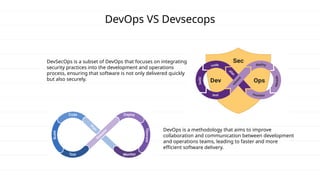
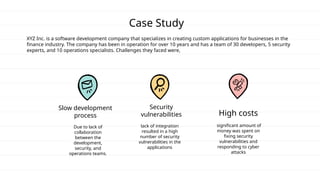
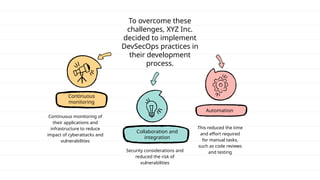
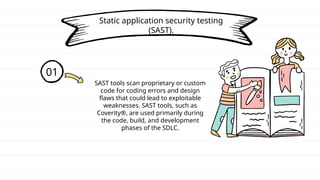
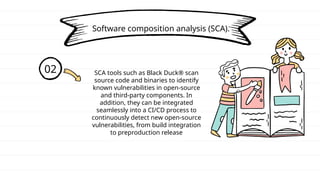
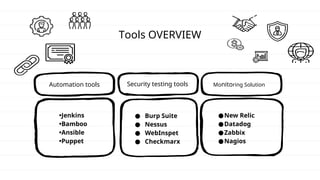
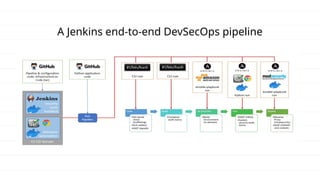
The document discusses DevSecOps, which integrates security practices into the DevOps process to enhance software security while maintaining efficient delivery. It presents a case study of XYZ Inc., illustrating the challenges faced due to security vulnerabilities, and the benefits realized through the implementation of DevSecOps practices, including improved collaboration and automation. Additionally, the document outlines tools and tutorials for effectively implementing DevSecOps in development processes.