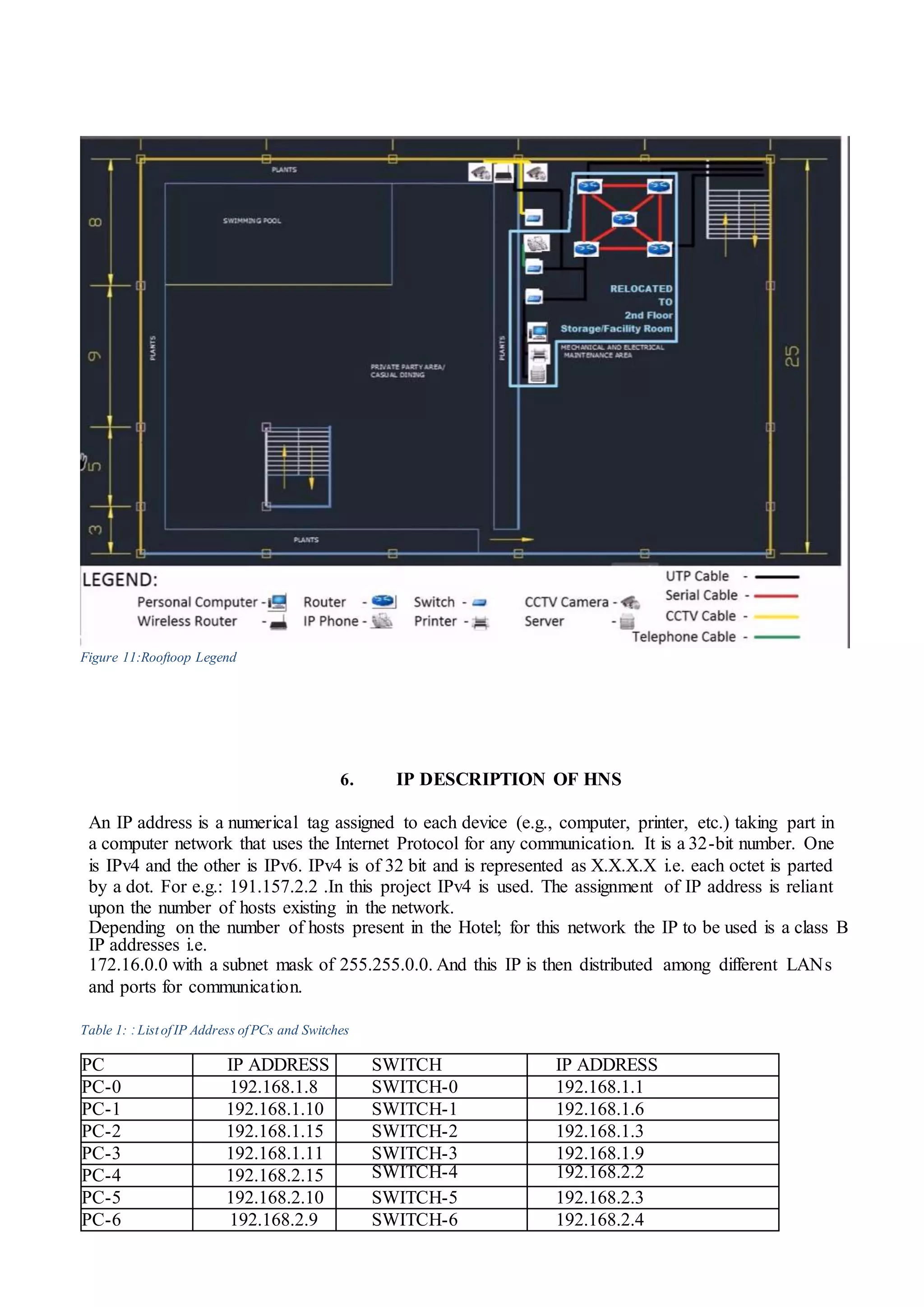
This document describes the implementation of a hotel network scenario using Cisco Packet Tracer. It includes:
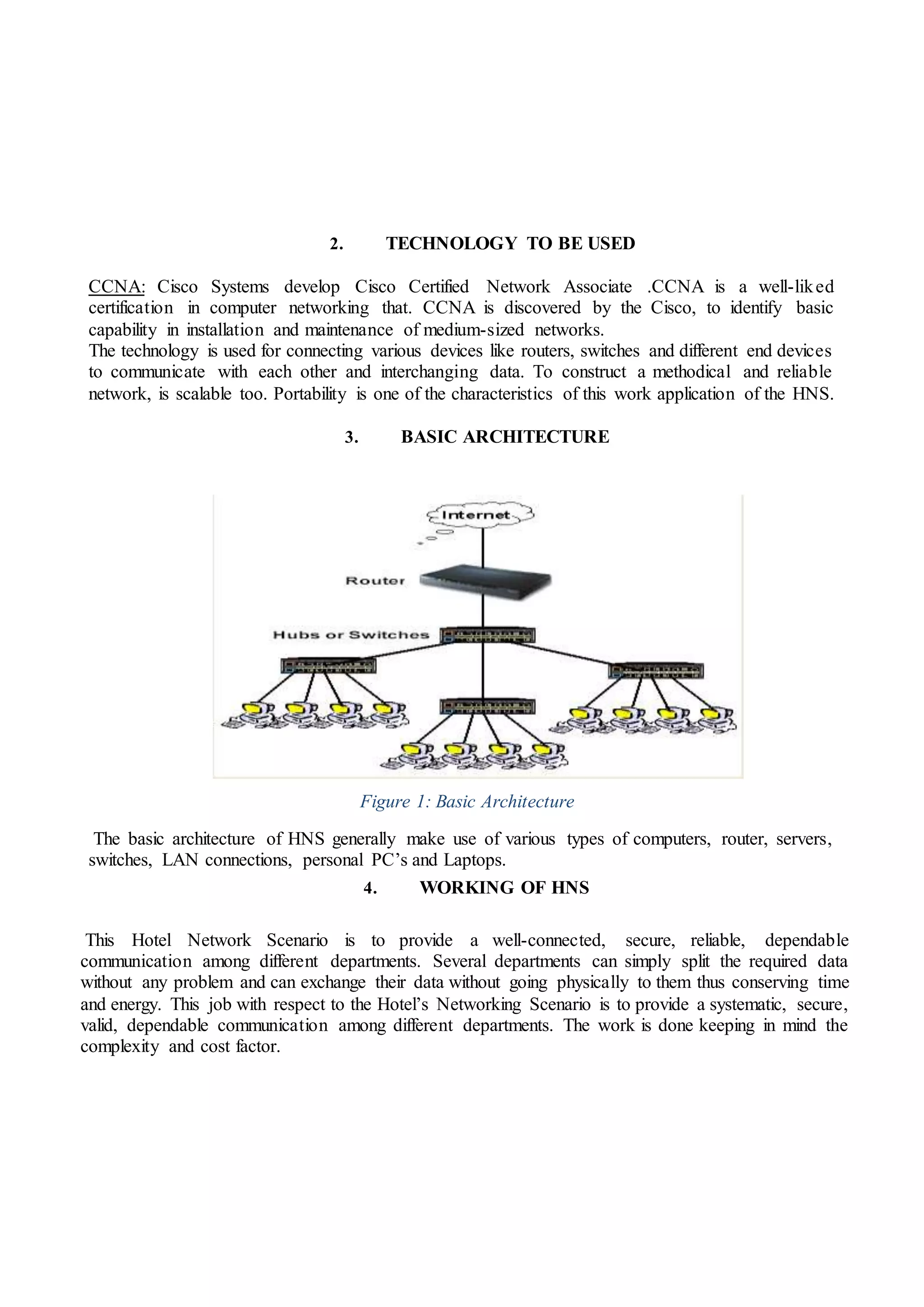
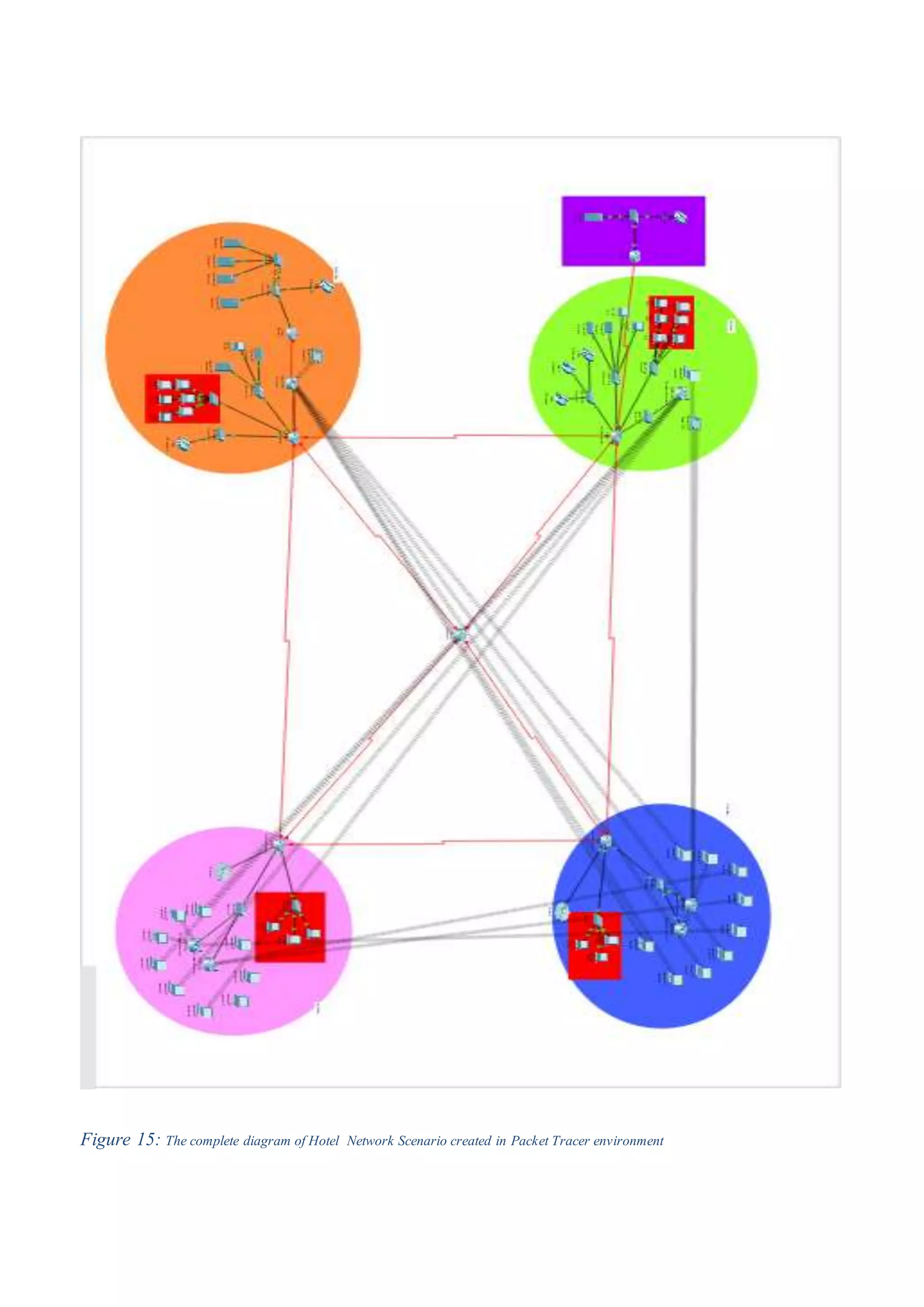
1) The basic architecture of the hotel network including routers, switches, wireless routers, IP phones, and computers across multiple floors.
2) The requirements for the network including hardware, software, interfaces, and the topology of each floor with assigned IP addresses.
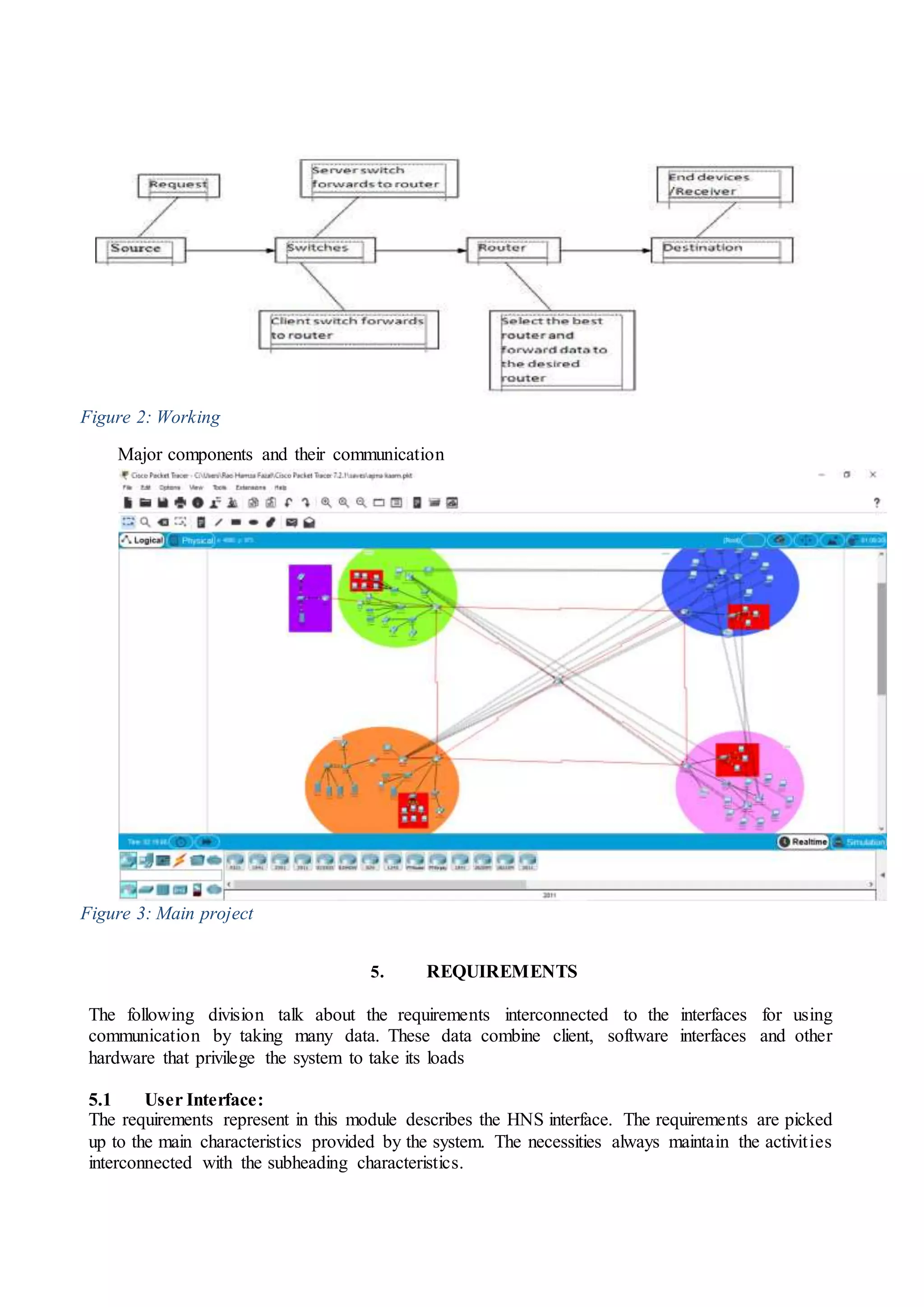
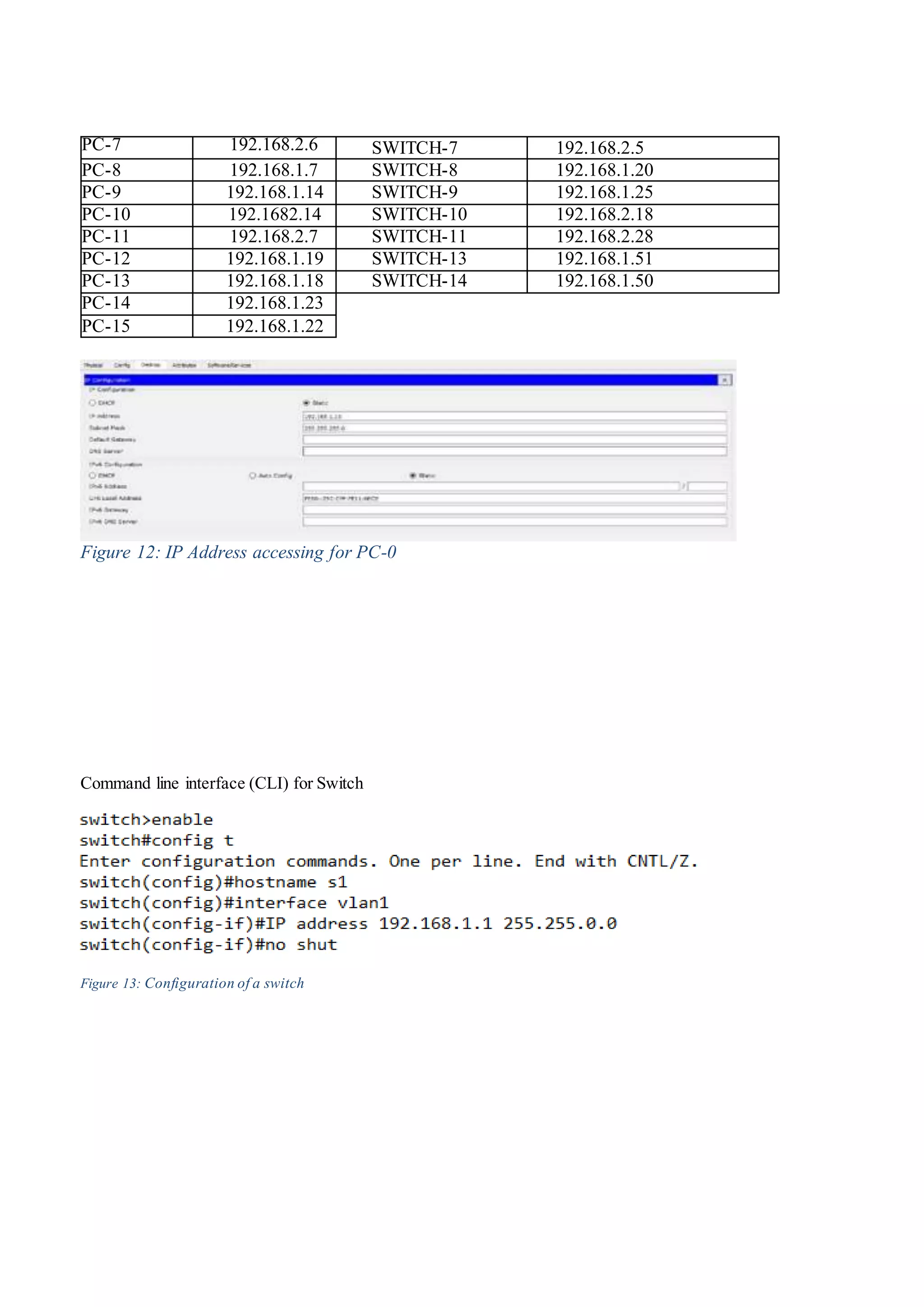
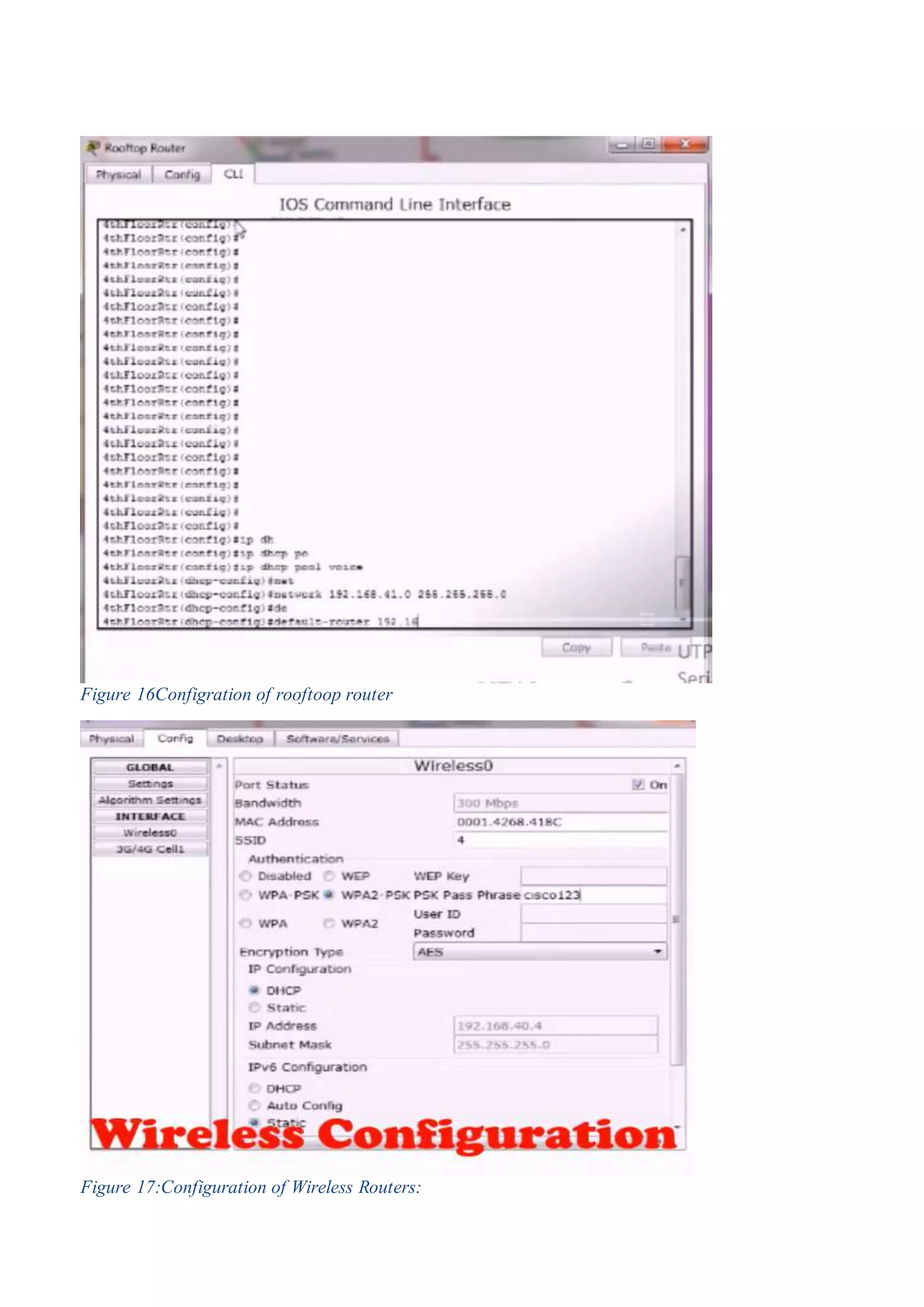
3) The configuration of network devices like routers, switches, and IP phones to set up the hotel network in Cisco Packet Tracer.