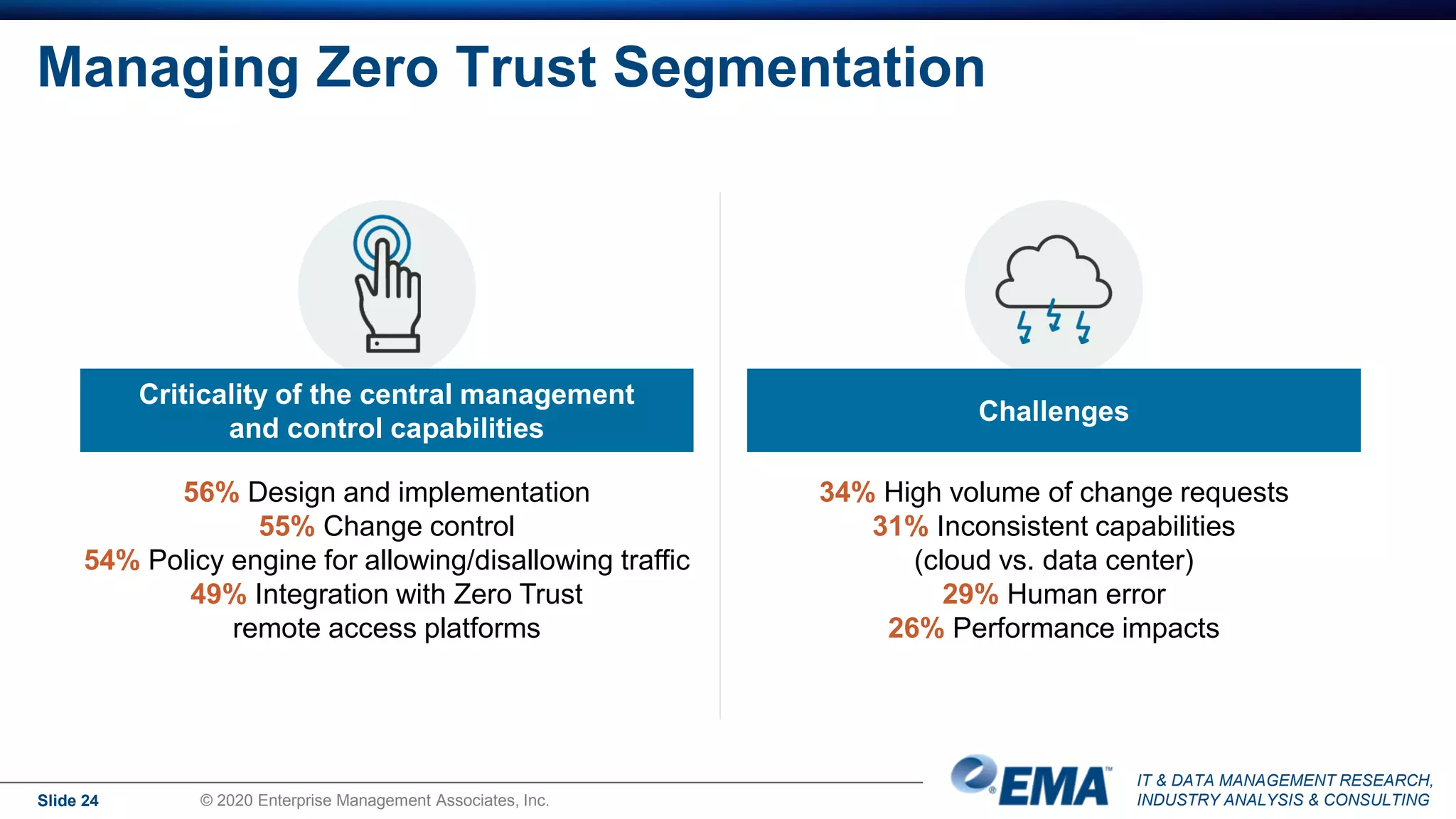
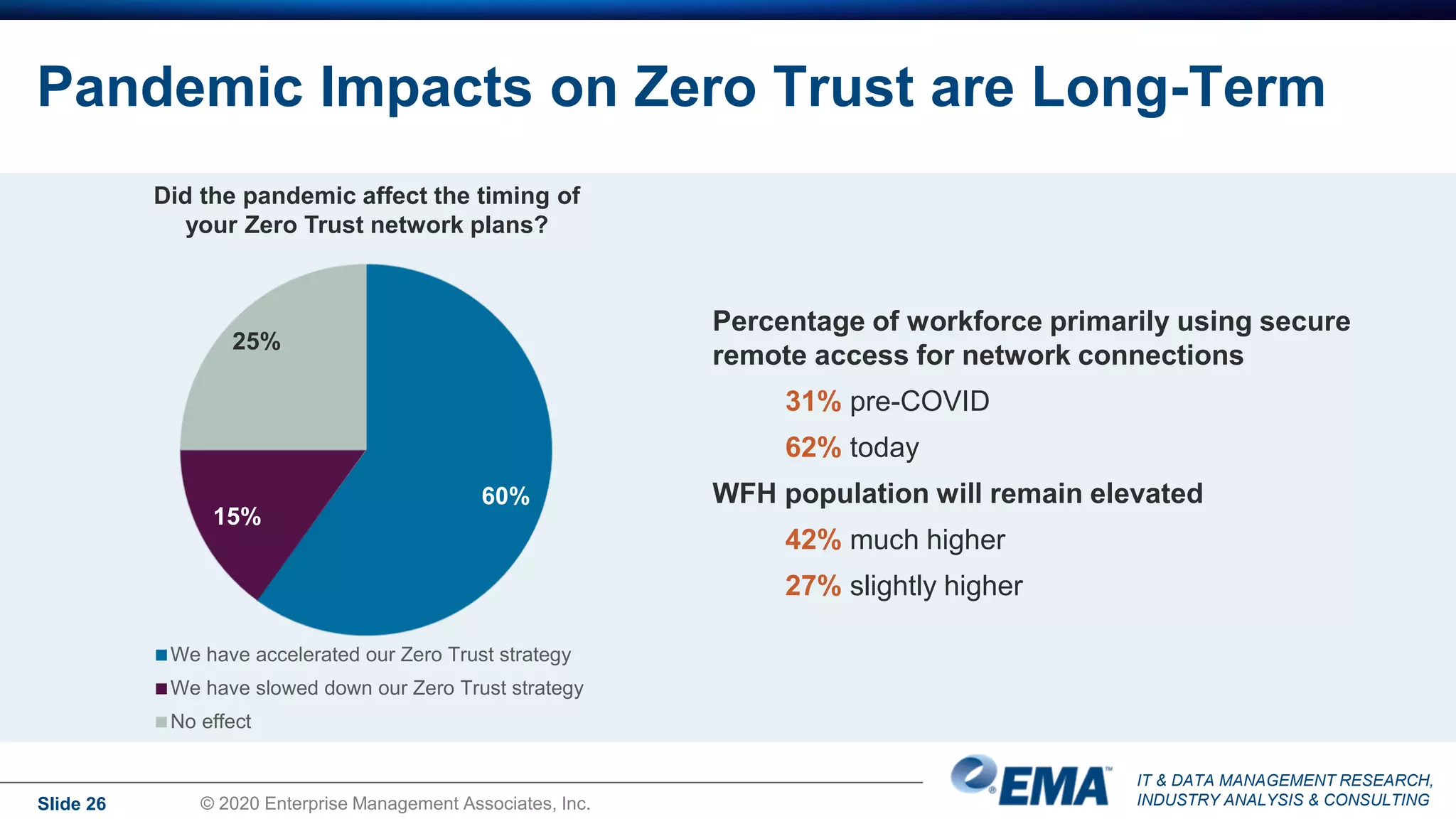
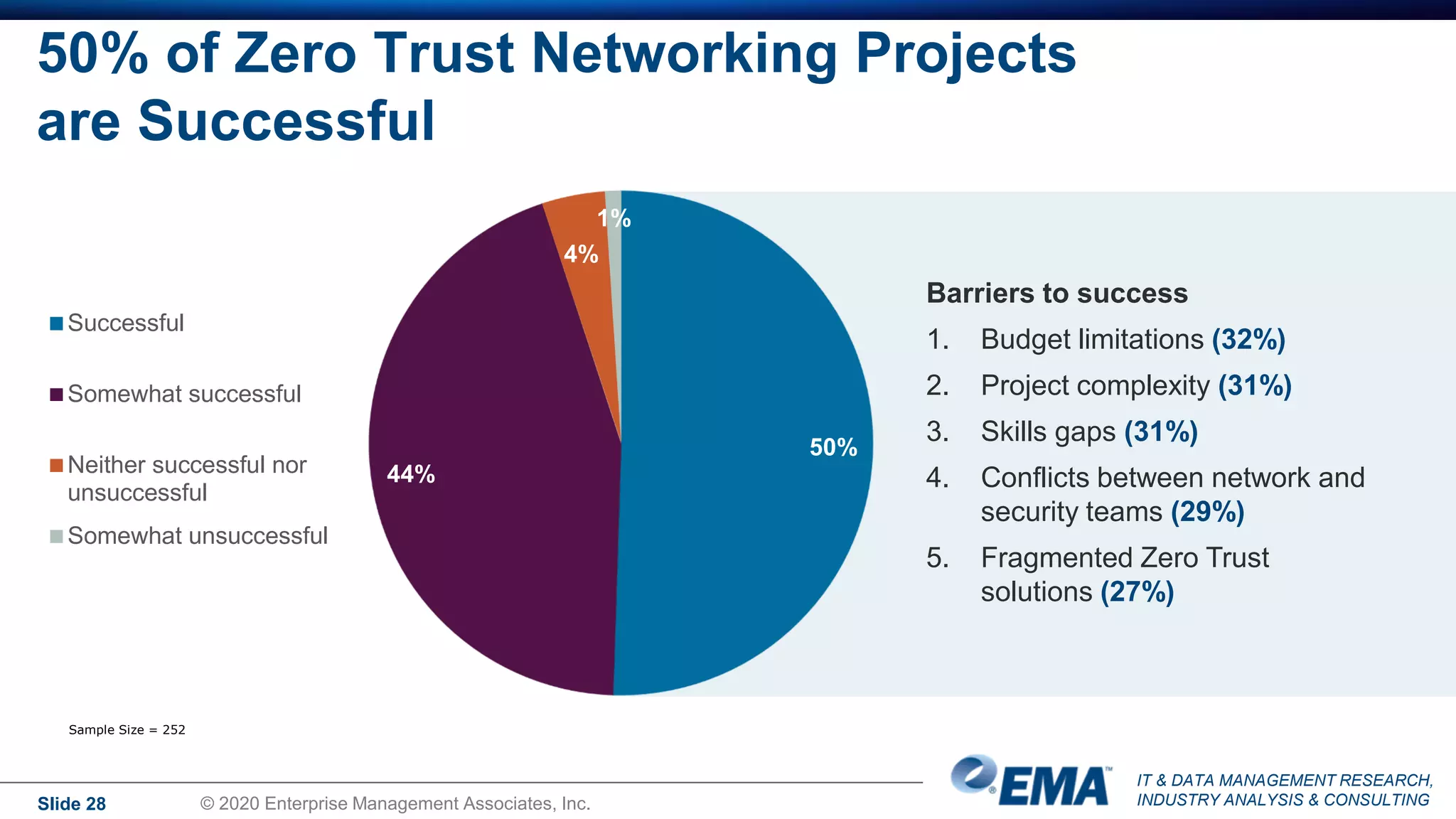
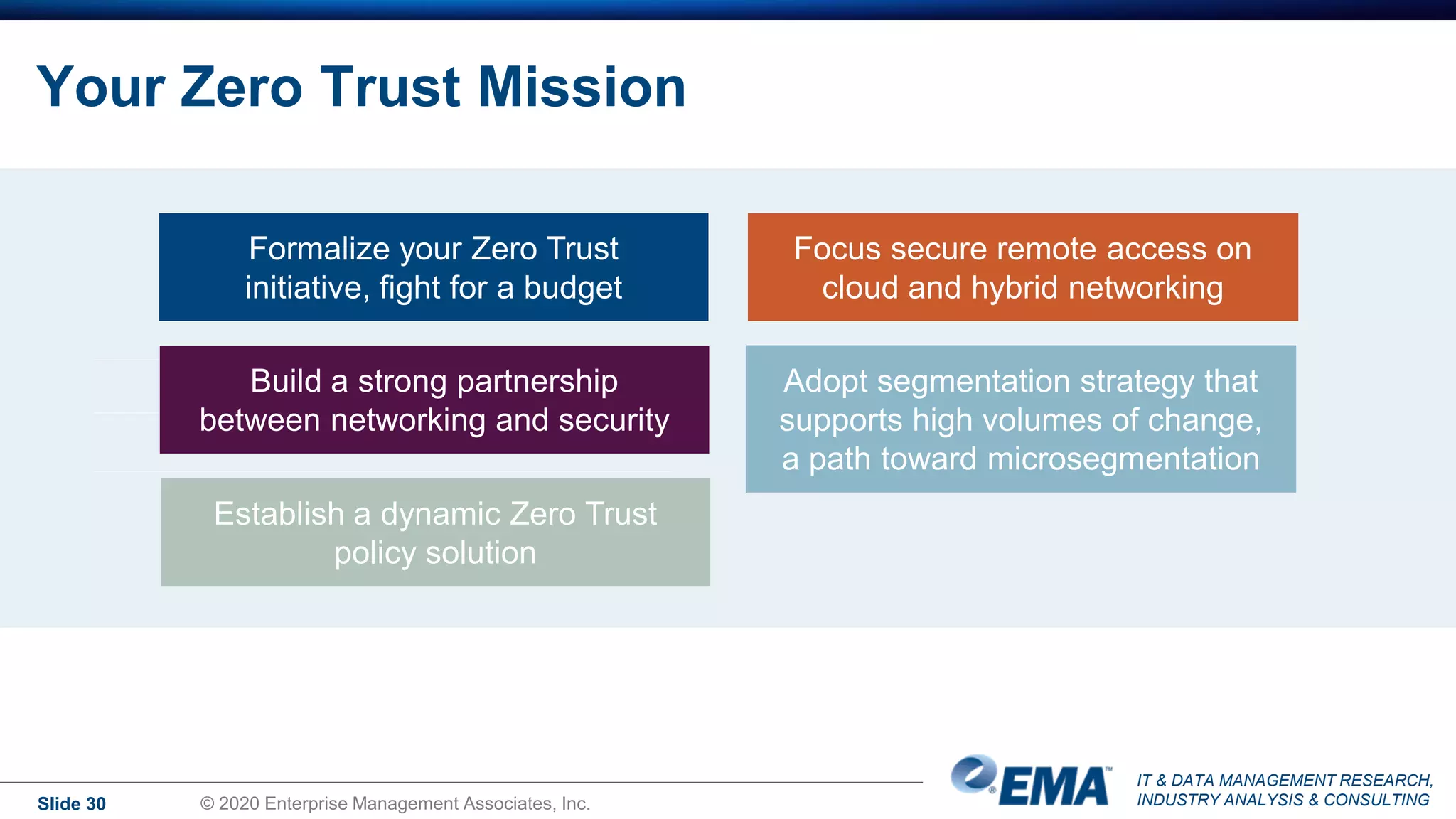
The document summarizes the key findings of a research report on enterprise zero trust networking strategies. It found that most organizations have formal zero trust initiatives with dedicated budgets. There is also universal collaboration between networking and security teams. Effective zero trust implementation requires dynamic policy engines and remote access platforms that support hybrid IT and cloud environments. Network segmentation and microsegmentation are important components but managing changes is challenging. The COVID-19 pandemic accelerated many organizations' zero trust strategies due to increased remote work. Half of zero trust projects are successful, with budget, complexity, skills gaps and fragmented solutions being common barriers.