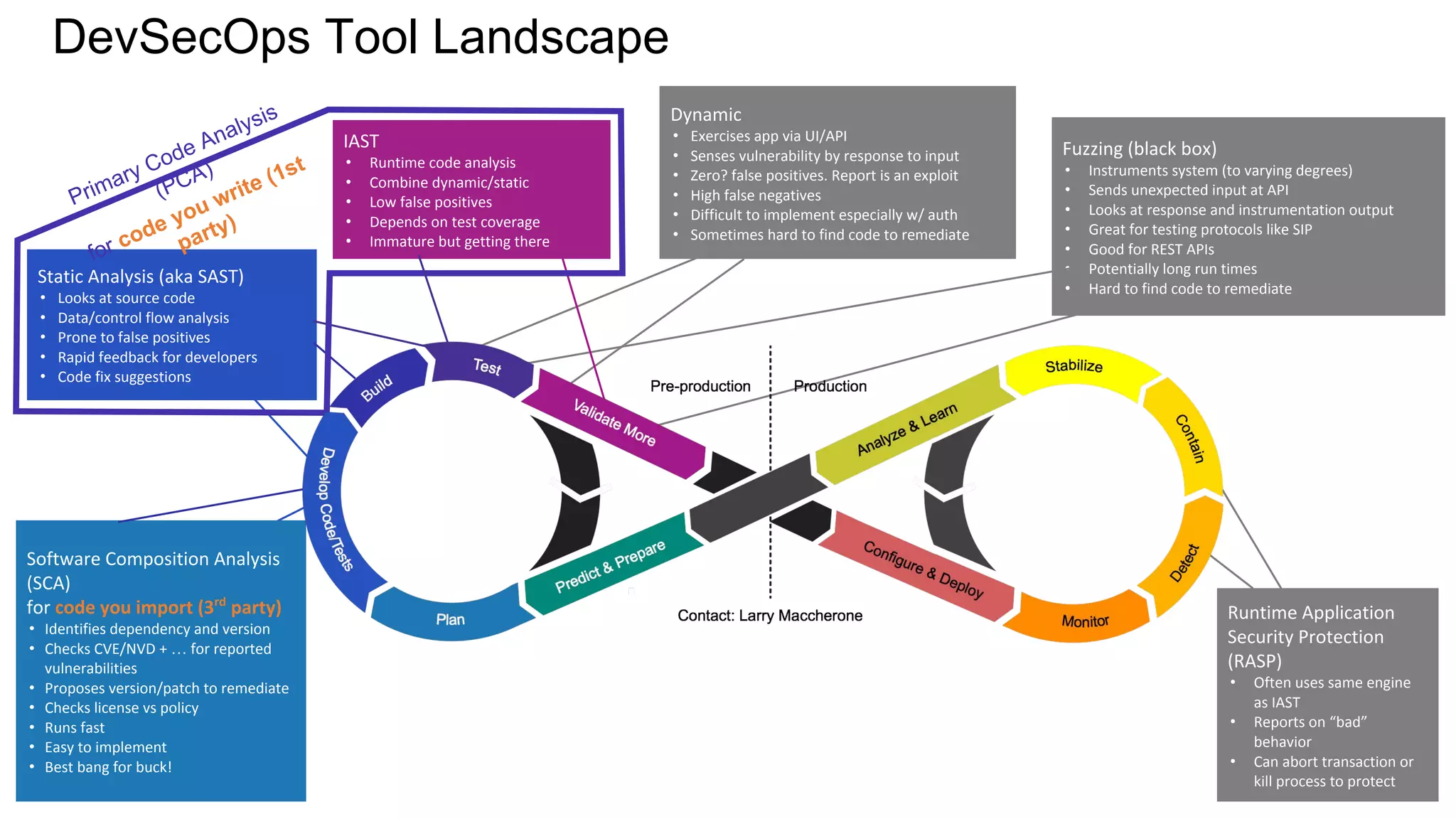
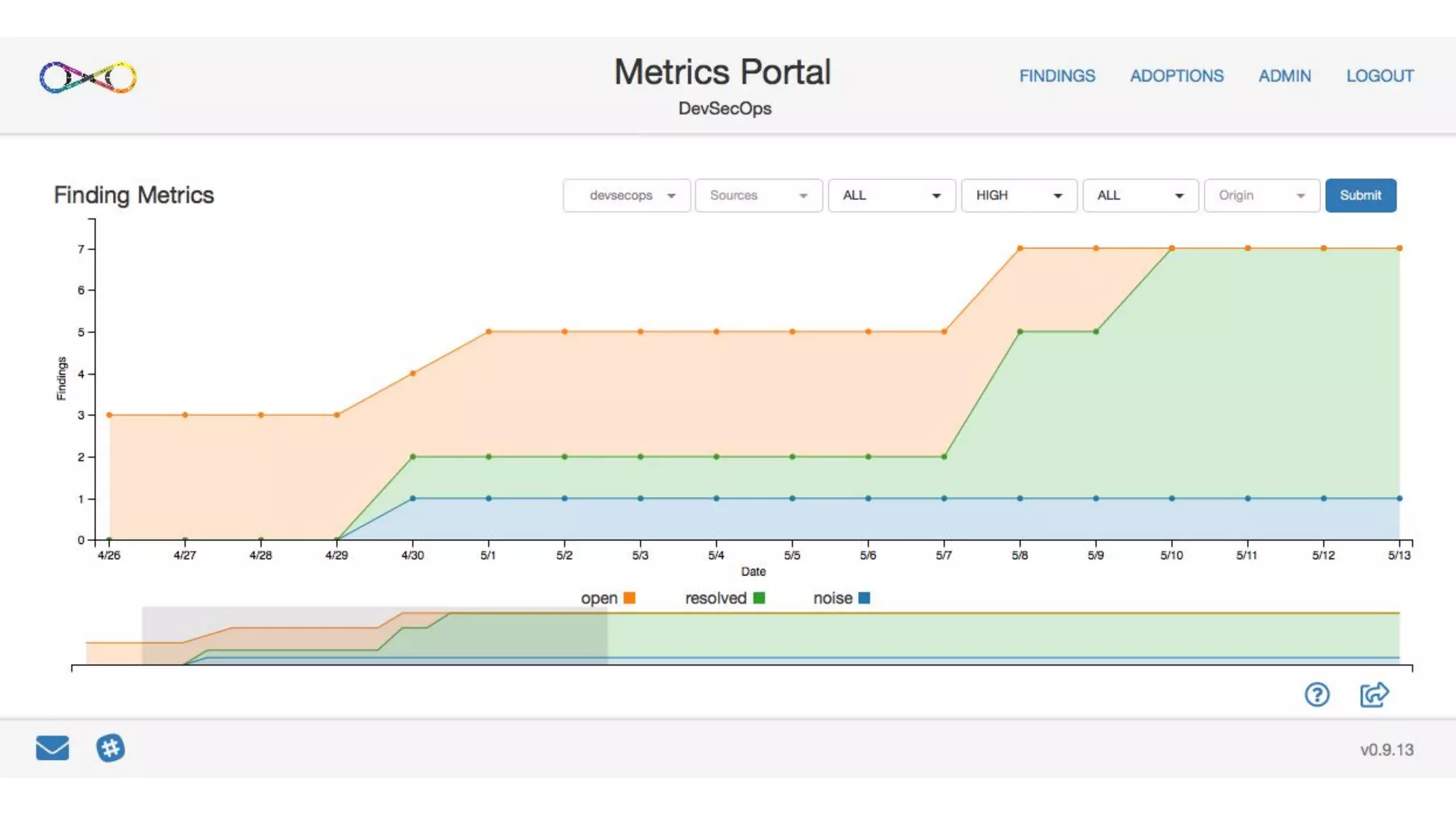
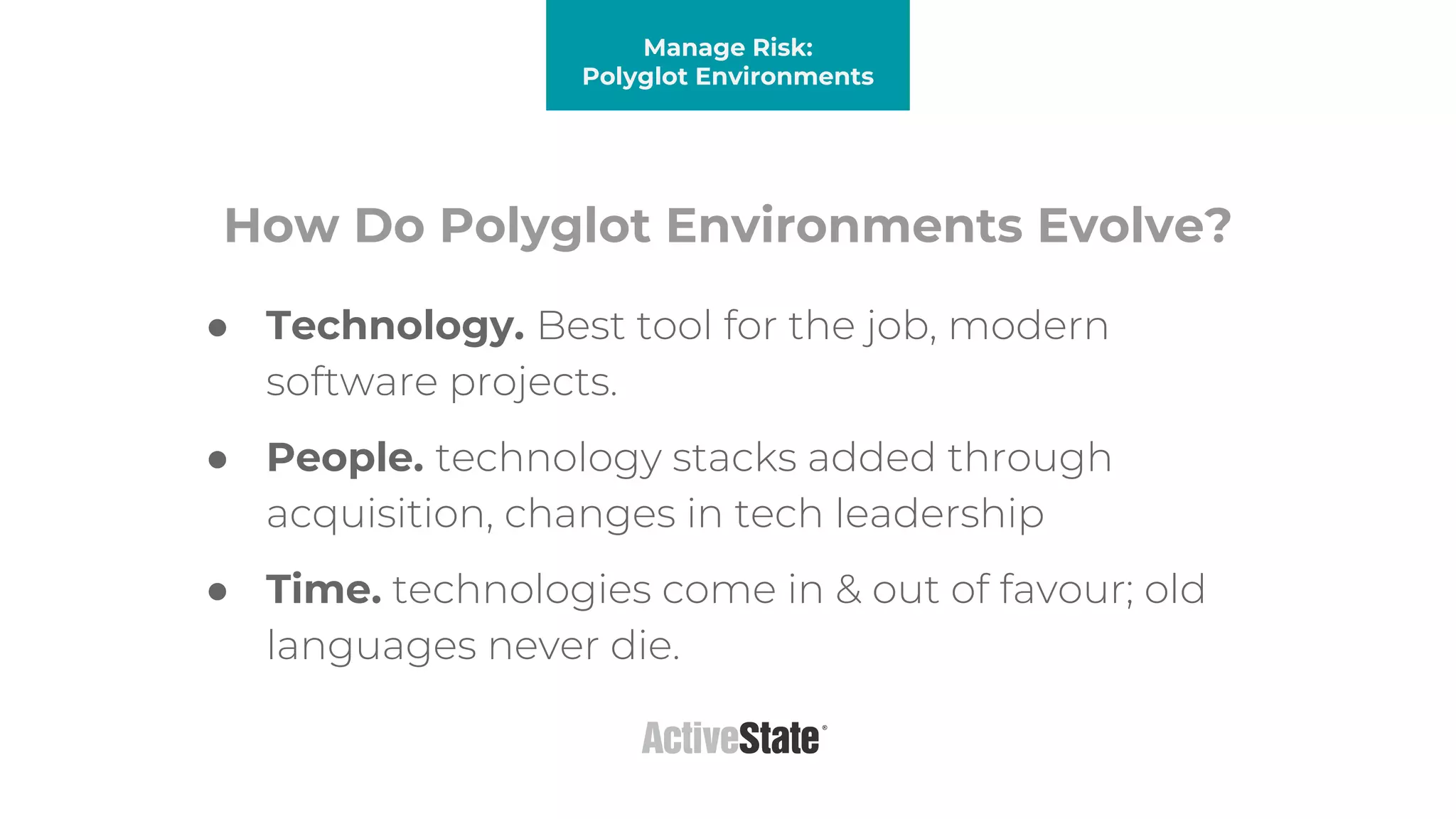
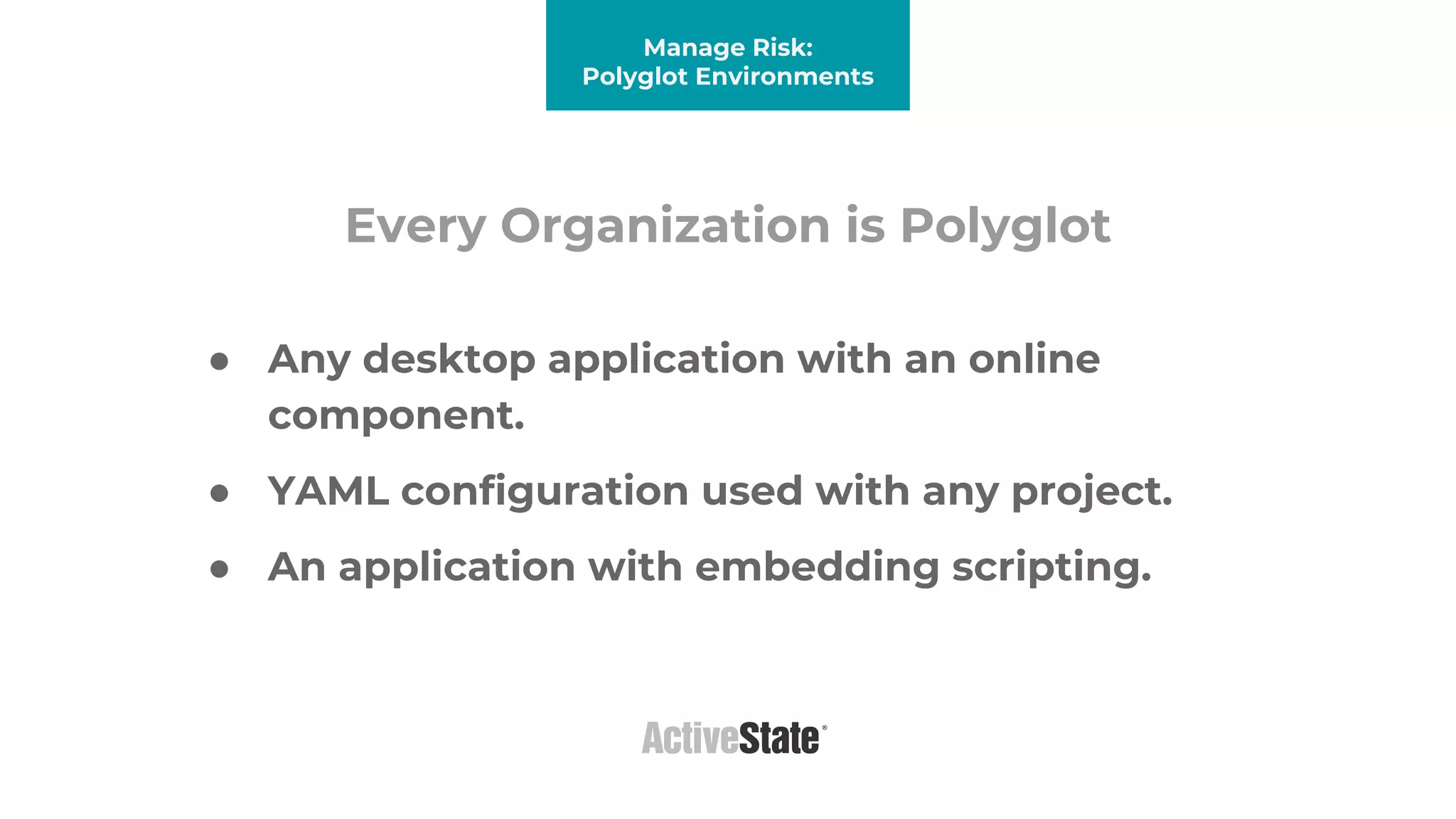
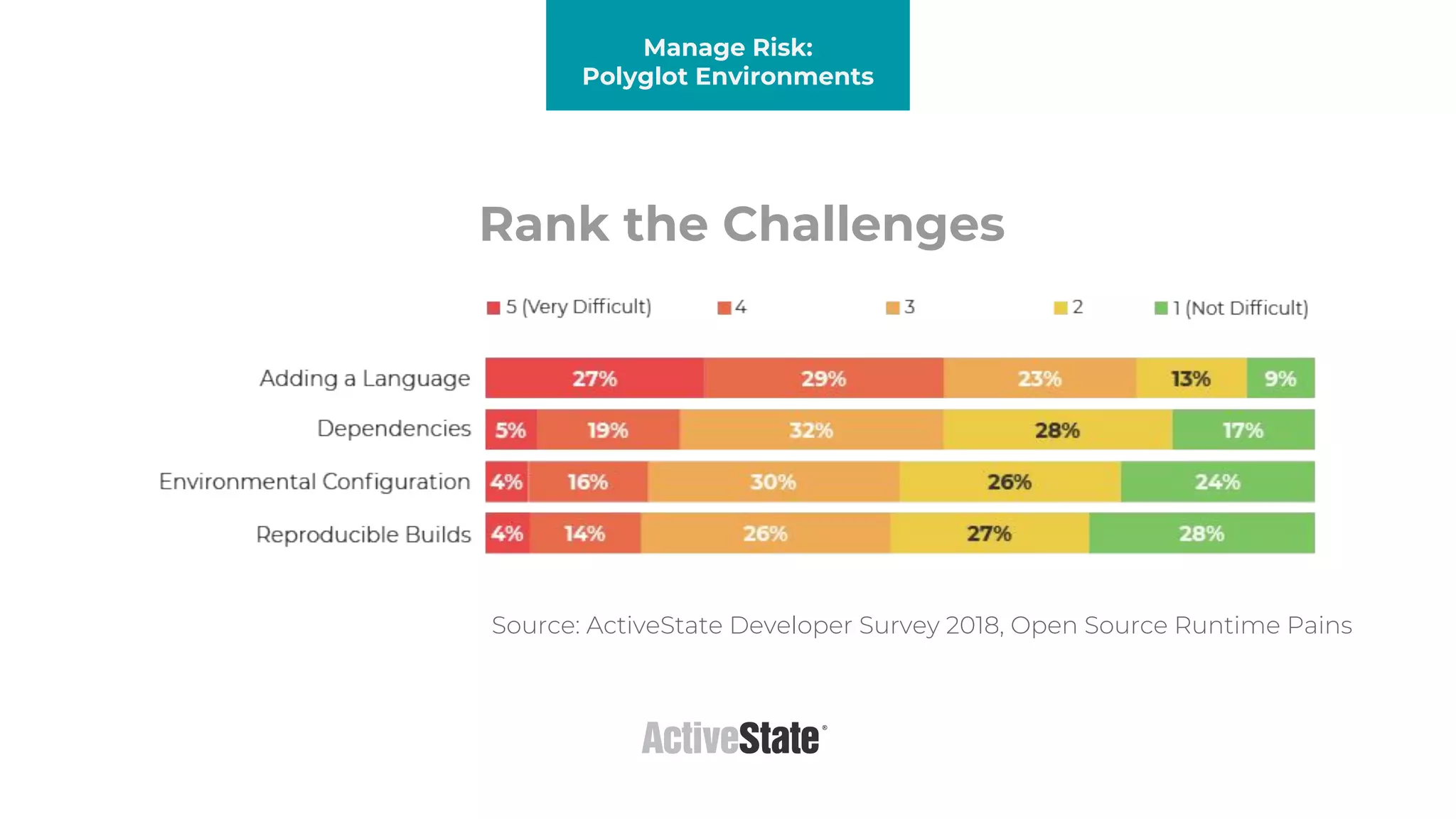
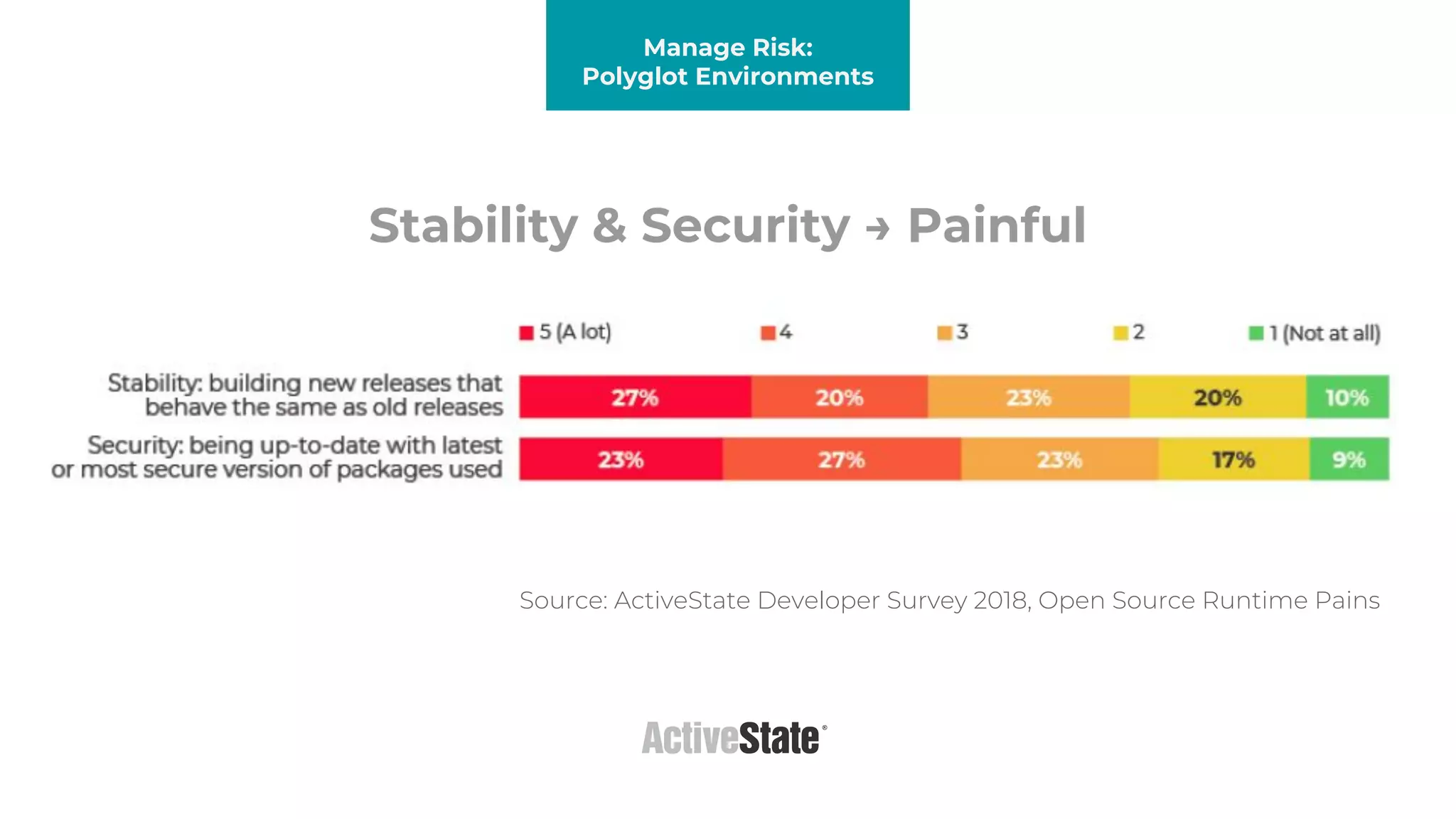
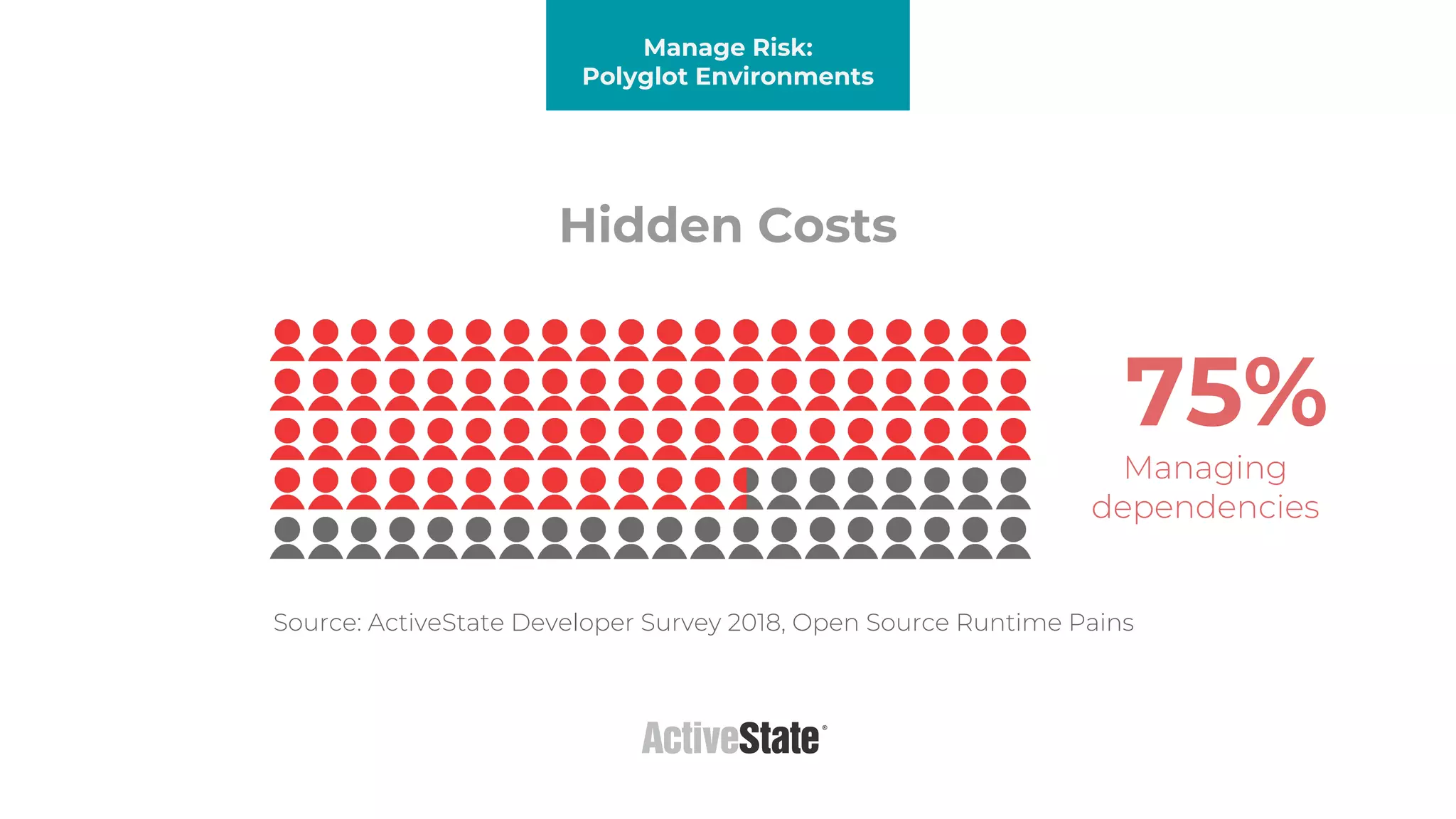
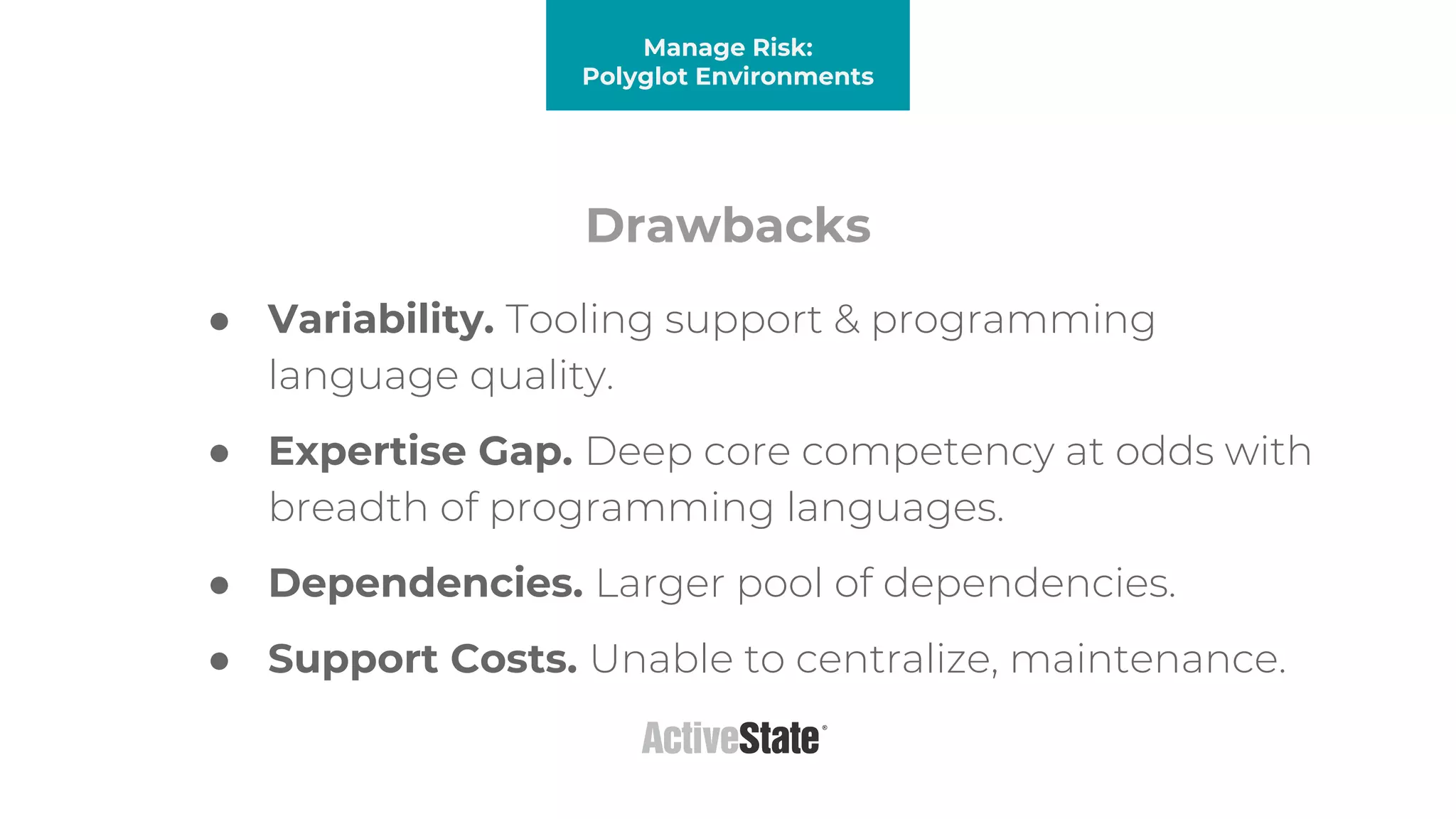
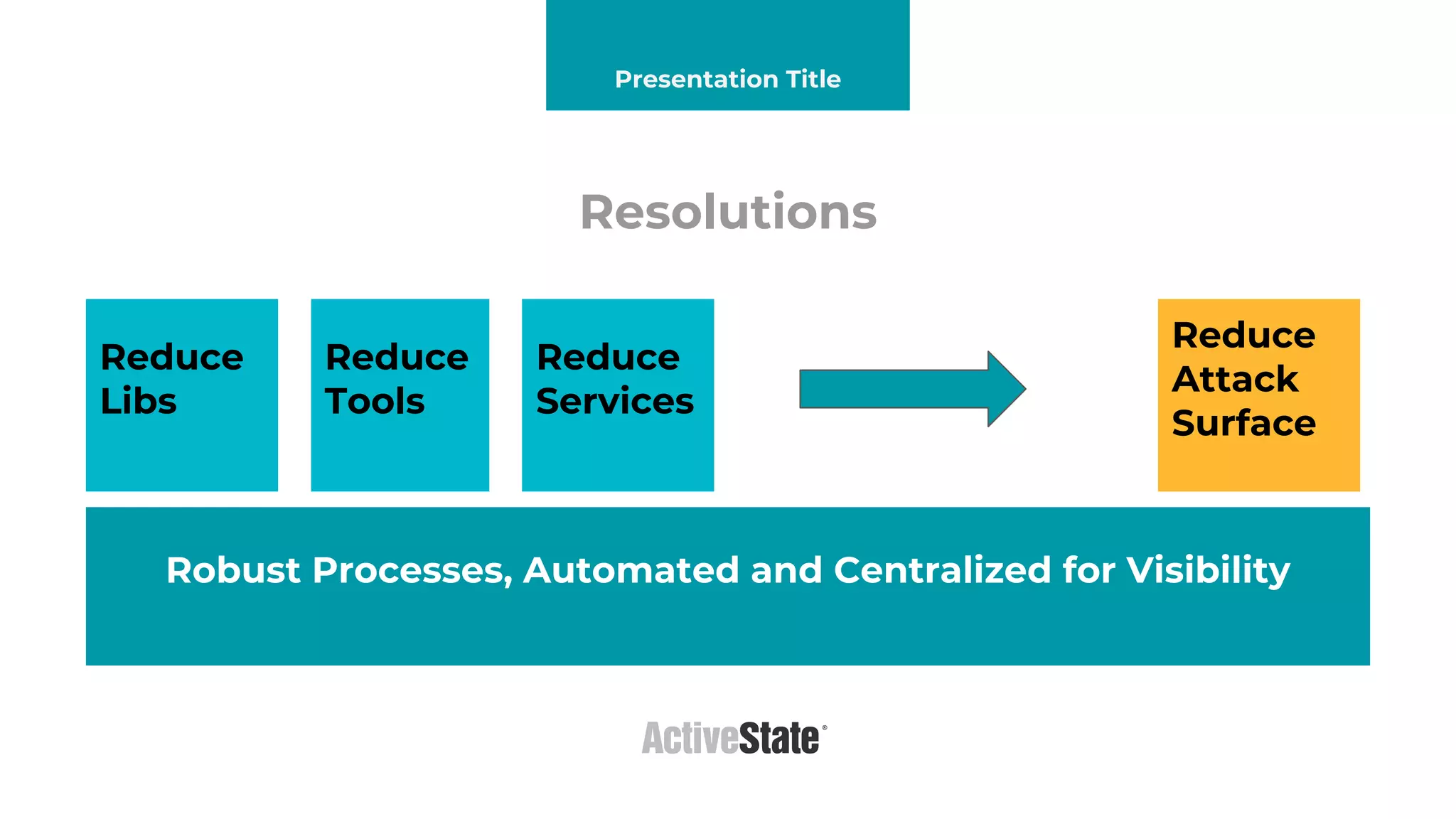
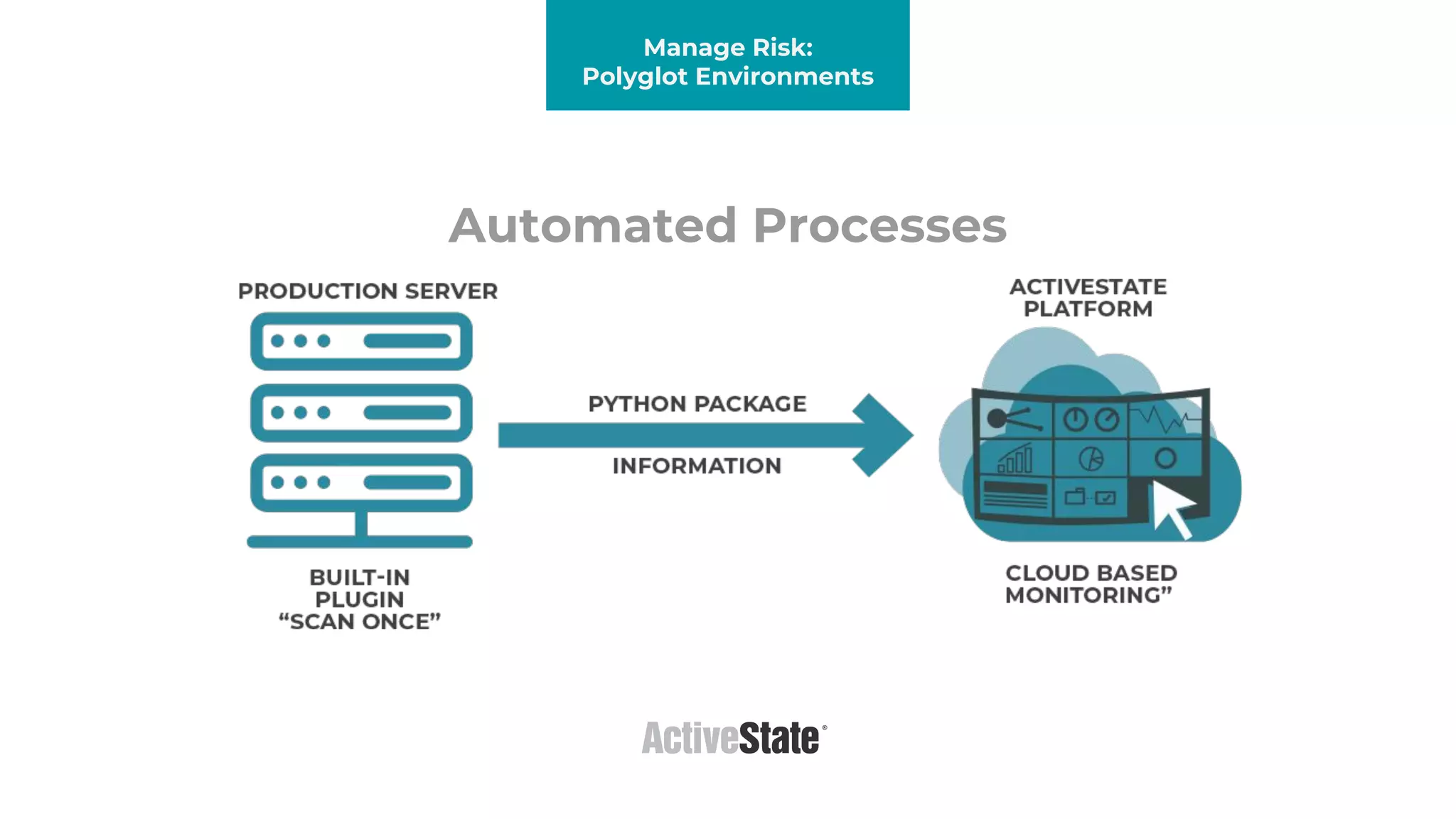
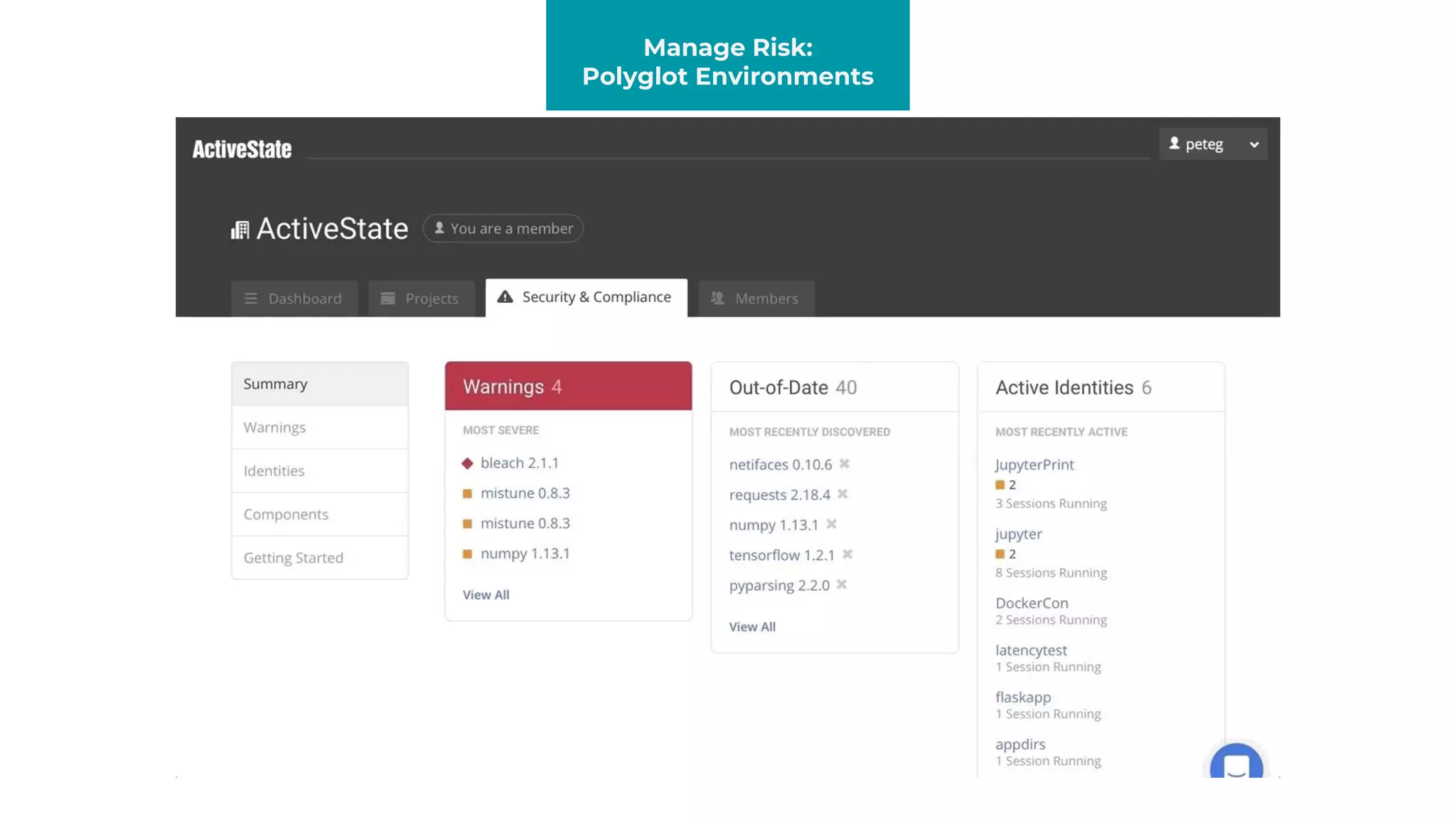
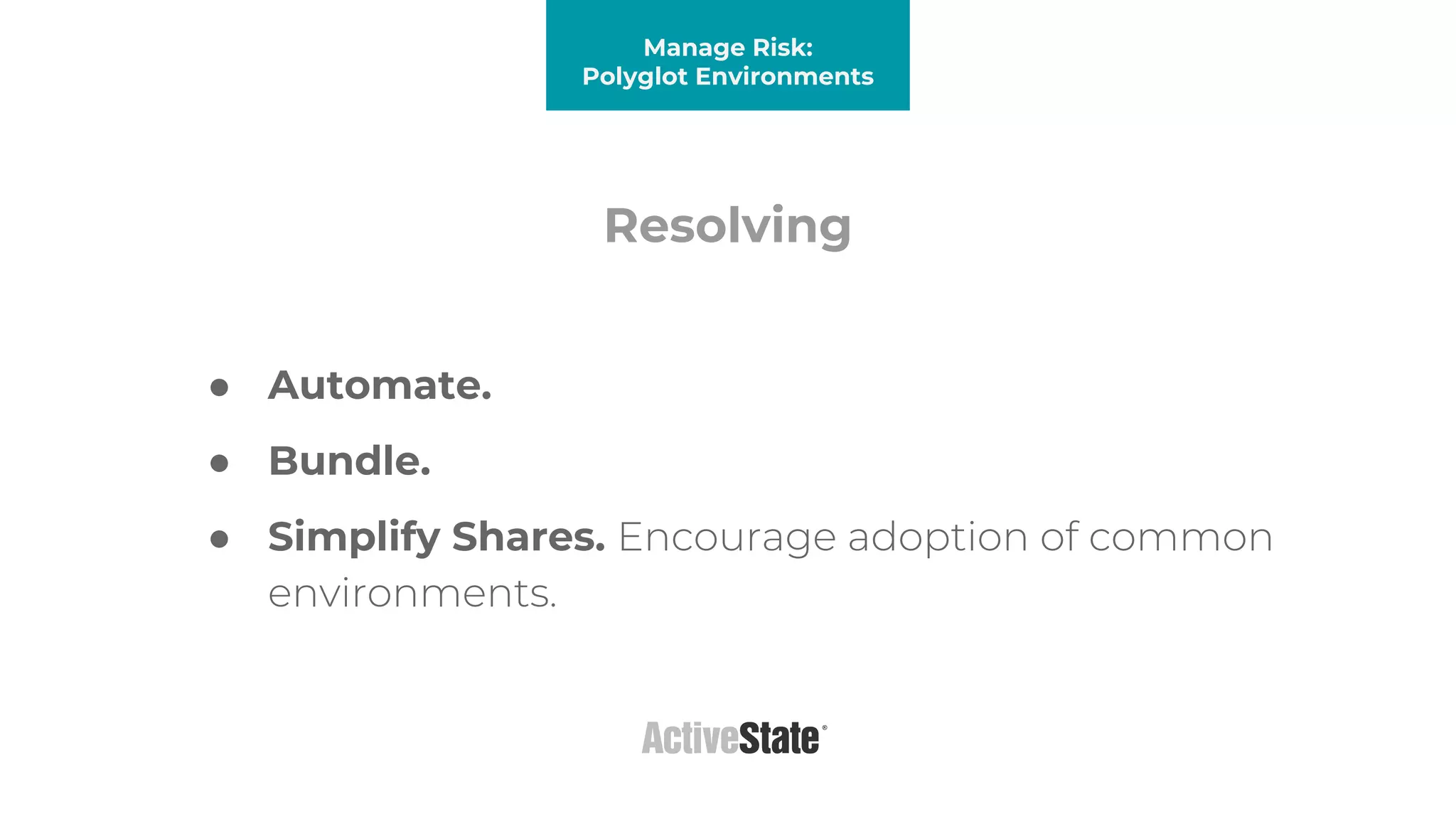
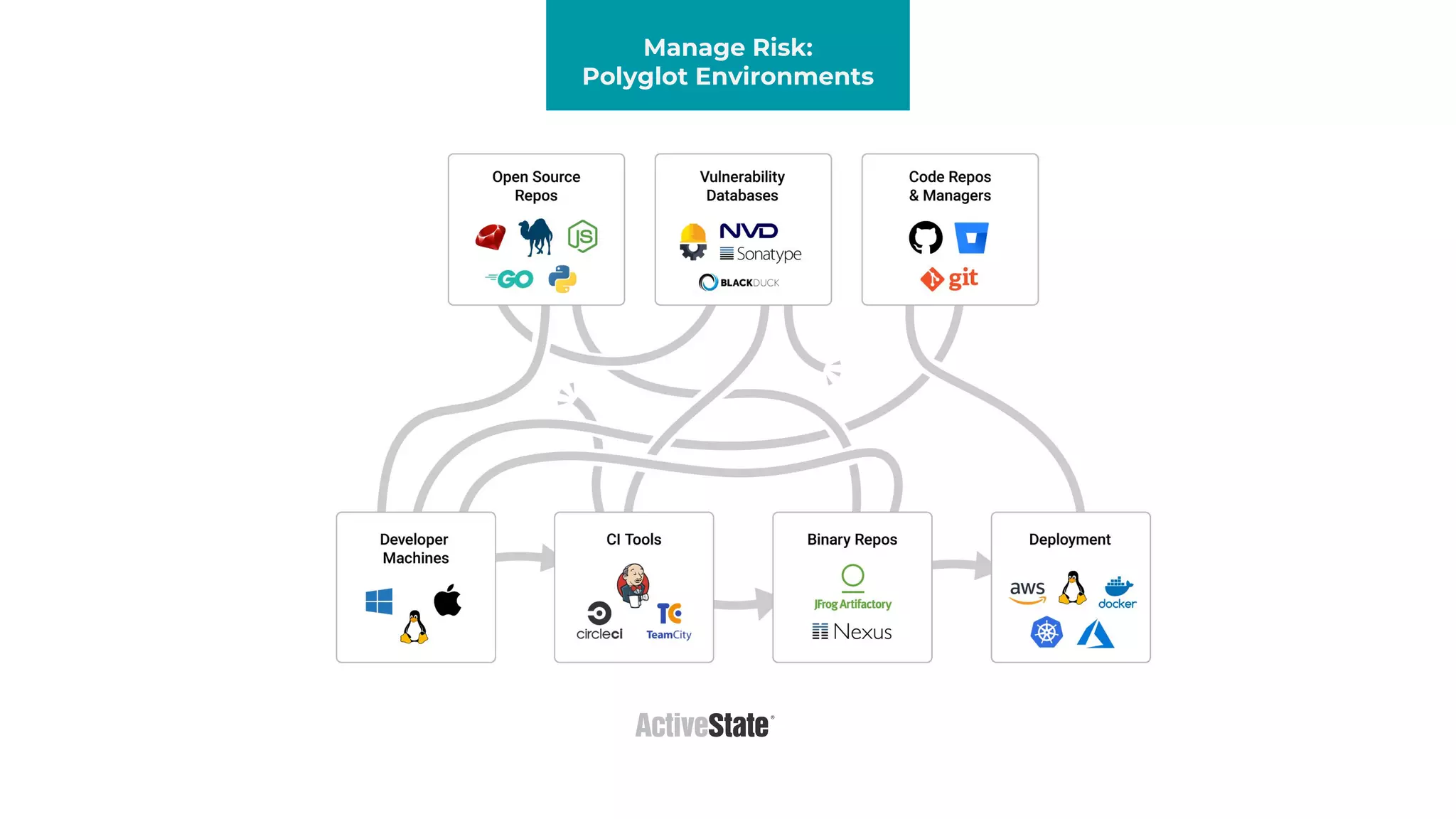
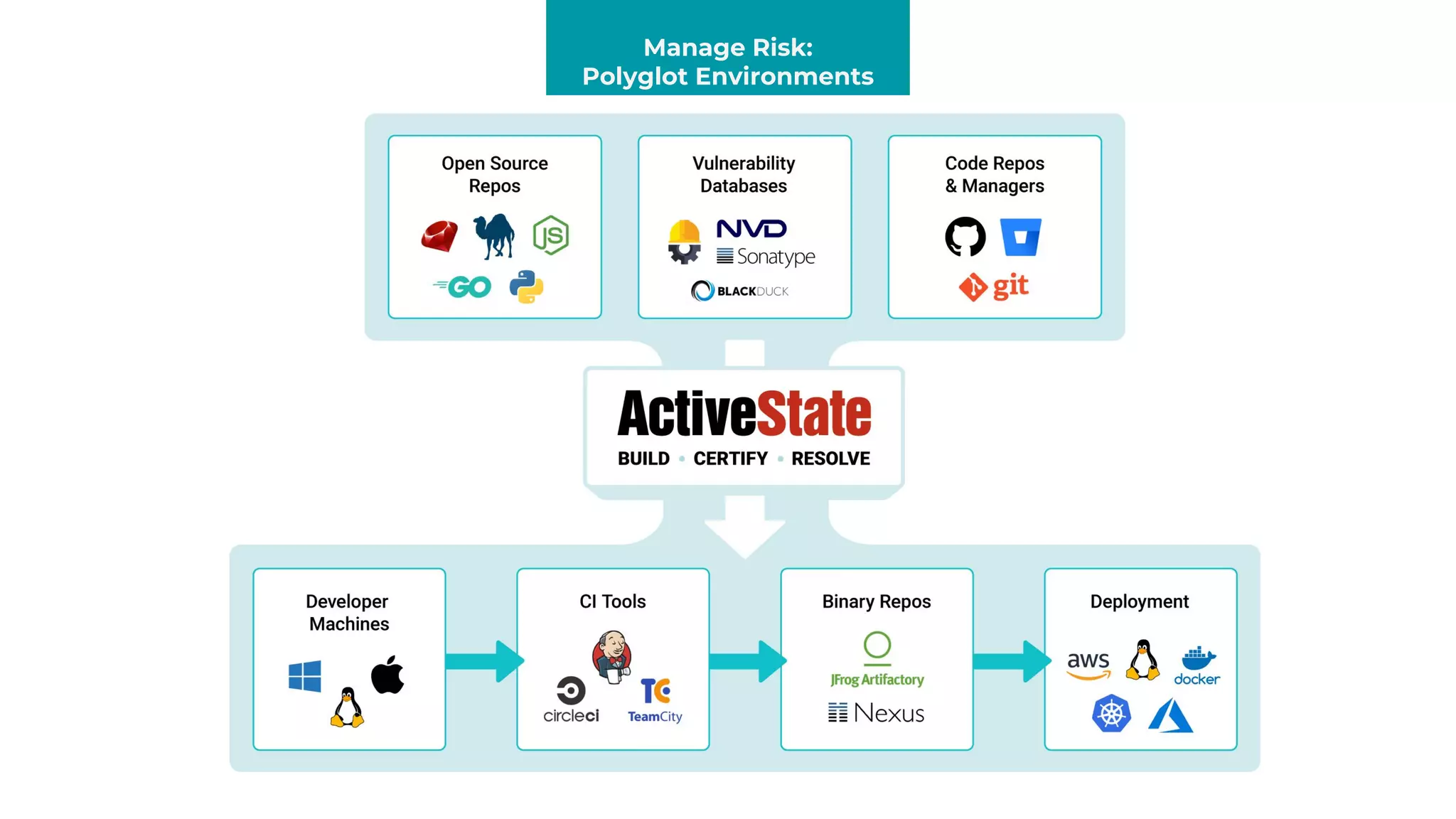
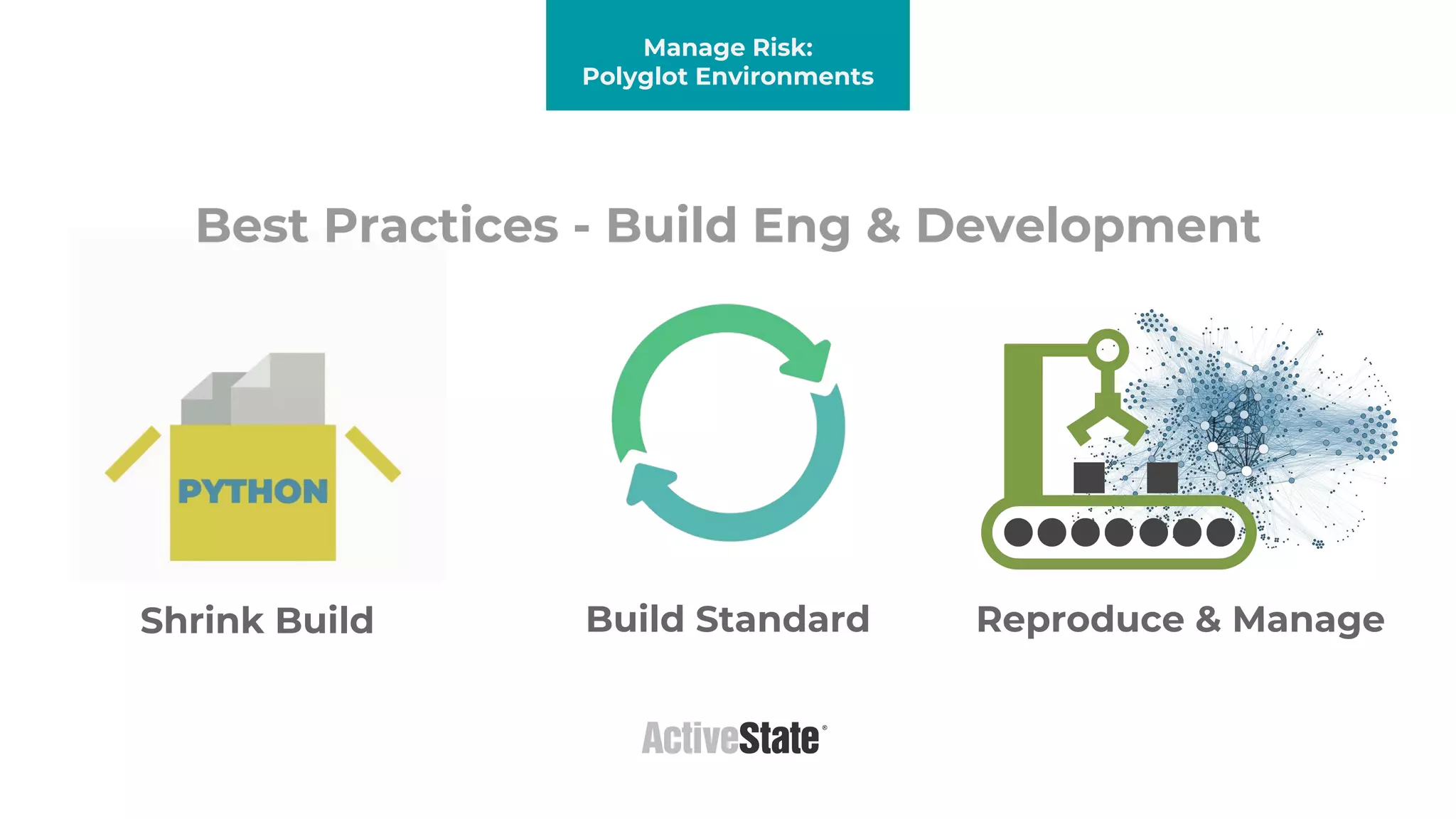
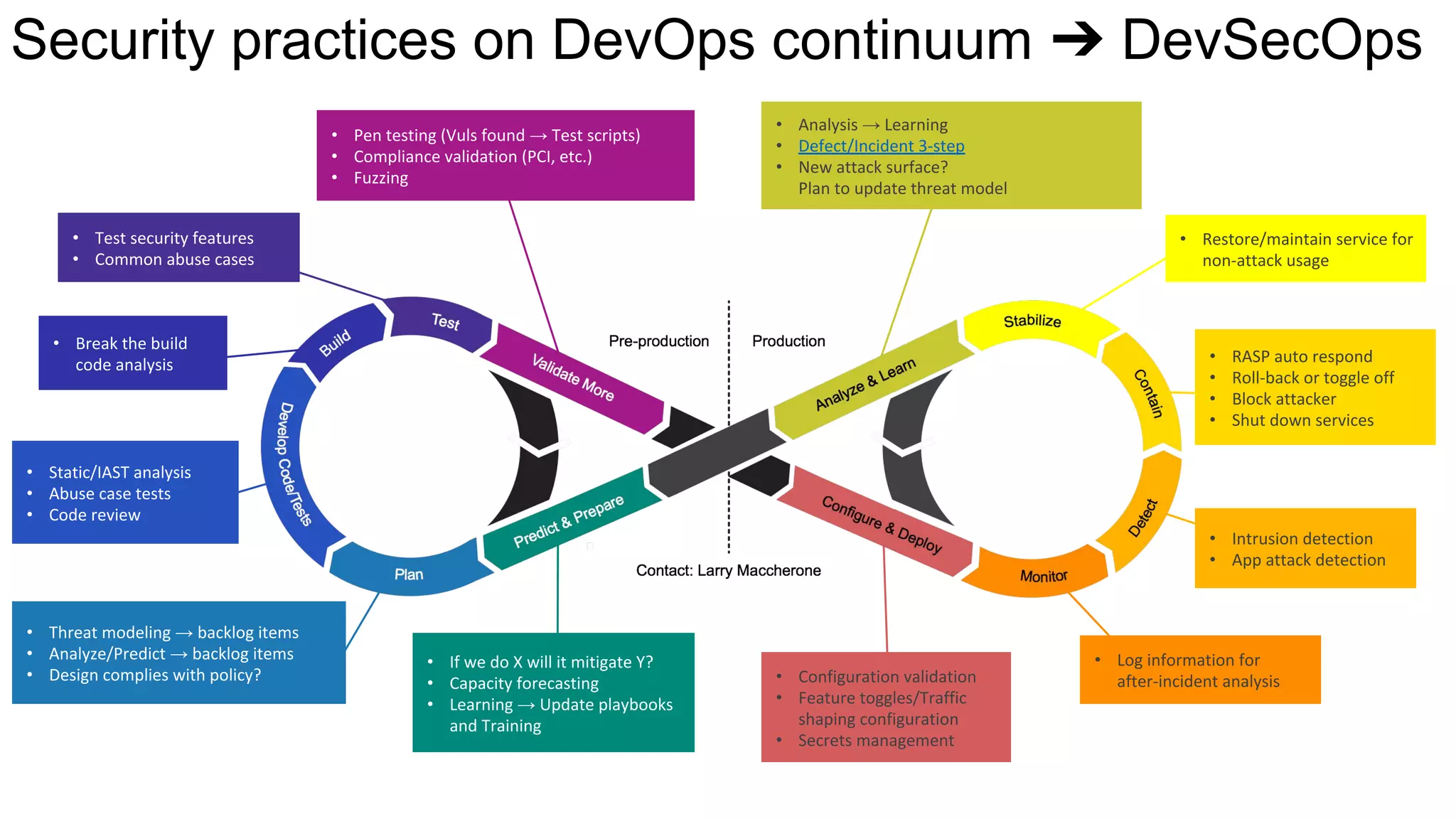
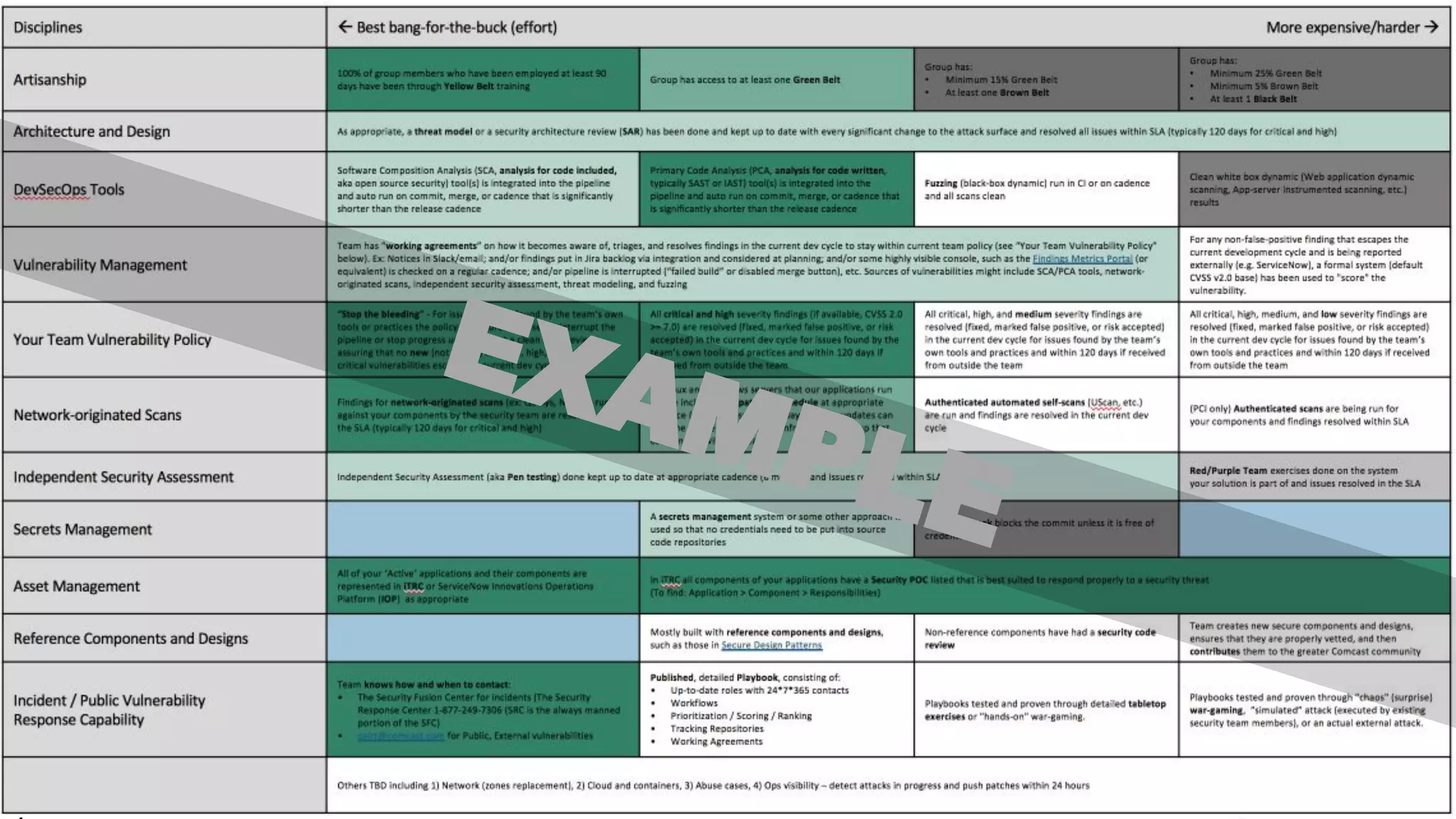
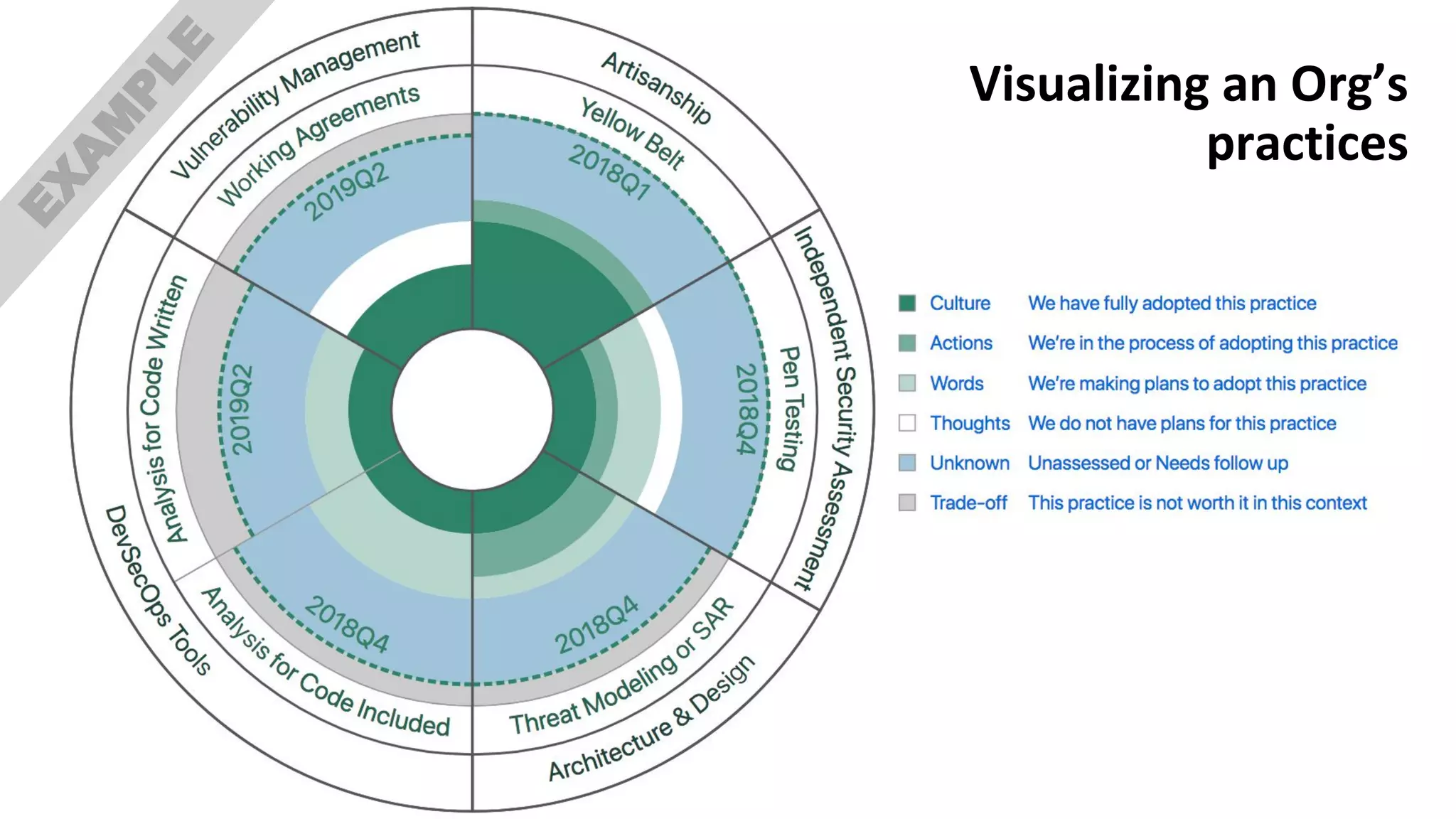
The document discusses managing risks in polyglot environments, which involve the use of multiple programming languages in software development. Key challenges include dependency management, variability in tooling, and expertise gaps, while benefits encompass faster innovation and improved flexibility in recruitment. Strategies proposed for risk management include automated processes, environment standardization, and integrating security within development practices.












![Dev[Sec]Ops is…
empowered engineering teams
taking ownership
of how their product
performs in production
[including security]](https://image.slidesharecdn.com/polyglotwebinar-181108153712/75/How-to-Manage-the-Risk-of-your-Polyglot-Environments-34-2048.jpg)