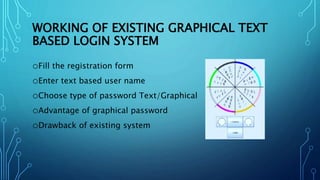
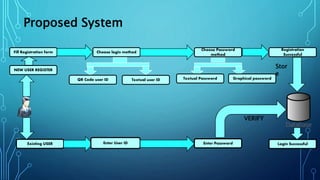
This document proposes a new shoulder surfing resistant graphical password scheme. It begins with an introduction to passwords and why they are needed for authentication. It then discusses different types of existing graphical passwords like passfaces, passpoints and draw-a-secret (DAS). The document outlines the working of current text-based graphical login systems and their drawbacks. It proposes a new login system using QR codes and password encryption to address these issues. It describes the current and future applications of this system and the hardware and software requirements. The document discusses the advantages of the new system in reducing shoulder surfing attacks and sending alerts on wrong attempts. It concludes that the proposed text-based color password scheme satisfies usability and security requirements.