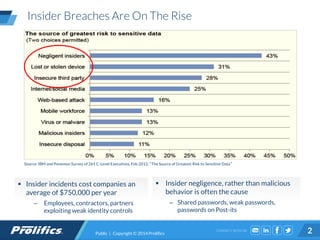
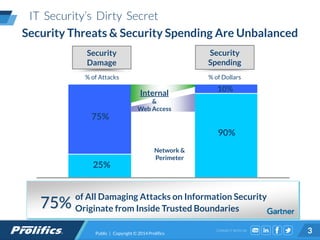
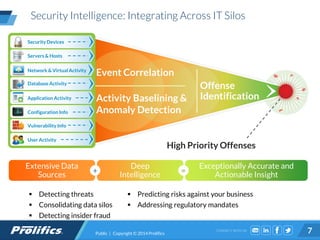
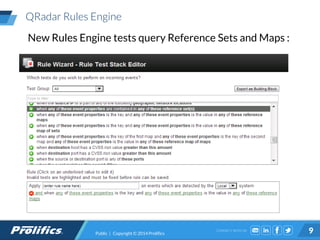
The document discusses the rising threat of insider breaches in organizations, which often result from negligence rather than malicious intent, costing companies an average of $750,000 annually. It emphasizes the importance of identity intelligence in managing risks associated with user activity and integrating security intelligence to detect threats, insider fraud, and ensure appropriate access controls. The text also highlights the evolution of security management from static, compliance-driven processes to dynamic, real-time analytics capable of providing actionable insights.