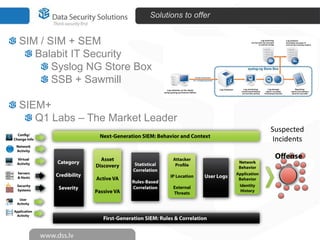
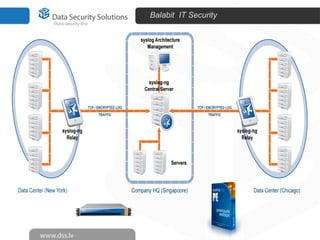
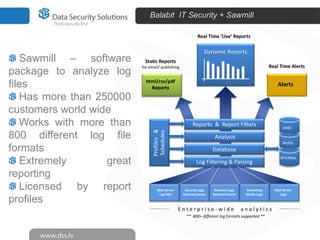
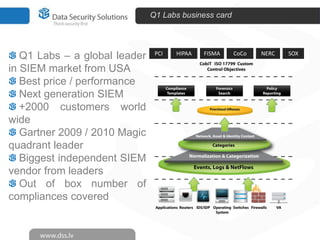
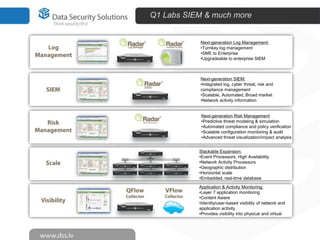
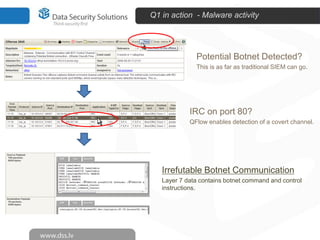
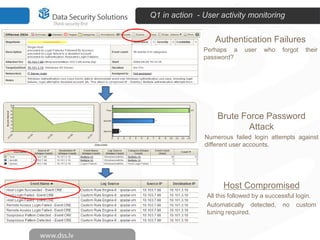
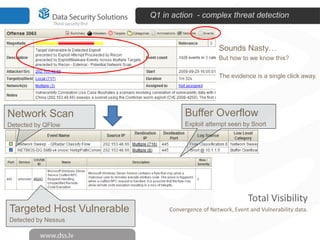
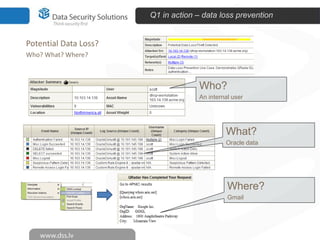
The document discusses innovations in data security, focusing on log management and SIEM (Security Information and Event Management). It highlights the increasing prevalence of cybercrime and the necessity for organizations to implement effective log management systems to mitigate vulnerabilities. The presentation also reviews market analysis, critical capabilities of various solutions, and outlines the importance of compliance with standards and regulations.