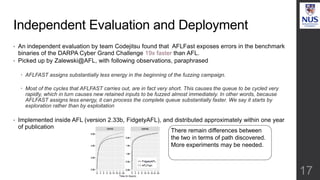
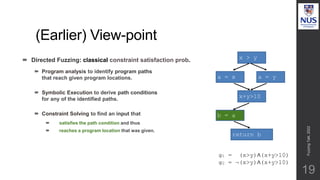
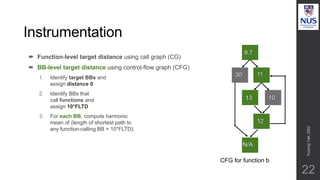
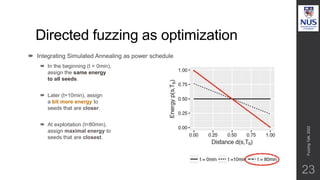
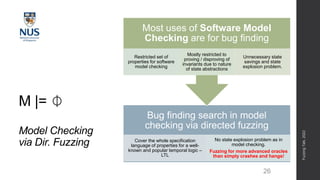
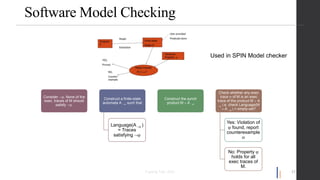
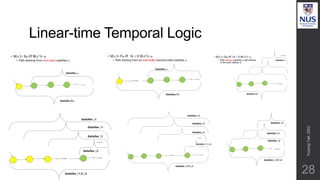
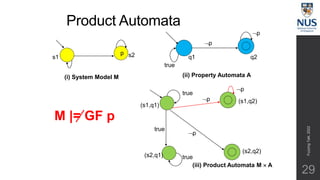
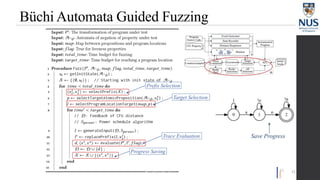
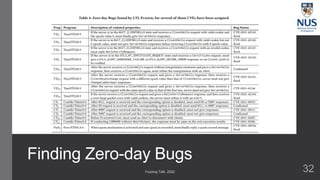
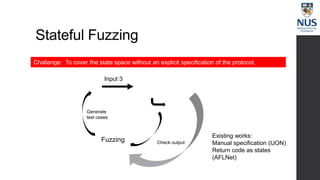
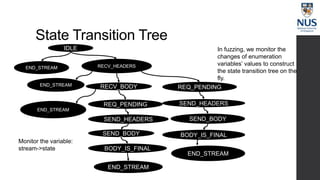
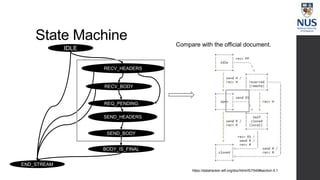
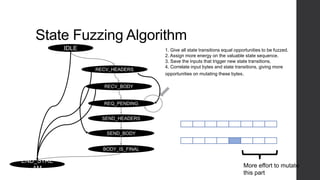
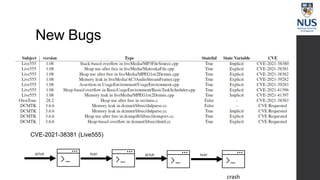
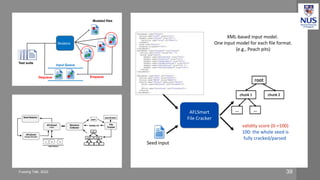
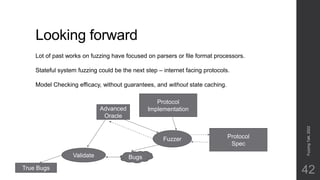
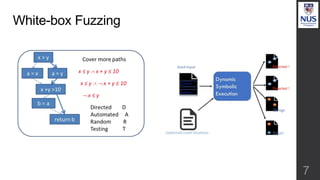
The document discusses advances in fuzz testing, focusing on different techniques such as grey-box and directed fuzzing to enhance vulnerability detection in software. It highlights the importance of using structured inputs and various mutation strategies to improve the efficiency of fuzzing, as exemplified by the success of tools like AFL and its variants. The presentation emphasizes the integration of symbolic execution elements with fuzz testing to achieve better coverage and detection of vulnerabilities in software systems.



![Who cares?
4
A team of hackers won $2 million by
building a machine that could hack better
than they could
Read more at
DARPA Cyber Grand
Challenge
Automation of Security
[detecting and fixing
vulnerabilities in binaries
automatically]
Fuzzing
Talk,
2022](https://image.slidesharecdn.com/fuzzing-220617065914-c2a5c01c/85/Fuzzing-pptx-4-320.jpg)
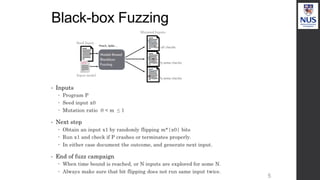
![Lack of specifications
• Many programs take in structured inputs
PDF Reader, library for manipulating TIFF, PNG images
Compilers which take in programs as input
Web-browsers, ...
• Generating a completely random input will likely crash the application with little
insight gained about the underlying vulnerability.
• Instead take a legal well-formed PDF file and mutate it!
Does not depend on program at all [nature of BB fuzzing]
Does not even depend on input structure.
Yet can leverage complex input structure by starting with a well-formed seed and
minimally modifying it.
Fuzzing
Talk,
2022
6](https://image.slidesharecdn.com/fuzzing-220617065914-c2a5c01c/85/Fuzzing-pptx-6-320.jpg)
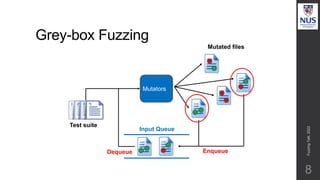
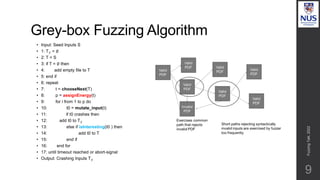


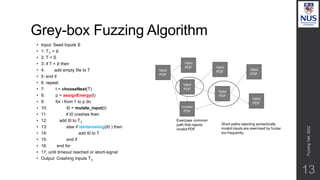

![Prioritize low probability paths
15
Use grey-box fuzzer which keeps track of path id for a test.
Find probabilities that fuzzing a test t which exercises π leads to an
input which exercises π’
Higher weightage to low probability paths discovered, to gravitate to
those -> discover new paths with minimal effort.
π π'
1 void crashme (char* s) {
2 if (s[0] == ’b’)
3 if (s[1] == ’a’)
4 if (s[2] == ’d’)
5 if (s[3] == ’!’)
6 abort ();
7 }
p
Fuzzing
Talk,
2022](https://image.slidesharecdn.com/fuzzing-220617065914-c2a5c01c/85/Fuzzing-pptx-15-320.jpg)