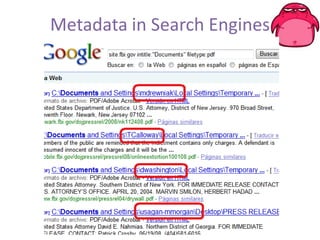
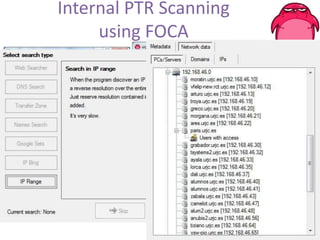
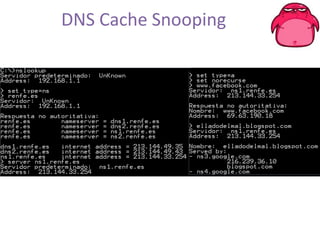
FOCA is a tool that analyzes documents and extracts metadata, hidden information, and lost data that can be used to discover details about an organization's network structure and information systems. It uses metadata analysis and techniques like DNS records analysis, web crawling, and digital certificates to map internal servers, users, groups, file shares, and other details. The latest version of FOCA incorporates additional network discovery capabilities like DNS cache snooping to detect internal software and vulnerabilities. It provides automated and customizable reporting of findings to help security teams identify risks from information leakage.