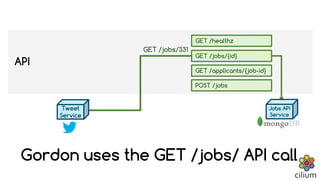
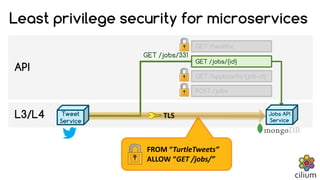
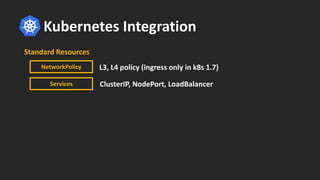
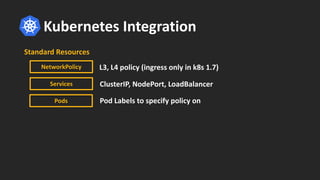
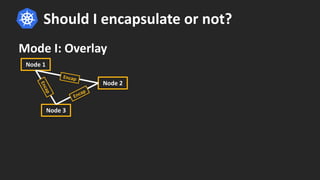
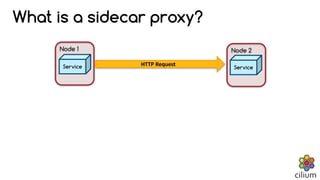
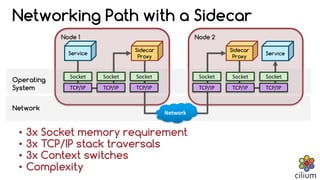
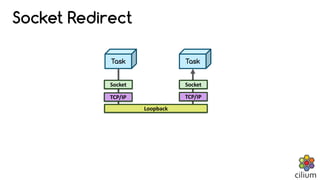
The document discusses how BPF and XDP are revolutionizing network security and performance for microservices. BPF allows profiling, tracing, and running programs at the network driver level. It also enables highly performant networking functions like DDoS mitigation using XDP. Cilium uses BPF to provide layer 3-7 network security for microservices with policies based on endpoints, identities, and HTTP protocols. It integrates with Kubernetes to define network policies and secure microservice communication and APIs using eBPF programs for filtering and proxying.






![BPF Revolution #2: XDP - DDoS mitigation
Metric iptables / ipset XDP
DDoS rate [packets/s] 11.6M 11.6M
Drop rate [packets/s] 7.1M 11.6M
Time to load rules [time] 3 min 20 sec 31 sec
Latency under load [ms] 2.3ms 0.1ms
Throughput under DDoS [Gbit/s] 0.014 6.5
Requests/s under DDoS [kReq/s] 0.28 82.8
Sender: Send 64B packets as fast as possible è Receiver: Drop as fast as possible
Source: Daniel Borkmann’s presentation yesterday:
http://schd.ws/hosted_files/ossna2017/da/BPFandXDP.pdf](https://image.slidesharecdn.com/cilium-networksecurityformicroservices-170913231349/85/Cilium-Network-security-for-microservices-7-320.jpg)