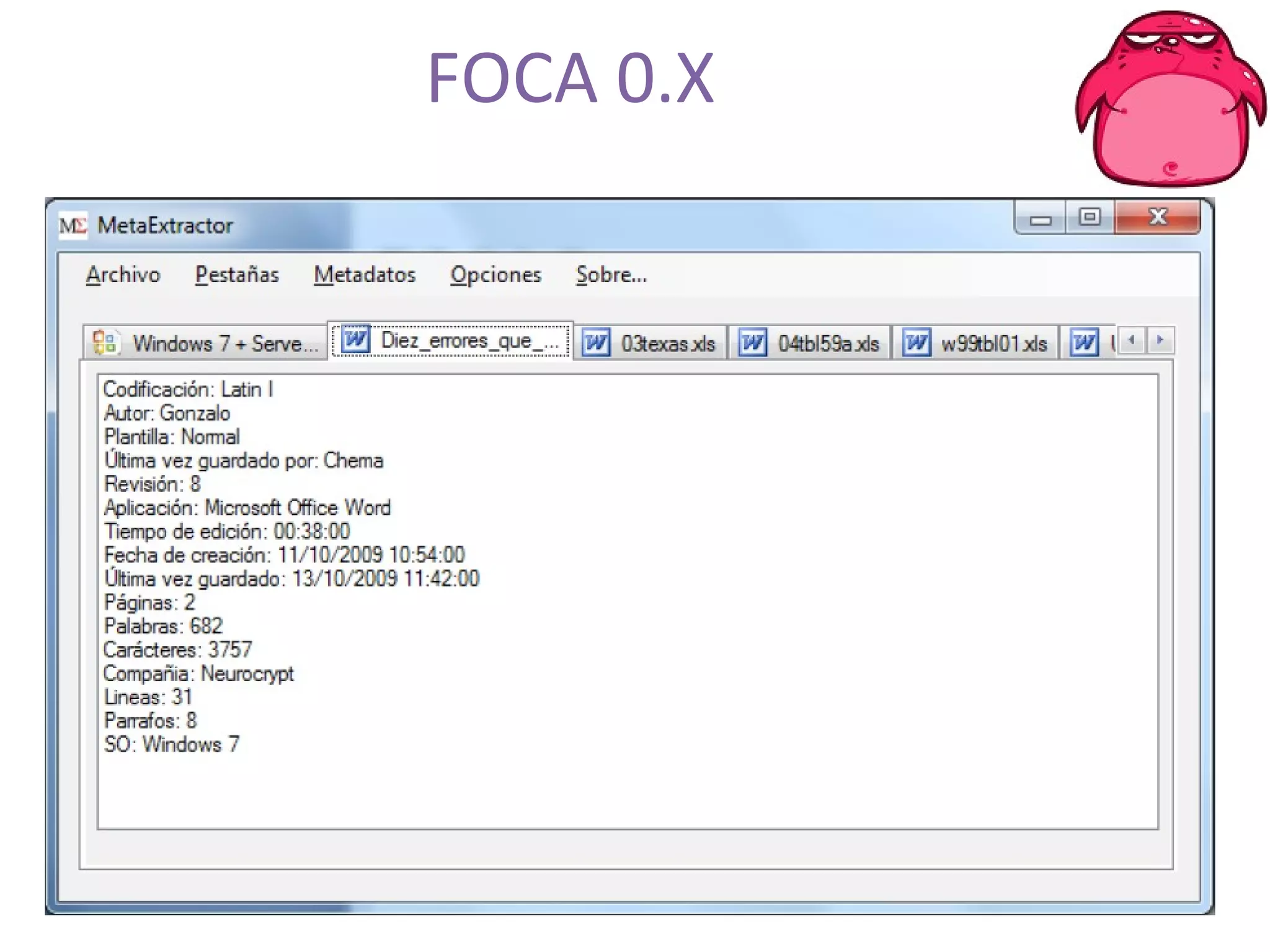
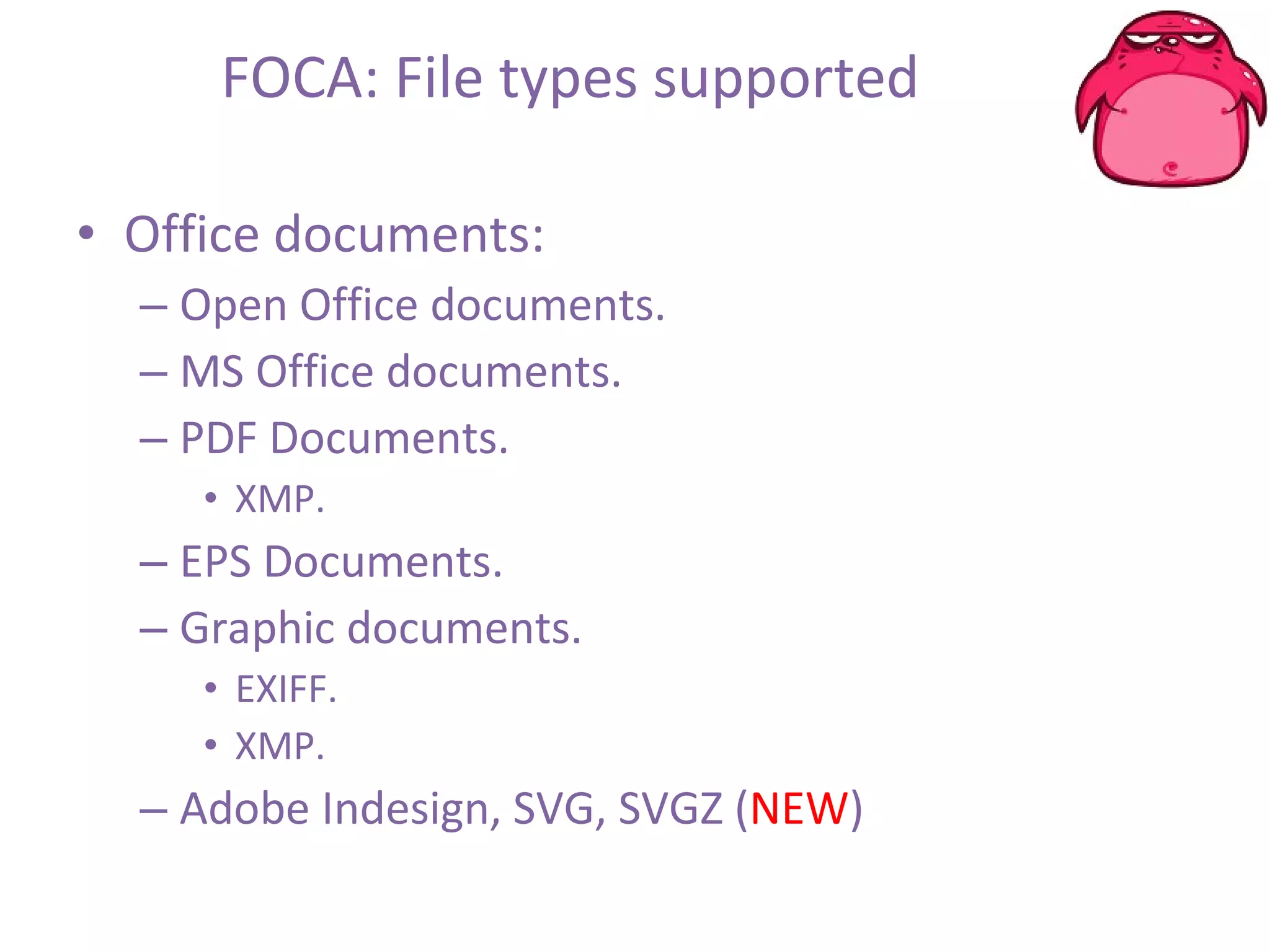
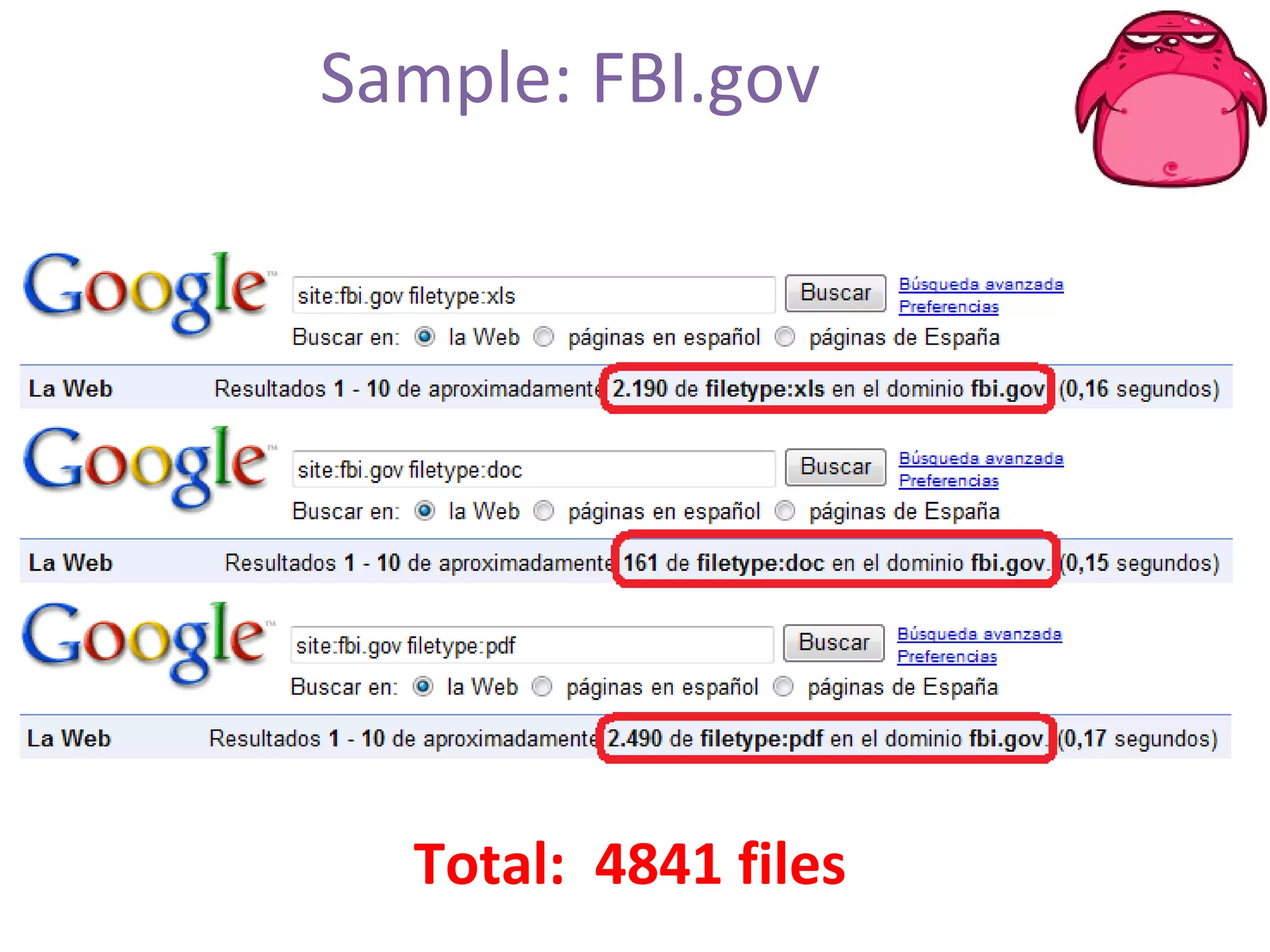
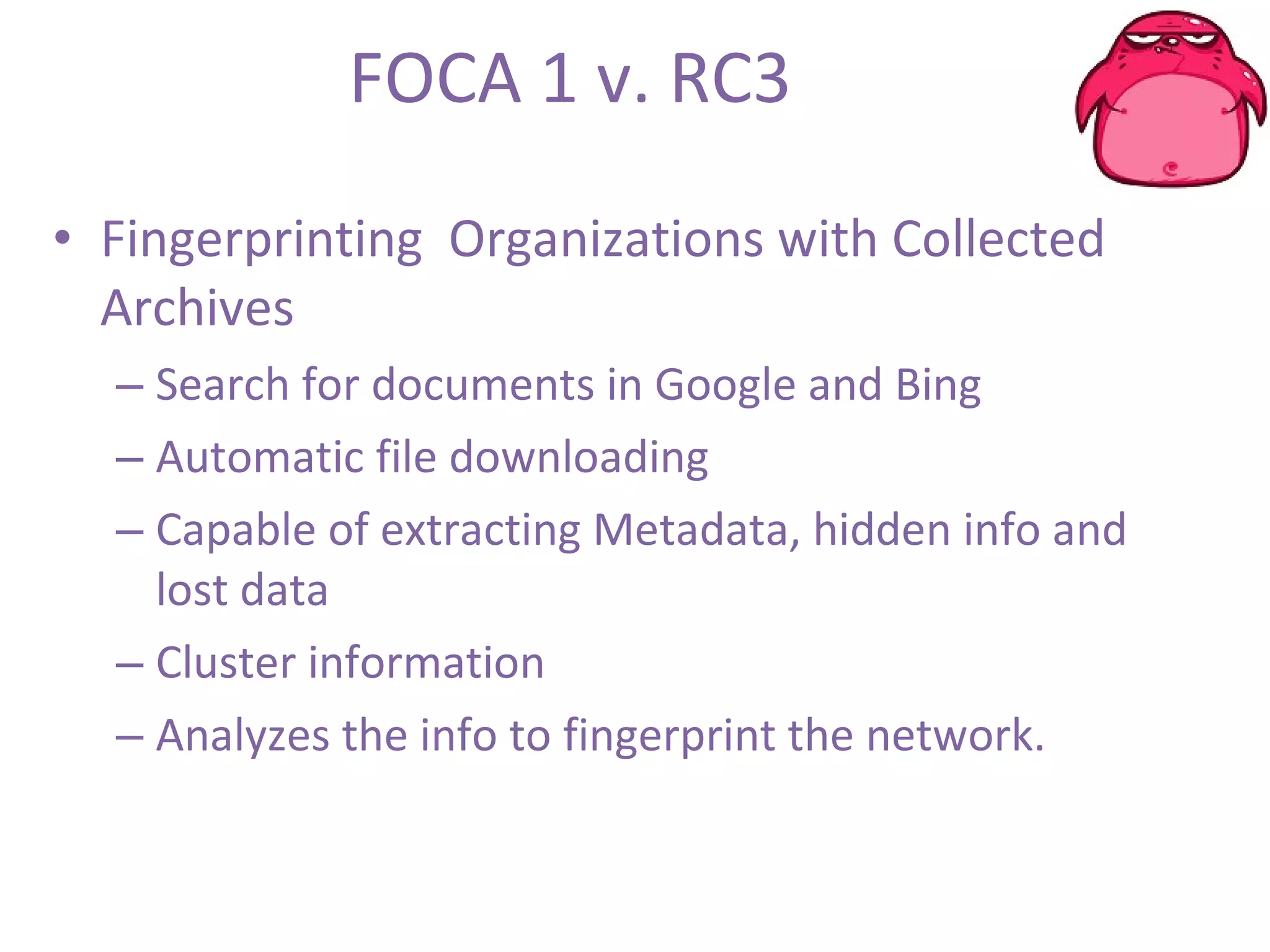
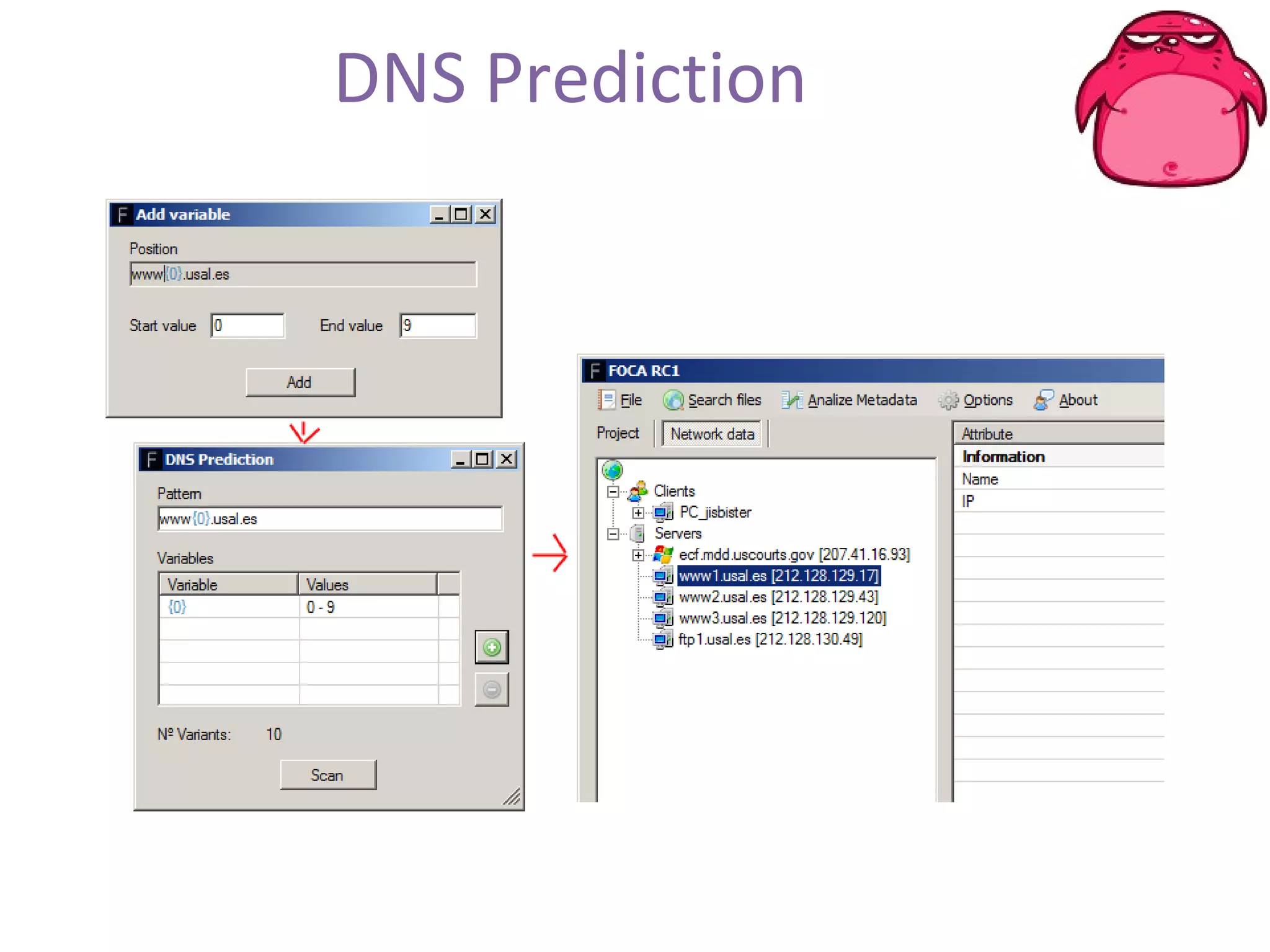
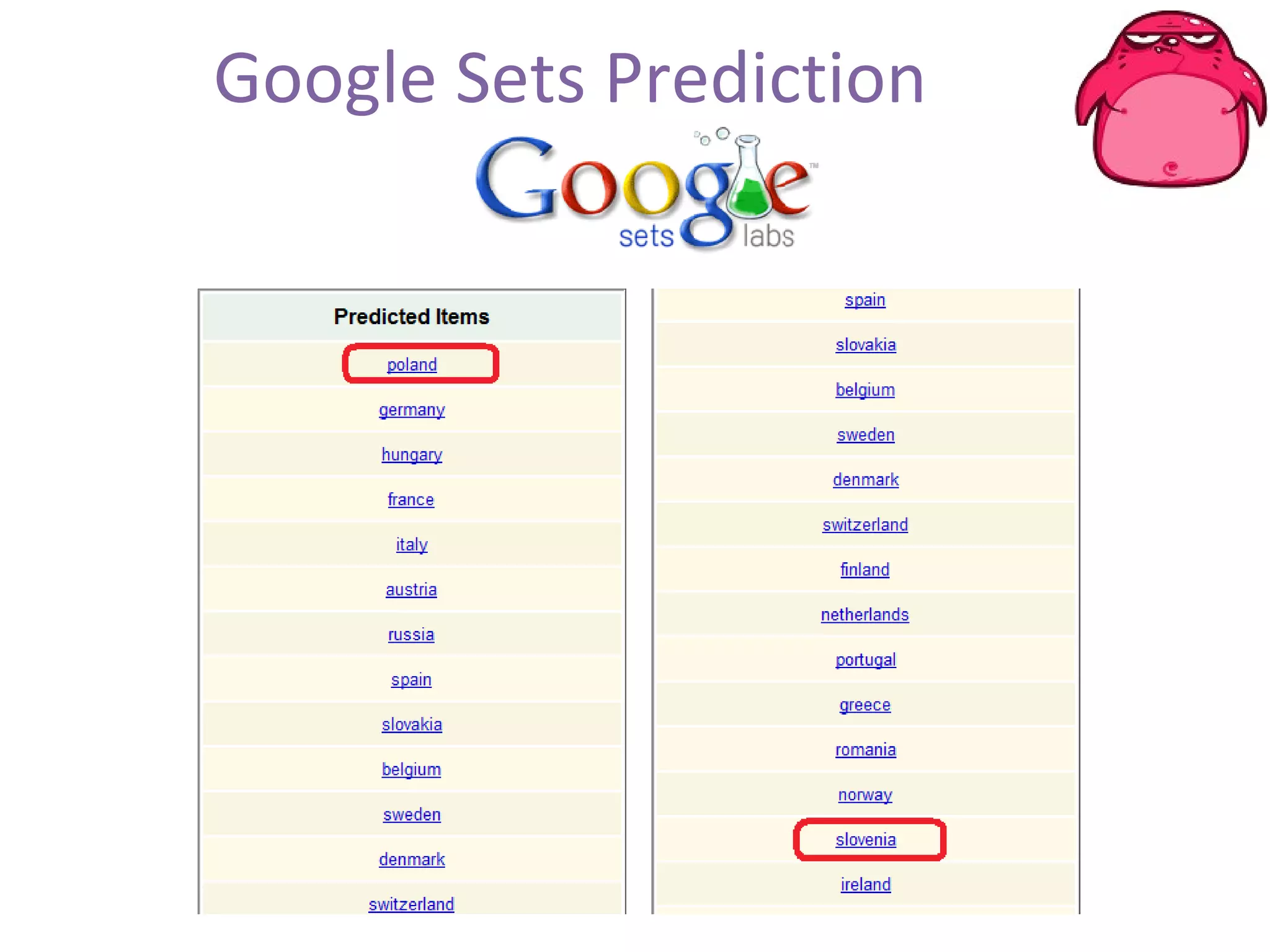
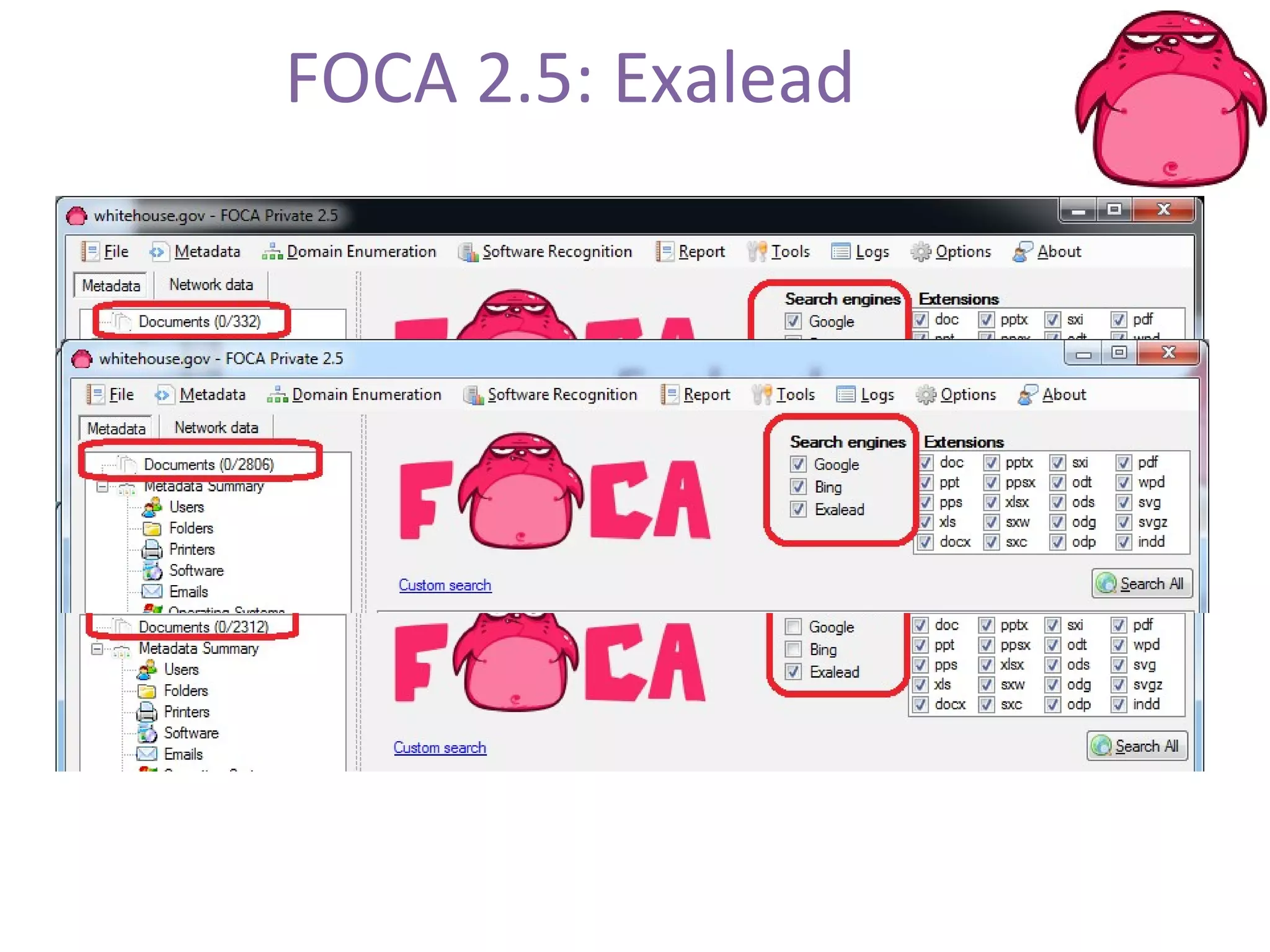
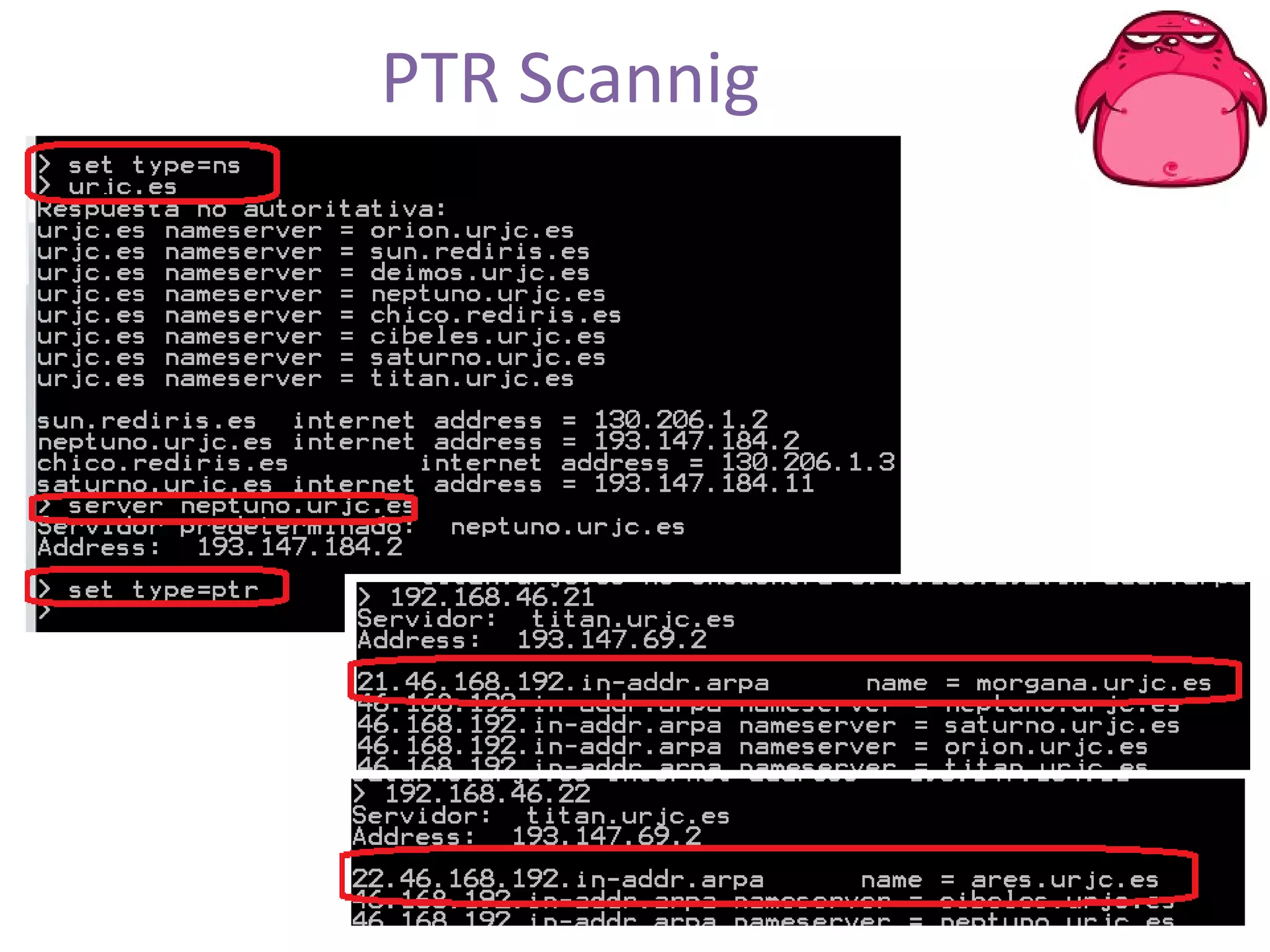
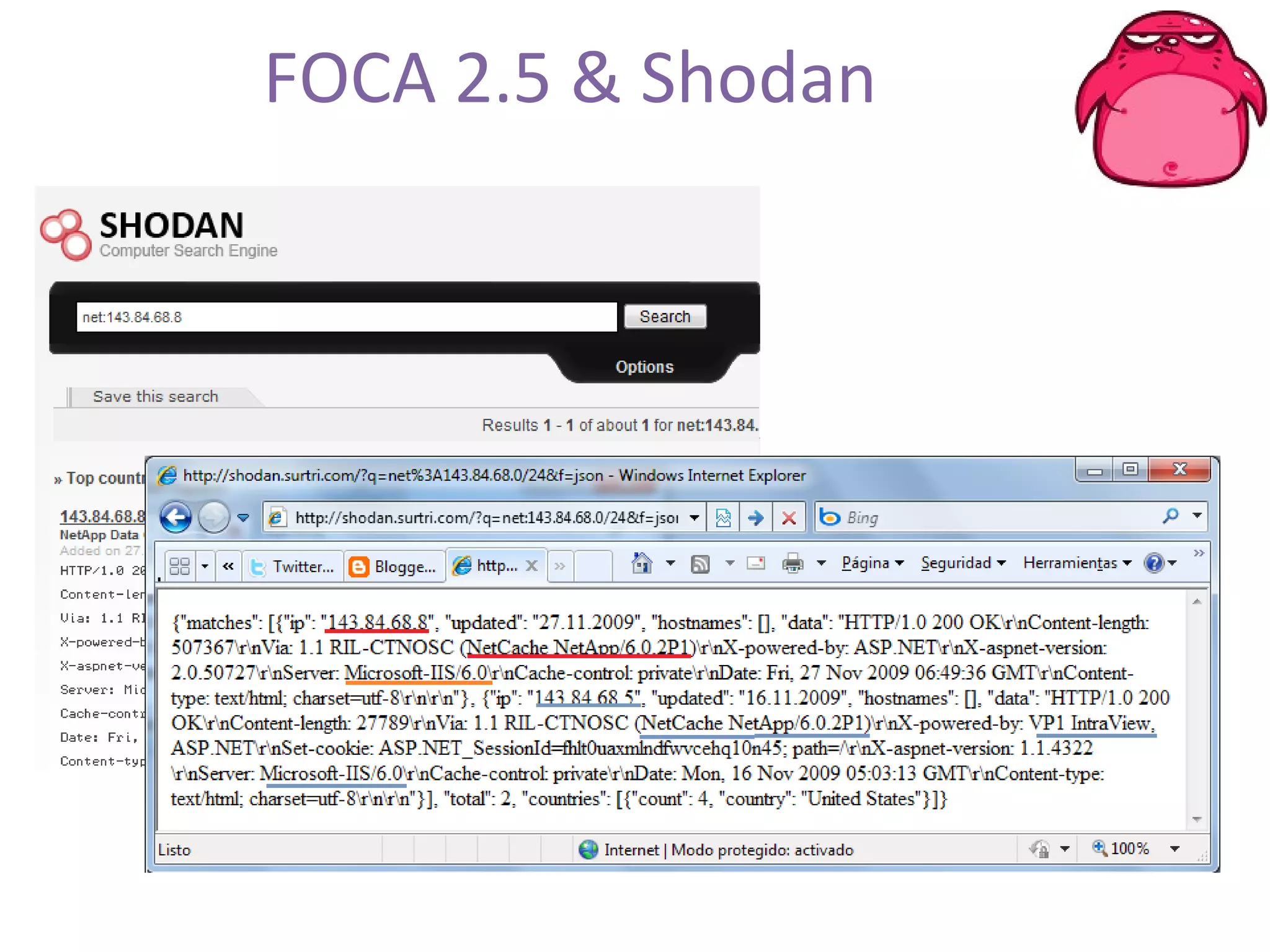
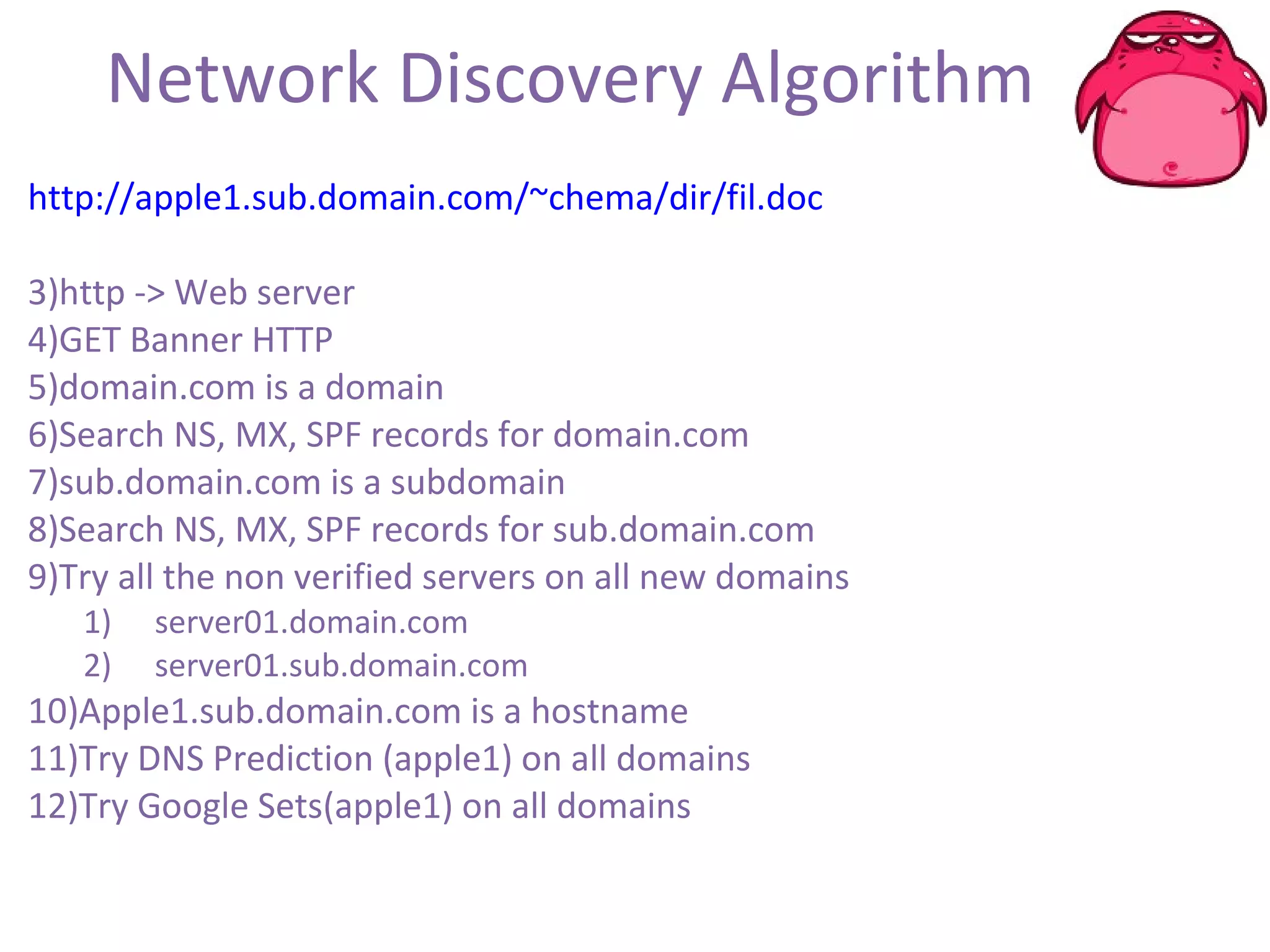
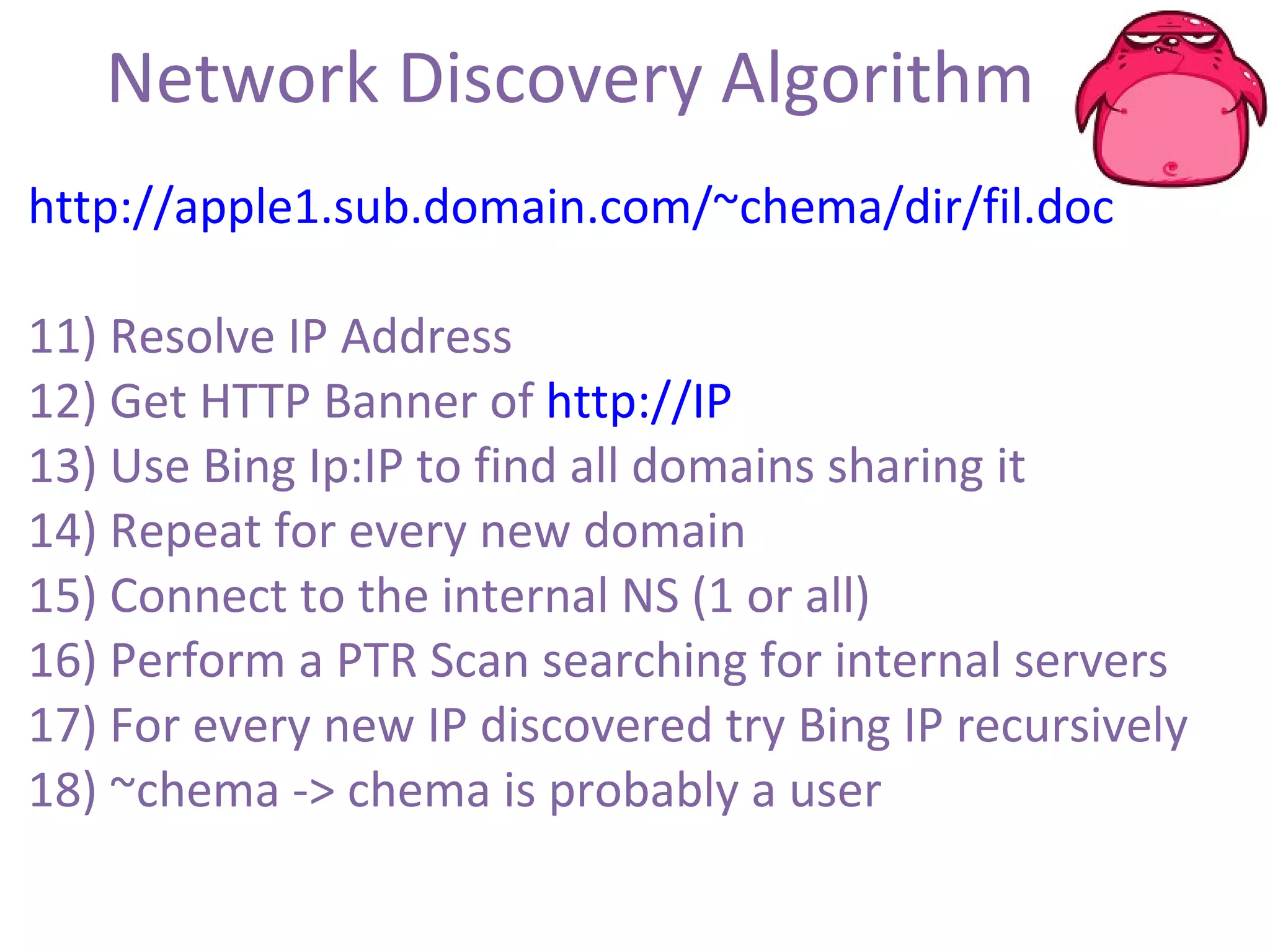
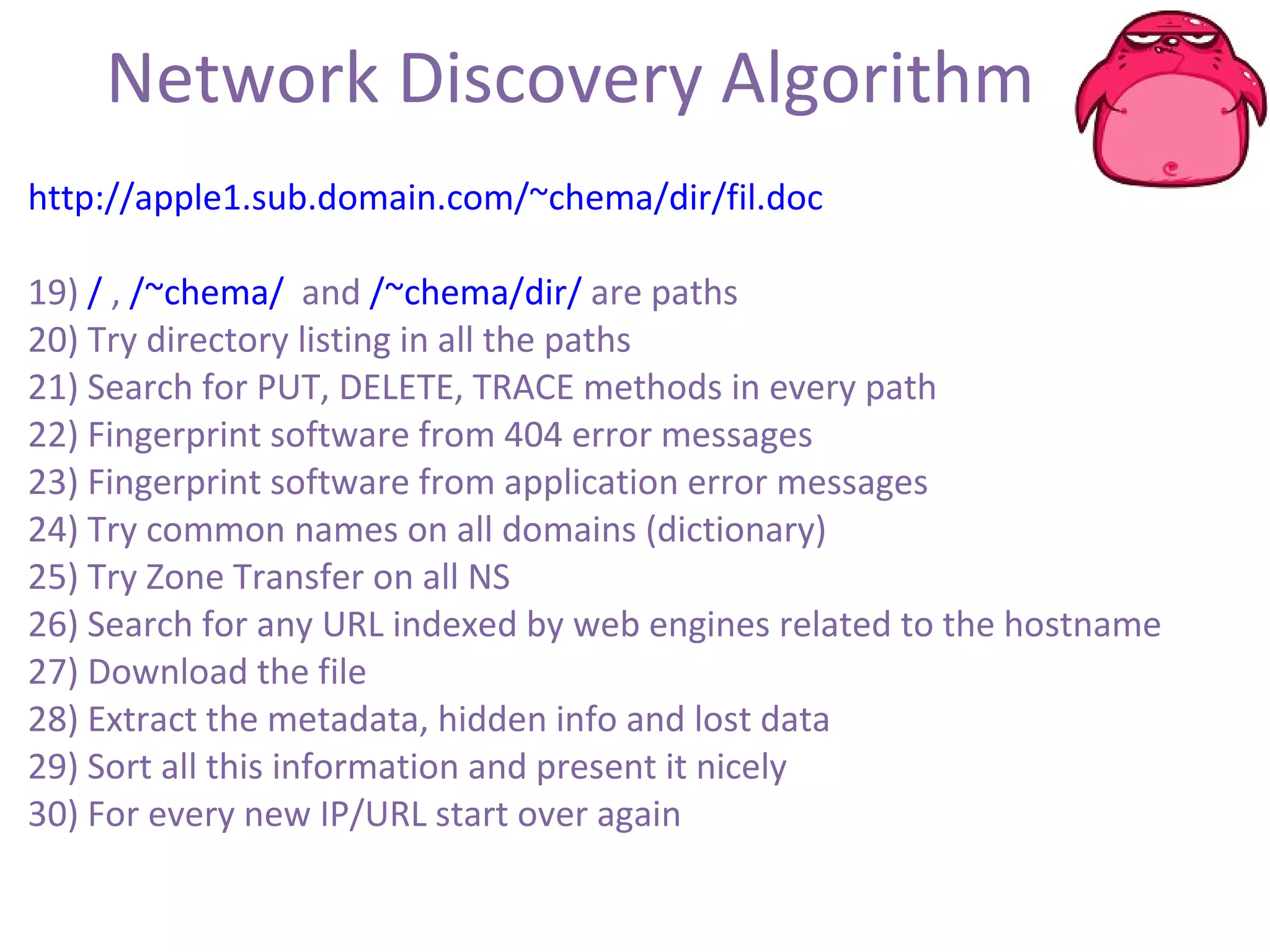
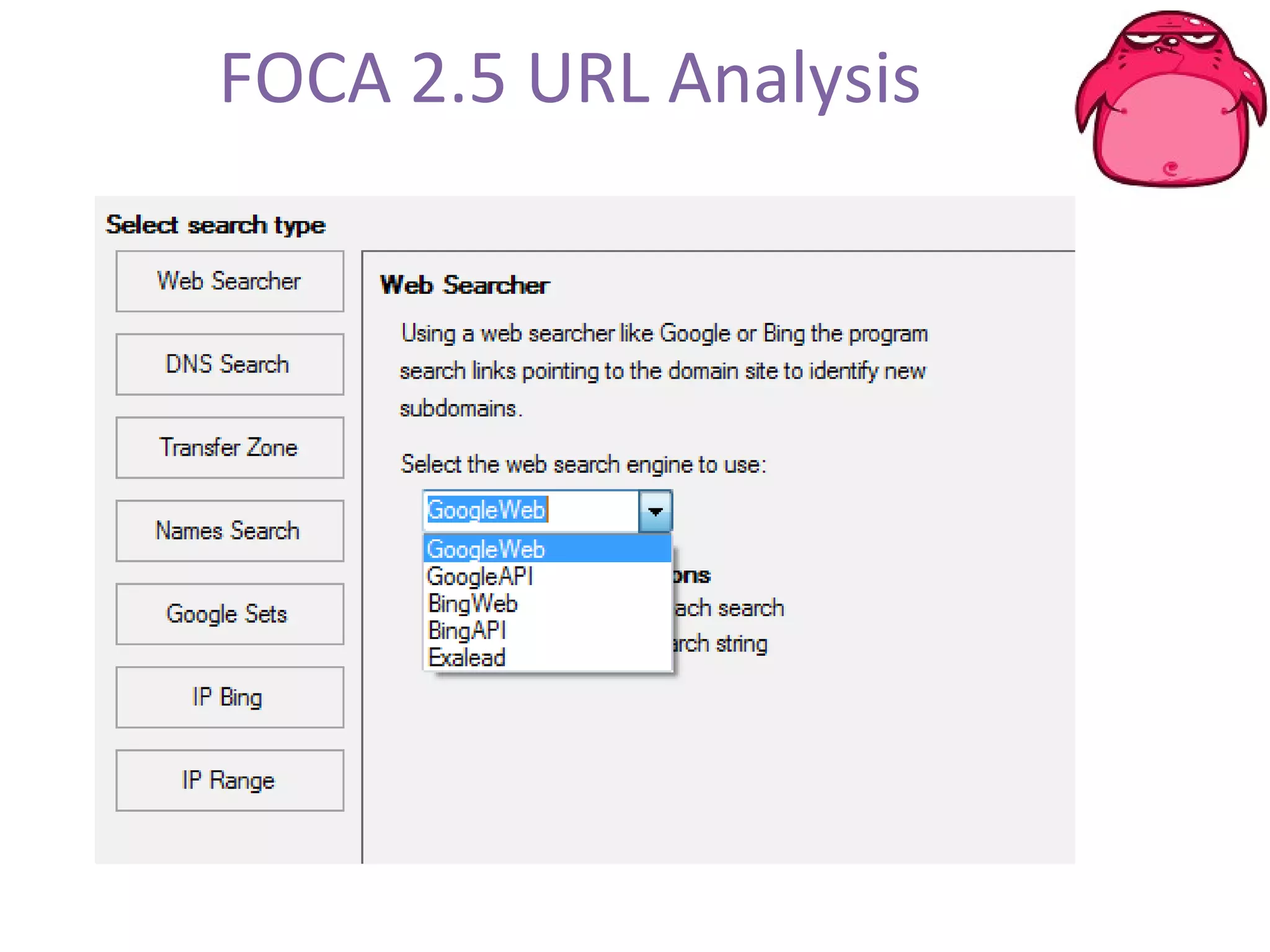
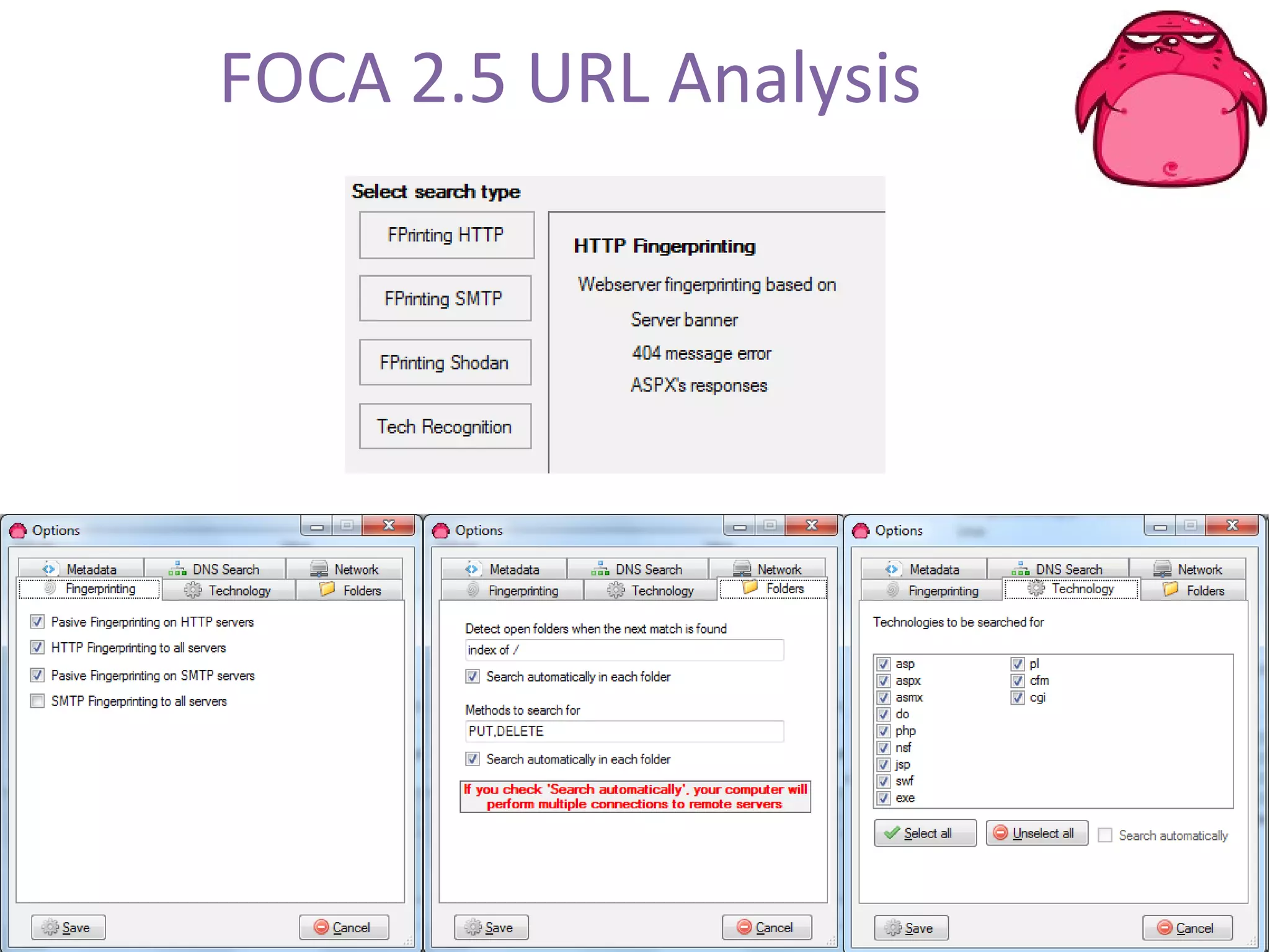
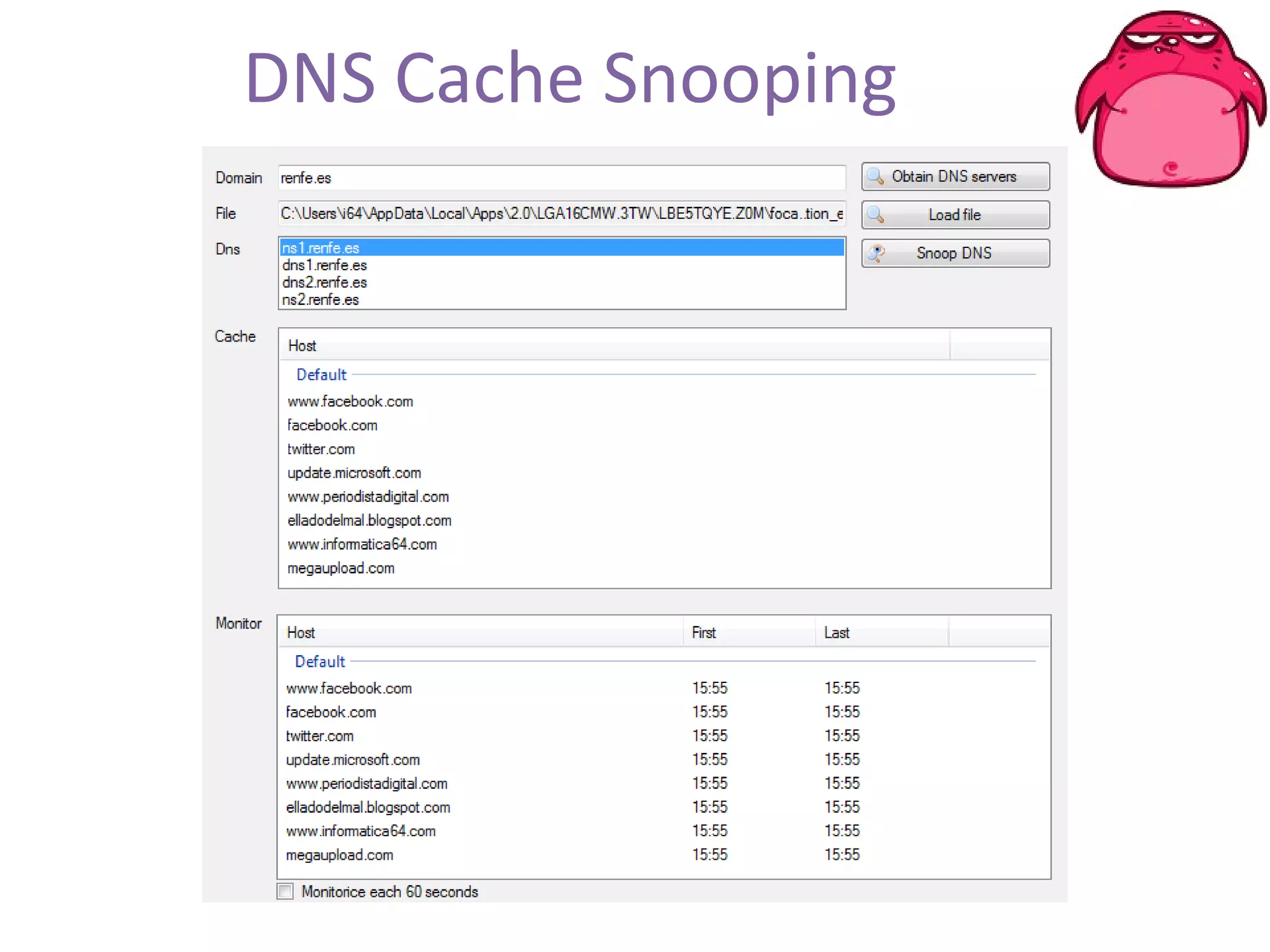
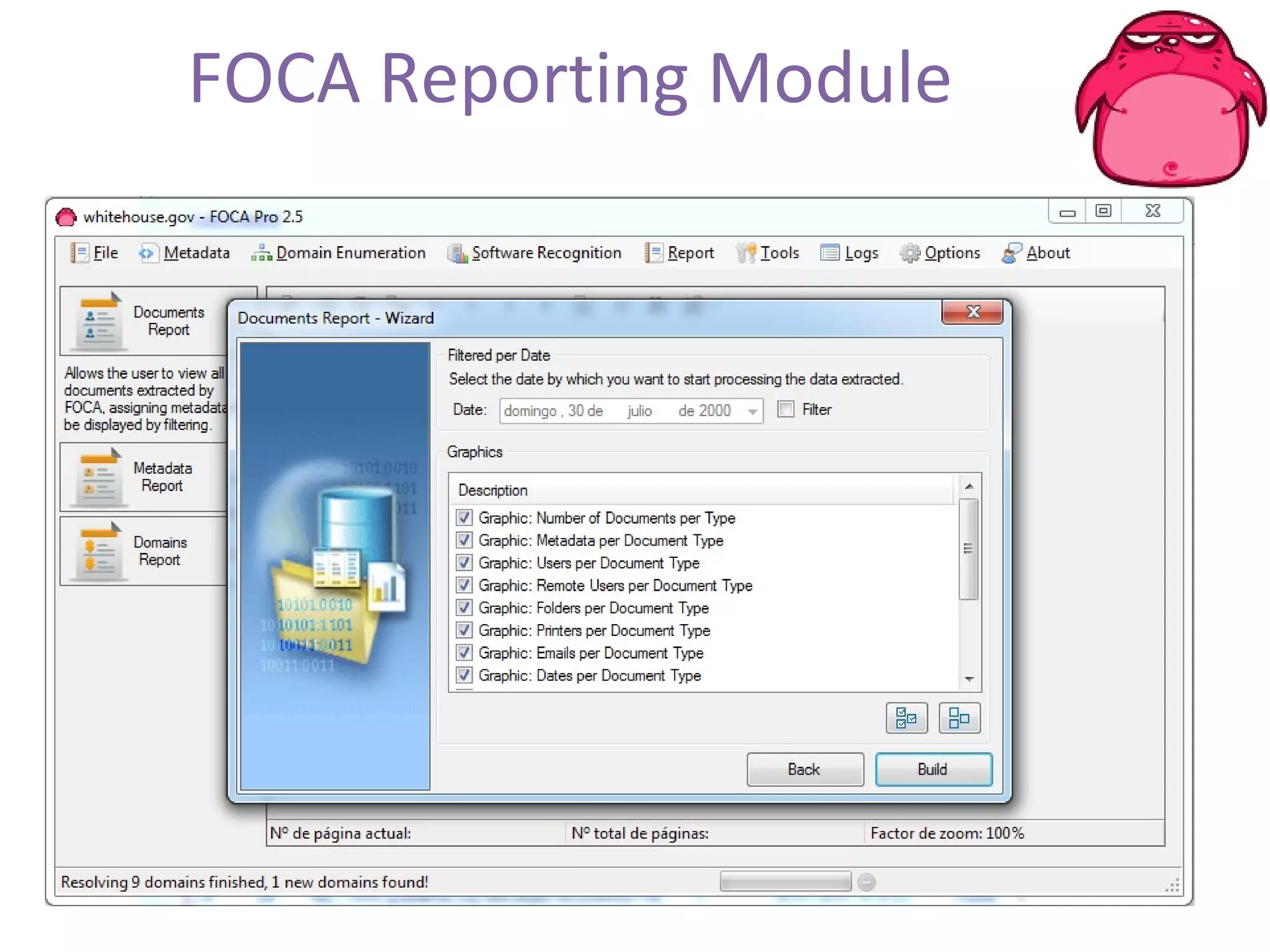
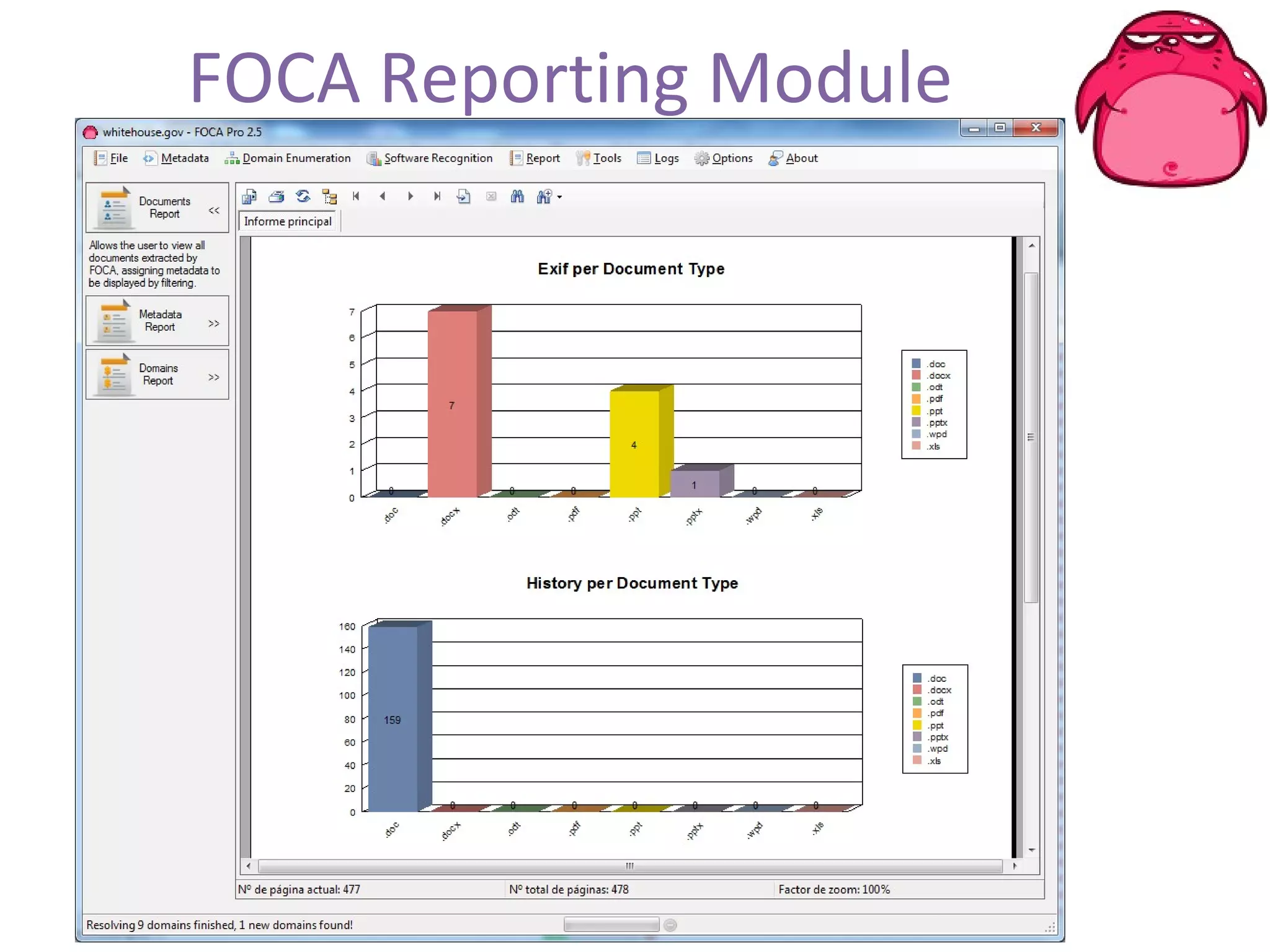
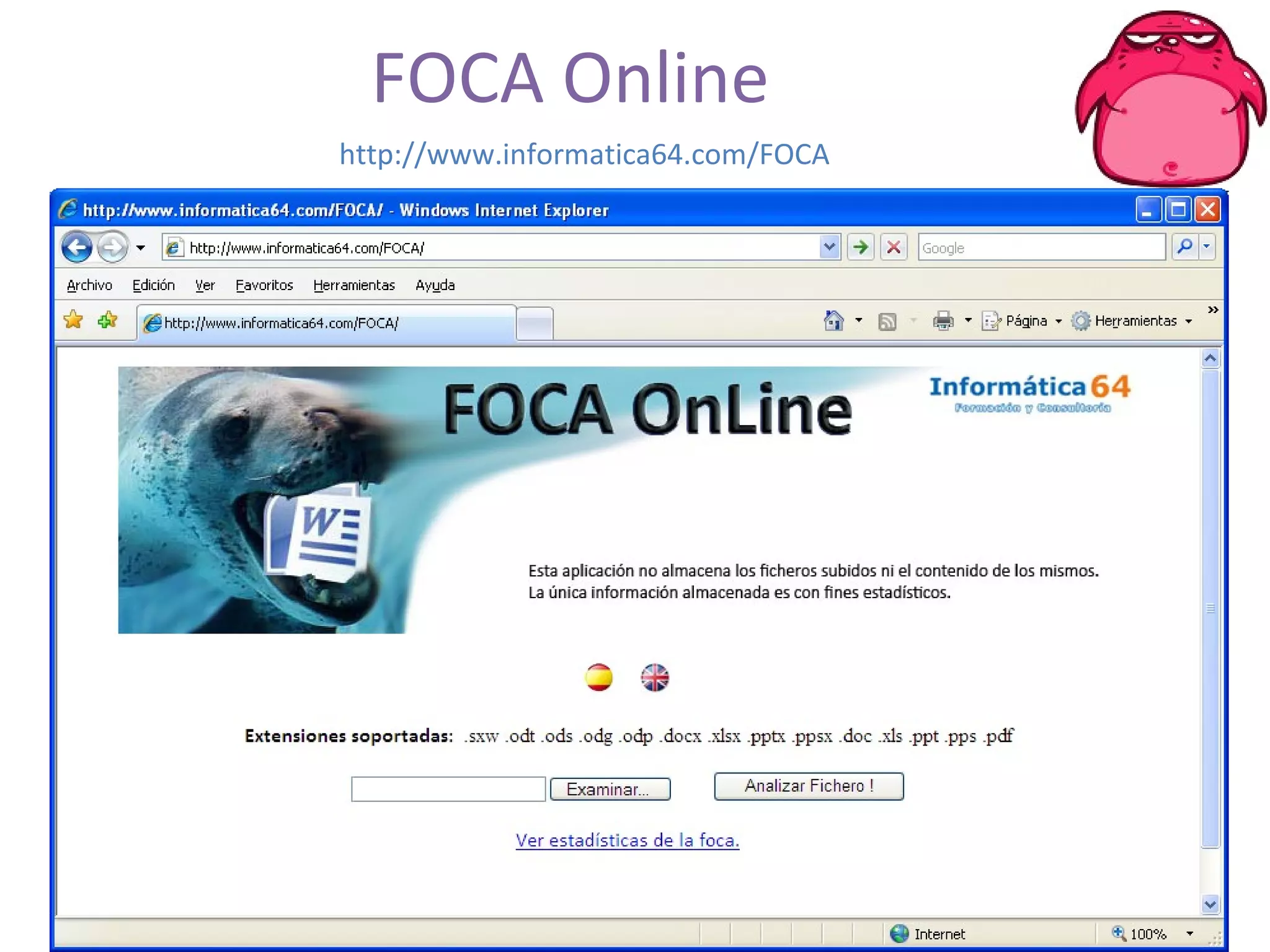
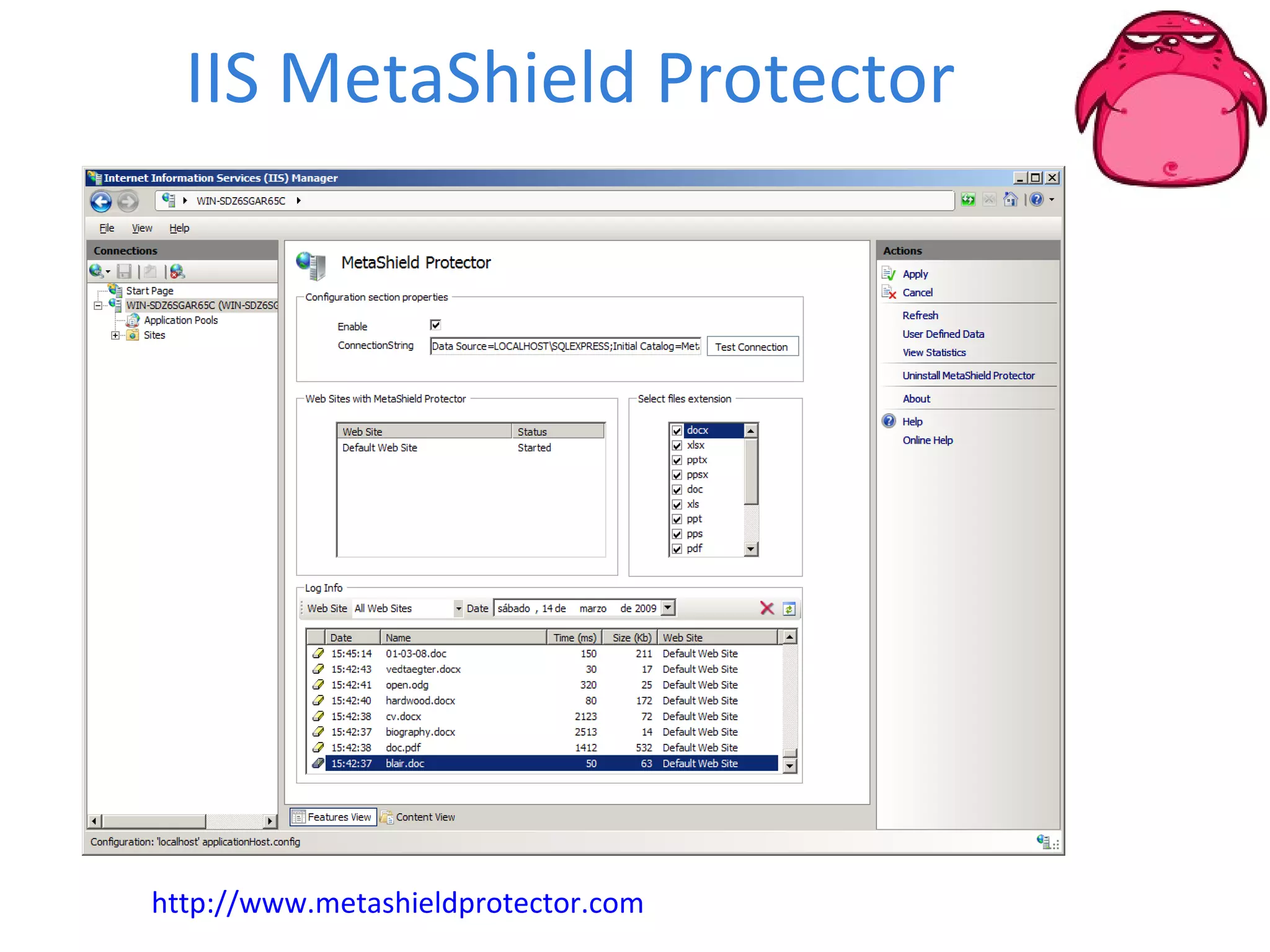
FOCA is a tool that analyzes documents and files to extract metadata, hidden information, and lost data. It can analyze files from websites like Whitehouse.gov. FOCA 2.5 includes new features like network discovery algorithms to recursively map internal networks by resolving IPs, checking DNS records, and using search engines to discover more URLs and domains. It also includes DNS cache snooping and a reporting module to organize extracted information.












![Questions at Q&A room 113 Speakers: Chema Alonso [email_address] Blog: http://elladodelmal.blogspot.com http://twitter.com/chemaalonso José Palazón «PALAKO» [email_address] Working on FOCA: Chema Alonso Alejandro Martín Francisco Oca Manuel Fernández «The Sur» Daniel Romero Enrique Rando Pedro Laguna Special Thanks to: John Matherly [Shodan]](https://image.slidesharecdn.com/foca2-100801114836-phpapp02/75/Defcon-18-FOCA-2-41-2048.jpg)