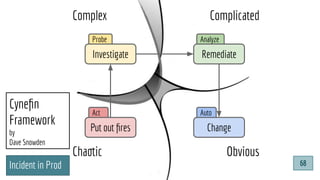
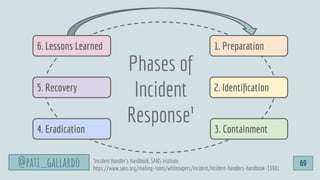
The document outlines a presentation by Patricia Aas on integrating security into software development through DevSecOps, emphasizing a collaborative approach between developers and security practices. It discusses vulnerabilities, incident response, and the importance of automated tooling and processes, including the Cynefin framework for navigating complex problems. Aas offers strategies for organizations to enhance security quality while maintaining delivery performance, suggesting that security and software quality are interconnected.


![Dev[Sec]Ops for Developers
How To Start
European Testing Conference 2020
Patricia Aas
Turtle
Sec
@pati_gallardo](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-3-320.jpg)







![@pati_gallardo
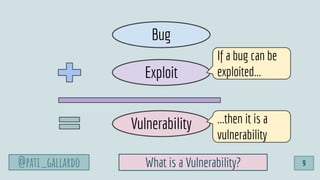
“In medical school, you are taught that if, metaphorically, there is the
sound of hoofbeats pounding towards you then it’s sensible to assume
they come from horses not zebras [...]
With House it’s the opposite. We are looking for zebras.”
‘Dr Lisa Sanders’ in ‘House M.D.’
@pati_gallardo 16](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-16-320.jpg)


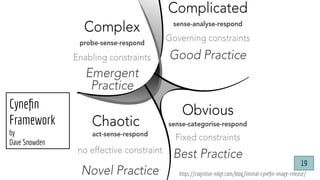
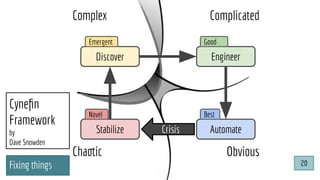
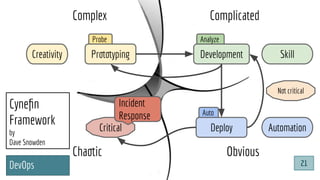
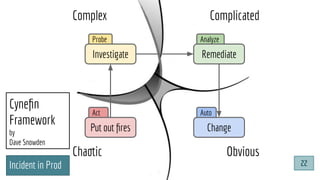
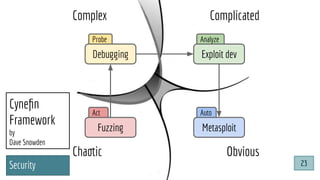
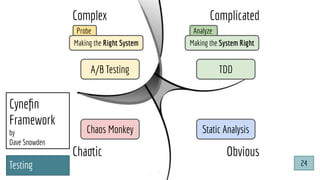
![@pati_gallardo
Dev[Sec]Ops
@pati_gallardo 25](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-25-320.jpg)
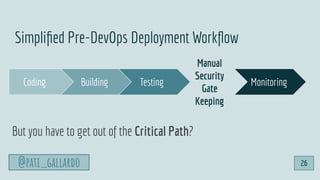

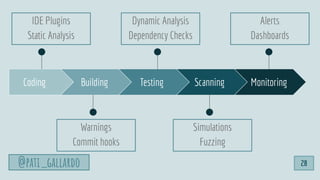



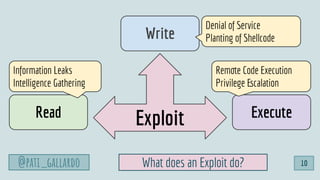
![1. Live Off the Land
2. Have Devs Build It
3. Trunk-based Development
4. Use Existing Crisis Process
5. Automate as Much as Possible
6. Infrastructure as Code
6 Dev[Sec]Ops Hacks
@pati_gallardo 35](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-35-320.jpg)

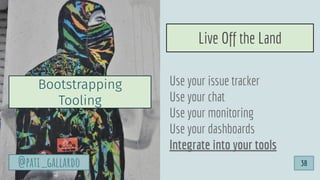
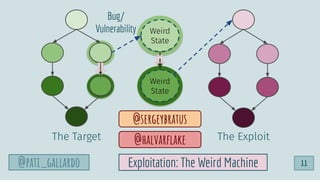
![1. Live Off the Land
2. Have Devs Build It
3. Trunk-based Development
4. Use Existing Crisis Process
5. Automate as Much as Possible
6. Infrastructure as Code
6 Dev[Sec]Ops Hacks
@pati_gallardo 39](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-39-320.jpg)
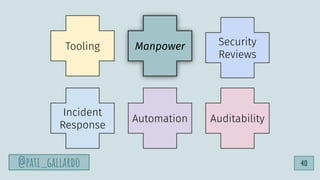


![1. Live Off the Land
2. Have Devs Build It
3. Trunk-based Development
4. Use Existing Crisis Process
5. Automate as Much as Possible
6. Infrastructure as Code
6 Dev[Sec]Ops Hacks
@pati_gallardo 43](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-43-320.jpg)
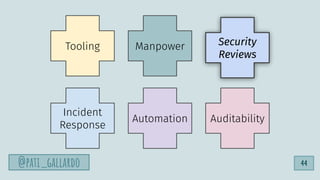


![1. Live Off the Land
2. Have Devs Build It
3. Trunk-based Development
4. Use Existing Crisis Process
5. Automate as Much as Possible
6. Infrastructure as Code
6 Dev[Sec]Ops Hacks
@pati_gallardo 47](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-47-320.jpg)
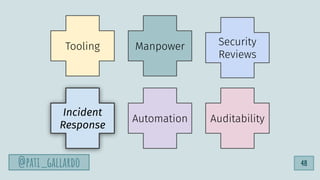


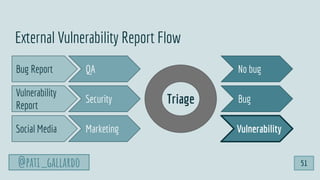



![1. Live Off the Land
2. Have Devs Build It
3. Trunk-based Development
4. Use Existing Crisis Process
5. Automate as Much as Possible
6. Infrastructure as Code
6 Dev[Sec]Ops Hacks
@pati_gallardo 55](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-55-320.jpg)
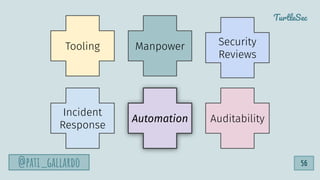

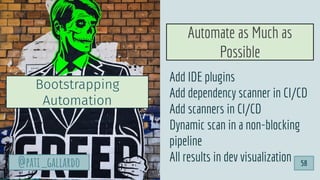
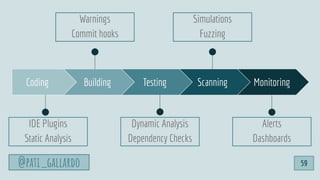
![1. Live Off the Land
2. Have Devs Build It
3. Trunk-based Development
4. Use Existing Crisis Process
5. Automate as Much as Possible
6. Infrastructure as Code
6 Dev[Sec]Ops Hacks
@pati_gallardo 60](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-60-320.jpg)


![1. Live Off the Land
2. Have Devs Build It
3. Trunk-based Development
4. Use Existing Crisis Process
5. Automate as Much as Possible
6. Infrastructure as Code
6 Dev[Sec]Ops Hacks
@pati_gallardo 64](https://image.slidesharecdn.com/devsecopsfordevelopershowtostartetc2020-200207090834/85/DevSecOps-for-Developers-How-To-Start-ETC-2020-64-320.jpg)