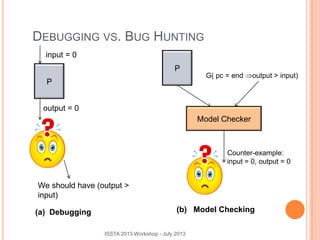
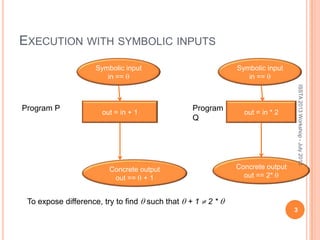
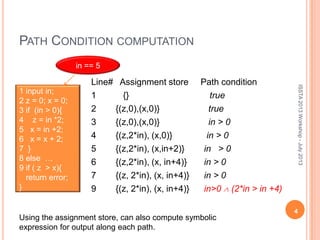
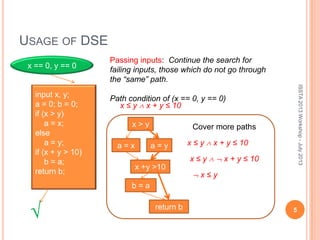
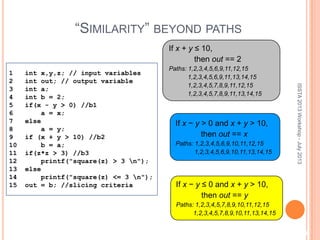
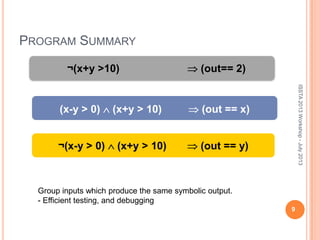
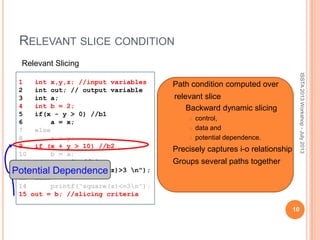
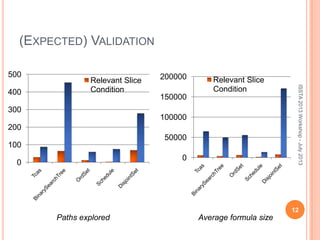
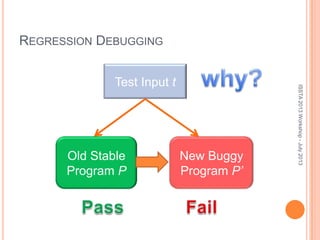
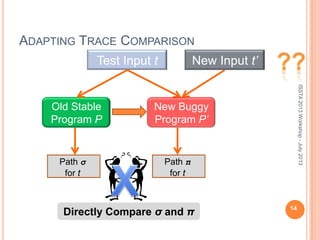
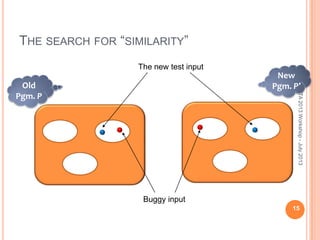
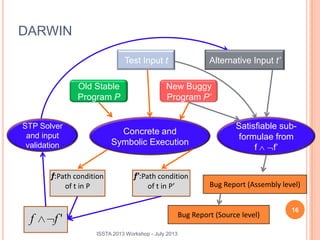
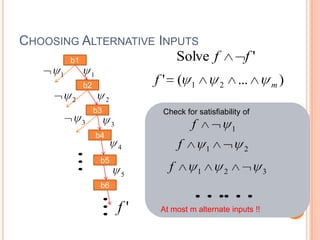
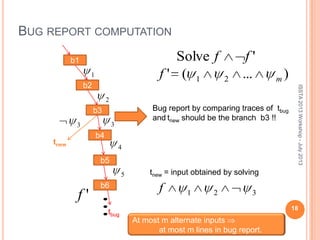
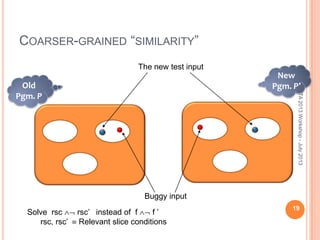
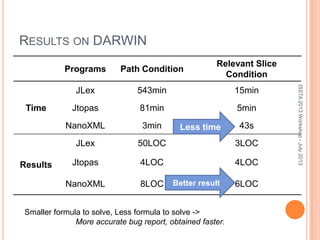
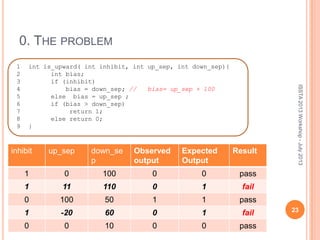
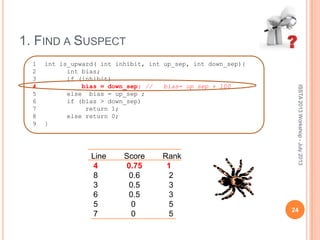
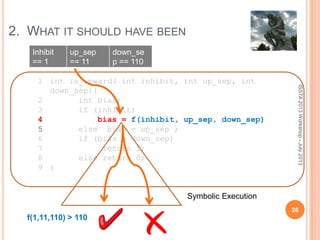
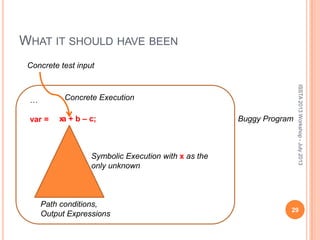
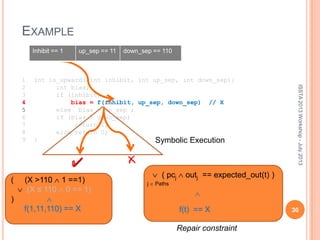
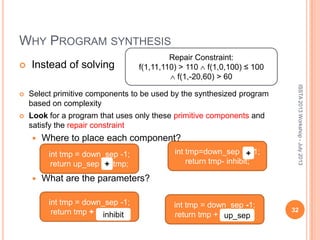
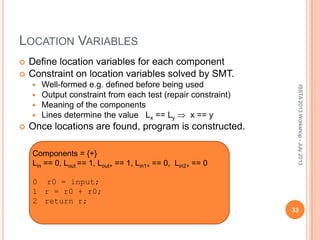
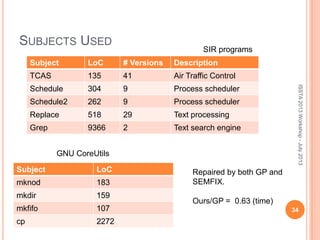
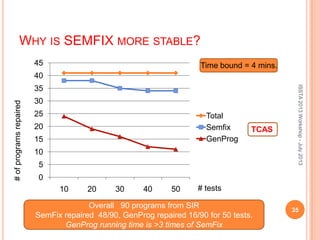
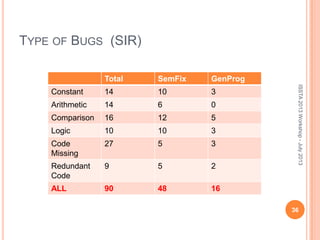
This document discusses using symbolic reasoning and dynamic symbolic execution to help with program debugging, repair, and regression testing. It presents an approach where inputs are grouped based on producing the same symbolic output to more efficiently test programs and debug issues. Relevant slice conditions are computed to precisely capture input-output relationships and group related paths. This technique aims to find a notion of "similarity" between inputs and executions that is coarser than just considering program paths. The approach is demonstrated on example programs and shown to reduce debugging time compared to only considering program paths.











![STEPPING BACK, PERSPECTIVE
[Obvious] Level of automation
Never completely ~ Programming environments!
Program synthesis likely to play a useful role.
Is debugging required?
Testing search and repair combined.
Avoid statistical fault localization.
Find the location to fix via symbolic reasoning and
MAXSAT – not clear about quality of repair produced.
Can generate suggestions instead of repairs?
What is a repair (or not) may depend on context.
38
ISSTA2013Workshop-July2013](https://image.slidesharecdn.com/issta13-workshop-130715134638-phpapp01/85/Issta13-workshop-on-debugging-38-320.jpg)

