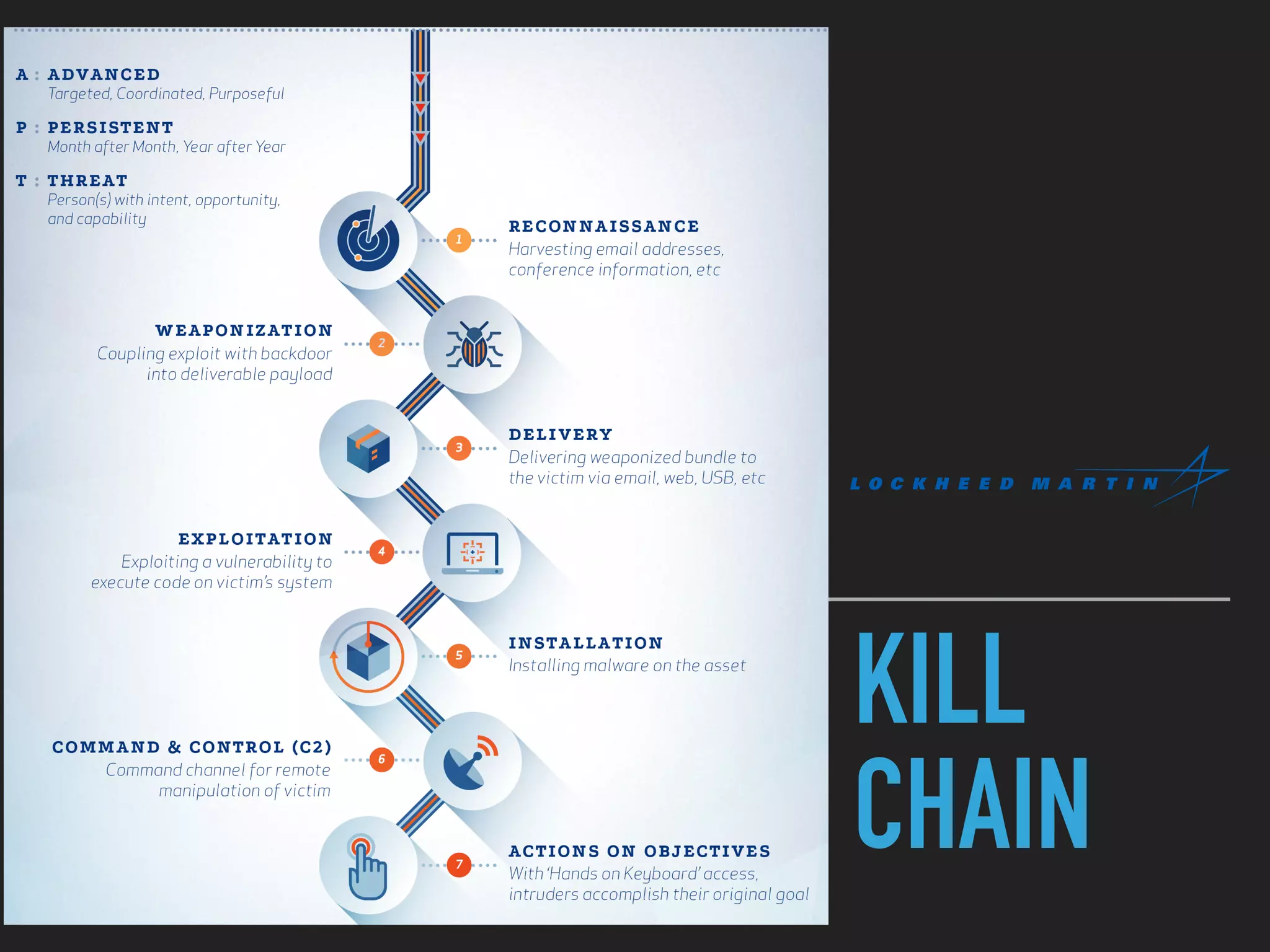
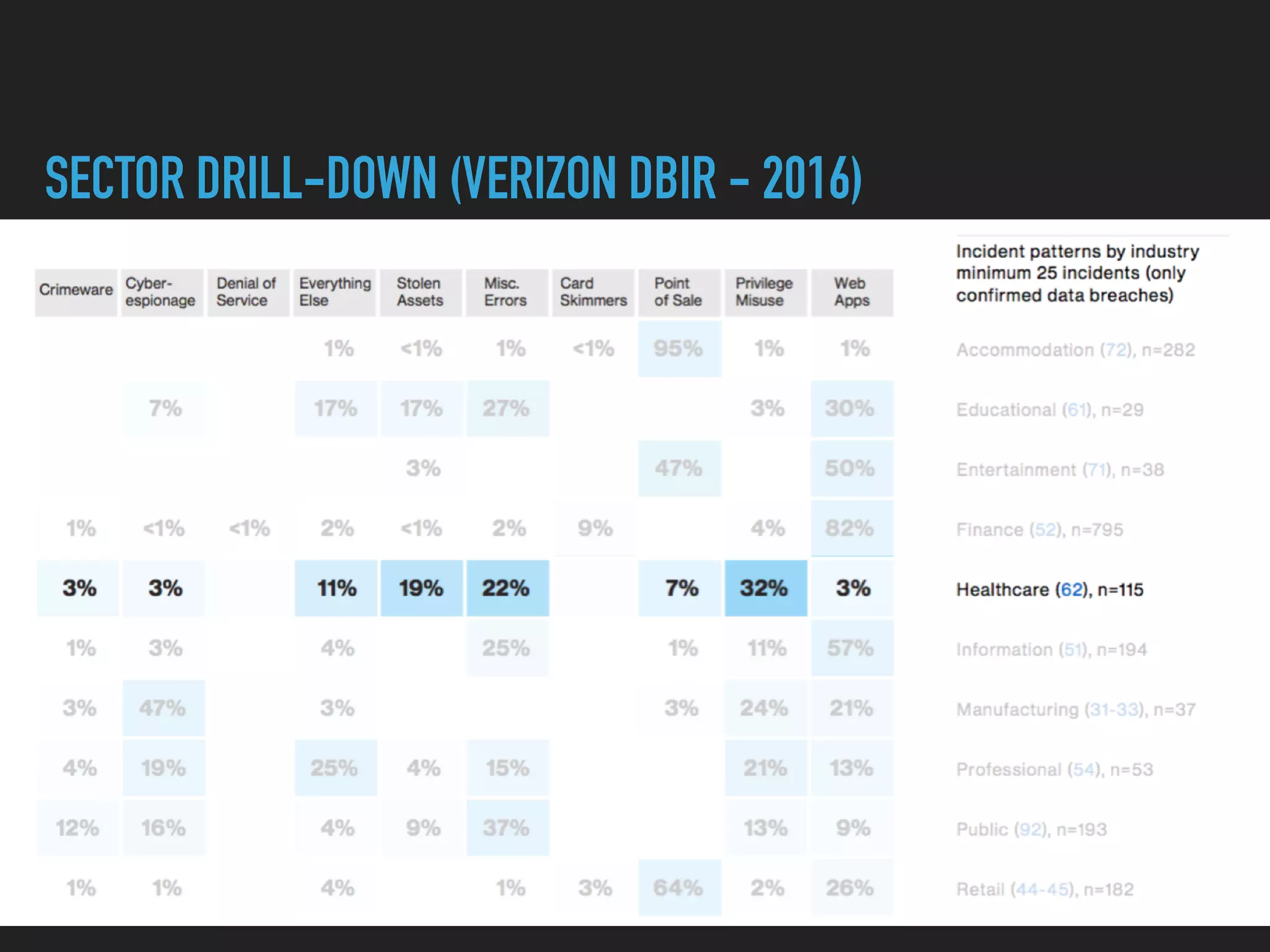
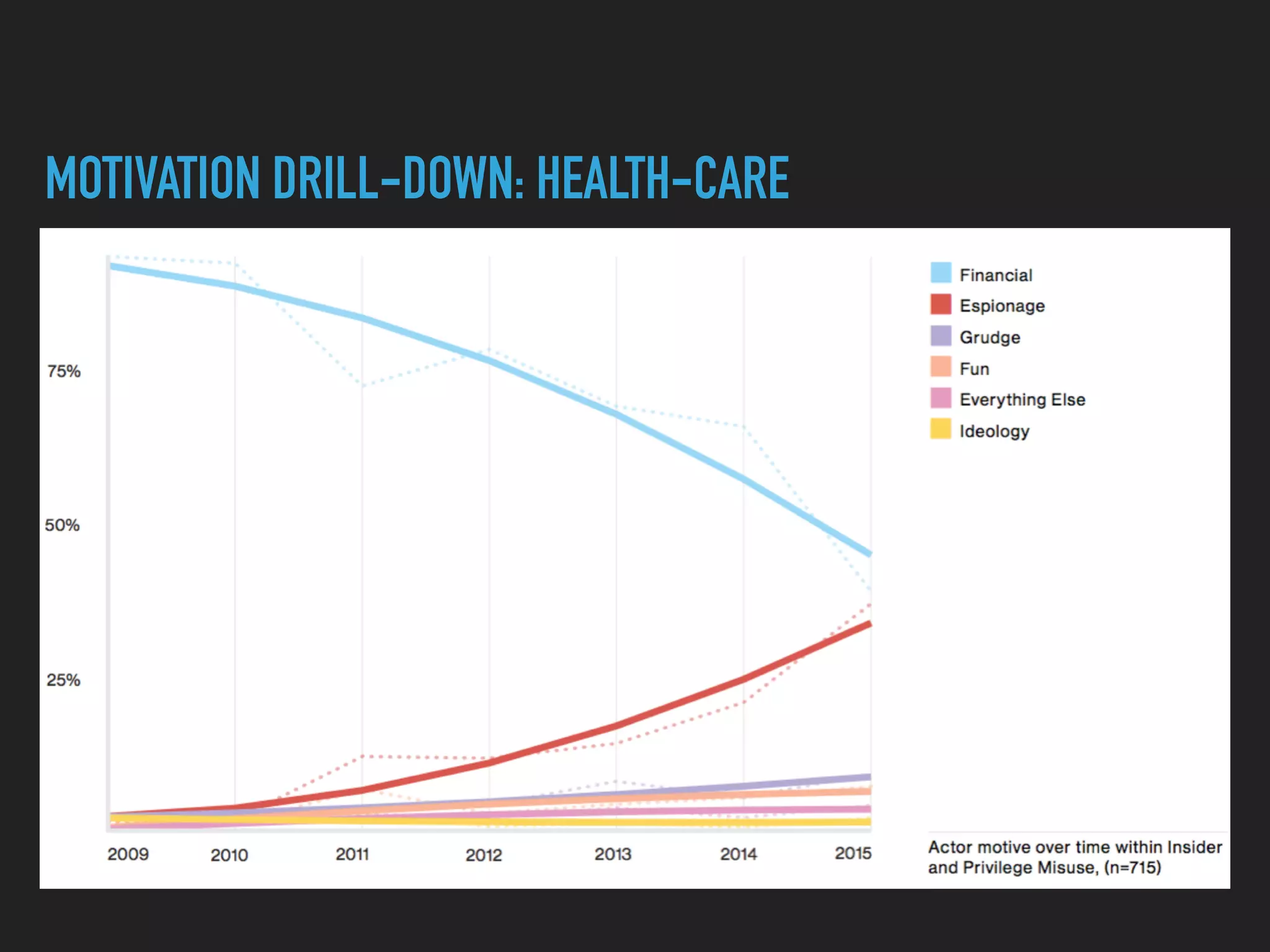
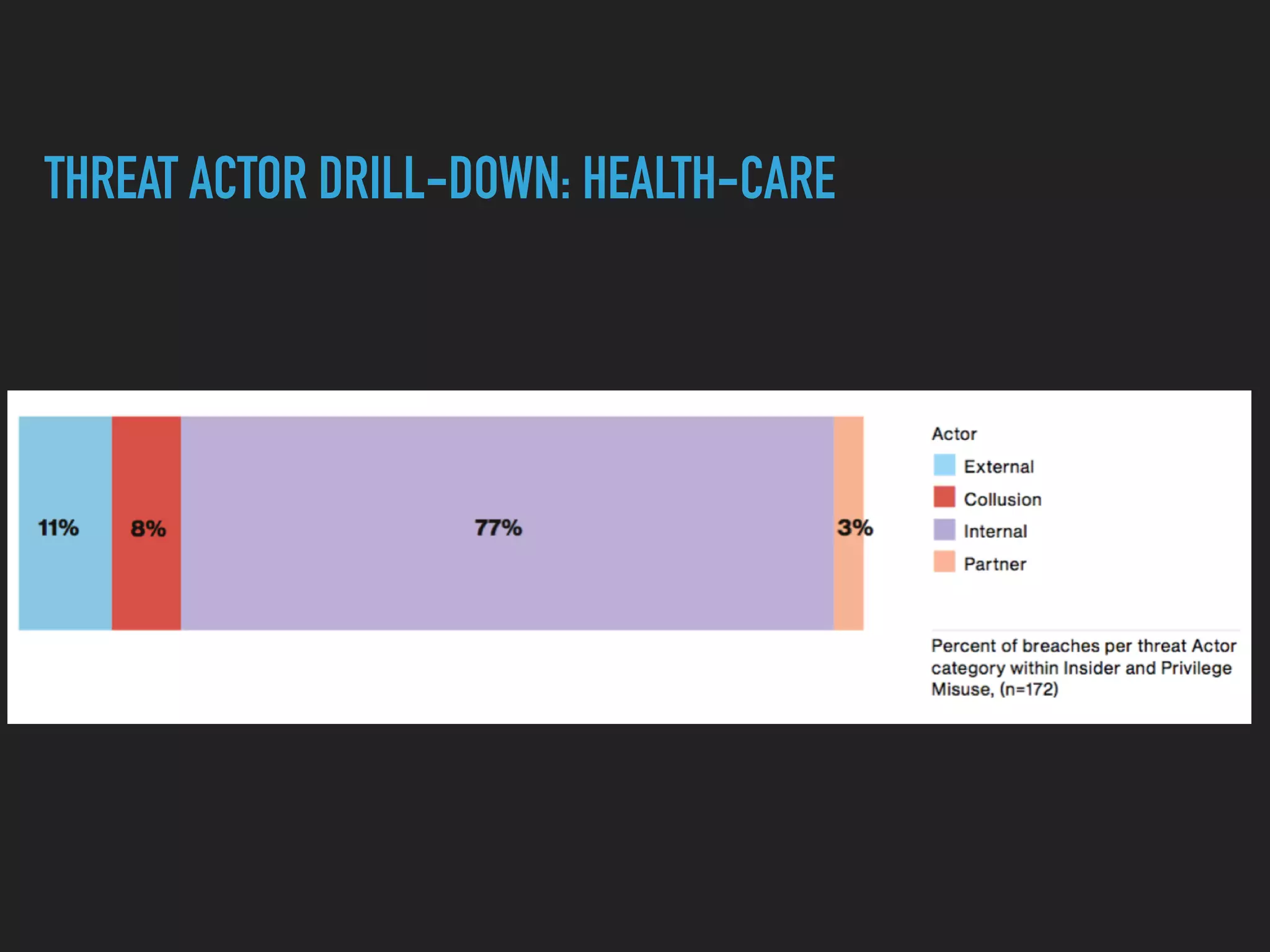
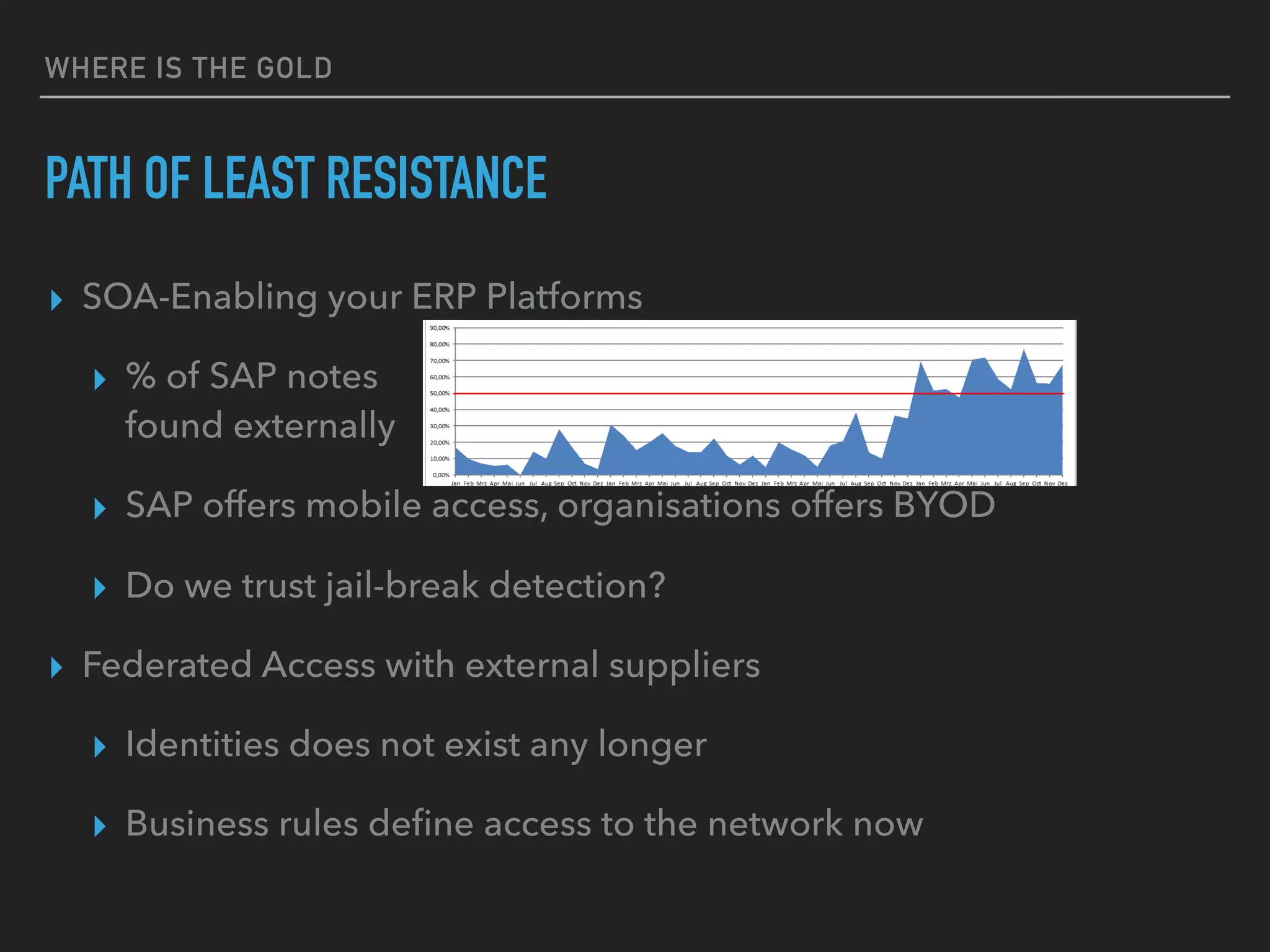
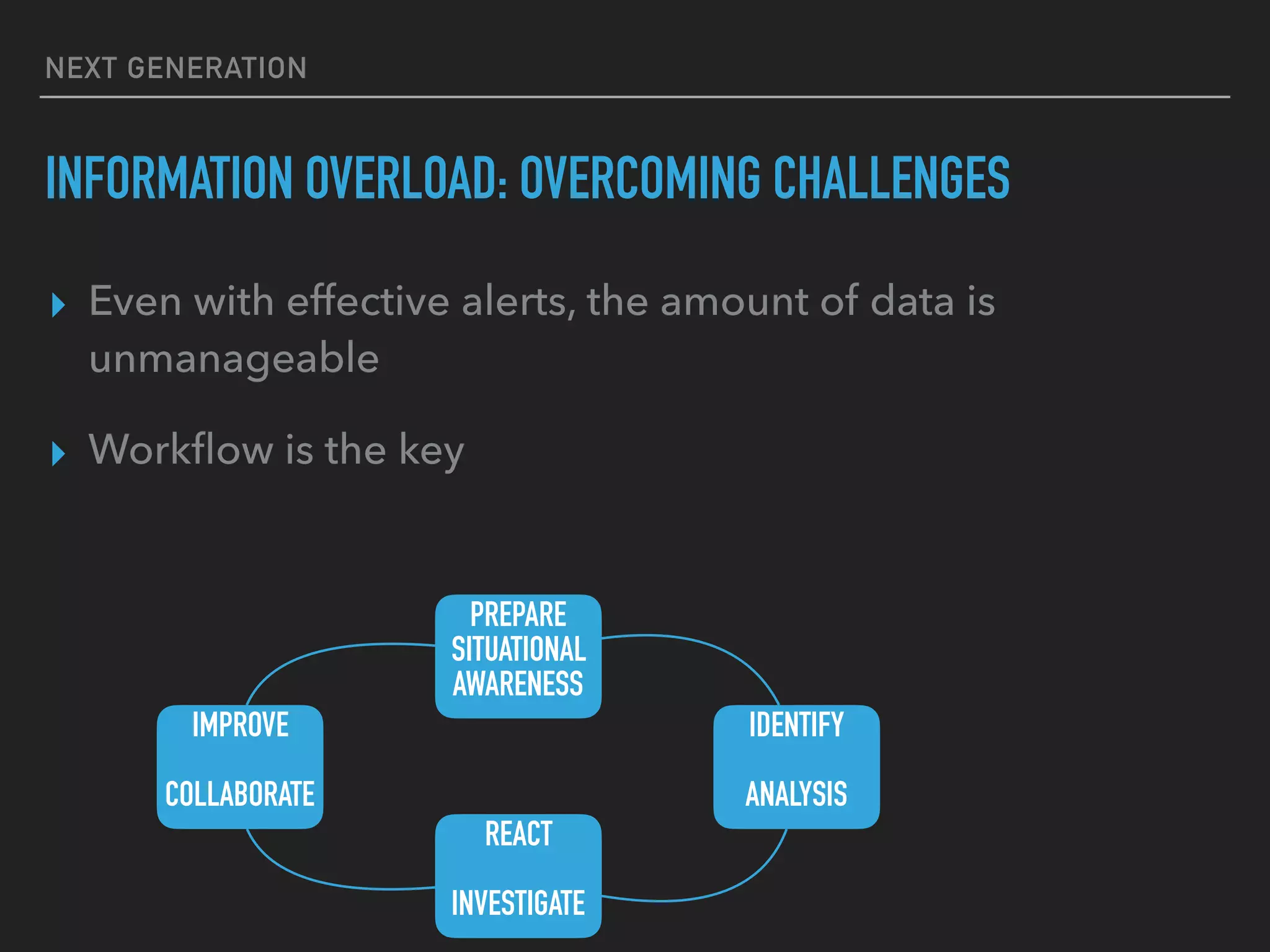
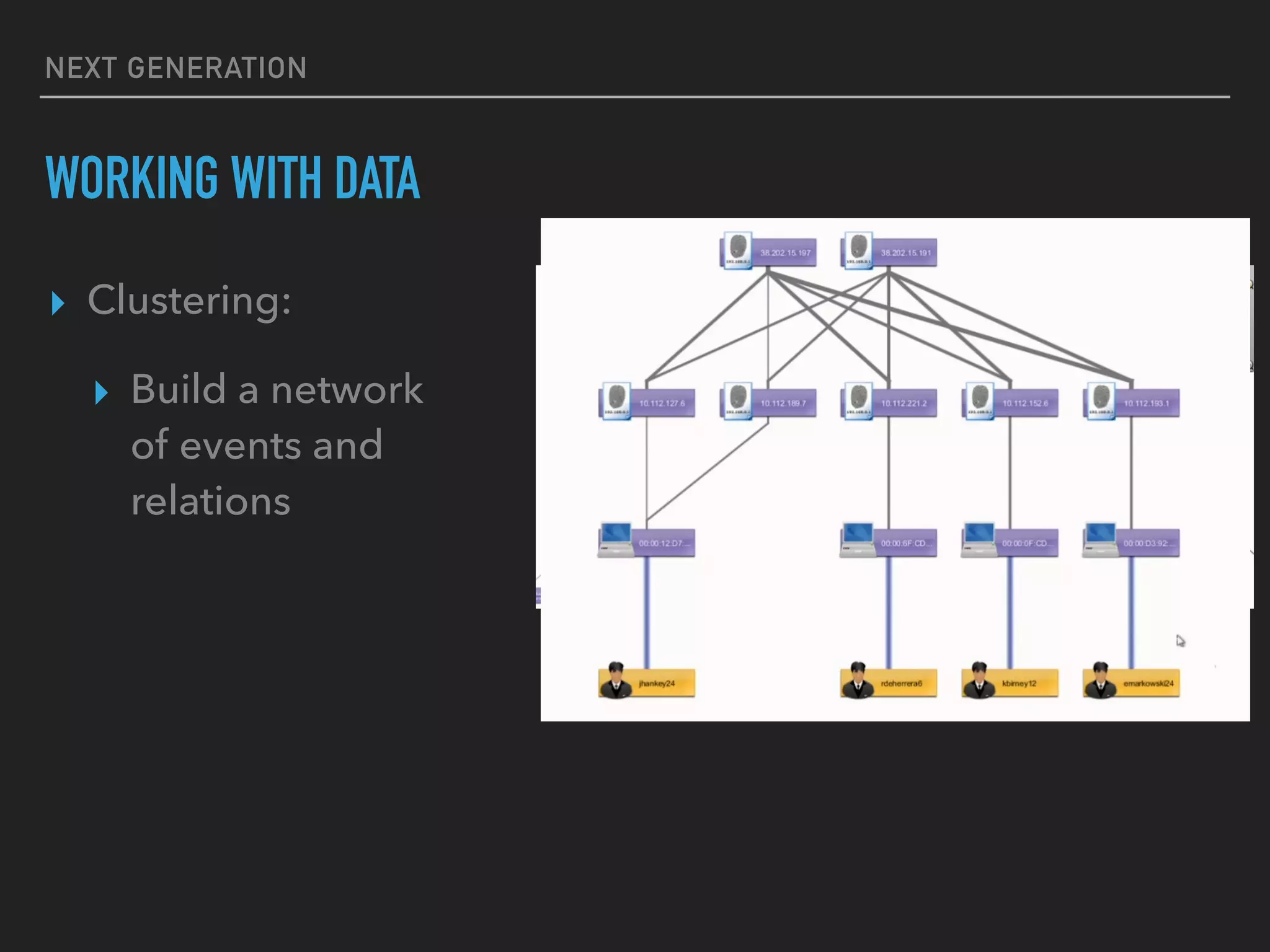
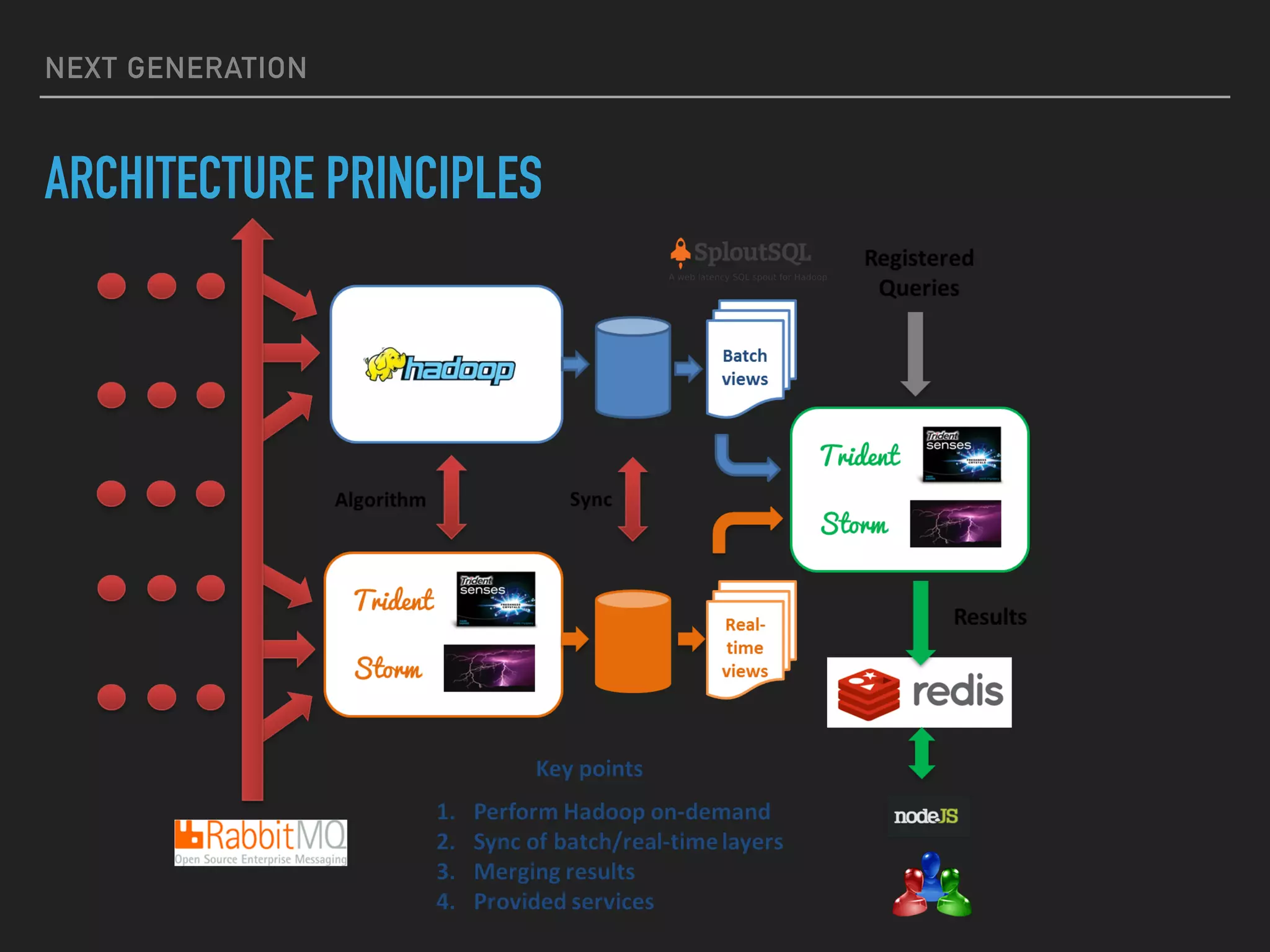
The document discusses the evolution and challenges of next-generation security analytics, emphasizing the economic benefits of attackers and the importance of adaptive security measures. It critiques existing security architectures, advocating for a shift towards more efficient big data frameworks and real-time analytics while incorporating advanced technologies like machine learning. The need for organizations to redefine their security strategies, understand threat landscapes, and leverage data for broader operational use is highlighted as essential for effective defense against evolving cyber threats.