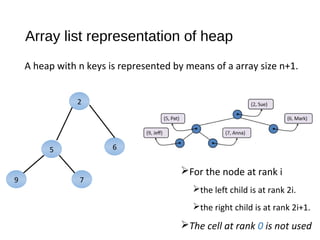
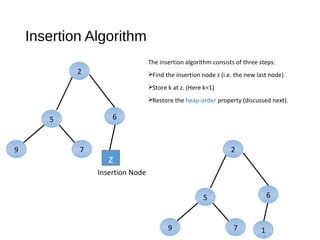
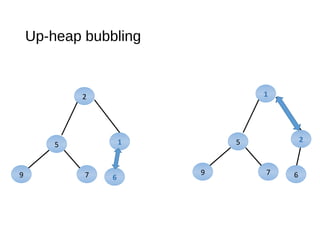
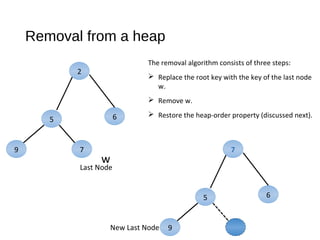
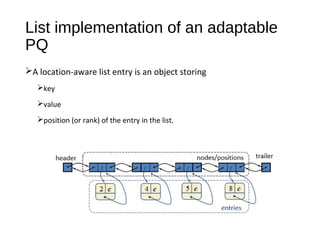
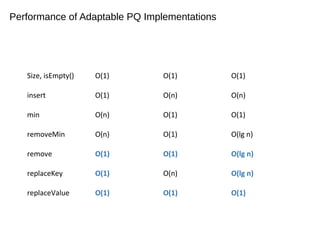
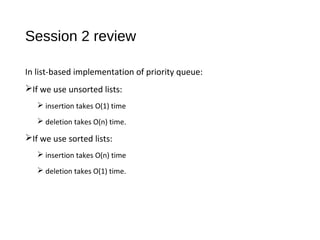
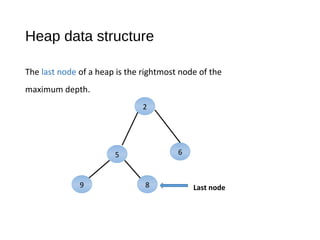
The document discusses heaps and adaptable priority queues, outlining their properties, operations, and performance across various implementations, including unsorted lists, sorted lists, and heaps. It details the insertion and removal algorithms, the structure of a heap as a binary tree, and how heap-sort operates within a time complexity of O(n log n). Additionally, it introduces adaptable priority queues used in specific applications, emphasizing their functionalities and efficiency in managing priority queue entries.





![Height of heap
A heap storing n keys has height h = [lg n]
For each depth i < h , there are 2i nodes and
at least one node at depth h. Thus,
n ≥ 20 + 21+ 22 + ... + 2h-1 + 1
≥ 1 + 2 + 4 + ... + 2h-1 + 1
≥ 2h
Which gives, h ≤ lgn.](https://image.slidesharecdn.com/heaps-170508114837/85/Heaps-Adaptable-priority-Queues-8-320.jpg)