Embed presentation
Download to read offline


















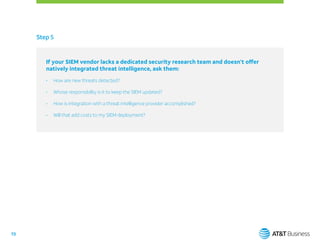


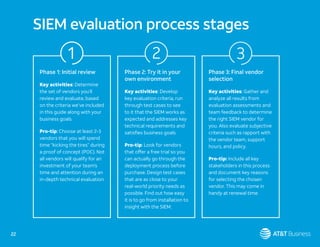




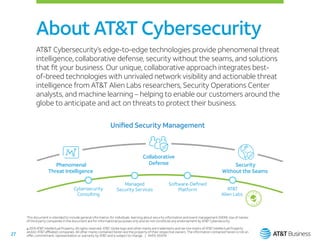
This document serves as an evaluator's guide for selecting a Security Information and Event Management (SIEM) solution, outlining six crucial steps for success. It emphasizes the importance of understanding specific use cases, identifying monitored environments, and integrating threat intelligence and automation into security operations. Ultimately, it aims to assist organizations in effectively preparing for SIEM deployment to enhance threat detection and management.


























