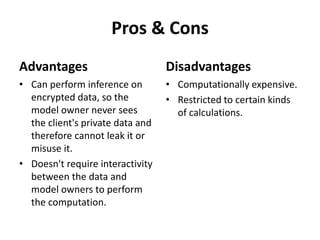
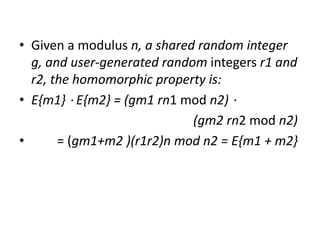
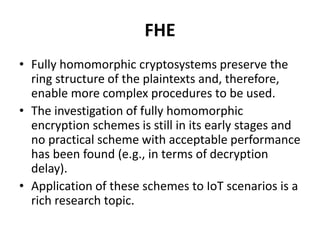
Homomorphic encryption allows for mathematical operations on encrypted data without compromising its security, enabling applications like medical image analysis and machine learning. There are different types of homomorphic encryption, such as additive and multiplicative, with fully homomorphic encryption supporting both but facing significant performance challenges. Current research continues to explore practical implementations, especially in conjunction with other privacy technologies.


![Examples of HE
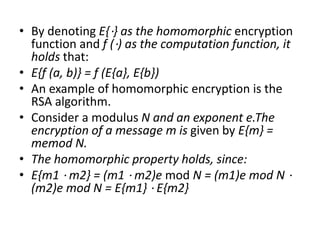
• An example of homomorphic encryption is the
RSA algorithm.
• Other examples of homomorphic encryption
schemes are
• The ECC encryption [133],
• The ElGamal cryptosystem [150] and
• The Pailler cryptosystem [151].](https://image.slidesharecdn.com/homomorphicencryptionscheme-231022145217-b602255d/85/Homomorphic-Encryption-Scheme-pptx-5-320.jpg)